PSA: Go Setup Multifactor Authentication for Office 365
Microsoft reported recently that they have seen a 300% increase in identity-based attacks within the last year. I know, I know–you are one of those people who NEVER get duped into clicking on bad links, or giving up credentials or other personal information, right?
“But I am too smart to get duped by the bad guys!”
–You
Yet I’ve seen very smart people end up in this exact scenario. The accounts subsequently get abused or leveraged for nefarious purposes (most often financially driven). Therefore, it is a good reminder to all of us that Office 365 subscriptions include Multifactor Authentication (MFA)–but it is not on by default.*
Getting this setup is highly recommended–these days, everyone should be considering a second factor to protect their logins. And, since it is already included in your subscription at no extra charge, you really have no excuse. So go get this set this up for yourself, and your users–it’s worth it.
*As a matter of fact, MFA will soon be mandatory for all admin level accounts–meaning MFA will be required by default if you are an administrator, unless you specifically opt out of the policy in advance. More on this later.
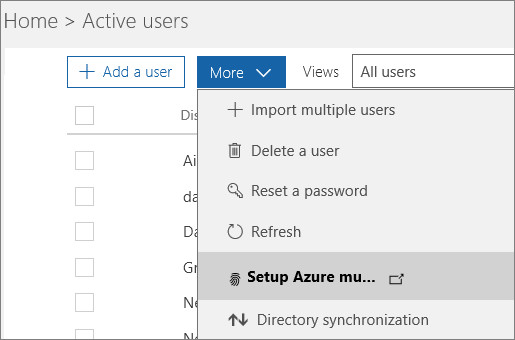
Quick setup steps
Go to the Office 365 Admin Center, and navigate to Users > Active users. Find More > Setup Azure multi-factor…
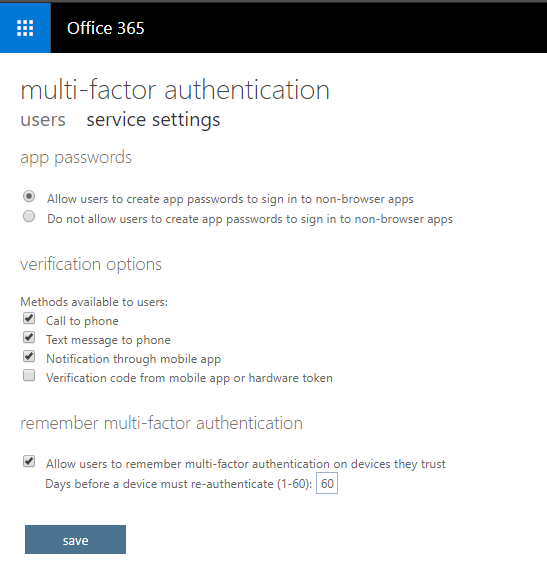
Configure app passwords and other settings
You can see your users listed here, but before you enable MFA for anyone in particular, check out the service settings area.
Here you can select various options surrounding the use of MFA. For example, allow certain types of MFA challenge such as phone calls, SMS, mobile app notifications, or hardware tokens. It is also where you allow or disallow users to generate app passwords (for applications that do not support a second factor prompt–e.g. older versions of Office apps, Apple Mail, etc.).
Note: I find the mobile app notification option is usually the best user experience.
Now, regarding app passwords, if your users have the latest and greatest Office 2016 apps via their subscription, they should not be required to use an app password for example, in Outlook. But in order for this to work properly, you need to check out one little setting via PowerShell in Exchange Online. Something called Active Directory Authentication Library (ADAL) must be enabled for your tenant.
Connect to Exchange Online PowerShell and run the following command to check the status: Get-OrganizationConfig | Format-Table name, *OAuth*
If you need to enable ADAL, run this command: Set-OrganizationConfig -OAuth2ClientProfileEnabled:$true
Enable your users for MFA
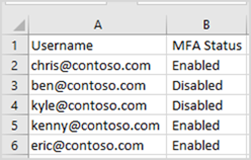
Simply select as many (or all) of the users, and choose Enable on the right. You also have the option to use the bulk update button at the top of this page, and provide a CSV file which is formatted as follows:
You may also notice that when you choose one or more of the users from this area, you also have an option to Manage user settings. You get these options, which are self-explanatory:
- Require selected users to provide contact methods again
- Delete all existing app passwords generated by the selected users
- Restore multi-factor authentication on all remembered devices
Instructions for end users
Communicate the change in advance to your end users. You can provide them with links to the Microsoft support literature on this, also:
Referring to the official support articles might be the easiest (vs. creating your own documentation), since Microsoft changes things every so often, anyway.
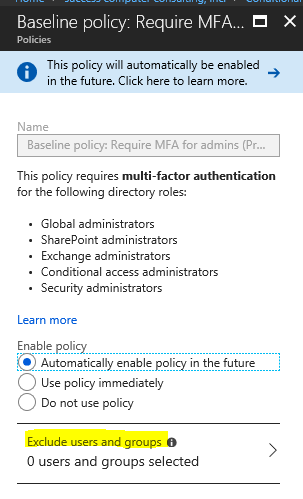
Admin accounts and the new conditional access policy
As mentioned, Microsoft is turning on a new policy (still in preview right now but will be enforced as it goes to General Availability). If you navigate to the Azure portal, find Azure Active Directory > Conditional Access (under the Security section). Here you can set your preference on this rule pertaining to administrative accounts. It is indeed possible to opt out, however there are some gotchas–although it would be better to remain enrolled for MFA, there are certain “shared” administrative accounts where this would not be an option.
Note: if you are going to exclude users (e.g. shared admin accounts or accounts for vendors where more than one person could be accessing the account), then you should treat these administrative accounts very differently than normal accounts:
- they should not be used for anything other than administrative tasks
- use a cloud-only ID with logon suffix such as “@tenant.onmicrosoft.com” rather than your vanity domain name, or some AD-Synced account
- change the password at least every 90 days, and/or after administrative users leave or are terminated
- regularly review the Risky sign-ins report in Azure AD for anomalies
- consider Azure AD Premium or EMS subscription to enable alerting and policy-based actions with Identity Protection
Here are Microsoft’s notes on this scenario, for further reference.
And one more thing which is of utmost importance: if you enable this on an administrator account, you have a whole new process for connecting to Exchange Online via PowerShell for management–the old method isn’t going to work.
Conclusions
This doesn’t take terribly long to setup, but it goes a long way–this is the best security feature that is included out of the box with Office 365, bar none. Of the dozen email breach events that I have seen happen this year so far, MFA would have prevented nearly all of them. So go set it up today–particularly for higher risk users like those in finance, C-level management or IT administration.




Leave a Reply