What is Advanced Threat Analytics?
Advanced Threat Analytics (ATA) is a security product from Microsoft that is included with the Enterprise Mobility Suite (EMS) subscription. Unlike most of the other EMS components that tend to be a bit more cloud-centric, ATA is an on-premises-based security solution that helps identify Advanced Persistent Threats (APT’s) and insider threats before they can cause damage on your local network.
Examples of the types of attacks and threats it can protect against include:
- Reconnaissance – these are malicious attempts to discover if an account exists, e.g. through account enumeration;
- Credential compromise – for example it can detect brute force attacks, use of dummy accounts, and it can detect and alert when credentials are being passed in clear text;
- Lateral movement – where access to one resource is leveraged to gain access to another resource, e.g. pass the hash or pass the ticket–where a valid ticket is stolen from an authorized computer and used or impersonated by an unauthorized one;
- Privilege escalation and forged PAC – e.g. where authorizations on a ticket are forged or added in order to open additional access not granted on the original ticket;
- Domain dominance – attacks where a domain controller becomes compromised either through malware, remote control, or theft of kerberos keys.
How does it work?
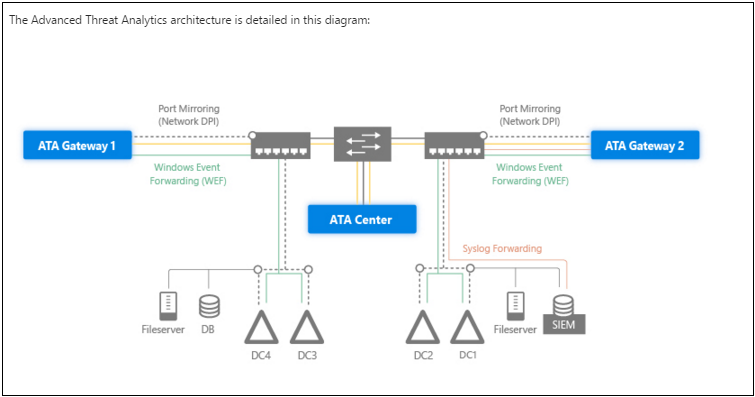
ATA requires some setup to get started. You will need at least one ATA Gateway (one per location or site), and the ATA Center installed on your domain.
Image credit: Microsoft TechNet: ATA Architecture
The purpose of the Gateway is basically to collect network traffic logs as well as data from local domain controllers, and do some processing of that data, before forwarding it on to the ATA Center. To facilitate this collection, you will need to configure port mirroring and Windows Event log forwarding for all domain controllers in the domain.
The ATA Center in turn is the engine that interprets the data, highlights suspicious activity, and uses machine learning to get better at doing so.
I am excited to get this setup and working–I would like to see how it performs over a long period of time (a few months). I will have a follow-up post on this product later down the road. Stay tuned for more!


Leave a Reply