How to enable auditing in Exchange Online
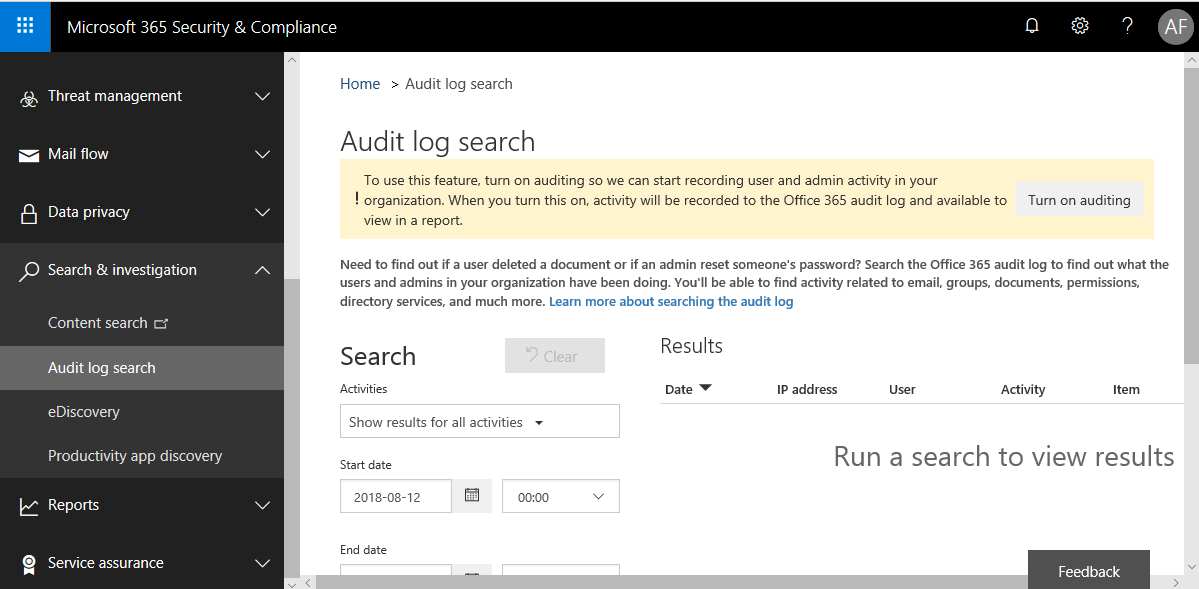
Microsoft 365 has a powerful Security & Compliance center that is becoming cooler every quarter that goes by. However, one rather important piece to understand is that auditing (logging of certain activities) is not turned on by default. They are in the process of updating this to be on by default, but for now it is still necessary to turn it on yourself. Find your way to the Security & Compliance center, and browse to Search & Investigation > Audit log search. Click Turn on auditing. If the link doesn’t exist, then your tenant most likely already has it enabled.
Update: Microsoft says mailbox auditing will be enabled by default in all tenants by the end of 2018.
You will notice that the informational banner at the top of this page will change to say that auditing will be available within “a couple of hours.” Note that it is also possible to turn this on using PowerShell in Exchange Online:
Enable-OrganizationCustomization Set-AdminAuditLogConfig -UnifiedAuditLogIngestionEnabled $true
But guess what? There is still more to it than that.
Enable mailbox auditing in Exchange Online
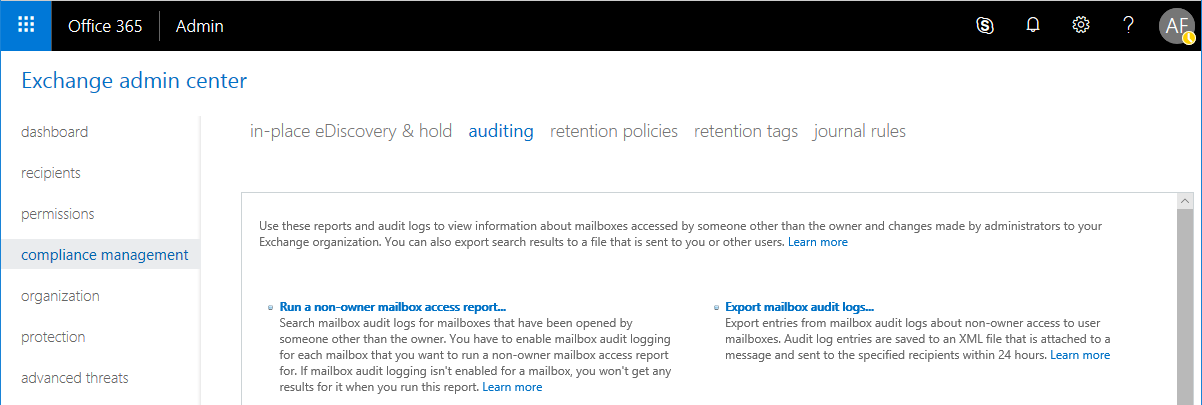
By default, Exchange Online does not have mailbox auditing enabled (and performing the steps above will not turn it on for you, either). For organizations that have to meet certain compliance requirements, this is a problem. If you go Exchange admin center > compliance management > auditing for example, expecting to review some of the handy reports–you might find yourself asking: “Why are all my reports empty?”
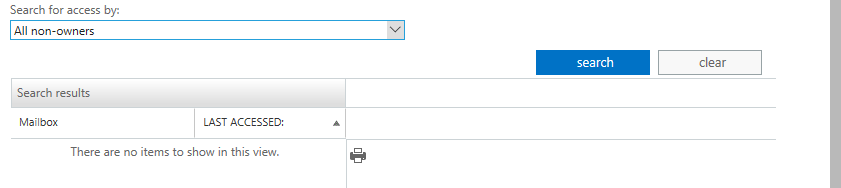
This looks handy: Run a non-owner mailbox access report…
There are no items to show in this view.
You: But my organization has lots of delegates and I know people are accessing each other’s mailboxes constantly… what gives?
If you want your reports to actually say something, you are going to have to enable mailbox auditing. Unfortunately, this cannot be accomplished in the GUI. Go get connected to Exchange Online using PowerShell. Once here, I like to run the Get-Mailbox cmdlet just to be sure I am in the right place (as a consultant I connect to a lot of tenancies in a given day). The first thing you need to do is turn mailbox auditing ON. You can (and probably should) do this for all your users in one fell swoop, like this:
Get-Mailbox -ResultSize Unlimited -Filter {RecipientTypeDetails -eq "UserMailbox"} | Set-Mailbox -AuditEnabled $true
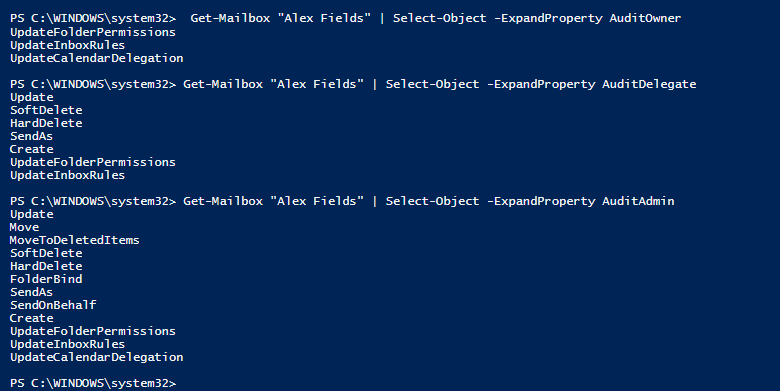
Great! All done, right? Sorry, no–or at least, probably not. There are three different types of users to consider when modifying audit settings: Owners, Delegates and Admins… and you may not like the audit actions that are selected by default for each of them. For example, by default, Exchange Online turns on almost nothing for auditing the actions taken by Owners. So in other words, if an owner does something–deletes an item for example–then it is not going to be logged by default. However, if that same person were to perform that same action on another user’s mailbox for whom they are a delegate, then it would be logged by default.
You can view what each of the defaults are at present, by running these commands (just choose one identity in your own organization to see an example):
Get-Mailbox "User Name" | Select-Object -ExpandProperty AuditOwner Get-Mailbox "User Name" | Select-Object -ExpandProperty AuditDelegate Get-Mailbox "User Name" | Select-Object -ExpandProperty AuditAdmin
I want to add at least a few to the AuditOwner category: MailboxLogin seems important, as do the deletions.
Get-Mailbox -ResultSize Unlimited -Filter {RecipientTypeDetails -eq "UserMailbox"} | Set-Mailbox -AuditOwner @{Add="MailboxLogin","HardDelete","SoftDelete","MoveToDeletedItems"}
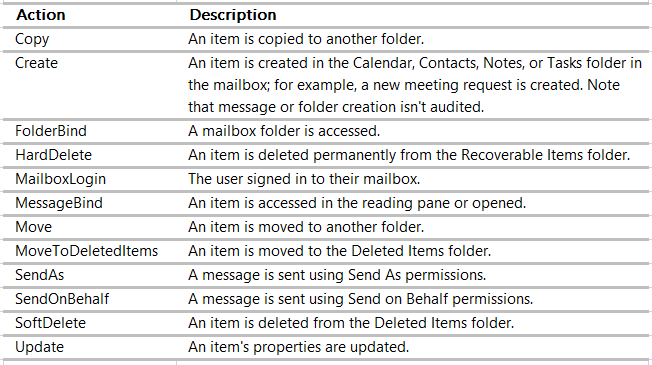
There we go, now these “Owner actions” will be logged: MailboxLogin, HardDelete, SoftDelete and MoveToDeletedItems. Review this table (copied from this source), in case you see any other adjustments you’d like to make:
That should about do it.
I have two additional caveats to share as regards the audit functionality in Microsoft 365 Security & Compliance Center. First: it can take time (30 minutes for some events, 24 hours for others) before the activity will actually show up in the various reports (Source). Second: Events are only retained for 90 days. If you need to be able to keep them for longer, then you will need to consider using a SIEM product that is compatible with Microsoft 365–one which can leverage its API for Management activity. This would allow you to pull data from 365 and retain it within your Security Information and Event Management software.


Comments (4)
Thanks for your great article.
I have one question. Is it also possible to log/audit actions performend on public folders? For example I want to log when an folder or an email in a public folder has been moved or deleted.
This might be the answer to your question…
Probably also a good idea to mention that you need to run this periodically to ensure any newly added mailboxes have your desired audit policies applied to them. Unfortunately there doesn’t appear to be a way to set a “default for new mailboxes” so this can be a one-and-done process.
So true, would love to see this feature added, so that the new user creation process can be simplified.