Customers always have a choice when it comes to security
I had a reader ask me recently whether I now recommend Microsoft 365 E5 or E5 Security for my clients, even though it is a more expensive option, and I was a bit surprised at the question–as if they were suggesting it is my decision to make.
It is important to remember that customers always have a choice about how much money to spend on security. Differences in price often come at a cost somewhere else. The old joke is that the cheapest way to make a system secure is to disconnect it from any networks, public or private (but then its functionality and value quickly diminishes to zero).
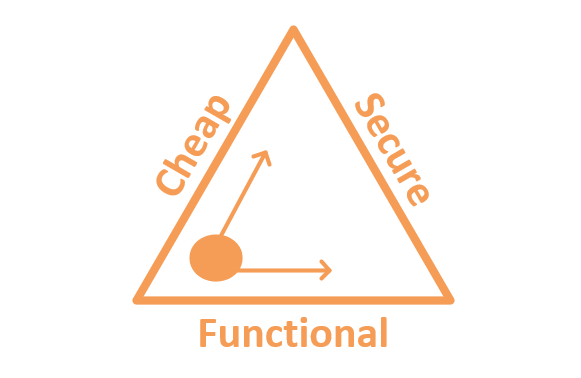
Consider the triangle above. “I can build you a fully functioning and secure system, but it will not be cheap.” Or, “We can keep it cheap and make it secure, but it will have negative impacts on functionality.” The challenge for the customer is making this choice as you begin to address each risk: which side of the triangle are they most willing to sacrifice? This same decision can oftentimes be evaluated independently for various controls or risks.
Practical Examples
First, consider limiting admin privileges on workstations (CIS Control #4): this is an inexpensive way to boost security very quickly. If the organization is willing to remove admin rights for their end users, that means one cannot install apps or make system changes on their device—at least not without getting an admin’s help. In some cases, this is going to add friction to the user experience, where certain administrative privileges are expected or required.
However, some third-party solutions will help you to make this transition more seamless and transparent. Tools like Least Privilege Manager from PolicyPak can make life easier and restore certain functionality (e.g. some apps need to run as admin even though the user does not have these rights). In other words, we can reduce friction by applying a little more money to the equation.
Consider another example, in the realm of data protection (CIS #13): let us assume that you want to encrypt files so that they remain protected no matter where they roam—whether attached to an email and sent out of the company, or copied to a USB thumb drive and used on another outside system. Microsoft 365 has a product built-in which does just that; it is called Azure Information Protection (which powers ‘Sensitivity labels’ in Office 365), and it comes in two flavors: Plan 1 and Plan 2 (the latter is available through their top-end E5 offering).
The difference between these subscriptions (aside from price) is a distinction in functionality between manual versus automatic labeling. Both subscription levels achieve the desired goal of data protection, but the more expensive plan is able to find and classify content automatically based on specific criteria—that is a more advanced functionality that makes your life easier, which means it is going to cost more money.
Accepting the risk is also an option
A very common scenario for accepting risk centers around Line of Business applications—especially ones that are no longer supported with security updates, or apps which are very costly to upgrade. In these cases, there may be other ways to address or at least mitigate the risk. For example, you can choose to isolate legacy systems on a separate network segment (VLAN) that does not have remote access or communication with the rest of the network.
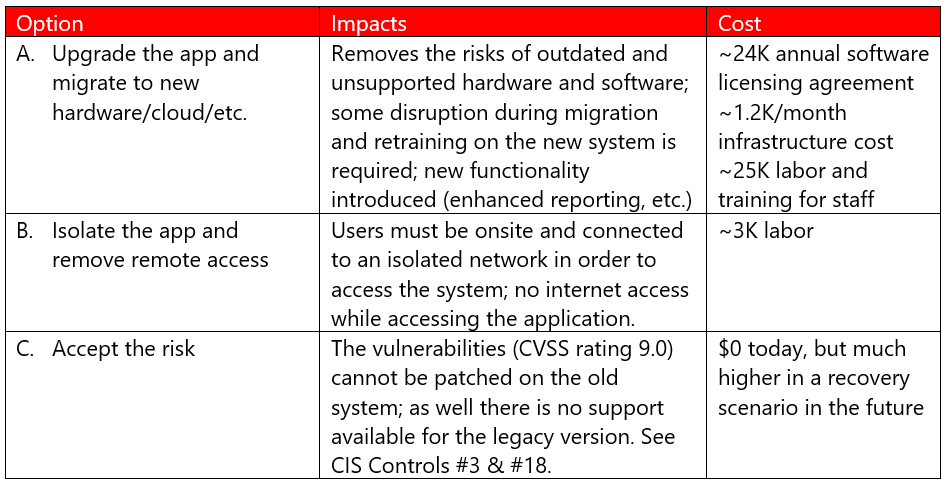
Perhaps Option B makes sense in the short term, as the budget remaining in the fiscal year does not allow for A. This may have impacts on how end users gain access to these systems until a different solution is achieved (upgrade, migration, etc.), but in the interim it does remove the risk of having the vulnerable system(s) exposed to the rest of your network. Or, perhaps there is no upgrade; the system can be retired soon enough, and the customer is comfortable “riding it out” for a few more months until they sunset the application in question (C). These decisions will always be influenced by the business context and the customer’s risk tolerance.
Whose responsibility is security anyway?
Sometimes a customer will just want you to make the decisions for them. “Well what do you recommend I do?” is a common refrain you will encounter. Obviously, your choice would be to address each risk to every extent possible, but that is not always feasible for every business and could get really expensive, or disruptive, or both.
Sure, there may be a few “top recommendations” that you can strongly advocate for—such as Multi-factor Authentication, an inventory tracking system, backup, regular patching, having some kind of detection and response capabilities as well as an incident response plan. However, the responsibility for the decision lies with the customer as they address their own risks.
If they attempt to dodge this responsibility and turn you into the decision maker, you may need to gently reiterate that your role is primarily to inform them of the risks—obviously you would like to see them address the risk to the highest degree that they can reasonably afford or tolerate—but ultimately the decision rests with them.
The moral of the story here is that you can always find ways to spend more money on security, but there are also ways to apply good security at a relatively low price. Your job is to help the customer find their own right balance between risk, budget, and functionality.
In my experience, when it comes to Microsoft 365 subscriptions, especially in the SMB space, the Business Premium package ticks off a lot of good security & compliance checkboxes at an affordable price. Add-ons or upgrades from there may help you further reduce your risk with some additional bells & whistles that make certain tasks easier, but again it all comes at a cost! It is very important to understand that it is always the customer’s choice at the end of the day. But it is your responsibility to at least educate them and make the offers available to them.


Leave a Reply