Navigating Device management in Microsoft 365: Registered vs. Joined vs. Hybrid Joined… and Intune
Device management is not a straightforward thing in Azure AD. I think that one major point of confusion for people is understanding the difference between various device states–for example, what is the difference between a device which is merely registered with Azure AD, versus one that is actually Azure AD joined? And what about Hybrid Azure AD joined?
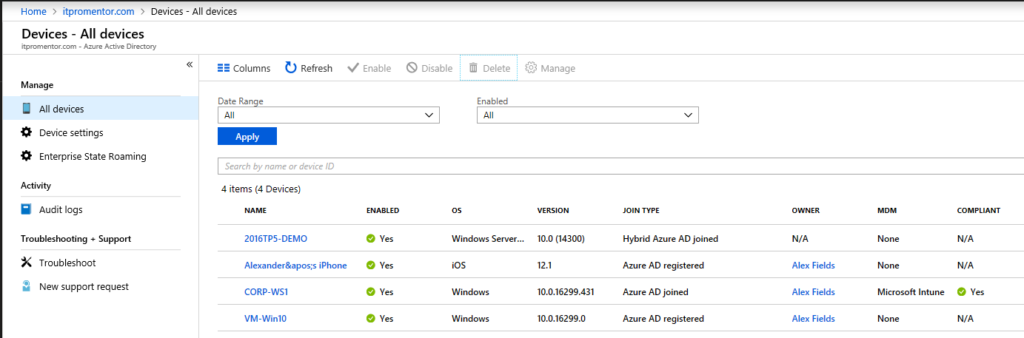
I will describe them all here in order from weakest to greatest level of association/control. First, take a look at all the different types in the Azure AD portal, under Devices > All devices.
You will see some devices listed as Azure AD registered, while other say Azure AD joined or even Hybrid Azure AD joined. On top of that, there may be some managed by Intune MDM, and others which aren’t. But fear not–it will all make sense shortly.
Azure AD Registered
This is a weak association (but an association nonetheless), and basically it just means that the device exists, and is accessing Azure AD-based resources (such as Office 365). This join type can apply to any device–Windows, macOS or mobile devices such as iOS or Android.
Registering is meant for “BYOD” scenarios and does not give admins much control over the devices themselves. We do however have the ability to report on these devices for inventory purposes, and to Disable or Delete the devices from Azure AD. And if you care about security at all, then you should regularly prune inactive devices as a best practice.
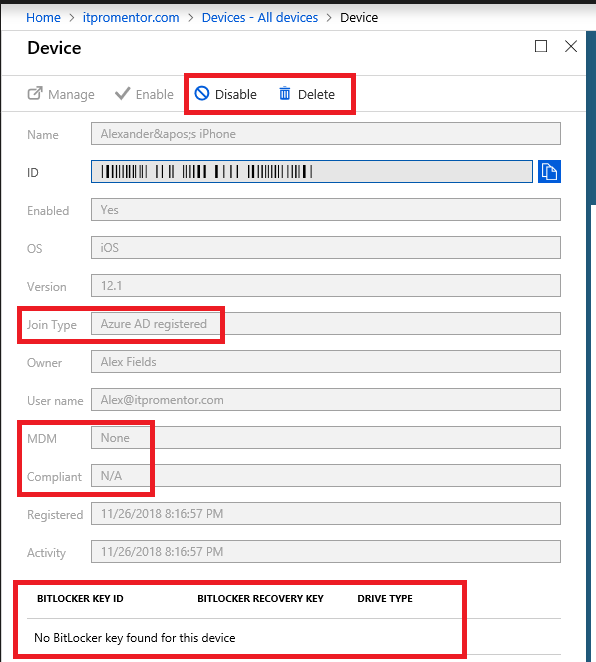
Notice in the screenshot above that the device Join Type is listed as Azure AD registered, and our available controls for this device are just Disable and Delete. Additionally, there is no MDM enrollment for this device, and no BitLocker keys. Know that it is also possible to have the device registered, and enrolled in MDM, but in this case the device is not enrolled for MDM.
NOTE: Exchange ActiveSync devices will not show up in your Azure AD device inventory by default–so those devices would need to be managed via Exchange Admin Center or PowerShell via Exchange Online. However, if stronger security is your goal, you could configure a Conditional Access policy (via Enterprise Mobility + Security) to require devices to establish a stronger connection to Azure AD and enroll with Intune, before granting them access to resources such as Exchange Online or SharePoint Online, for instance. With this setup, Exchange ActiveSync clients would also show up in your inventory.
Azure AD Joined
Joining is just an extension of registering the device. They are nearly the same thing, except that in addition to receiving an identity in Azure that can be disabled/deleted, joining also changes the local state of the device, such that it is possible to sign-in to the device using Azure AD credentials. This join type only applies to Windows devices–it is possible for them to join Azure AD instead of joining a local Active Directory. This can be accomplished in several ways.
From the OOBE or “first run” experience in Windows 10, a user can choose to sign-in using their Work or School account, and when they do, the device is thereby joined to Azure AD. Or, you can configure this option from another, local admin account on the device if it is setup at a later time, after OOBE. Navigate to Settings > Accounts > Access work or school. Click on Connect.
Do NOT simply fill in your work identity and click Next on this screen. That would have the effect of registering the device against Azure AD, only. Instead, you will choose Join this device to Azure Active Directory under Alternate actions. If you don’t see this option, make sure you have the 2017 Fall Creator’s Update, and that you are not joined to an on-premises Active Directory already.
For the Enterprise who needs to provision many devices quickly, we also have a bulk option, and Windows 10 Autopilot.
The benefits of joining Azure AD are that you will be able to sign into the device directly using your Azure AD / Office 365 credentials, and thereby enjoy Single Sign-On to all of your cloud-based resources. Additionally with Windows 10 you get access to Enterprise State Roaming (sync user settings across devices), Windows Hello support, and other enhancements–for example, it is also possible to store your BitLocker keys in Azure AD, and later retrieve them online using your account, if needed. Otherwise, the main administrative controls pretty much remain disable or delete the device.
In the above screenshot, we see that the Join Type is Azure AD joined. We can still Disable or Delete this device, but notice how we can also store and retrieve our BitLocker Key. In this case, we are also not enrolled in MDM. It is possible to layer MDM on top of this, as always. When we do, the Manage option will light up for us, as we will see.
A device that is Azure AD Joined is one which is “cloud-first” or “cloud-only”–meaning that these users would primarily do their transacting on cloud-based applications such as Office 365, and other SaaS apps. It is also supported to have purely Azure AD Joined devices in a hybrid environment–for example for users who are hardly ever in the corporate offices, and rarely connect to the premises-based corporate infrastructure–this is a fantastic option to use. And when they have line of sight to a local DC, they can still enjoy single sign-on to the corporate domain.
Hybrid Azure AD Joined
Microsoft 365 Business and Enterprise editions all support the ability to “Hybrid Join” devices–meaning that Windows 10 PC’s can join a traditional Active Directory as well as Azure AD. This can be accomplished individually on each PC, in a manual fashion, or by using Azure AD Connect to sync your on-premises Active Directory joined devices to Azure AD. You will enjoy the same SSO benefits with this setup. Although the end users are still signing into the local AD domain on their device, having it Hybrid-Joined will also sign them into Azure AD simultaneously–thereby granting the benefits listed above.
The way this happens manually is the same steps you would take to register a device against Azure AD. If the local domain user account is synced to Azure AD, then registering the device with Azure AD can be accomplished easily on top of this–and that makes it “Hybrid Azure AD joined.” That is to say, a properly joined device on-premises will yield a properly joined device in Azure AD (and of course, with Azure AD Connect properly configured).
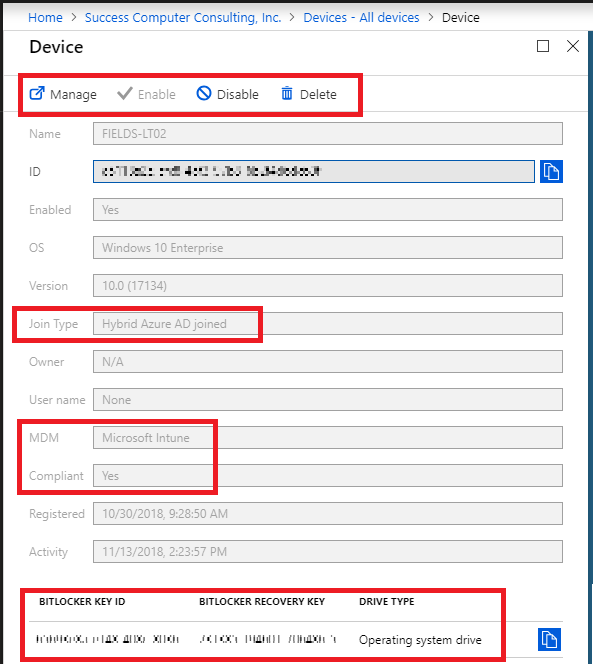
Take a look at the device in the below screenshot. Here, the Join Type is Hybrid Azure AD joined, and in addition to that, we are managing the device with Microsoft Intune. Note that it is also possible to have a hybrid-joined device that is not managed via MDM. This one happens to be. You will notice also that we have the Manage option in this case (this is because the device is managed by Intune–and that happens to be a link out to the Intune portal). And of course, we have the BitLocker keys available again, as we did above.
Intune (MDM)
The ideal scenario for maximum security and leverage over your devices is to register or join Azure AD and to have the device enrolled for MDM via Intune. So an important point here is that any type of device listed above–whether registered, joined or hybrid-joined–will receive additional attributes within Azure AD once they are enrolled with Intune. And you will have more capabilities to boot!
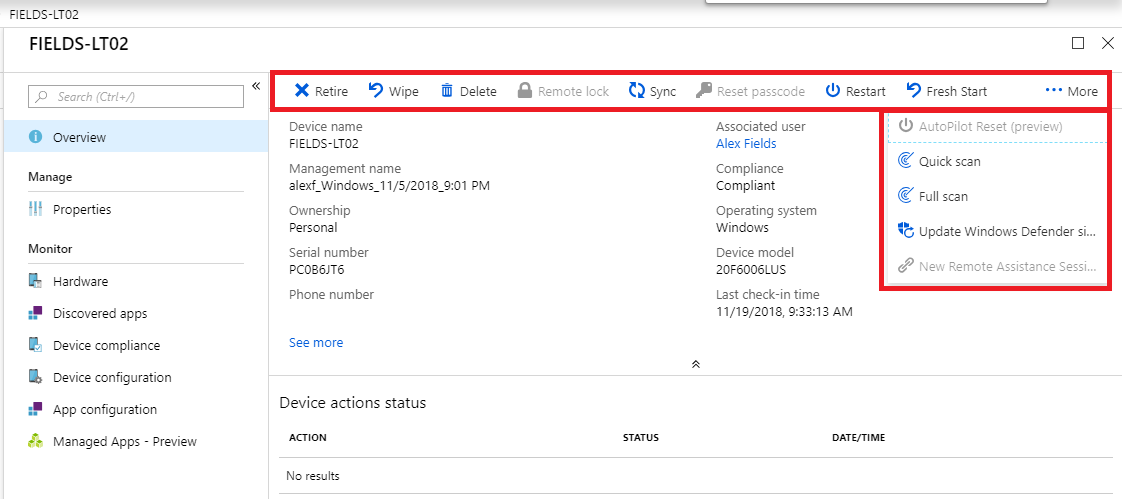
In that example above, when we follow the link to Manage, we are brought over to the Intune console to manage the device. Just look at all the new options we have available! Perhaps most notably: Wipe. Since this is a Windows 10 device, there are also Windows Defender controls and some other goodies under the ellipses (More)–so don’t miss those, either!
The primary benefits to enrolling in Intune, is that you will gain much greater control over the device. With Intune, it is possible to:
- Wipe the device remotely (most commonly requested feature)
- Push certain policies, profiles and controls to the device
- Manage and push applications
- Enforce Conditional Access (with Azure AD Premium/EMS)
- And more
If you already setup your device policies when establishing your Microsoft 365 subscription, then any Windows 10 device that subsequently joins Azure AD will also become enrolled into Intune MDM automatically. The Windows 10 device policies you define should be applied upon joining.
For mobile devices, you would need to configure additional policies, and then enroll devices using the Intune app that you can get from the app store, which steps you through the enrollment process. When you have an appropriately configured Conditional access policy alongside of Intune, you will be directed to do exactly that (depicted below), if you were to attempt to configure an email profile, for instance. A fair warning: there are quite a few screens to step through to complete this process. The trade-off is you get maximum visibility and control of all the devices in your environment.
In conclusion…
I hope this has cleared up some of the confusion around the device management options within Azure AD. Let me know if there is anything else you’d like clarity on in the comments.







Comments (6)
As always, excellent and very useful information! Thank you!
nice and useful article. helped me a lot in understanding the difference. thank you
Great write up on Azure AD device state. Still unclear on one thing. If I go down the road of Hybrid Azure AD Join, does that change the logon state for the users? Will it change how they log onto their on-premises domain joined computers?
Thanks.
Dave L.
No. Hybrid join = domain join + azure ad registered
I’m in a interesting situation where I have machines in Azure AD in the Azure AD Registered state but recently configured for Hybrid Azure AD. How can I transition these to HAADJ but retain the bitlocker keys associated with the AADR machines? MS Documentation says that with Windows 10 v1803 machines and up, the duplicates are automatically removed. How long does this process take? What happens to those bitlocker keys?
You should be able to complete the steps to setup Hybrid Azure AD Join. See this article: https://docs.microsoft.com/en-us/microsoft-365/business/manage-windows-devices