12 Steps you can take to up your Office 365 Security & Compliance game
I don’t mean to oversimplify things here. This is not a comprehensive guide or anything like that. Every organization has different goals and business objectives, and depending on your industry, etc., you could have very different compliance regulations or whatever, that you need to consider. My goal is just to point out that Office 365, on it’s own and without any administrator interventions, is neither a secure nor compliant platform. It is just a technology platform, and like any other, you can make it as secure and compliant as you want, or as insecure and non-compliant as you want.
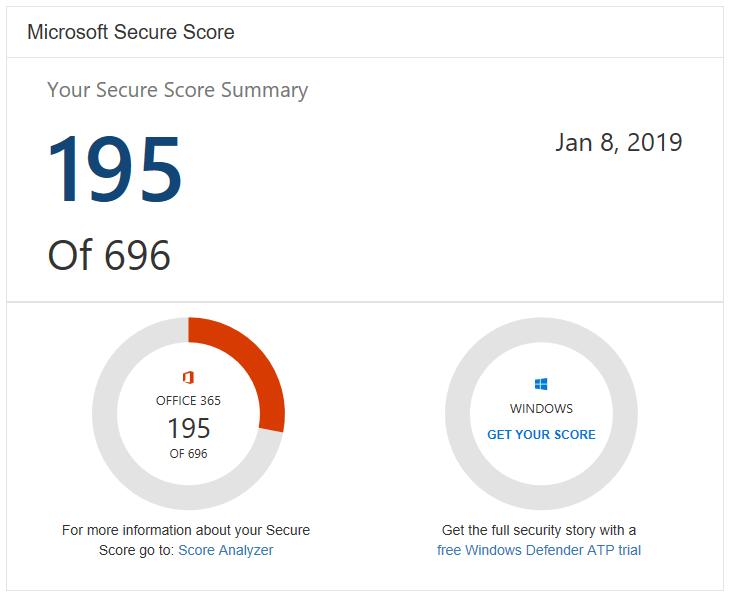
When you get a chance, just check out your “Secure Score” in Office 365, and you’ll see what I mean.
I will break this article down into two sections: in the first section, I will include steps that you can take with any Office 365 subscription, regardless of bundle inclusions/exclusions. The second section will apply specifically to Microsoft 365 Business plans (or plans with the right add-on subscriptions, which I will also indicate). And remember: this is not complete or comprehensive, it is just offering suggestions for where you can get started.
One more note before we begin: I am proceeding under the assumption that almost every organization starts their journey into 365 by moving email from an on-premise Exchange server or other hosted provider. So most of these items apply to Exchange Online, but some will be applicable to the other 365 applications as well.
Available with all subscriptions
1. Configure Multifactor authentication (MFA): This is becoming more and more a required “thing” for so many organizations–not just because of compliance but just for general safety. The number of targeted spear phishing attacks, credential leaks, and other scary things out there today is just too rampant. A compromised password or identity can be mitigated using a second factor of authentication such as a mobile app or hardware token. MFA is the number one recommendation.
2. Dial in your anti-spam settings: The defaults in Exchange Online leave something to be desired, for example you might want your users to have an anti-spam digest, and you probably want at least a few other settings flipped to “on” in your tenant. For example, you probably want to be notified if your outbound SPAM filter is catching content coming from your users. Review and dial this stuff in; it doesn’t take long to do, and can go a long ways.
3. Disable client forwarding: There are several ways to accomplish this, but in general you should be wary of allowing users to auto-forward emails to outside addresses. This is usually one of the first things attackers do when they gain access to a mailbox account.
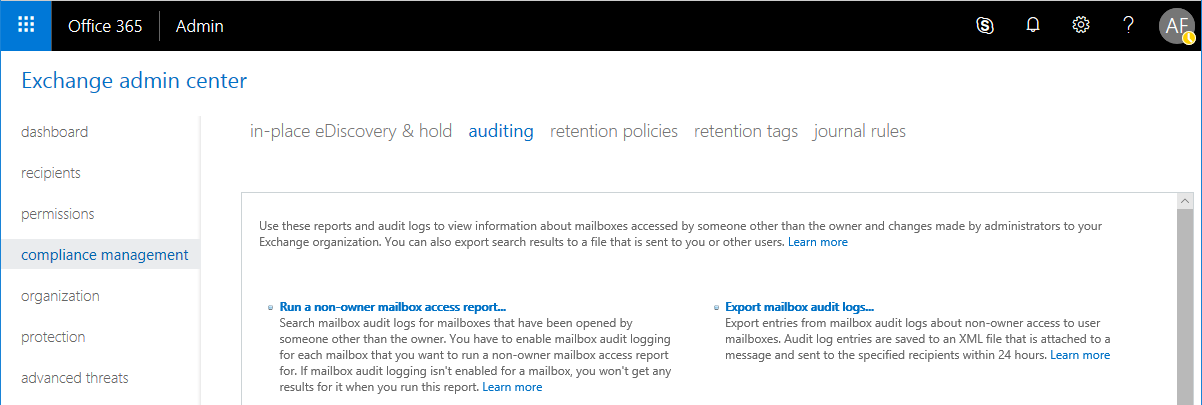
4. Auditing in Exchange Online: This is one of those things… In the past, tenants did not have auditing configured, so most of the useful reports were empty and contained no data. Now, Microsoft is going to be enabling the audit features by default, which is a good thing. Regularly review reports such as the non-owner mailbox access report.
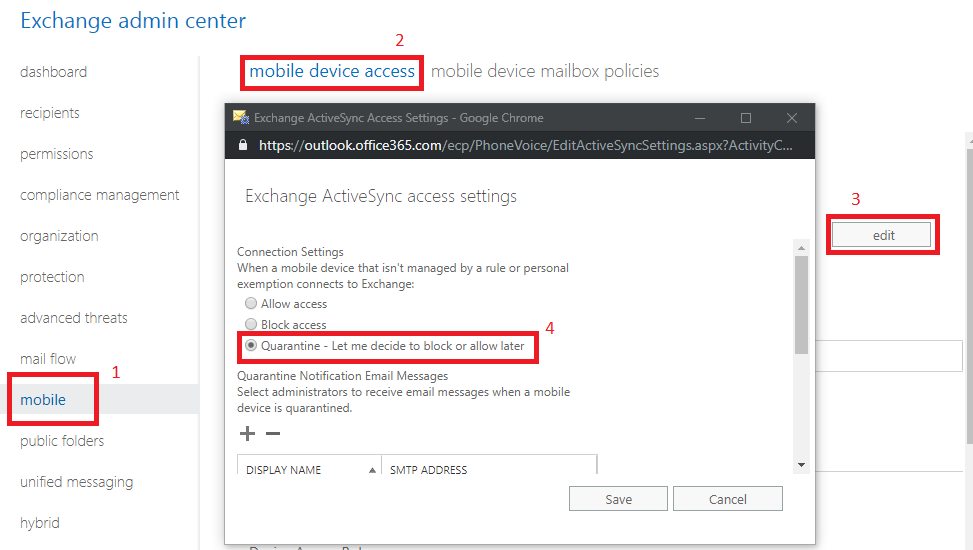
5. Device management: Manage mobile devices, either through an MDM policy or an Exchange Active Sync policy. Intune takes things even further here and if you have that subscription then I encourage you to explore it, but start with Exchange Active Sync, at the very least. If you are primarily using Exchange Online, you should check out this script, to output an inventory of mobile devices with details by user from Exchange Online–do this regularly, at least once per quarter. Also, you can setup a quarantine for devices, so they have to be approved by an admin, before being allowed to connect to Exchange Online:
Finally, you can also join Windows 10 devices to Azure AD, and this has some benefits you should read up on. Just as with mobile devices, you should audit the inventory of your Azure AD-joined devices registered in Azure AD, and prune the stale devices. This regular maintenance is most effective when paired with an actual inventory to compare against–so do try and figure out how to identify whether devices are legitimate, before you review any reports/data coming from your tenant. The options are expanding and getting more interesting as we move forward with the new Microsoft 365 plans, also–so consider that as well.
6. Limit admin privilege: This actually applies to any/all technology platforms, and should go without saying, but I will say it anyways: You should always limit your admin access to those people who absolutely need it, and only when they need it. Usually this means, for example, that as an IT admin for your organization, you do NOT assign the global admin role to your own user account, which you use everyday for Exchange email, SharePoint, etc; instead, you would configure a separate admin account with different credentials. And of course, protect that sucker with MFA (which will be the default anyway, soon enough, due to a default Conditional Access policy that is being added to all tenants). Last, know that Azure AD Premium P2 licensing includes some special tools for managing Privileged identities (PIM), which might be worth looking at, but again you can do a lot to limit admin privilege manually, without fancy tools.
7. Configure SPF, DKIM and DMARC: Protect your domain from being spoofed and from other common attacks. SPF is a bare minimum, but DKIM and DMARC are recommended as well, since they add the ability to digitally sign email headers, and prove to recipient servers that your organization’s messages came from “the right place.”
Available in Microsoft 365 Business
8. Configure archive and retention policies: If your plan includes Exchange Online Archiving (sold separately for USD $3.00/user/month), then your organization may want to protect and retain information for a given length of time, or delete it after a certain time period has elapsed. Archive mailboxes and basic retention policies can be configured within Exchange Online, but when managed from the Security & Compliance center, it can become an even more powerful tool, as we can apply policies to content across the entire Office 365 ecosystem (not just your email).
9. Enable Office Message Encryption (OME): Azure Information Protection is included with Microsoft 365 Business, but can be purchased separately for USD $2.00/user/month, allowing your users to encrypt messages sent inside or outside the organization, and protect attachments or other documents with certain restrictions, if they so choose.
10. Configure Data Loss Prevention Policy (DLP): DLP is a feature that allows you to name some conditions (such as finding content containing credit cards, bank numbers, tax identification numbers, etc.), and take some action based on that criteria–for example blocking the content from being shared externally, notifying the offending user or filing an incident report with a compliance administrator. You can also configure a policy to auto-encrypt content, rather than block it.
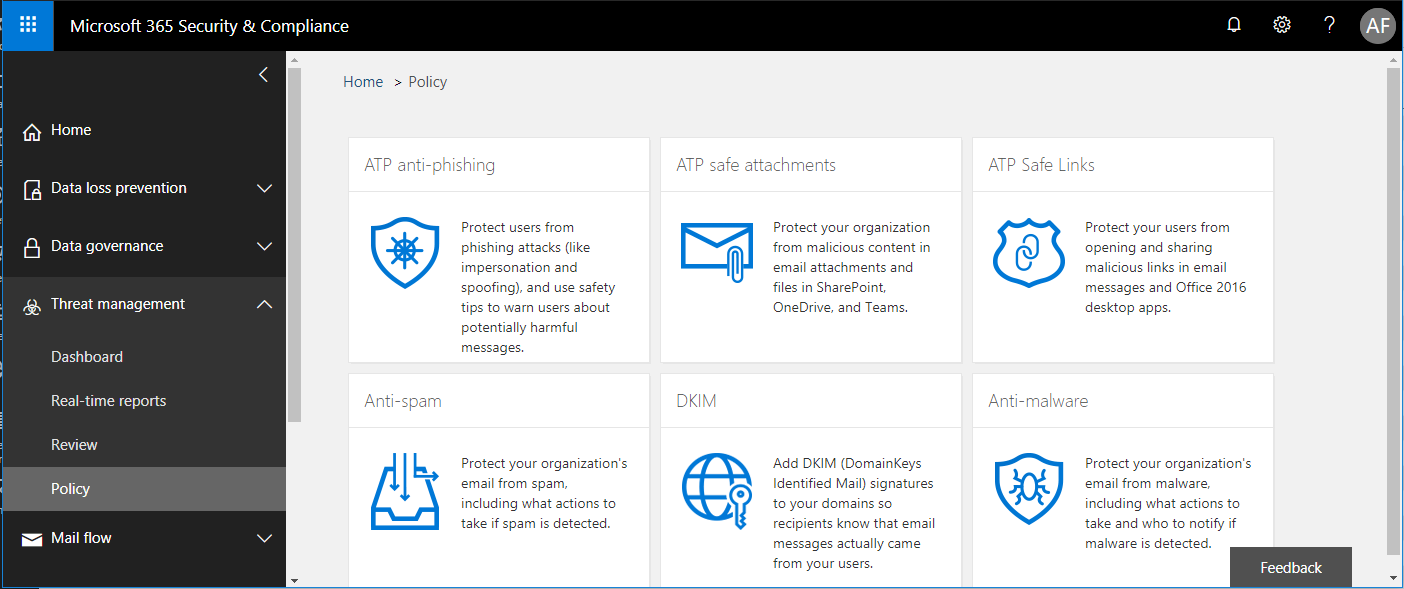
11. Advanced Threat Protection (ATP): This subscription is bundled with both Microsoft 365 Business and Enterprise E5 plans; it would be $2.00/user/month USD as an add-on to other plans. This is a nice toolset which allows us to apply advanced protections against zero day and spear-phishing attacks. For example, using machine learning to detect potential malware or other threats delivered via email web links and attachments, as well as some anti-phishing policies.
12. Backup: Technically this is not included with any Office 365 or Microsoft 365 plan. Office 365 is a robust service with highly available infrastructure and good up time. However, it is possible that any item which was deleted, either nefariously or via negligence, if not recovered within the retention period, can be lost forever. Having a third-party backup may be worth your consideration. In addition, with Exchange Online it is also possible to keep a Journal, or a copy of email messages, to another third-party location (often searchable and useful for legal and compliance reasons). To be clear, neither of these are subscriptions you would purchase from Microsoft, but rather from third parties.
Conclusion
Again, I am just highlighting some items that I have found to be rather accessible, and easy to implement. There is no such thing as a comprehensive or complete action plan when it comes to this security stuff. Many of these items will also help you to improve your Office 365 Secure Score, and there is no good reason not to start hitting up that list, to help protect your customers and/or internal end-users. Again, be sure to check it out at https://securescore.microsoft.com for a good breakdown of action items that you can take with your own tenant. You’ll find some of the items I mentioned here, and others–and of course, not every suggestion is right for every customer. Good luck to you out there!




Leave a Reply