Managed Services Providers Are Doing IT All Wrong
As a Microsoft MVP and frequent community contributor, I have been invited to participate as a “subject matter expert” in several groups and online communities. Since I also work for an IT Managed Services Provider, some of these invites have brought me into peer groups comprised of folks who own IT Managed Services companies.
Aside: I know a large portion of my readership either works for or owns IT consulting companies, and of course there are others here who work in different areas of the IT industry. But I think the content of this article will be interesting to everyone.
During my time interacting with these peer groups, I was shocked to learn how many of the MSPs out there seemed to lack basic cybersecurity practices and hygiene. As well, in 2019 and 2020 we have seen a barrage of news reports about MSPs who have been breached (and usually ransomed along with their customers). It makes sense—after all an MSP holds the keys to every customer’s Digital Kingdom. We manage servers, networks, cloud services, and even endpoints with our tools and software. One-stop shopping for cyber criminals!
So why are MSPs doing such a poor job with cybersecurity and ending up in the news over and over again? Cybersecurity should be a #1 priority for them, don’t you think? I started asking around in these groups about why people are not taking cybersecurity more seriously. The responses I got to this question were alarming.
- Some have argued that cybersecurity is “too expensive” for the typical SMB customer, or that their customers “won’t let them” spend the extra dough it takes to “get secure.”
- Others claimed that there is no point trying to stay ahead of the attackers, and that it is “better by far” to focus on just two things: “good backups and cyber insurance.”
- I even had one person reply that formal cybersecurity practices/service is not needed in the SMB space; they already do “everything necessary” for their customers. You know: antivirus, updates, and firewalls—what more could you ask for?
As if the news reports, together with the scattered responses I was getting back in these public forums was not enough evidence to show that we are simply misaligned on this issue as an industry, I decided to get a little bit more concrete. So, to make my point, I sent out a quick cybersecurity survey to some of these groups. To develop my questions, I simply referred to the first few Critical Security Controls published by the Center for Internet Security (CIS).
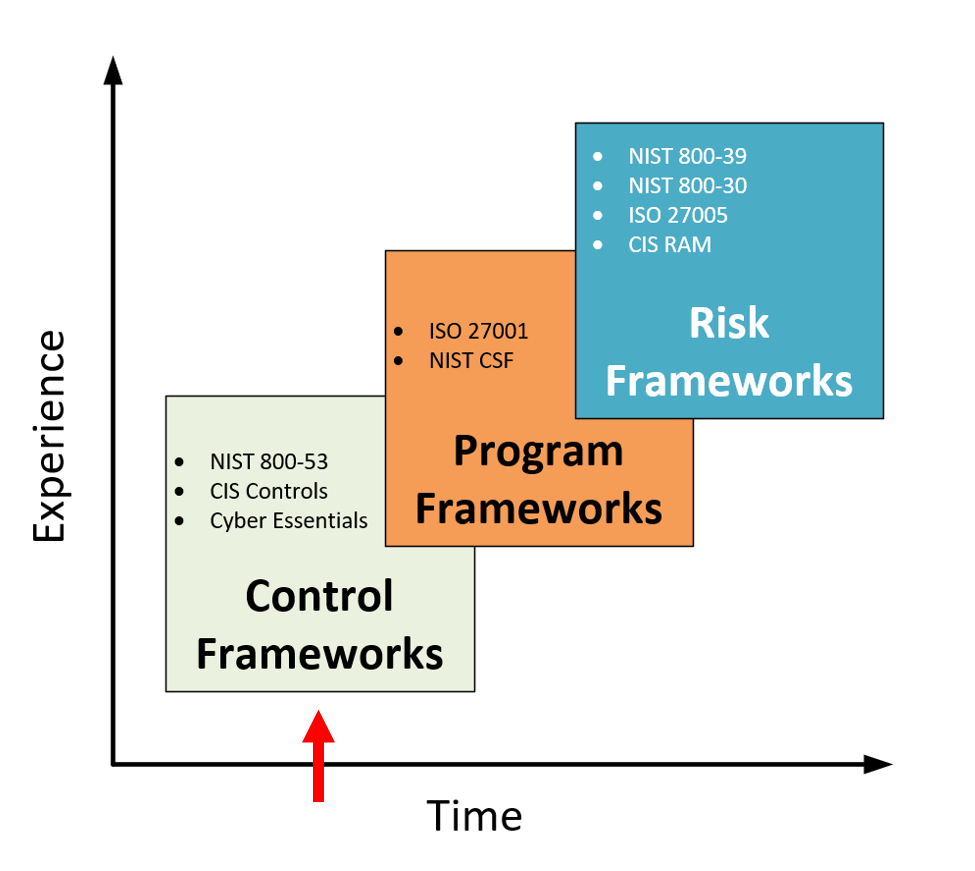
Now the CIS Controls is a “simplified” cybersecurity framework, known as a Control framework—this is much easier and quicker for organizations to implement than a formal Program framework such as the entire Cybersecurity Framework from the National Institute of Standards and Technology (NIST). The CIS Framework has collected the top 20 “Critical Security Controls,” derived in part from NIST, and in part based on real-world attacks, such as those cataloged in the annual Data Breach Incident Report from Verizon. The controls in this framework were selected as the “most critical” to implement precisely because they are so effective at mitigating real-world cybersecurity incidents that organizations experience every day, such as ransomware.
Note that many of my writings on ITProMentor.com, as well as my publications on GumRoad and my courses at Teachable, are focused on applying these same cybersecurity best practices–usually with the help of Microsoft 365.* This is also the topic of my presentation this year at Microsoft Ignite (which has gone virtual due to COVID). I’ll put the link to that session up once the Ignite content goes live. So if you already follow my materials, then you will be aligning pretty well with the CIS.
Now instead of asking about every single control in the framework, I decided to focus on the first six controls (CSC #1-6), which the CIS refers to as the Basic controls—so called because if you fail to implement these six things well, then any subsequent efforts at cybersecurity could be undermined (by the fact that you did not prepare a good foundation). In other words, you could skip ahead to apply later controls such as Information Protection (CSC #13), Multi-Factor Authentication (CSC #16), and Security Awareness Training (CSC #17), but without the basic controls in place, you’re still stuck with Swiss Cheese Security—and that means open season for the bad guys.
So I wanted to find out whether the orgs I was polling implemented any of these top six controls—and if they did not, then we can reasonably assume that it does not matter what else they are doing right (so I am purposefully not asking them about Multi-Factor Authentication or other commonly known cybersecurity best practices). Let us take a look at some of the data from my poll results.
Summary of Results
CSC #1: Inventory & Control of Hardware Assets
Do you take actions today on a regular basis to positively identify both authorized and unauthorized devices that are accessing company apps and data?
- No: 39%
- Yes, for my org only: 9%
- Yes, for my org and some customers: 40%
- Yes, for my org and all of my customers: 9%
- Yes, for some customers, but not my own org: 3%
- Yes, for all customers, but not my own org: 0%
Do you take actions today to prevent unauthorized devices from connecting to corporate apps and data? (e.g. Device-based Conditional Access)
- No: 33%
- Yes, for my org only: 11%
- Yes, for my org and some customers: 40%
- Yes, for my org and all my customers: 9%
- Yes, for some customers but not my own org: 7%
- Yes, for all customers, but not my own org: 0%
CSC #2: Inventory & Control of Software Assets
Do you take actions today on a regular basis to positively identify applications in the environment that serve a business purpose, as well as those which do not serve a business purpose?
- No: 48%
- Yes, for my org only: 14%
- Yes, for my org and some customers: 24%
- Yes, for my org and all my customers: 9%
- Yes, for some customers, but not my own org: 2%
- Yes, for all customers, but not my own org: 2%
Do you take actions today to prevent unauthorized applications from executing in the environment (i.e. Application Control)?
- No: 71%
- Yes, for my org only: 2%
- Yes, for my org and some customers: 19%
- Yes, for my org and all my customers: 4%
- Yes, for some customers, but not my own org: 4%
- Yes, for all customers, but not my own org: 0%
CSC #3: Continuous Vulnerability Management
On a regular basis, do you perform vulnerability scans to identify vulnerabilities on devices that participate in the corporate infrastructure, or that have the potential to access corporate infrastructure, apps, and data, whether connected to the network or not? Select all that apply.
- None: 40%
- External vulnerability scans: 36%
- Internal vulnerability scans (LAN): 38%
- Endpoint vulnerabilities (whether on LAN or no): 38%
- Selections above apply to my own org: 33%
- Selections above apply to some of my customers: 36%
- Selections above apply to all of my customers: 12%
CSC #4: Controlled Use of Administrative Privileges
Do you monitor administrative roles and alert on new accounts or services that have the potential to cause system-wide changes?
- No: 40%
- Yes, for my org only: 7%
- Yes, for my org and some customers: 43%
- Yes, for my org and all my customers: 10%
- Yes, for some customers, but not my own org: 0%
- Yes, for all customers, but not my own org: 0%
Today, do you limit the ability for end-users to install applications and make other system changes on their devices by removing local administrator rights?
- No: 26%
- Yes, for my org only, and only for some users: 7%
- Yes, for my org only, for all users: 0%
- Yes, for my org and some customers, only some users: 24%
- Yes, for my org and some customers, all users: 20%
- Yes, for my org and all my customers, only some users: 5%
- Yes, for my org and all my customers, all users: 7%
- Yes, for some customers but not my own org, some users: 10%
- Yes, for some customers, but not my own org, all users: 2%
CSC #5: Secure Configuration of Hardware and Software
Do you have a documented configuration standard (i.e. baseline) defined for any of the following? Select all that apply.
- None: 14%
- Firewall: 55%
- Switches: 40%
- Wireless Access Points: 38%
- Servers: 43%
- Workstations: 48%
- Mobile devices: 28%
- Other network devices/printers/peripherals: 14%
- Selections above apply to my own organization: 40%
- Selections above apply to some of my customers: 33%
- Selections above apply to all of my customers: 26%
Do you monitor for configuration drift or departure from any of your security configuration baselines?
- No: 64%
- Yes, for my org only: 7%
- Yes, for my org and some customers: 20%
- Yes, for my org and all my customers: 7%
- Yes, for some customers, but not my own org: 0%
- Yes, for all customers, but not my own org: 2%
CSC #6: Maintenance, Monitoring and Analysis of Audit Logs
Do you audit security events and monitor your event logs for suspicious and abnormal activity? Select all that apply.
- No: 38%
- Yes, for my LAN and/or servers: 31%
- Yes, for cloud-based identities: 26%
- Yes, for Office 365 cloud apps: 50%
- Yes, for other cloud apps such as DropBox, GSuite, Salesforce, etc.: 5%
- Yes, for endpoints: 17%
- My selections above apply to my own org: 31%
- My selections above apply to some of my customers: 29%
- My selections above apply to all of my customers: 14%
Analysis
In an upcoming post, I will share some additional commentary on these responses individually. But the bottom line here is that on average we are seeing nearly half of respondents admit that they do not implement these basic controls at all—for themselves or their customers. Now that on its own is very concerning. But what is even worse is that the number of respondents who apply these controls consistently across their own environments and all customers is vanishingly low: about 10% on average. While some providers are taking a (presumably) more deliberate approach to cybersecurity, they are still positioning these practices as “add-ons” or premium offerings—so only some customers receive what is considered in the industry to be very basic cybersecurity hygiene.
I am sorry, but I have to call you out here, fellow MSPs: the basics should not be considered a premium offering. Cybersecurity is not a “nice to have”—it is just part of doing business in the 21st century. Therefore, when you say things like, “Customers won’t spend the money,” you have already misunderstood your role here. While it is true that you can always find ways to spend more money on security, there is a certain amount of basic hygiene that you are responsible for pushing and maintaining regardless of what other budgetary choices are made. You need to build basic cybersecurity best practices into the DNA of your normal service offerings, or you are doing it wrong.
This is about good management more than anything (better management results in better security automatically). Put another way, if you were starting an MSP today, then I would NOT follow the crowd and do all of the other things they are doing. I would start here instead, and make sure you’re doing the things we just went over, first. Add services from there, but this is the foundation.
If you are already a Managed Services Provider and need some help understanding where and how to get started on this important task, then check out the many resources I make available on this blog, plus, I have a course on Cybersecurity Best Practices for the MSP, on Teachable, which follows the CIS Controls and NIST. All of my publications and projects are updated regularly, and all participating community members have access to future updates for life! As well, you are welcome to contribute any feedback, which helps to steer the direction of the content that you find most helpful, and keep the community in touch.
If you just want to stick to free resources I can appreciate that, and I can wholeheartedly recommend these places to start:
- Critical Security Controls from the CIS (they have a free PDF download)
- Australian Essential Eight (see my commentary and guide also)
- NIST Cybersecurity Framework (plan to have at least a cursory understanding of the five functions, but again, remember that the CIS has prioritized the category/sub-category selection for you).





Comments (5)
The results are worrying but unfortunately expected based on what I’ve experienced and seen in online groups :-(
Do you have detals on your ignite session? I don’t see it in the session catalogue (yet?)
It is up, also on TechCommunity embedded in this post: https://aka.ms/cis4m365
Great article Alex! looking forward to your Ignite presentation.
This may help with CSC #6:
https://www.ncsc.gov.uk/information/logging-made-easy
I agree this is how it SHOULD be. It’s even how it IS with larger customers. The problem arises (usually) when the customer is small. If your most basic offering costs $100/computer per month (because it covers all the security baseline stuff like AV, proxy, firewall, admin-control, configuration management, network monitoring and service denial, etc), and the prospect only has $50/mo in his pocket, you never get past the front door. The prospect never becomes an MSP customer. He may be a break-fix customer or just go elsewhere. None of this should be blamed on the MSP–the customer/prospect has final say on if he spends his money on you, not the other way around.
On the other side of this equation, the MSP has bills to pay, as well. If the MSP can secure lots of large customers willing to pay the $100/mo per computer basic price or more, then all’s well. If the MSP refuses to do business with smaller customers because he must get his $100/mo to cover his security costs per computer, but doesn’t have larger ones, the MSP quickly goes out of business. This is the real world from a business owners perspective.
The only middle ground I can see is to unfortunately make some compromises to allow for a lower price of entry, but also provide a roadmap to get to where everyone should be at a minimum. Remember that IT Security is not about blocking bad things. It is about allowing business to happen in as secure a way as possible. A network can be 100% secure, but will likely not allow business to occur, so the security is meaningless. A network can also be left wide open to threats and will allow business to happen freely, until the threats hit, then business stops, so the (non)security is also meaningless. IT Security is therefore about compromise. How much security can the business afford now, and how to increase business so that more security can be afforded later. There’s also the concept of fitness to a particular environment. One would never put a Cisco enterprise-level firewall/router into a 1-person office, for instance.
I think we agree on more than we don’t. For example, see my write-up on the security triangle. But I also believe it is possible to get the basics done for SMB-affordable prices. So the way you build it is you draw a line in the sand, and say that there are certain things that the customer must do, if they are going to be my customer. Choose your baseline–I suggest the CIS Basic Controls (plus MFA, plus backup–those come in during the Foundational Controls, but they belong in the baseline). Some items the customer has a choice on, and that includes how fancy they want their endpoint protection to be (e.g. basic AV only vs. full EDR, etc.). So some items I place into an “Advanced Security” add-on or separate service tier.