How to enforce the use of managed applications (e.g. the Outlook app for Exchange Online) using Conditional Access in Azure AD Premium
In a previous post I demonstrated how easy it is to create a Mobile Application Management policy in Microsoft 365. With the addition of Azure AD Premium P1, we can also leverage Conditional Access polices that will require users to interact with corporate data through the Microsoft applications such as Outlook. After all, you can create a MAM policy, but those settings are only meaningful within the Microsoft apps themselves–so if you want those protections to be strictly enforced everywhere, you will need to steer your users into the right set of supported applications.
Enter Conditional Access. Here we can tell Azure AD to deny access to apps that are unsupported. Also see my post on requiring MFA for devices that are unmanaged, which is another good pairing for Mobile Application Management (MAM) policies.
Two paths diverged in a wood….
Now, if you have both MAM and MDM in your environment, you might need something a little bit different. Users who are enrolled in Intune for MDM, with their devices registered against Azure AD might be allowed to have a managed email profile in the native mail app for instance, and so need not be required to use MAM (since they are managed already via MDM). Therefore, in a follow-up post, I will also cover how to create variations on these policies which require one of the following to be true:
- Users must use approved (managed) applications that are protected by MAM
- Users will be required to register against Azure AD and Intune (MDM)
Let’s look at the first scenario–just requiring managed apps across the board (steering the entire organization toward MAM rather than MDM). Achieving this goal will require three policies:
- Policy #1: requires managed applications to be used on mobile devices for Exchange Online and SharePoint Online
- Policy #2: requires managed applications for Exchange ActiveSync (EAS) clients
- Policy #3: disables legacy clients of any kind
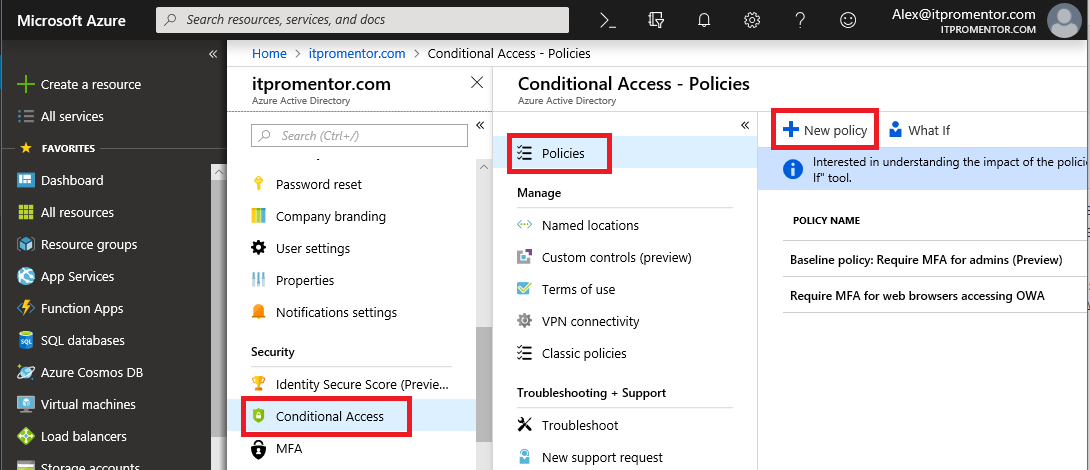
Step 1: Create a new Conditional Access policy requiring MAM-enabled apps
You can find Conditional Access from Azure AD Admin center, or the Microsoft Intune admin center (In the Azure portal). Select Policies > New policy.
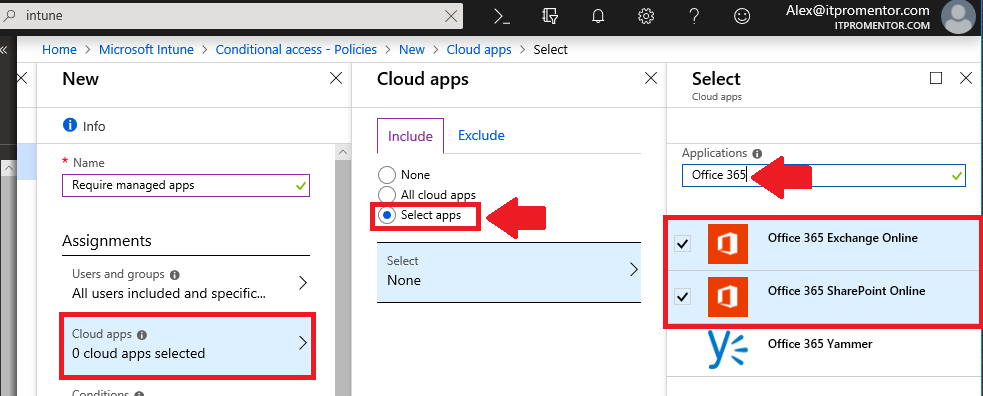
Step 2: Select your assignments
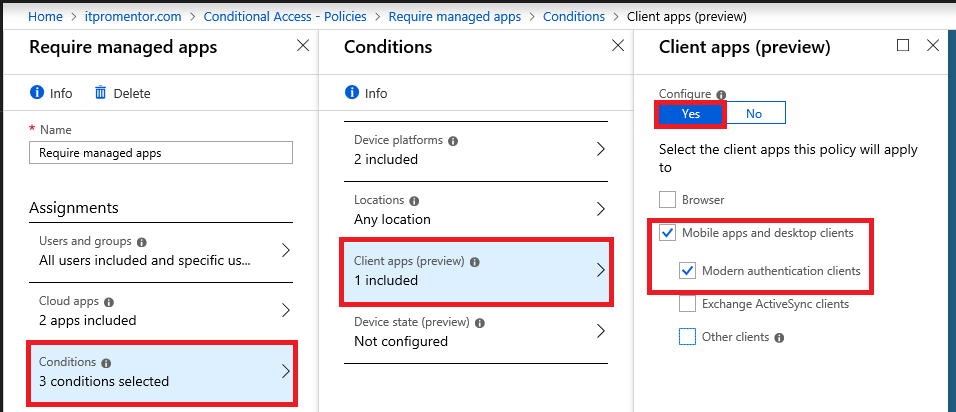
I will name my policy “Require managed apps” and pick my assignments. I want this policy to apply to All users, but you can (and probably should) scope it to a group, and/or also exclude at least one admin account. Under Cloud apps, you should pick Office 365 Exchange Online and Office 365 SharePoint Online–these apps are where most data worth protecting is stored.
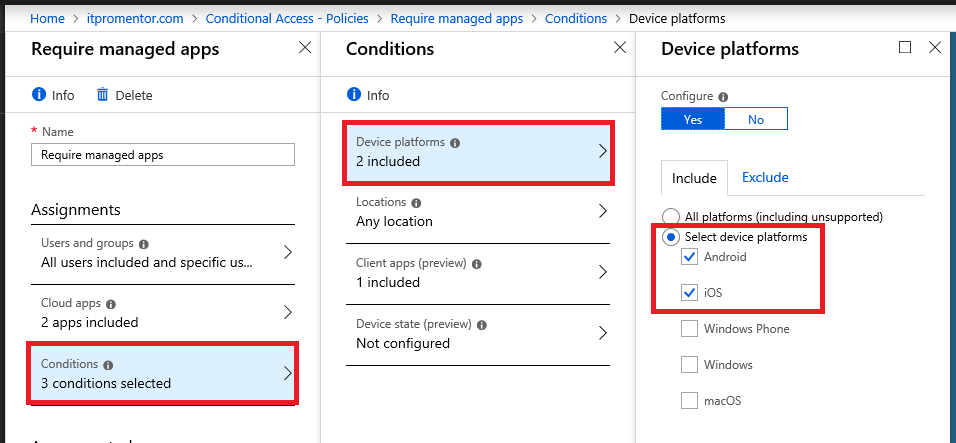
Step 3: Pick your conditions
Device platforms: This policy’s goal is to require managed apps on mobile devices (MAM). Choose Android and iOS (and I suppose Windows Phone if that is seriously in use anywhere?)
Locations: Optional, or just pick Any location.
Client apps: Choose Mobile apps and desktop clients as well as Modern authentication clients. Leave the options for Browser and Exchange ActiveSync clients un-checked. The control will not apply to web browsers, only to applications; I recommend a different policy for web browsers (require them to use MFA). As well, we cannot configure the Exchange ActiveSync clients in the same policy due to some inherent limitations with Conditional Access. So we will need to configure a second policy specifically for EAS clients.
Device state: You do not need to configure this condition.
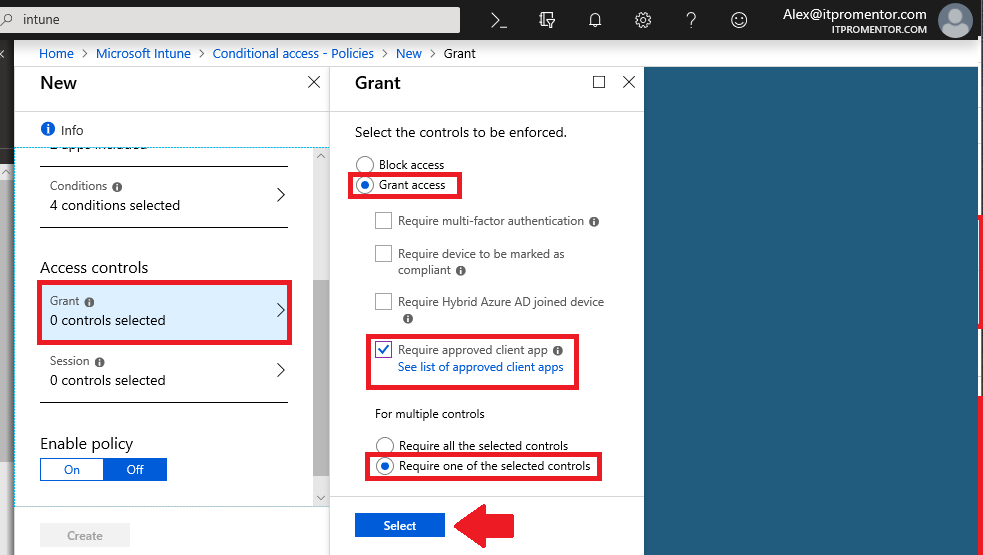
Step 4: Choose access controls
Choose Grant access, and tick the check mark box for Require approved client app–you can also click the link to see Microsoft’s list of approved apps.
When you are ready, you can save and enable the policy by choosing On, then Create.
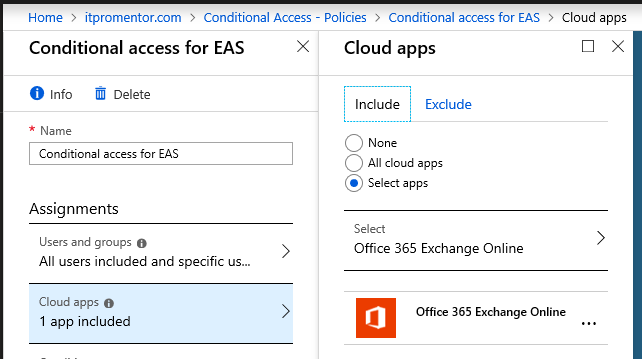
Step 5: Create policy #2: EAS client policy
As I mentioned above, you will need another policy that applies to Exchange ActiveSync clients. Microsoft requires EAS clients to be managed separately at this time. Create another policy, and give it a descriptive name. This will have the same settings as above, basically, except that under Cloud apps, you must have Office 365 Exchange Online as the only application in this policy in order for it to work correctly.
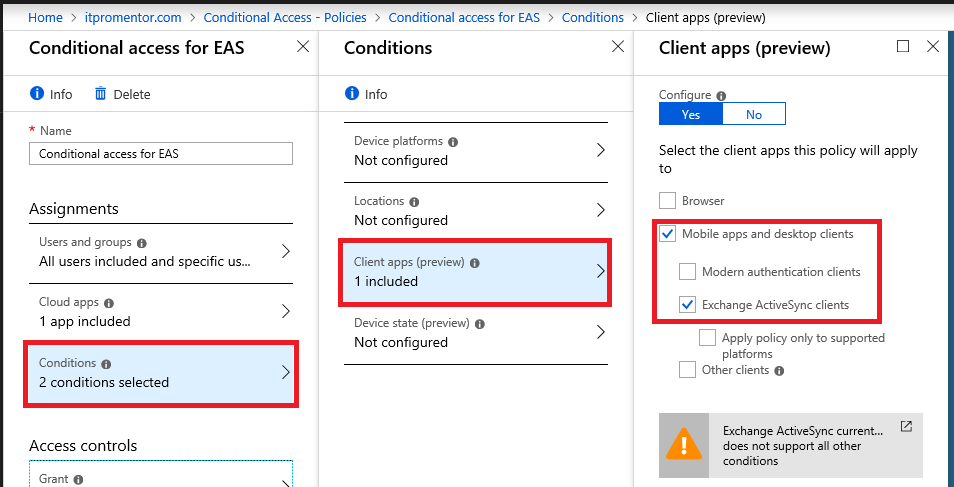
Now under Conditions you only have to define one: Client apps, and you will select only Mobile apps and desktop clients as well as Exchange ActiveSync clients. At this time, technically no other conditions are supported when you build a policy including Exchange ActiveSync (there is a note below the selection to the same effect).
The Access controls section remains the same as in the first policy. Choose Grant access and Require approved client app.
Step 6: Create policy #3: Block access to older legacy apps
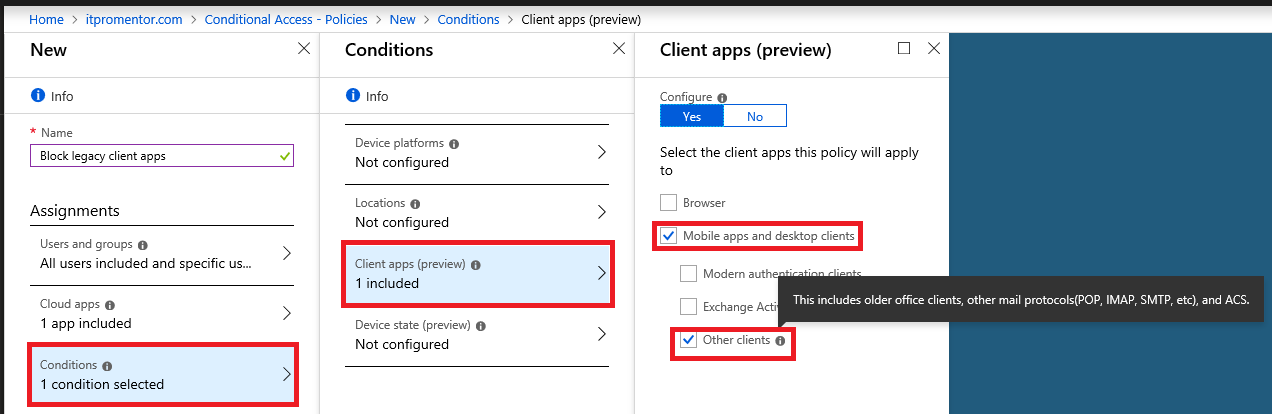
One more policy to create! The selections are quick and painless, however. This will prevent older clients from connecting to Exchange Online. Only add this policy if you have modernized your organization with newer client software such as Office 365 subscription-based desktop apps. Name it something descriptive like Block legacy client apps for Exchange Online. Again you will select only Office 365 Exchange Online for the Cloud app, as we did above. Under Client apps you need only to select Mobile apps and desktop clients, and Other clients.
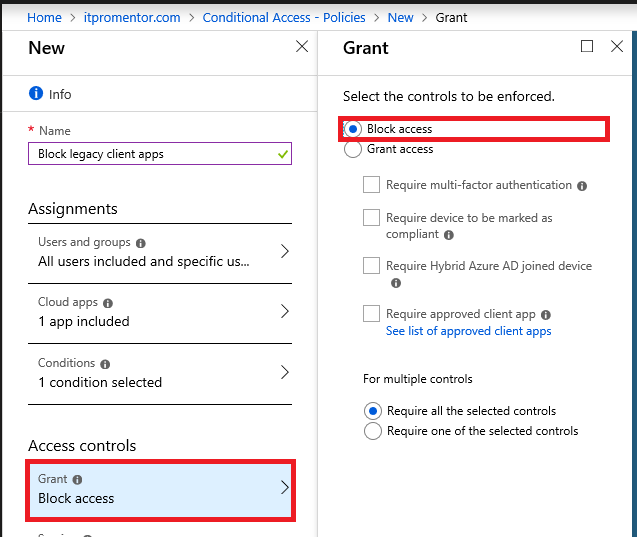
And, instead of Grant we will Block access, under Access controls.
Save your selections and Create your policy.
Step 7: Test it out!
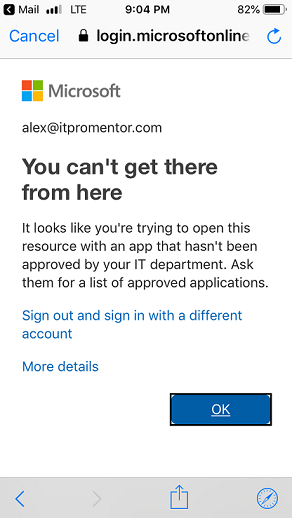
And if in your policies you accidentally included the Browser category somewhere, you may notice that access is denied as well. In my opinion, it is better to simply protect browsers by requiring MFA–raising your confidence in the authentication requests coming from the web. This should already be happening for unmanaged devices, if you’re using that policy in conjunction with this, and again IMO: this should be good enough. Nevertheless, you can imagine how easy it is to create a policy that applies to Browsers and requires MFA globally–it would be simple and quick to setup and apply universally (whether devices are managed or no).
Good luck with your own MDM, MAM and Conditional access strategies!


Comments (2)
How do you get managed apps though? it blocks access to the company portal app.
Do not target “All cloud apps” or at least exclude the Microsoft Intune Enrollment cloud app. Normally I just target Office 365 instead of All cloud apps for this situation.