Teams, SharePoint and OneDrive best practices? More like considerations… Part 1: External sharing and communication
This article is part of a series. Also see Part 2, Part 3.
Ever since I released the Office 365 Email Security Checklist, I have had a lot of people asking me for similar best practices checklists related to the “other” Office 365 services–especially Teams, SharePoint Online and OneDrive for Business.
The thing is, there are hardly any “best practices” which I would consider to be hard and fast rules when it comes to configuring these collaboration tools. Maybe there exist a handful of recommended settings for most organizations to adopt across the board, but they certainly wouldn’t be necessary or even appropriate for everyone.
Therefore, when you ask “What are the best practices for SharePoint?” it’s a little bit like asking, “What are the best practices for using Excel?” Everyone has different workflows with different processes they need to support, so it is very difficult to just lay down a blanket script or something that applies to everyone in every business.
Instead, this area of collaboration is your opportunity to add consulting value, whether you are an IT department serving end-users or an IT consultant serving other organizations. And that means while there is no real “best practice” here, the only way to execute a “wrong practice” is by NOT talking through the possibilities with actual stakeholders.
Let me give you a few examples, focused around security & compliance, to illustrate this further. Feel free to take this list and expand upon it in your own IT practice (or even add some other suggestions to the comments below)! I will cover these broad areas:
- Part 1: External sharing and chat communication
- Part 2: Access controls and notifications
- Part 3: Data retention, data classification, and DLP
Here is the TL; DR version in a simple table:
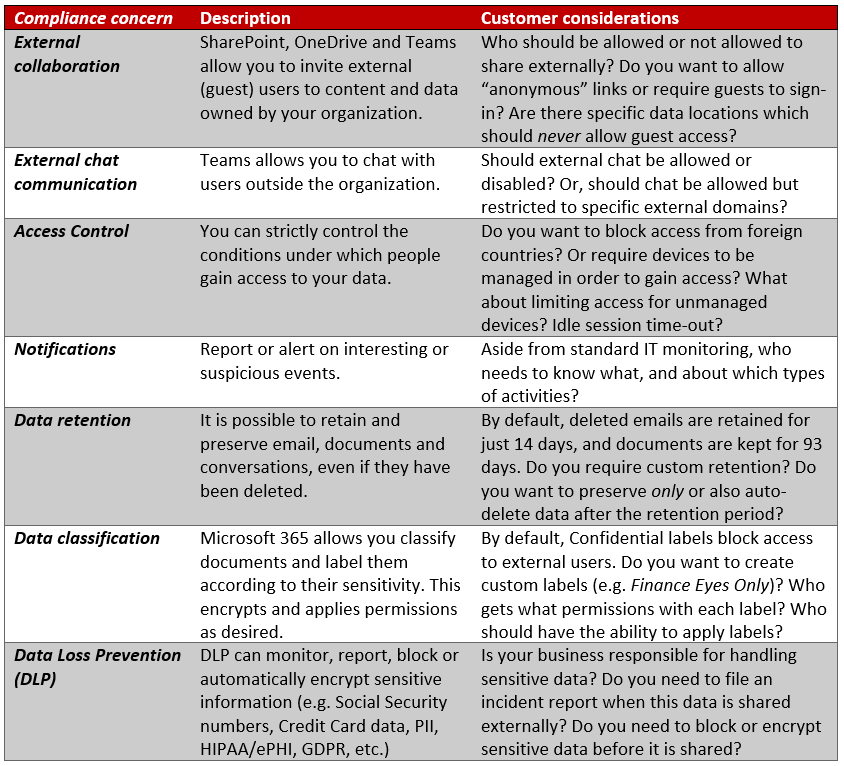
By the way, this list is by no means exhaustive, but you certainly wouldn’t want to leave any of these items out of the conversation. After all, these are big conversation starters! In a consulting engagement you might be invited to work on SharePoint for instance–various sites, lists, navigation, menus, metadata and more.
Now even though SharePoint is the launch pad for this engagement, you can quickly branch into other areas from there–and the above reference sheet is one way to do that. Then, as you gain trust and experience with the stakeholders, you might branch into other areas still–maybe Flow, if you’re tasked with workflow automation for instance. The opportunities are everywhere.
But these security & compliance pieces I have highlighted above are too often overlooked and shamefully, most stakeholders just never know that these controls are available to them. They just think that migration to Office 365 means moving email and documents into the cloud. To them it may be little more than a new container. What a shame! Therefore, I think that when people ask you about best practices as it relates to these “collaboration” tools, you should start here. And a world of opportunity will open up to you from there.
External sharing and collaboration settings
It is possible to invite external users to collaborate on content in OneDrive, Teams and SharePoint. Some organizations may want to limit or control this pretty strictly, for example if they work in a highly regulated industry like medical, government or military. But other organizations, such as non-profits who focus on community outreach programs and try to spread their content as far and as wide as possible, will likely want a very easy and open sharing environment.
As you will see, there really isn’t a “best practice”–but some settings will be better fits than others in different situations–and its up to you, the trusted technology adviser, to key in on the right match-up.
‘Global’ impact: Azure AD Admin center
There are several places to control external sharing settings. To impact sharing globally across all services, we can use the Azure AD Admin center, navigate to the Organizational relationships blade, and click on Settings.

Most of these same things can be controlled at the service level, for example within the SharePoint or OneDrive admin center. In general, it “could” be considered a best practice to leave sharing as open as possible in Azure AD, and manage permissions at the service level instead. But then again some highly regulated business admins may disagree with that approach.
My commentary on these settings are as follows:
- Guests can invite: Most SMB organizations are surprised to learn that guests can re-share content by default and many of them will ask for this option to be disabled–nevertheless I still plan to remove this item from my Azure AD Best practices checklist, simply because it is not a hard and fast rule
- Enable Email One-Time Passcode… this setting does make life easier for guests without a Microsoft account
SharePoint and OneDrive: Sharing settings
Whether you find these settings via the new SharePoint admin center, or the OneDrive for Business admin center, you’ll be looking at essentially the same options. From the SharePoint admin center > Policies > Sharing.

If your organization’s goal is to publish and spread its content freely, then the default options may work just fine. However, pay special attention to the “Anyone” setting. This means that users can send ‘anonymous’ links, which can be used to gain access to shared content, no matter who has the link.
Many organizations, especially those that work with sensitive data sets, will not necessarily want that capability turned on by default, so you can dial this option down to “New and existing guests” which means that users will not have the option to send anonymous links, and the people who receive links to shared content must therefore sign in.
It is worth mentioning here that you can make your OneDrive settings more restrictive than SharePoint Online, but not less restrictive. So sliding down the SharePoint selection, you will notice, also dials down the toggle for OneDrive, but the reverse is not true.
If you choose to keep anonymous links enabled, you should further consider whether you want those links to expire after a certain number of days (e.g. 7, 14, 30, or some other value). Scroll down to find the “Advanced settings for ‘Anyone’ links.” As well, you can decide whether these types of links will give others the ability to view only or also edit/upload changes.

And there are some other options, too. For example you can limit who has permissions to share externally to specific security groups.

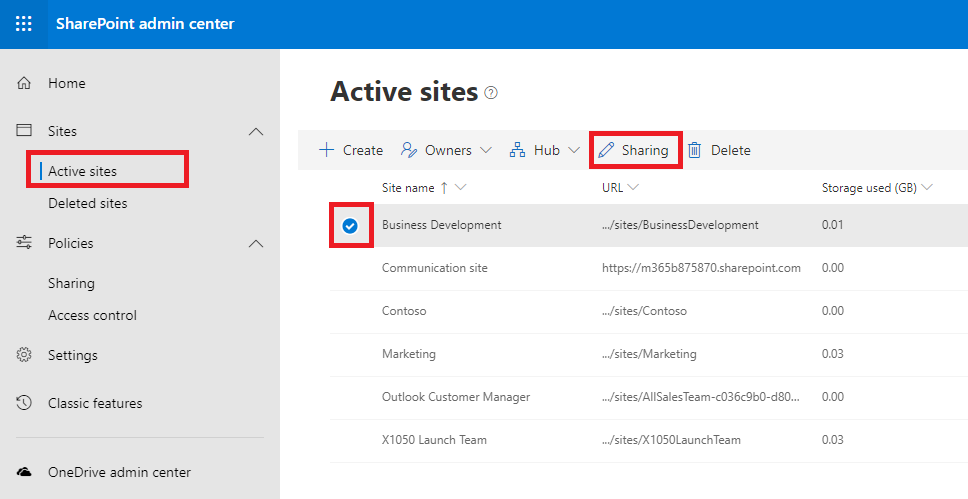
One more note re: SharePoint and OneDrive sharing: you can also manage these sharing settings at the site collection level (this is handy if there is a specific library or set of libraries that need to be more restricted than the service-level settings). Go to Active sites, pick one from the list and edit the Sharing settings from there.
Teams external chat and collaboration settings
Teams allows a couple of different scenarios with regard to external users. The first is related to chat only (not collaboration in a team); you will find the settings that control whether users are allowed to chat with external contacts in the Teams admin center under Org-wide settings > External access.

You can either allow all domains and block specific ones, or block all domains and allow specific ones. Or just turn it off completely. Note that (at the time of this writing) while Teams users can communicate with Skype for Business and Teams users in outside organizations, there does not yet exist a federation with Skype (consumer) accounts, like we had with Skype for Business.
To enable or disable Guest access within Teams channels, you would pick Org-wide settings > Guest access. Off by default, I find more orgs than not want this turned on. Once enabled, there are some other settings that light up which you can review.

It is also worth mentioning that creation of Private channels can be controlled as well.

Other Teams-specific collaboration settings and policies
And there are many other Teams-related settings, while not specific to external users, may also be worth looking at and discussing with your project stakeholders. Be sure to check out the policies and settings pages under Meetings, as well as Messaging policies and Teams apps > Policies.
For example, one very important decision for the organization to make is: Should we allow users to attach external storage locations like DropBox and others, or should we restrict sharing to native locations that we own and control?

For another example, check out Messaging policies. By default, owners cannot delete sent messages, but you may want that feature enabled for instance.

I won’t go through all of the settings in every policy here; the point is that every organization may want to make up different defaults, or apply different policies to different groups of people. It is worth your time to learn what the options are and then consult with your customers or project stakeholders about them.
Thanks for reading. In part 2 of this series we will cover access controls and notifications.



Comments (2)
Private channels already available? Maybe in preview still? I haven’t seen an official announcement ?
Yes, good catch–they are *almost* here.