How-to setup Intune quickly (and strategically) in your environment
Update March 2023: Much of what is written here eventually became the basis for my SMB Guide to Threat Defense and Microsoft Defender. Which in turn is part of the Consultant’s Bundle. I encourage you to check it out!
UPDATE: I have updated the setup script to now be a single script, with the JSON files embedded within it. You do not need to download the JSON files separately, however they are provided for reference.
I have previously covered the benefits of using Microsoft Intune to manage devices in a more “modern” way than what is available to you via traditional GPO. So let’s talk about implementation and how you can get from point A to point B. I hear this kind of thing from a lot of IT admins and other consultants when I engage with them. They would love to learn the new tools… but they just don’t have the time.
You have seen that old cartoon of a guy chopping wood with a dull axe, right? Someone asks, “Hey guy, why don’t you just sharpen that axe?“
“Because I don’t have the time!” he replies. “Just look at all this wood I need to chop!“
You do have the time. This tool will pay you back bucket loads of time, if you could just start adopting it…
So here is what I have done. I wanted to make it even easier for you to get started with Intune, so I did you a solid, and created a few baseline policies (see footnote #1) in the form of JSON files, which you can import into your environment, using scripts that Microsoft provides freely on GitHub.
I collected these scripts and JSON’s into my own new GitHub repository, and included a “master” script entitled Setup-Intune.ps1

Literally, all you have to do is download all the files Setup-Intune.ps1 from my Intune folder to a local working directory of your choice (e.g. C:\IntuneScripts or whatever you want), launch PowerShell, and run .\Setup-Intune.ps1
You will be prompted to enter your admin user name and upon sign-in, grant permissions to the Intune Graph (one time only), and then the importing is done for you (also see footnote #2).
What is the result of running this script?
I didn’t want people coming back to me all angry, saying like “Hey, I didn’t realize that MAM would require my Android and iOS users to enter a PIN in Outlook!” or “You mean this causes my Windows 10 PC’s to reboot?!” etc., etc. Plus, there is a right way and wrong way to roll out Intune–just pressing “Go” all at once is the wrong method. So, I figure the best thing is to just import the policies, and let you test, modify, deploy, etc. from there. None of the policies are assigned to any groups by default.
Implement using the typical processes to validate user experience and make adjustments as you see fit. This means:
- Deploy the policies to a test or “pilot” group first.
- Review the user experience in that small group, get feedback, etc.
- Make adjustments as needed and roll those out
- Communicate the final experience to your next deployment ring, for example “Wave 1” which might be a slightly larger group of people
- Rinse and repeat, continue with the remaining waves / deployment rings until everyone is on-boarded
Overview of what gets built
Mobile Application Management:
- iOS App Protection Policy
- Android App Protection Policy
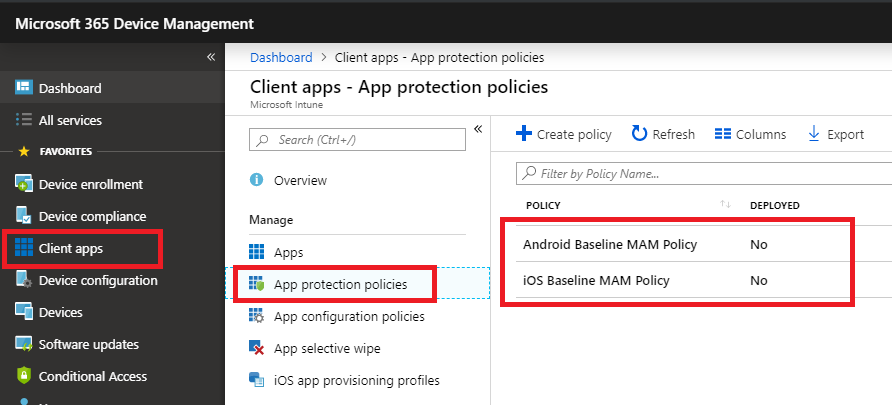
These policies exist to enable MAM, and are located in the Intune GUI via Client Apps > App protection. These are a great alternative to fully managing BYOD mobile devices.
The policies will place controls and enforce encryption on Microsoft apps such as Outlook, OneDrive, Teams, Word, etc. I chose not to restrict the ability to copy/paste/save to personal apps, although you could modify your policies to do that, if it were important to you (I find that it isn’t for many small businesses, but there may be exceptions to that for highly regulated industries e.g. Healthcare).
When you are ready to start deploying the policies to your pilot group and other rings, then you just click on a policy, pick Assignments, and assign to groups.

Mobile Device Management:
- Compliance policies for iOS, Android, Windows and MacOS
- Configuration profiles for iOS, Android, Windows and MacOS
MDM is the other side of mobility, where you control the entire device. Often used with corporate owned devices. Some notes for each below.
iOS Devices
If you plan to enroll iOS devices, you have to go setup a certificate with Apple. This is very easy to do, there is a wizard within Intune that will walk you through it (10-15 minutes tops). To do that, just click on Device enrollment > Apple enrollment and pick the big button for Apple MDM Push certificate. The cert must be renewed annually, so be sure to keep track of that icloud account, and set yourself reminders!

If you don’t plan to enroll iOS devices for full management (like if you go the MAM route instead), then forget about it–skip this section–and remember: just because the policies are there doesn’t mean you need to assign them to anyone.
Compliance Policies
- iOS Compliance policy: Block jail-broken iOS devices
- Android Compliance policy: Block rooted devices, require Google Play services and app integrity
- macOS Compliance policy: Require encryption and system integrity
- Windows 10 Compliance policy: Require firewall, antivirus and antispyware
I chose to keep the compliance requirements very minimal–anything you specify here becomes “the bar” that devices must meet in order to gain access to resources (only if you couple this with Conditional access–and you should). You are free to edit these policies and make your own selections however you see fit; this is just a “starting point” for you that is both low risk and low impact.

Compliance policies are found under Device Compliance > Policies.
Device configuration profiles
You could use Compliance policies to require a PIN or passcode on mobile devices, but I have chosen to enforce a PIN requirement using the Device restriction profiles instead. Just keep in mind, when you are working in Device configuration > Profiles, these policies do not have any bearing on Conditional access.
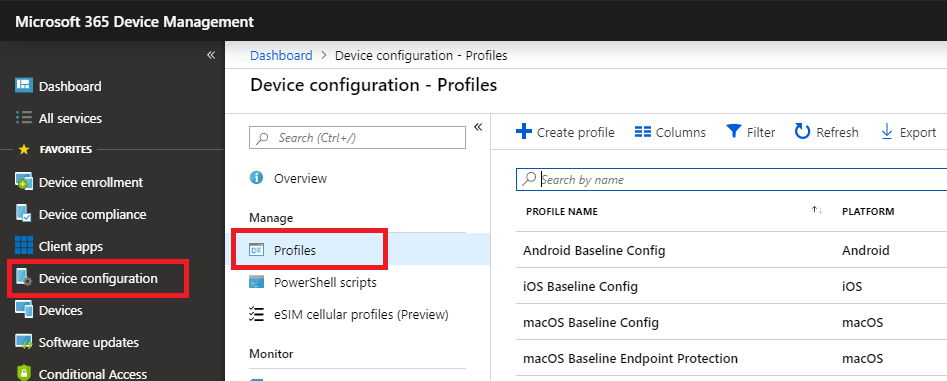
- Android Baseline Config: just a PIN requirement, 4 digits
- iOS Baseline Config: same, just PIN
- MacOS Baseline Config: just a password requirement
- macOS Endpoint Protection: enable the firewall in Stealth mode
Windows 10 configuration profiles
As with the application policies for Android and iOS, you can create device configuration profiles for Windows 10 using the Microsoft 365 admin center (Devices > policies). But you only get a limited selection of options in that portal (it is still a fine place to start–that’s where I started).
There are several notable differences with the baseline profiles you will be importing from JSON. To begin, I split the policies out by feature/function. That way, you can implement one feature at a time, and if there are any issues applying a policy, you can quickly see which devices are having trouble with which configuration settings.
Aside from an optimized config of Windows Defender Antivirus, I have also enforced the option to block all incoming traffic using the Windows Firewall, enabled Windows Defender SmartScreen and turned up the UAC settings to Always notify (don’t be afraid of it–this is critical).
We also have Application Guard in place. Did you know it is supported on Windows 10 Pro 1803 and higher (used to be restricted to Enterprise edition)?
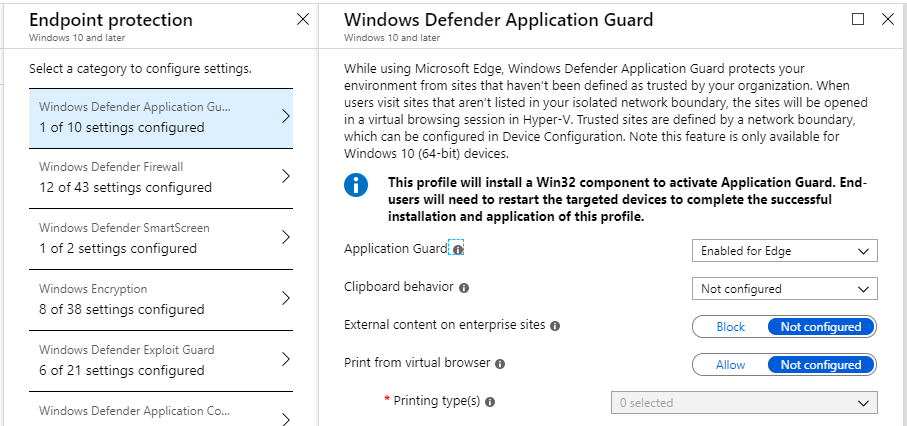
Application Guard will isolate untrusted/non-corporate websites within Edge/Internet Explorer into a virtualization container. This means that websites which turn out to be malicious (and get past your other controls) have no access to the host operating system. This setting requires a reboot. Note however: currently there is a known bug with this Intune setting causing it not to be applied–a fix is expected soon.
You will also see Credential Guard in here, which again uses virtualization to help prevent well known hacking tools e.g. mimikatz from gaining access to your secrets.
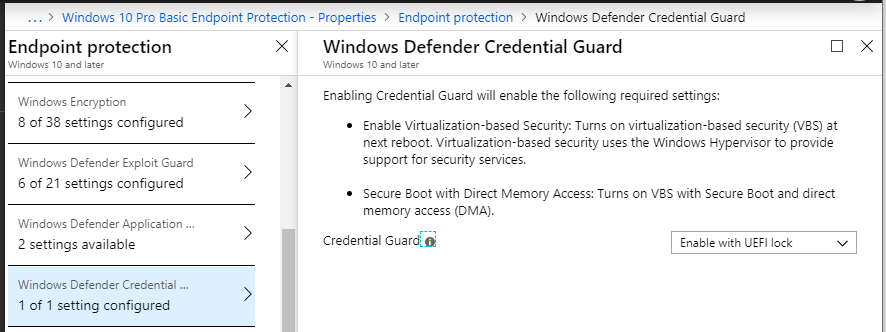
Remember: whenever settings like Application Guard and Credential Guard are turned on, they rely on virtualization. At the very least this is going to require a reboot of the endpoint, and may have some performance impacts as well. Make sure your system meets the minimum hardware and software requirements for this feature. For example, you need to ensure that the endpoints have Secure Boot and TPM enabled.
A quick description of the Windows 10 Baseline policies are below. (Request: if you think you know your stuff, and you review these and find anything missing here that you feel should be included in a good baseline configuration, please let me know in the comments or via my contact page).
- Antivirus config: This policy defines behavior for Windows Defender Antivirus, and includes several important optimization settings
- Application Guard: Isolates untrusted/non-corporate websites within Edge/Internet Explorer into a virtualization container (e.g. if a website turns out to be malicious then it has no access to the host OS)
- Bitlocker: requires Bitlocker to be enabled the key to be stored in Azure AD
- Credential Guard: Isolates Windows credentials using virtualization-based security
- Defender SmartScreen: Protects against malicious content downloaded from the Internet
- Exploit Guard: A set of intrusion prevention capabilities that help to reduce attack surface; there are two versions of this policy:
- Basic: These options can be enabled via the Microsoft 365 admin center in any version of Microsoft 365 (including Business–though I’m not 100% sure Pro is licensed for all of these features)
- Enterprise: These options go further but are for sure not officially supported on the Windows 10 Pro/Business license
- Firewall config: Turns on Windows Defender Firewall in Shielded mode (deny all inbound connections)
- Passcode requirement: Sets a default 6-digit PIN requirement for Windows Hello
- Security Center: Disables non-critical notifications from the Windows Defender Security Center
- UAC: Enables User Account Control settings
Again, test the policies out in your environment. For the most part, these are safe and even recommended as a general baseline. Noticeable impacts are most likely to come from Application Guard and Exploit Guard (especially Enterprise). The rest aren’t too bad.
Note that you can customize–for example both Defender Antivirus and Defender Exploit Guard (e.g. Controlled folder access) can be modified for specific inclusions/exclusions.

Remember that you are free to modify these however you like. I don’t care. I just want to see more people adopting the modern management tools, because it helps raise the bar, so to speak, for everyone out there.
At this time, I have not included anything for Microsoft Defender ATP (only supported with Enterprise licensing). Oh, and I know some of you will ask me about Conditional access… but those polices aren’t exposed via the Graph yet, so we can’t import them from JSON. Once they are available (I’m watching–go vote it up), then I’ll get those JSON’s and scripts added here also, to enforce managed devices, managed apps, etc.
Anyway, be sure to test all this out on a pilot group first–again be aware that there is a chance that some of the features could have impacts on the endpoints and you’ll want to be prepared to communicate them to the end-users, make tweaks to your liking, etc. Seriously, it isn’t that bad–I wanted this to be an easy place to start, not overly difficult. I hope you have fun with it, and learn some stuff!
Conclusion and next steps for you
That is really it. Go download these scripts and JSON files, get them imported into your environment, and test drive them out a little bit. I am open to feedback and improvements as well. I hope this takes some of that initial “activation energy” out of playing with the new hotness and learning some of its gotcha’s.
Hardly anyone in the SMB space is out there using this stuff, so set yourself apart and get educated. This year is going to be THE year of Microsoft 365–especially in the small and mid-sized business. Don’t be a laggard, be on time to this game. You won’t be early at this point–this stuff has been much more widely adopted in the Enterprise long ago (and is picking up legs quickly in the SMB space with the growing popularity of SKU’s like EM+S and M365 Business).
Just follow the test/pilot/production strategy as I said–and you may decide to make some adjustments. Maybe you don’t like Application Guard or something–okay, whatever, disable it for now–maybe that’s next quarter for you. But soon enough you’ll have this stuff down pat. Just. Get. Moving.
HERE is the link to GitHub again
Cheers!
Footnote #1: What about the Security baselines that Intune introduced? Well, they aren’t ready yet. Microsoft explicitly says not to use them in production. Also, without making any adjustments to the default selections on the October 2018 baselines, they follow SECCON 3, which is pretty restrictive and not a great user experience (albeit a good security baseline to aspire to). I’d like to see MS package the rest of the security configuration framework also…
I find that the policies I have included here are a great baseline for many small and mid-sized orgs. Always room for improvement, no doubt, and we have to keep an eye on the packaged baselines as they evolve. But this is enough to get you going in the right direction.
Footnote #2: By the way, the scripts save you time, EVERYtime. If you make a ton of modifications to the policies or make up your own policies, just use the export scripts from Microsoft (also included on my GitHub), and you’ll be able to modify the Setup-Intune.ps1 to pull those policies in.


Comments (32)
Wow this is really useful, thanks Alex!
Hi Alex,
Can you please remind me what extra subscription do I need to have all of these controls besides Microsoft 365 Business?
Thanks mate.
-Mario
If you have M365 Business you already have Intune, however, certain features that you can enable on Windows 10 are not supported by Windows 10 Pro/Business edition. It is also recommended to use Conditional access in conjunction with Intune, which requires Azure AD Premium P1, until MS changes the subscription (which hopefully they do). See this link for detail on what is included or not in different versions of Windows: https://www.microsoft.com/en-us/windowsforbusiness/compare
Hi Alex, thank you for lots of valuable info on your site.
When I try import script I get this error: ampersand (&) character is not allowed.
How do i get past this?
Thanks.
Not sure I’ve got enough info there to go on–Which script? The one to run (or manipulate to your liking) is Setup-Intune.ps1–is that the one you are running? That script will call on the import script, and you can see the syntax that is being used against the import script in Setup-Intune.ps1, in case you want to try importing your own JSON separately, or adding a JSON to the “master” setup script.
Great Work!
Out of curiosity, now that Security Baselines are available, do you use those now instead of individual device configuration policies? Currently if there are any conflicts between a baseline line policy and device configuration policies it needs manual remediation (no inheritance, priority or group policy like behavior here!)
Also, do you include the conditional access policies in your script? eg: you have MAM policies and device configuration baselines, so do you have the appropriate conditional access policies for corporate owned and byod owned devices?
I haven’t been brave enough to deploy the security baselines in production yet. The first time I piloted them there were several major issues. At first it bricked a laptop on me. Got over that hump. Then, Teams app dll errors and some other stuff. But that was back when it was still preview. I haven’t deployed the latest one. Also I noticed that a lot of the items in there are actually Windows 10 Enterprise features. So if you took the time to comb through and disable the items you didn’t want, clean it up and so forth, test, etc., then I suppose that would work. But I should probably play with them a bit more before I render an opinion. Would be nice if there was a picker for Windows 10 Pro/Business subscriptions vs. Enterprise, and they fold in the items that are most appropriate to your subscription. Also I read back when these were first launched that the baselines mimic SECCON3, but I would like to see a selector for others also like SECCON5, which they recommend for typical information workers, where 3 is more sensitive and restrictive.
As regards Conditional access policies, they are not yet exposed via the graph. You could vote this feature up, but based on the latest update in July, sounds like they should have a public preview date soon. As soon as it is possible, I will be using this, for sure.
This is a great resource! Thanks Alex!
One question, is there any conflict or things to be aware of if I have already add the scripts from your Windows 10 Best Practices scripts to Intune?
Thanks.
There will be some overlap. This was meant more as an intro to Intune and fast on-boarding. I have policies that are specific and separated out based on function (e.g. a BitLocker policy, a Defender AV policy, etc.), whereas all of those are bunched together in the Windows 10 security profiles. If you are using the security profiles, you don’t have to turn on the individual policies that are imported that pertain to Windows 10. Everything is imported without being assigned to anything so there shouldn’t be an issue there. Simply do not assign the ones you don’t need.
I would also add the auto sync OneDrive option in here:
New Configuration policy > Administrative Templates > Search for ‘Use OneDrive Files On-Demand’ setting and enable it;
Search for: ‘configure team site libraries to sync automatically’ and enable it with the desired teamsite settings;
Search for: ‘silently sign in users to the OneDrive sync client with their Windows credentials’ and enable it.
Yes, I have outlined that process here.
Noice.
Hi Alex,
when I run the either the new or previous script as admin, I also get the ampersand error. Please see below of the copy/paste.
The two scripts are in c:\intunescripts
PS C:\IntuneScripts> .\Setup-Intune.ps1
At C:\IntuneScripts\Setup-Intune.ps1:144 char:19
+ Sign up
+ ~
The ampersand (&) character is not allowed. The & operator is reserved for future use; wrap an ampersand in double quotation marks (“&”) to pass it as part of a string.
At C:\IntuneScripts\Setup-Intune.ps1:171 char:190
+ … ata-ga-click=”(Logged out) Header, go to Features”>Features <span cla …
+ ~
The '→Customer stories <span cla …
+ ~
The '→Security <span cla …
+ ~
The '→Explore GitHub <span cla …
+ ~
The '→Learn & con …
+ ~
The ampersand (&) character is not allowed. The & operator is reserved for future use; wrap an ampersand in double quotation marks (“&”) to pass it as part of a string.
Not all parse errors were reported. Correct the reported errors and try again.
+ CategoryInfo : ParserError: (:) [], ParseException
+ FullyQualifiedErrorId : AmpersandNotAllowed
PS C:\IntuneScripts>
Never mind, the download was incorrect. Although it saved it as a ps1, it actually dowloaded a web page.
Hi Alex,
Thank you for all your guides they’re extremely helpful in simplifying a lot of the Microsoft unneeded jargon. I have a question regarding the exporting/importing of policies.
I’ve been trying to research if there a way to export information from 2 parts of Intune (Microsoft Endpoint Manager)
– Apps > All apps
We’ve created a policy here we’re using to install “Microsoft 365 Apps for Windows 10”
– Policy > Policies for Office apps
We’ve created a policy here which applies settings to the Microsoft 365 Apps (in particular Outlook)
Thus far it seems the exports don’t appear to be capturing these parts of Intune and if we were able to export / import these it’d be super handy.
Thanks again,
Thomas
Yes, you should just refer to the original here–on github there are these Intune samples, and you will find export/import scripts for various things including applications as well as app config policies. https://github.com/microsoftgraph/powershell-intune-samples
Is it just me or has the Setup-Intune.ps1 script broken?? I get the below error hmmm
Adding MAM policies for mobile devices…
Response content:
{
“error”: {
“code”: “BadRequest”,
“message”: “Request not applicable to target tenant.”,
“innerError”: {
“date”: “2020-07-21T21:23:06”,
“request-id”: “681c3270-0796-4f46-ac10-37128f94c064”
}
}
}
Add-ManagedAppPolicy : Request to https://graph.microsoft.com/Beta/deviceAppManagement/managedAppPolicies failed with
HTTP Status BadRequest Bad Request
No there have been some issues with the service. I have had similar things happen, then just waited, ran later, and it goes through fine.
Hi Alex,
The Import-Applications.ps1 is giving all errors when you try to import Android Apps. All other scripts and JSON import/exports are working find but this isnt. You know if there is a fix for this?
MDM Application ‘Managed Home Screen’
Response content:
{
“error”: {
“code”: “BadRequest”,
“message”: “{\r\n \”_version\”: 3,\r\n \”Message\”: \”An error has occurred – Operation ID (for customer support): 00000000-0000-0000-0000-0000000
00000 – Activity ID: f84c8843-e294-4d09-8a1c-4b5751d61e94 – Url: https://fef.amsub0502.manage.microsoft.com/AppLifecycle_2007/StatelessAppMetadataFEServ
ice/deviceAppManagement/mobileApps?api-version=5020-06-22\”,\r\n \”CustomApiErrorPhrase\”: \”\”,\r\n \”RetryAfter\”: null,\r\n \”ErrorSourceService\”
: \”\”,\r\n \”HttpHeaders\”: \”{}\”\r\n}”,
“innerError”: {
“date”: “2020-08-08T22:08:27”,
“request-id”: “f84c8843-e294-4d09-8a1c-4b5751d61e94”
}
}
}
Add-MDMApplication : Request to https://graph.microsoft.com/Beta/deviceAppManagement/mobileApps failed with HTTP Status BadRequest Bad Request
At C:\PowerShell\intunetooling\Import-Applications.ps1:357 char:1
+ Add-MDMApplication -JSON $JSON_Output
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [Write-Error], WriteErrorException
+ FullyQualifiedErrorId : Microsoft.PowerShell.Commands.WriteErrorException,Add-MDMApplication
This would be a question for the original script repo–which is by MSFT (the intune samples for MS graph).
Hi Alex,
Thanks for the reply, turns out this was because the tenant wasn’t actually licensed for intune as I thought it was.
Cheers
Alex, your guides are very useful and easy to follow. I think you made deploying M365 dummy proof. The scripts are made for every demand. All I had to do was filter out the stuff we don’t need. Thanks for making this!
Alex, great work and thanks so much for sharing! I just noticed that it looks like the import/export of CA policies is now available. https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/howto-conditional-access-apis
Yes, and I have a post on using PoSH to deploy CA as well.
Hi Alex,
Great work, i was fiddling around with these scripts the past year, and saw you handy work. So i stole it :P What i did though was make it more readable for the less devine engineers.
. ./APP_WIP_MAM.ps1
. ./APP_WIP_MDM.ps1
Add-MDMWindowsInformationProtectionPolicy -JSON $APP_WIP_MDM #OK
Add-WindowsInformationProtectionPolicy -JSON $APP_WIP_MAM #OK
Instead of 6199 lines, i an down to 1035.
Cheers and thanks for the great work.
In your article you mention being able to import custom policies via exported JSON in place of the ones you configured in the original IntuneSetup.ps1 file. I have tried just copying and pasting a custom JSON file that was made in Intune and then exported in place of one of the base ones you listed. This does nothing but provide errors as a result. Can you provide any insight on how I could accomplish this function.
The script has been changed slightly since the first publishing, so that you do not rely on separate JSON files, and all the JSON is embedded into the single script. If you are replacing the JSON that is in the script (they are each represented in a variable), be sure to remove lines from the JSON you are bringing in which are extraneous, or refer to information about that tenant specifically. For example, there may “version” information, and date created/modified, etc. Notice which values are in the JSON that is there currently, you would want to remove the extra lines from your own replacement.
Thank you so much for your reply Alex. Looks like removing the extraneous/tenant information worked for allowing the script to run successfully. Just out of curiosity is there a way to add ADMX/Group Policy Scripts into the main script. I know there are other scripts that will allow to perform just that action. Was just wondering if there was a way it could be integrated in the intunesetup.ps1 to make it a one stop shop for Intune setup.
I have struggled to get the ADMX working in line with the script. The closest resource I found for ADMX import is still kinda janky. It puts each object into a folder path/tree. So like Computer configuration \ Windows components \ etc. down at the level of the object will be a small JSON. I don’t want to have to zip up a folder tree and have to unzip it just to import the stuff. I want some other way of describing the path to the policy object. But I haven’t found it yet. If you know of any other scripts out there that will import ADMX without relying on folders, let me know!
Hi Alex, Thanks you for these scripts. They are really useful for CSP. Is there one available for importing the ADMX templates that get exported?
Thanks
Rob
I really wish there was, but so far no. The samples repo that MSFT provides does not include the ADMX stuff yet. I do not know what is taking them so long. There was another MVP who figured out how to do this in an “unsupported” way that is also a bit clunky. What happens is that when you run the export it creates a folder structure that represents the path to the config inside the ADMX (e.g. Computer configuration\Windows Components\etc.) and then the setting name is the name of an XML file and the setting is listed inside that file as JSON. It’s insane, and not super practical; I am hoping MSFT updates their samples repo soon so that we have a simple export/import like we have with everything else.
Looks like the AzureAD module is/will soon be deprecated? Will these be updated to support Graph?