Unboxing Defender for Business, Part 2: Threat & Vulnerability Management
Last time we looked at how to get started with Microsoft Defender for Business and the so-called “Simplified configuration process,” which helped us onboard our first Windows devices and apply basic policies to manage antivirus and firewall settings across the organization. In this blog post, we will ask the question: what else can we do, now that we have all that data coming in from our fleet of endpoints? Let’s start answering that question using a feature Microsoft calls Threat & Vulnerability Management (or TVM).
What is TVM?
One of the CIS Critical Security Controls (CSC #7) reads:
Develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and minimize, the window of opportunity for attackers.
Everyday, new vulnerabilities are discovered in software. Known as Common Vulnerabilities and Exposures (or CVEs), these bugs are documented and assigned a CVE ID. As well, each vulnerability undergoes some analysis to receive a score that indicates its relative severity on a scale of 0-10 (this is called the Common Vulnerability Scoring System or CVSS). If left unmitigated, CVEs can expose an organization to serious cybersecurity risks.
Oftentimes the way to mitigate these risks involves applying a simple patch or update to the affected software, but not always. Other times there is a deprecated or unused feature that can be disabled, or some other configuration change which is recommended by the vendor. While you can find information about CVEs in general at places like Mitre and NIST, how do you know which ones are actually impacting your environment at any given moment?
Microsoft Defender for Business catalogs all of the software that is installed across your endpoints and reports that information back to the cloud, and that means we are able to monitor for these vulnerabilities in near real-time. Enter Threat & Vulnerability Management.
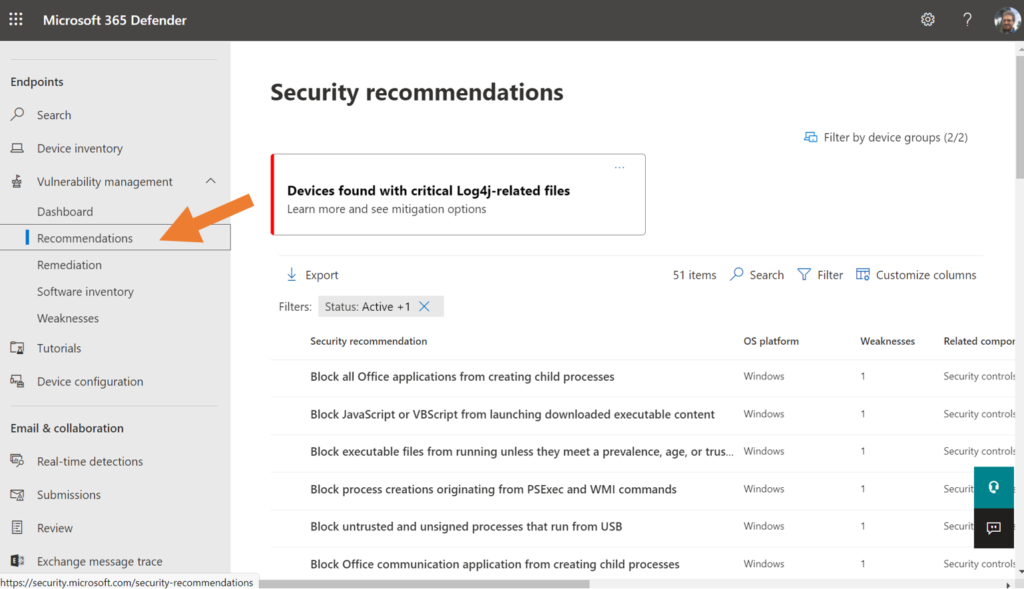
From the Microsoft 365 Defender portal, find Endpoints > Vulnerability Management to begin exploring the TVM data. For example, you can review the vulnerabilities impacting your systems using Weaknesses, but if you visit Recommendations, you will be a presented with a list of actions that you should take to mitigate any corresponding CVEs.
As well, you may notice that there are other security recommendations in here, which are not related to any specific CVE per se, but which nevertheless could improve the overall security posture on your devices (for example, enabling Attack Surface Reduction rules: something we will explore in an upcoming post).
Getting notified of new vulnerabilities
Right now I have access to two tenants with Microsoft Defender for Business, and in one of them, the notifications feature does not appear to be working yet. So I hope to get more information on that soon. But, this product is still in preview, so I guess I will cut them some slack. Let me know if you run into anything similar in the comments!
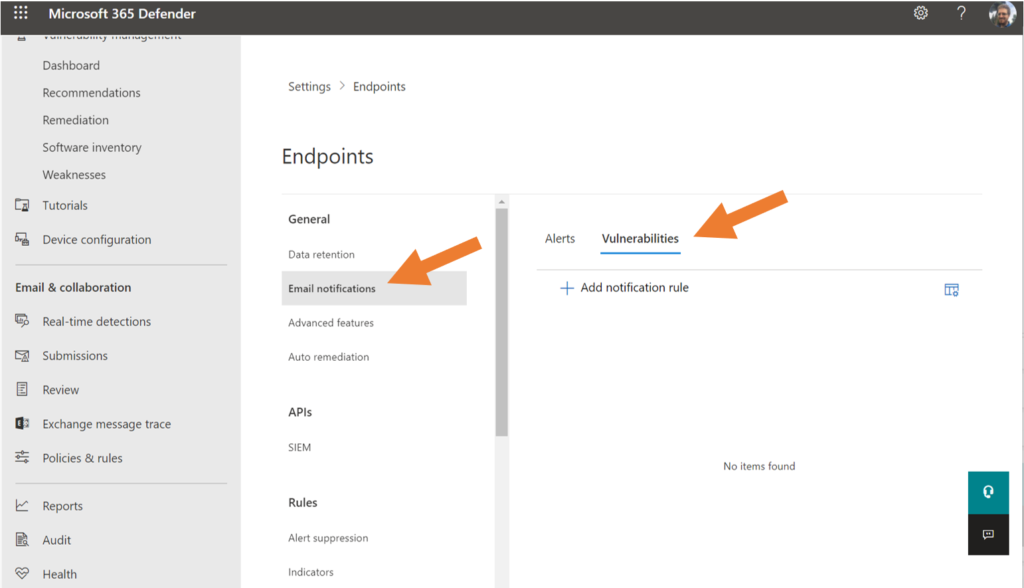
For those with working tenants, navigate to Settings > Endpoints > Email notifications (actually, I expect that this step will be included in the first-run wizard experience eventually, but right now we still have to do it separately). You will want to select the “Vulnerabilities” tab.
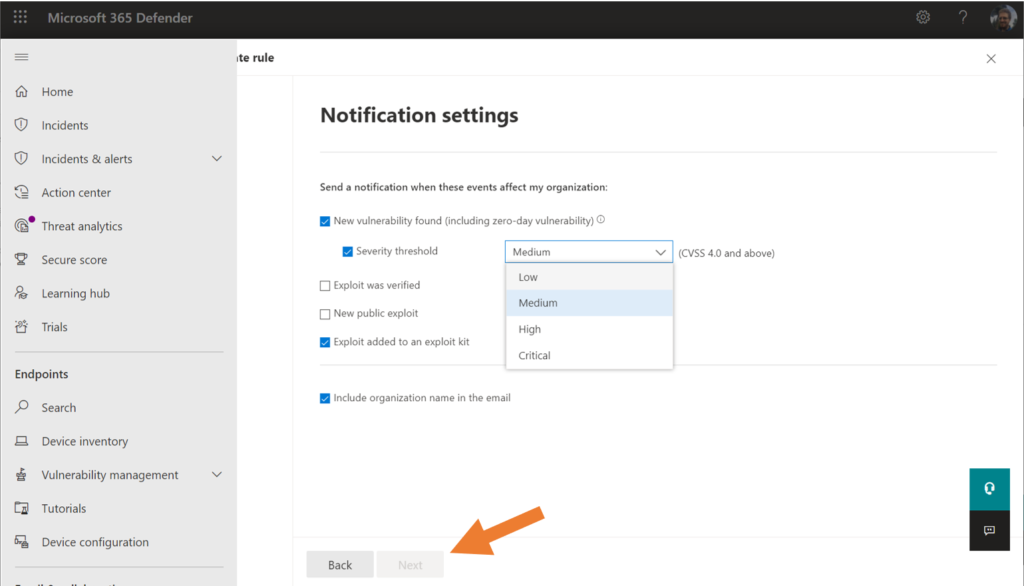
As I mentioned, in one of my tenants, I can begin the process of creating a notification rule, but it will not allow me to finish the wizard (see how the Next button is greyed out below).
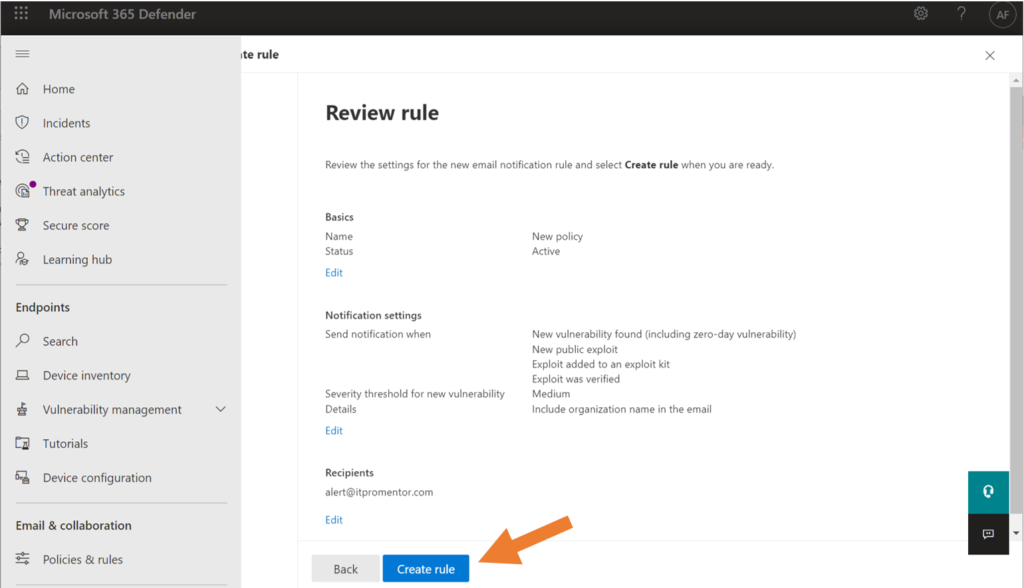
This is an especially handy feature for Managed Services Providers who have to monitor multiple tenants, so I hope this is not a widespread bug for the other previewers out there! When it does work, you can proceed through, choosing your options and clicking Create rule to finish the process.
Now you will be notified when new vulnerabilities matching your criteria are discovered in your environment.
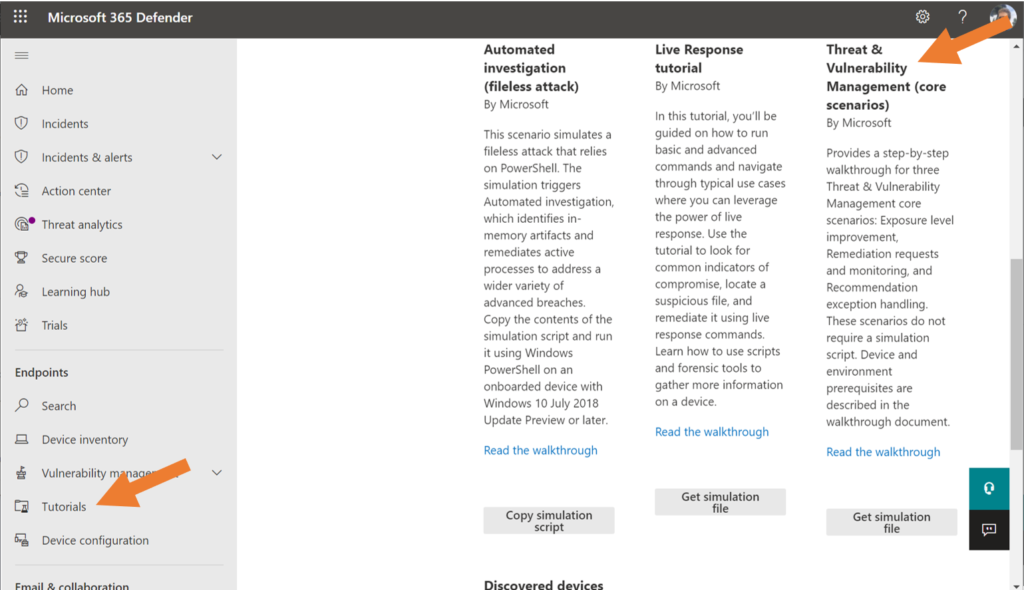
Tutorial available
Microsoft also makes available several Tutorials from the left navigation. Find the one for Threat & Vulnerability Management (core scenarios), and download the walkthrough and simulation file so that you can get some practical “hands-on” time with the tool.
For example, you will learn how to assign and track your Remediation activities (or alternatively how to make exceptions).
Conclusion
Threat & Vulnerability Management is a great way to increase your visibility, and shrink the time that devices remain exposed to new threats. This tool is a perfect fit for MSPs who have so many different customers to keep an eye over, with all sorts of different applications and potential vulnerabilities.
At the same time, I am seeing some instances (hopefully rare) where this preview isn’t yet working as desired. I generally do not like to report on these types of things until I have at least a theory as to the cause and a potential workaround or solution. Right now I’m at a loss for both. But, simply raising awareness to the issues is sometimes the necessary first step. If you are experiencing anything similar with the preview to what I described (or other issues with MDB), do let us know in the comments below! The community would benefit from it, and I would love to get Microsoft’s eyes on it, too!
In Part 3 of this series, we will review Attack Surface Reduction rules, and also demonstrate how TVM data can help you to implement these rules with minimal interruption to your users.





Comments (2)
I’m having difficulty understanding all the different flavours of Microsoft Defender and what is included in each, so I have my M365 Business Premium license which gives me Defender for Office 365 P1 but now I get Defender for Business as well! and it’s all accessible through one portal so it all blends into one!
Thanks, I will have to pull together a post on this topic. The flavors (or “flavours” in Queen’s English) of Defender can be rather confusing. Basically MDB covers endpoints (SMB version of the MDE product), and MDO covers email/collaboration. There are a few other Defender monikers out there but none that have a bearing on Business Premium itself.