Conditional access for the SMB, a how-to guide
**This resource was updated 09/01/2019**
Unfortunately it is not yet possible to import CA policies from JSON, the way we can for Intune compliance policies or device profiles. Nevertheless, now that Conditional access is available to all Microsoft 365 Business customers, you will want a good roadmap for getting started.
I have created just such a resource, adapted from Microsoft’s own recommendations. However, in my version, I have removed any references to features that are only available in Azure AD Premium P2 (E5 plans). Additionally, I’ve corrected a couple of things that I think were errors in the Microsoft articles.
The literature defines two sets of custom policies: a recommended set (for every customer) and second set set which is a bit tighter, for sensitive or highly regulated businesses.
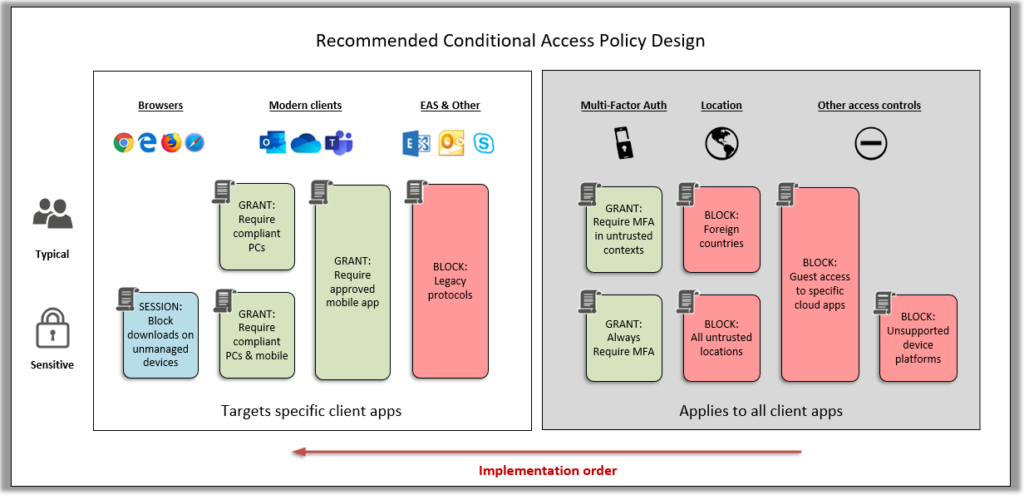
This literature will also be included with the updates to my Microsoft 365 Business Admin guide (coming soon).
- You can view the guide here
- And here is a spreadsheet which describes the policies*
*Spreadsheet design borrowed and adapted from Daniel Chronlund
Summary explanation of policies “for everyone:”
- BLOCK – Guest access to specific cloud apps: Guests should generally get access to resources in SharePoint, Teams, etc.–not All cloud apps.
- BLOCK – Foreign countries: This policy will block any sign-in attempts from countries outside of those from which the company does business.
- ALLOW – Require MFA in untrusted contexts: Devices which are not yet enrolled and compliant or coming from a corporate location will be caught by this policy and the user must perform MFA successfully to gain access.
- BLOCK – Legacy protocols: IMAP, POP, SMTP and other legacy client protocols will be blocked by this policy
- BLOCK – Exchange ActiveSync: Older email client apps that depend on EAS will be blocked by this policy. Use only if you are requiring mobile devices to use Modern authentication apps (Microsoft apps)
- ALLOW – Require approved apps for mobile devices: iOS and Android devices must use the Outlook app and other approved Microsoft applications to gain access to resources. Native mail app will be blocked.
- ALLOW – Require compliant PC devices: Windows and Mac devices must be enrolled and compliant with Intune policy in order to use modern apps such as Outlook and OneDrive.
Sensitive / highly regulated businesses:
- BLOCK – Unsupported device platforms: Prevents unsupported devices (e.g. Chromebooks) from connecting
- ALLOW – Always require MFA: Replaces the policy Require MFA in untrusted contexts. Users must always perform MFA to gain access to resources.
- ALLOW – Require MFA for guests: Enforces MFA for guest users
- ALLOW – Require compliant PC and mobile devices: Replaces the policy Require compliant PC devices; all devices must become enrolled to gain access via modern apps such as Outlook and OneDrive–mobile and desktop/laptop computer alike.
- SESSION – Block web downloads on unmanaged devices: Allows web browser access, but prevents unmanaged computers from downloading content over the web from SharePoint/OneDrive and Exchange Online.



Comments (24)
As always, you’re the best! Thanks for this resource!
You are welcome!
Hi Alex
Keep up the good work! I look forward to all your new posts.
Just a small thing that I noticed. The notes in the “Block foreign countries” does not mention an exclusion for Device state – “Hybrid Azure AD joined” & “Device marked as compliant”, although the spreadsheet DOES have these included.
Am I right in saying that the spreadsheet is correct in having these exclusions as it means that when your known users visit foreign countries, their work laptops (Hybrid AD joined) and work phones (marked compliant) will still continue to work as normal and not be blocked?
Thanks
Tony
Correct, and good catch! I will add that to my next update.
Hi Alex
Im looking at implementing just the 7 “Recommended for all Businesses” policies, and there doesn’t seem to be one where “Client Apps\Browser” is selected. Wouldn’t it be appropriate to select the Browser option for both the “Require compliant devices” and “Require managed apps on mobile devices” policies, which would allow logging into 365 using a browser on a Device (Windows Phone/Windows/Mac) and also a mobile device (iPhone/Android)?
Without this I don’t believe a browser would be allowed to access 365 (such as OWA etc).
Thanks
Tony
No, that’s not quite right. The protection that you are applying to Web browsers in the “all businesses” baseline is Require MFA. Because the policy called Require MFA on unmanaged devices will prompt for any client app (including web browsers). If you targeted web browsers in the policy that requires a compliant device, then an unmanaged machine could never gain access to resources on the web–it would have to become managed per the policy. The baseline makes it so you can access resources over the web browser, but you will be required to perform MFA. The reasoning is that a web browser does not store data on the client device, like a modern app does (think about Outlook or OneDrive client)–those store data on the device, so you should require the device to be compliant/managed. That way, you can wipe it if you need to. But a Web browser can be protected with MFA instead of device compliance. In more highly regulated industries, you might require even web browsing to be limited to managed devices.
Hi Alex. I think I get it now (Im still trying to get my head around the whole topic!).
If you stipulate “browser” in just one policy, and if this applies to “All Users”, then this means that all users will have to reference that one policy and could therefore only login to 365 using a browser by fulfilling all of the access requirements on that one particular policy.
Yes, and in fact, whenever CA policies are evaluated they are done so simultaneously. Users who fall in the scope of each policy must meet all of the specified access controls under the specified conditions. Block always wins, so if there are two policies that have the same conditions and scope, and one is Block but the other is Grant with MFA, Block wins. Also, if you have two policies with the same conditions and scope, and one says Grant but require MFA, and another says Grant but require compliant device, then both access controls will apply. So looking at that unmanaged devices policy, I did not specify web browsers on purpose–I wanted it to be wider than just web browsers. Therefore the enrollment process for instance would still require MFA, even though that takes place in a modern app, not a web browser. I wouldn’t want someone to be able to enroll a device without providing MFA, then have a managed device (and therefore not be challenged for MFA).
Alex, can I please ask a question about Guest access.
The background to my question is primarily related to inviting external users to login to one of our company websites created in sharepoint online.
If we have setup the “Block Guest Access” in the “recommended for all businesses” policies, are there any concerns over security as it Excludes the cloud apps SharePoint & Teams? These exclusions will of course be necessary if we want people to be able to login to browse the site.
I also appreciate that these exclusions will be necessary to invite external users to become active members in Teams created on-prem.
Should we really be implementing the policy that requires MFA for Guests, without any exclusions?
The purpose of the policy “for everyone” is to block access to other apps–we generally want to allow people to be invited to SharePoint and Teams. And, you still have the option at the service level or the Site Collection level of denying external sharing for specific locations, if you want to. But there is no reason guests should be attempting login to other services, so we close those doors while leaving the essentials in place. As for the MFA for guests, I think it is a good one for very sensitive or restricted environments. But not necessary for most small businesses. If you deal in government secrets or highly confidential patents, etc., then yeah, I’d require MFA for everyone, even guests.
Has anybody noticed an issue with their conditional access policies which seems to have occurred over the last few days?
I have a couple of policies whereby the Grant Access control has “Require Multi-factor authentication” selected only, but when I open up the policies, the tick-box for this control is now empty, with the tick box purple in colour, as if it should be ticked, and when I try to exit out it says I cant and must choose something?!
I haven’t made any changes to any policies for at least a month or so.
I believe the policy is still working as I’m prompted for MFA in the right circumstances, and I’m guessing it wont be a problem if I simply tick the box again and save, but this is making me very nervous indeed.
My guess is that Microsoft have made some changes in the background which has had an effect on my policies.
I have seen the same in my tenants that I’ve been working with. Even though it doesn’t appear correctly in the browser, it appears to be enabled still in reality.
Just an update on this. I decided not to touch anything and just leave it for a few days, and hurrah, the ticks are back!
Yes, I see the same. They are definitely making some changes. Also, in the Intune portal, I noticed this week that it doesn’t report settings accurately when you are configuring certain policies, e.g. it will say “X number configurable” instead of “X configured out of Y” or whatever, like it used to.
Exceptional post and blog resource in general… It’s not often I add things as a bookmark but your site now makes the cut! I would have loved to have found this resource 2-3 years ago… I remember creating a CA policy LONG ago to block foreign countries and others were like, wow, good idea….
My struggles at our hospital is I have 40 ppl that actually use email remotely so that is easy for enabling MFA. Then, I have 180 other employees that are NOT approved to use O365 outside of our 4 walls. Thus, I’ve struggled for years now, how can I expect a random nurse who only looks at her email 2 times a week to setup MFA on her personal phone – who will NEVER even use MFA since I’ve whitelisted our IPs as a trusted location in MFA.
What I’m currently doing is creating two AD groups, one for those that are approved for remote access (MFA mandatory) and the other default AD group of NO remote access. Then if you are in the AD group of NO remote access I have that tied to a CA policy that blocks all cloud apps in all locations excepting if coming from our internal networks. I just can’t think of a better way to do this without really enabling MFA for ALL ppl…!
Any thoughts on that CA policy approach vs MFA for all? Thanks!
That seems like a decent solution given the requirements. There are some places that have resources and personnel which are very sensitive, and often those will have strict location-based access rules–only allowed to access resources from the trusted networks, and nowhere else. Think DOD, certain military/defense units, or businesses who contract with those entities. And there are probably others. If they give back the ability to have exceptions on the baseline policies I think the end user protection policy is a solid option, too. Because you would have to register for MFA, but you may never need to use it in practice, unless there was a problem (and then you’d want it to trigger anyway, as there is high chance it is not a legit logon request).
Hi Alex, the link to the guide is not working.
thanks for the heads up, link has been fixed!
Hey Alex,
I’m looking to implement the below MFA setup, but I’ve managed to get myself a little confused, hoping you can help! :)
Requirements are:
– When in an untrusted Location but on a Trusted Device – Asks for MFA
– When on a Trusted Location & Trusted Device – no MFA is required
– Untrusted Device – Asks for MFA
I assume I would need three CA policies for this, but is there anyway you can help me understand this a bit better
You would only require two policies:
1. Policy name: GRANT – Access from trusted locations:
Use Conditions > Locations > All trusted locations
Access Controls: Require MFA, Require device to be marked compliant, Require Hybrid Azure AD Join (then require ONE of the selected controls)
2. Policy name: GRANT – Access from untrusted locations:
Use Conditions > Locations > All locations, but excluding All trusted locations
Access Controls: Require MFA
This means that outside of trusted locations MFA is always required. Inside trusted locations, either MFA or a managed device would suffice to meet access requriements.
Any thoughts on how I could block access to Exchange Online from Outlook clients external to my network but still allow mobile and web access to OWA/ActiveSync via a Conditional Access Policy?
It can be done; personally I would not restrict it from a specific network but rather use managed devices as the bar to access–hybrid joined or compliant with MEM/Intune policy. What difference is it if that device is local to your network in a post-perimeter world? Think of the conditions like a filter or selector–if you pick Client apps > Modern authentications clients, and clear all the other checkboxes, you are going to be applying the policy specifically to those clients. Likewise, if you select only Windows 10 and MacOS under device platforms, you are filtering out other possibilities such as mobile.
To do what you’re asking, you would also need to select locations, and I would select all locations, but exclude the trusted locations on the exclude tab. Then just block access instead of grant access under your access control. This means Windows 10 & Mac attempting to access via a desktop client will be blocked unless they are at a trusted location (when devices are in that location this “block” policy will not apply to them).
But to do what I recommend instead would be to leave location out of the picture and just use the “grant” access controls for hybrid joined or compliant device–then it can’t just be any device that gets that access–it must be a device that you specifically know about, that you have leverage over.
Alex,
Excellent guide and I’ve been enjoying your other posts as well.
I’ve not found a way to do this, but can a CA policy be set to only allow Outlook/M365 logon days/hours (M-F, 7am-5pm)? This would be ideal for our now hybrid office staff and keep them within our HR department’s compliance requirements.
That’s a great feature request, but to my knowledge CA policies do not have a “time-of-day-fence” type of feature.