How much security is ‘enough’ security? Looking at Microsoft 365 Defender vs. Azure Sentinel
How much security is ‘enough’ security? This is in fact a trick question, I just threw it in there to get your attention. When it comes to security, one can never be ‘safe,’ but only ‘safer’ (even with the most expensive of cybersecurity tools and talented, dedicated humans to back it up). At the same time, there are so many different cybersecurity products available, even from a single vendor like Microsoft, that it can be difficult to understand what you are getting yourself into when you buy certain products or bundles.
Today, I want to talk about two distinct products that many of my readers still find confusing: Microsoft 365 Defender products (formerly Microsoft Threat Protection), versus Azure Sentinel.
Microsoft 365 Defender
Microsoft 365 Defender is now described as Microsoft’s XDR solution (Extended Detection & Response). It is in fact a marriage of several products under a single banner, and all of these are available through either of the SKUs:
- Microsoft 365 E5
- Microsoft 365 E5 Security
The products that are included under the Microsoft 365 Defender brand are also available as standalone add-ons to any other subscription, and each of them provides coverage over a specific domain or area:
- Defender for Office 365 provides zero-day anti-malware and anti-phishing protection for Exchange Online messages as well as files stored OneDrive for Business, Teams and SharePoint Online
- Defender for Identity provides actionable insights and cybersecurity alerts against traditional Active Directory domains
- Defender for Endpoint is Microsoft’s Endpoint Detection & Response (EDR) product, so this covers security events on endpoint devices
- Microsoft Cloud App Security provides the same types of cybersecurity insights and alerts, but with regard to cloud apps such as Office 365, as well as third-party apps like Box and Salesforce (and several others)
All of these products can share insights with each other through the Microsoft Intelligent Security Graph, and thereby provide Security Operations Center analysts some correlations between seemingly disparate events in different domains. The key here is that these products exist to surface “interesting data” out of all the noise of raw log data.
Plus, you can do some cool stuff like take threat information from a device and integrate that with Azure AD Conditional Access to automatically bar access to devices which are over a certain risk threshold according to Defender. Or, if a malicious file is discovered by Defender on an endpoint, that data can be shared back through to Office 365, where any copies of that malicious attachment, if it exists in any mailboxes, can be ZAP’d into oblivion.
Azure Sentinel
Azure Sentinel is a cloud-native SIEM and SOAR tool, which you can use to collect log data from any number of sources, including Microsoft 365 Defender! However, you can also import logs from other on-premises sources such as servers or security appliances including firewalls.
Once you have the log data being ingested into the Azure Sentinel workspace, you can run queries against that data either automatically or manually, and set up your own custom alerts as well as automated responses or playbooks when certain criteria is found or met. This tool would require you to have a more advanced, dedicated SOC team to configure, monitor, tweak and customize this tool over time.
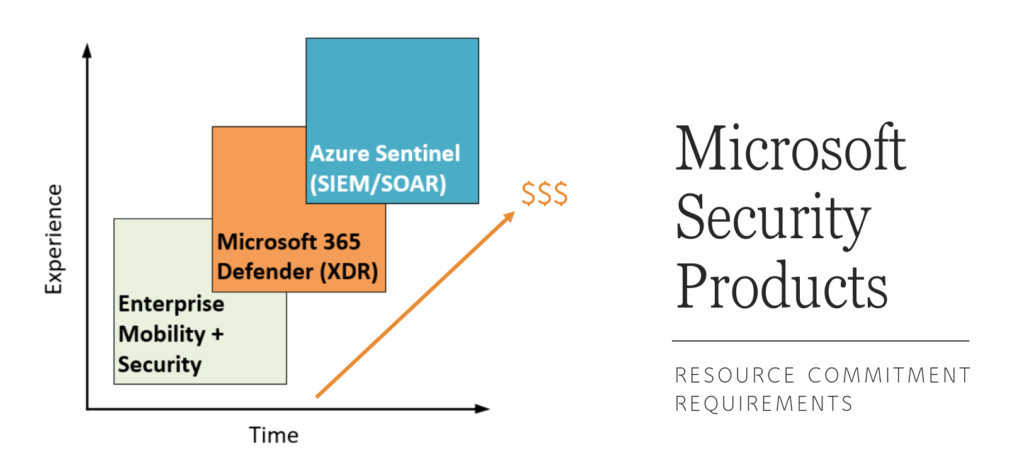
I contrast Sentinel against Microsoft 365 Defender (XDR) products in the following ways:
- I argue that the Defender products are a bit easier/quicker to implement and are less to manage on an on-going basis; even junior, start-up or “part-time” SOC teams can get benefit from these tools quickly and without much capacity being dedicated to their development and maintenance
- Sentinel is much broader in its application and much better for getting at raw data, and building custom queries and hunting. This is especially important when you have data sources outside of the Microsoft 365 space such as on-premises servers and security appliances; as well you can choose to retain your data for longer periods of time in Sentinel.
Microsoft Defender does give you some access to raw data, but it is optimized to surface “interesting” events via alerts (potential incidents). That having been said, know that even Sentinel has some pre-canned alerts and playbooks that you can deploy and use out of the box, meaning you can get value from it pretty quickly. The reality however, is that to get the full benefit of this tool would require a more nuanced approach and more experienced cybersecurity professionals with dedicated capacity.
Opportunity for Service Providers
Both the Microsoft 365 Defender XDR products, as well as Azure Sentinel, are ripe with opportunities for Service Providers who are looking to build a Managed Security Services Practice (MSSP). Defender for Endpoint and Microsoft Cloud App Security are my favorite go-to recommendations for teams who are just getting started; they can often replace other endpoint and/or cloud monitoring tools with these native products, and I think they often do an even better job at certain things, vs. some of the competition (plus Gartner consistently puts Microsoft Defender in the Magic Quadrant).
But I will also add that Sentinel has a unique value proposition for Service Providers in particular. Why? Because Azure Lighthouse will allow you to manage multiple Sentinel workspaces from all of your various customer tenants/subscriptions. Unlike Microsoft Defender products, we aren’t waiting for multi-tenancy; we already have it, and you can stand up a pretty comprehensive solution with centralized management built-in.
The other really good news is that Microsoft Defender data can be ingested into Azure Sentinel for free. Most other data sources will result in additional charges, but not the native Microsoft stuff. Therefore, if you configure some of the Defender products such as Microsoft Cloud App Security, Defender for Endpoint and so on, then you can surface that information in your multi-tenant portal, in Azure Lighthouse/Sentinel.
So that is the reason that you will most likely want to consider both very carefully, if you are building a Managed Security Practice (they are certainly better taken together). That having been said, if you are brand new to all of these products, I would recommend that you “dig in” starting with the Defender XDR stuff, and moving over to Azure Sentinel after that:
- Microsoft Defender for Office 365
- Microsoft Cloud App Security
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity (legacy AD environments only)
- Azure Sentinel (to bring it all together)
Now remember that you can also offer a “Basic” Managed Security Service without touching any of these additional “super-tools”; indeed, that is basically the subject of my first two cybersecurity courses on teachable. However, adding Microsoft 365 Defender and Azure Sentinel will certainly help to reduce your risk further, and to raise your visibility and awareness to certain pre- and post-breach events. They will take you much further into “detection & response” territory. Therefore, these would be an excellent basis for launching an “Advanced” Security offering / MSSP service.
Here are some other resources if you are getting started with these tools:
- My own Beginner’s Guide for E5 Security on GumRoad (Updated November 2020)
- Become a Microsoft 365 Defender Ninja
- Become an Azure Sentinel Ninja
- Microsoft 365 Defender Connector for Azure Sentinel (preview)
- Using Azure Lighthouse and Azure Sentinel to Investigate Attacks Across Multiple Tenants
- Build a scalable security practice with Azure Lighthouse and Azure Sentinel
What is the take away?
Do you really need all of these different security tools? Never forget: the customer always has a choice. At the present moment, Sentinel is probably the best option for a serious Service Provider given the multi-tenant functionality via Lighthouse, not to mention the fact that you can standardize on one tool, regardless of what other security subscriptions are present in any given customer’s tenant. But Sentinel comes with a steeper resource commitment. You have to be really serious about building an offering on this; if you are going to do it, be prepared to invest some serious time and money into the undertaking.
If you want to get started with less investment, then I can report that tools like Microsoft Cloud App Security are extremely easy to use, and MCAS in particular even allows you to send notifications from custom email addresses (so a ticketing system can more easily identify which customer each alert is associated with). Defender for Endpoint is much like other endpoint security products, and can likely replace whatever you already use in this space (plus it is “agentless” so that makes for easy deployment and immediate benefits when integrating with Conditional Access and other areas in the Microsoft ecosystem).
We have never had this many solid options before from a single vendor (and there are so many other choices out there from excellent third-party security vendors, too); it is certainly not a bad problem to have, even if it can be a bit difficult to navigate.




Comments (7)
Alex,
Can sentinel receive any data from none ATP enabled endpoints such as those with an M365 Business Premium license?
With a Microsoft 365 Business Premium license you will be able to ingest Office 365 data for free, and when you add Microsoft 365 Defender subscriptions then you will also be able to import the Defender data for free. The big gotcha is that Business Premium includes Microsoft Defender for Office 365 P1, and P1 does not allow you to port the data free of charge. If you buy P2 then you would qualify. Basically if you own the “full” products individually or through a bundle you have the benefit of importing the data to Sentinel free of charge. So, really they should say the data ingestion is “included” with the price of your subscription–there is no such thing as a free lunch ;)
Ah ok I see. Thanks for clarifying. ?
Great read Alex. What parts of M365 Defender are included with M365 Business premium? Can you create a chart similar to your licensing chart but have it be MS security services and what they are? I know MCAS is not included but Cloud App Discovery is. How does that work and is that useful?
There may not be enough interesting data for an entire chart. When it comes to M365 Defender products, the only piece that is included with Business Premium is Defender for Office 365 P1 (not P2). So there probably exist charts about this out there, but, P1 = the policies such as anti-phish, safe links and safe attachments. P2 = Threat Explorer, Attack Simulator, Automated Investigation & Response. Basically P1 = protect, P2 = detect & respond. As for cloud app discovery–that is included with Azure AD Premium P1, and it isn’t as valuable on its own, since you need the full MCAS + Defender for Endpoint to be able to discover cloud apps at the device layer (vs. uploading firewall logs–and with most folks working remote/from home these days that’s really pretty dull feature).
Very good article!
Very complete and detailed.
But I was left with a question that maybe you can contribute.
I have the solutions in my environment and I’m in doubt about how to centralize everything.
I have Azure Sentinel receiving the Defender Atp, MCASB, Azure ATp, Office 365 ATp logs, among others.
I also have MCAS integrated with Azure ATP.
The question is. Where should all technologies be centralized?
That is, if I use Microsoft 365 Security Center to centralize Defender ATP, Azure ATP, MCAS and Office ATP, does it still make sense to receive these logs in Sentinel?
Would it be possible to integrate alerts generated in Sentinel with Microsoft 365 Security Center?
If I receive the solution logs on Sentinel, what would be the meaning of Microsoft 365 Security Center? Can I work with both, centralizing the solutions in both?
I know that there may not be a final answer, but I would be happy to get your position.
Thank you.
Sentinel is certainly another ball game. All of the M365 Defender tools should roll their data up nicely into the new security center (and MCAS does a pretty good job too for the identity and cloud app data). But, these tools are hyper-focused on the “interesting data” from the M365 security suite. The Sentinel is a SIEM, and like any SIEM, it is basically a giant log collector and analyzer, but not as easy to use. You would not push Sentinel data to M365, but only the other way, you can ingest M365 to Sentinel (and any other input you like).
The M365 security tools are “easy to use” and will be more “intuitive” to navigate as you investigate and respond to alerts. If you get into the SIEM tools, you will probably spend more time wrapping your mind around them, and tuning them over time.
At present, if you are a service provider it is the best place to push data because we have Lighthouse in Azure, which allows us to see more than one tenant’s data. But we do not have similar with M365 security tools themselves. If you are just managing a single tenant, then your best and lowest friction/startup cost will still be the M365 security tools. Sentinel you are reaching into a new pandora’s box. It can be powerful but you have to be committed to it.