From Ignite 2019: Office 365 ATP Best Practices Analyzer, and other actions MS is taking to democratize security
I haven’t had time to write an overall review of Ignite and all the various announcements that were made. And honestly, I might just skip that because there are so many others out there doing the same. They probably did an even do a better job than I would. So go check out the Tech Community blogs–anything dated 11/4 – 11/8 is probably worth reading to catch up on the big story arcs. Or, go to Twitter–honestly it’s one of the best ways to stay up to date in the Microsoft space.
Interestingly, although I presented on a security-related topic (with regard to Microsoft 365 Business) I attended almost no Security & Compliance related sessions while I was at Microsoft Ignite (well, I still caught a couple of them). I spent most of my time with the Productivity track this year, and I was especially keen on learning more about end-user training and adoption. I think this is where IT is going to have to invest considerable attention moving forward.
But in this post I want to focus on one of my personal favorite announcements in the security space that I heard this past week at Ignite (and it hardly got any attention it seems). We will soon have a “Best practices analyzer” for Office 365 Advanced Threat Protection (ATP), as well as some new policies that can be applied to maintain a “best practices” configuration and protect you against drift moving forward.

Sometime next year, in the Security & Compliance center, we will find under Threat Management > Policy three new cards on the top row: the Config Analyzer, and two protection templates: Standard protection and Strict protection.
Regarding the Configuration analyzer, this is already available via PowerShell. To get started, simply run:
Install-Module -Name ORCA
And once it is installed, run:
Get-ORCAReport

After the output, it will deposit a report into a local appdata folder, and launch it like so:

In the future you would be able to review this type of report online using the Config Analyzer–the screens they shared at Ignite may possibly be conceptual only at this point:

Currently the PowerShell module checks 26 different items. I found a few areas where my best practices were out of alignment–but mostly these weren’t a big deal. For example, MS prefers the Junk Mail Folder (MoveToJmf) for say bulk mail or regular spam, but they prefer that high confidence spam and phishing emails go to Quarantine. Well, I generally send everything to Quarantine. I dislike having two disparate places where a false positive mail message might be lurking.
But honestly, I’m not going to hold on to my pride here, I am just going to update my scripts to fall into step with what MS is recommending using this tool (unless they were recommending something obviously bad). In the future, staying on their recommended config will become even easier–read on.
The idea behind the “Standard” and “Strict” protection templates is that you can “subscribe” to one of these pre-defined configurations, and even when Microsoft introduces a new feature or changes their best practices in any way, your tenant can be automatically updated to reflect their preferred config. This is a huge win for MSP’s and other organizations that need to manage a lot of tenants and want to take out some of the manual configuration and guesswork, not to mention managing configuration drift and revisiting all of your customers every time there is a change in the service.
For instance, there is a new option now in ATP AntiPhish policies, where you can enable mailbox intelligence for the entire tenant (they got a lot of complaints about the 60 users limit on user impersonation detection–so this should help with that). But that means we now have to loop back through all of our customers and update these policies. That’s a lot of manual work. Wouldn’t it be better to have a protection template that does this for you?

These announcements are very much in line with a theme I have seen emerging over the last while, and pronounced explicitly in a few Ignite sessions: Microsoft routinely sees that the top reasons for compromise are poor tenant configuration. Either a critical protection was available and not configured, or it was misconfigured, or in the case of email for example, they find an allow rule or bypass rule that explicitly skips the filters and protections that were put in place (and yes, there are people out there white-listing “gmail.com”–believe it or not).
To be fair, even aside from egregious mistakes like white-listing entire domains or IP blocks, it is confusing and hard to keep up with all of the changes in the enormous cloud service that Microsoft 365 represents, so Microsoft is trying to take some steps here to democratize security and enable easier access to a base level of default protections across all tenants. I think this is a good thing, and it should (in theory) make our jobs easier.
And this philosophy does not just apply to email.
We also have the Security Defaults. These are available today, and will soon replace the Baseline Conditional Access Policies. As the name implies, the Security Defaults will eventually be enabled by default. And that means that all users must register for MFA. I have not seen a solid date on this change yet, but it promises to be a big deal. MFA is just not optional these days, but so few tenant admins are turning it on. Microsoft needed to do something, and it sounds like this is going to be it.
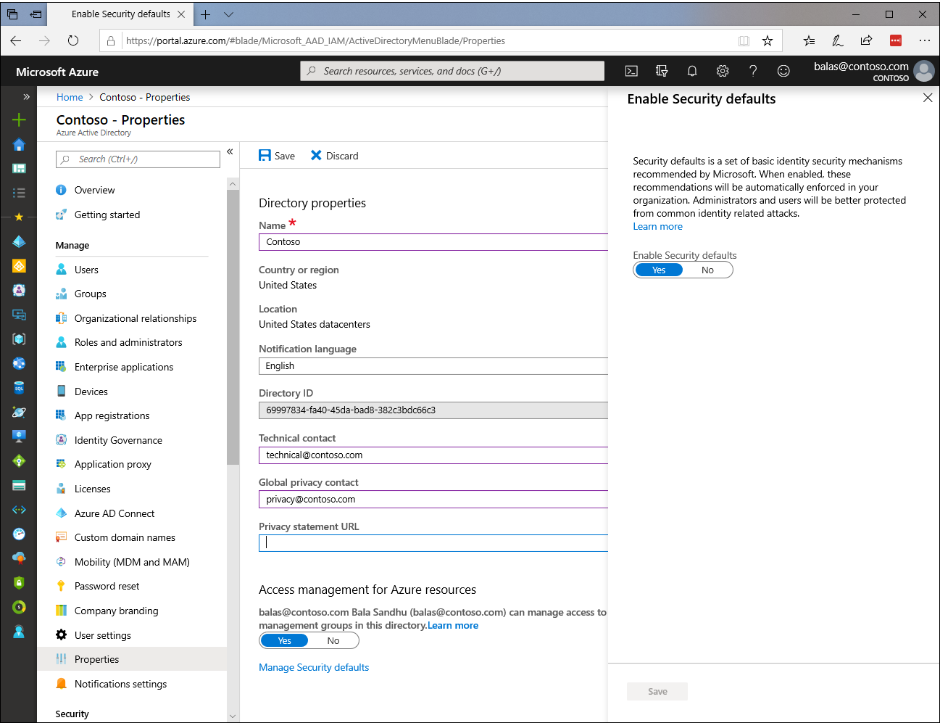
With regard to these Defaults, the other important thing to remember is that they will need to be disabled if you plan to implement your own custom Conditional access policies (which is basically every tenant I work with). You would then need to re-create the baseline policies to enable tenant-wide MFA and disable legacy authentication, in addition to other custom policies you want to have. Still, this is a welcome change for those who do not have the full Microsoft 365 suite, or the Enterprise Mobility & Security SKU in their tenant.

As regards endpoint / device security, you can already go browse the MDM baselines in the Device management portal (part of Microsoft Endpoint Manager now). There are some additional new baselines coming, including Edge and Office.
And so the theme continues through much of the Microsoft 365 space. The tools are all there to implement a really good security configuration–but hardly anyone is using the tools. I think Secure Score was one early effort in this space, but it just hasn’t been enough on its own to get admins started down a good path.
Therefore I am hopeful that the new upcoming additions will help accelerate (especially SMB) tenant admins in their journey to a better security posture. It has also inspired me to start working on something even simpler for low-skill “accidental” tenant admins out there who are just looking for the “easy button.”
Of course, good security is not just an “easy button” and never will be, but nevertheless we do need a better baseline than what comes out of the box today (I wouldn’t be surprised to see items like the Security defaults continue to get pushed out by Microsoft as well, in the future).
If you want to tune into the sessions I mentioned here, check out:
- Superlative protection, unparalleled intelligence: Learn why Office 365 ATP is the most trusted solution
- Your users are under attack! Strengthen your anti-phishing defense with these O365 ATP best practices
- Protect against phishing and other cyberthreats with Microsoft 365 Business
- What’s new in Microsoft 365 Business: Advanced security for small and medium businesses (This was the session I co-presented with Microsoft’s own David Bjurman-Birr)


Comments (5)
To be fair many announcements during Ignite are for Q1-2 or even later in 2020. So it will be more useful to cover when it is actually available. They also tend to rehash a lot. Say in Yammer blog they posted 3 nearly identical posts in one day..
Orca output looks like a great way of generating reports quickly that is available now.
I did find that it had issues detecting I was connected to Office365 already, but using
get-orcareport -noconnect
after being connected already allows the report to continue through successfully.
I couldn’t agree more that the focus needs a paradigm shift to the end-users and overall adoption and awareness. With that said, thank you for always producing such great content for all of us and congrats on your recent Microsoft MVP status!
Thanks for flagging this – I thought I had most announcements from Ignite covered but this one passed me by.
For those who are using the Baseline policies there has been an update:
“Baseline Protection policies are a legacy experience which is being deprecated. All Baseline Protection policies will be removed on February 29th, 2020. If you’re looking to enable a security policy for your organization, we recommend enabling Security defaults or configuring Conditional Access policies.”