Implementing the ACSC Essential 8 with Microsoft 365
I have had this request on my backburner for a while, and I finally got around to knocking it out: from a reader in the Land Down Under–Australia!
Update: Microsoft has a much-improved set of Learn articles on the Essential Eight, with detailed guidance on implementing the three Maturity Levels (MLs) for each of the Essential Eight security controls.
Have a look at these resources if you are looking for the “most bang for your security buck” so to speak.
Background
The Australia Cyber Security Center (ACSC) published Strategies to Mitigate Cyber Security Incidents some years back. The most effective of these strategies were identified as the “Essential 8” (last updated April 2020 at the time of this writing). These have a lot of visibility in Australia, and other organizations around the world have picked them up as well–they act as a sort of “baseline” or reference point for cyber incident mitigation efforts.
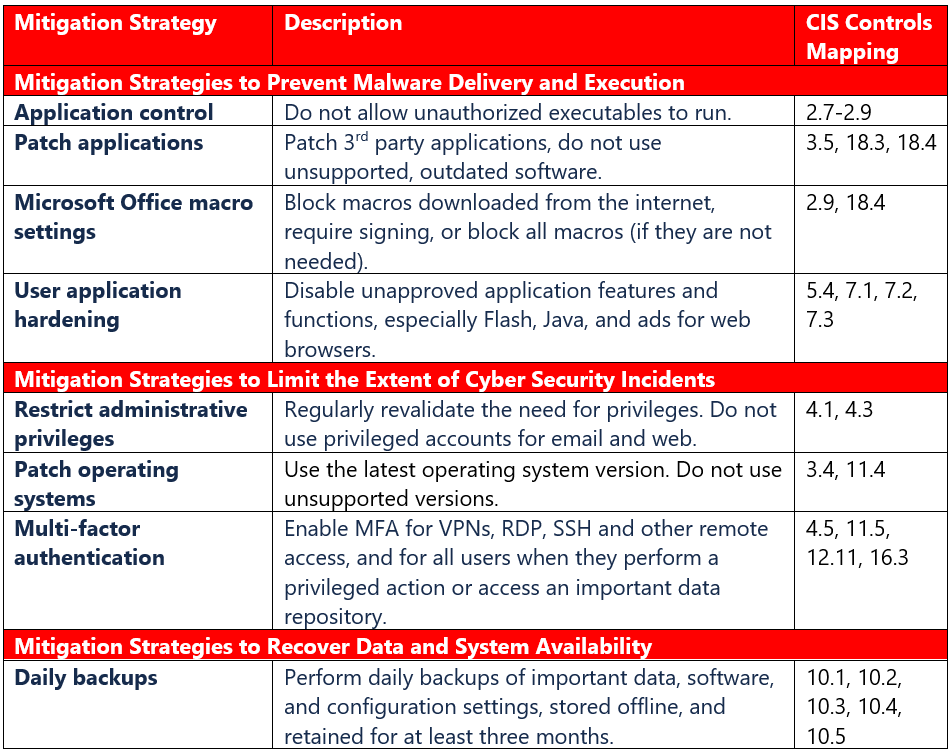
Above, I have mapped these to the CIS Controls so that you can see how implementing this list will also help you to meet (at least partially) specific sub-controls in other cyber security frameworks; or said another way: these are the CIS sub-controls you would focus on to move the needle on the Essential 8.
Even though it overlaps with areas in CIS, it is not a complete cyber security strategy on its own—remember that if you fail to meet the Basic CIS Controls up to at least the Implementation Group 1 maturity level, then other mitigation strategies may be undermined (for instance, without an accurate hardware and software inventory up front you cannot implement these strategies effectively across all of your systems). Yet, the Essential 8 can be seen as another way of prioritizing your risk reduction backlog.
No Detection Strategies?!
I was also initially surprised that none of the ACSC’s Mitigation Strategies to Detect Cyber Security Incidents and Respond made it into the Essentials list. I suspect this is due to the additional expense and pre-requirement for on-going monitoring and human labor—which many small and mid-sized organizations simply have not had access to historically. I believe this should change within the next couple of years with more MSP’s offering services focused around cybersecurity, including Incident Response. In any case, note that the Essentials as they stand today tend to focus primarily on Protect, rather than Detect and Respond.
Nevertheless, detection and response is going to be a very important area for you to focus on as a service provider—so do not lose sight of it!


Comments (5)
I’ve had a lot of discussion about whether it necessary to do an external backup of Office 365, at least one Aus gov department has decided that the redundancy provisions and retention capability in the E5 license is enough. I have since heard (from a backup vendor) that this would not meet Essential 8 requirements, but I can’t find a definitive statement one way or the other.
What would your take on this position?
Cheers,
Stuart
The fact is that no backup vendor out there can truly back up everything in Office 365. Ask them if they backup flows, or planner, or forms, or any app other than mailboxes, onedrive accounts and sharepoint sites. The answer is always no. So you can protect your email and file data in the MSFT cloud natively using stuff like Retention policies, labels, litigation hold, etc. OneDrive even has a restore feature which is great for ransomware situations. It would be nice if we had that same feature on all data locations, but for now just OneDrive. To do a restore of deleted data is not super easy but it can be done provided you have the proper protections in place. The real benefit of a third party is: how easy and painless can they make the restore process?
As for whether it “meets the requirements” I think this is a dubious statement. What precisely does the native protection option fail on? Here in the US, in Exchange Online at least we know that their solution meets SEC 17a-4 which means there is separate storage isolated from the primary storage, and you cannot alter the secondary storage. I am unsure whether they are meeting that requirement for SharePoint yet. So that is one possible area for clarification.
Might be a good time to run an update on this article. Not sure whether E8 Maturity Levels were in place when you did the initial post but ML3 in particular describes monitoring relevant event logs and taking action for most categories, which meets the “Detect” and “Respond” at very high level. I have to agree that the primary emphasis is definitely still Protect though.
Do you have any updates for this for 2023 Essential 8 Compliance?
Some of the links are broken as the ACSC likes to move things around.
Some elements of E8 have changed since the time of this being written.
Older article, true. Will be doing a course on E8 soon–early next year. Will likely announce it on the blog and update this post to point to it as well when it is ready.