Leveraging Conditional Access to enforce either MDM or MAM–user’s choice
In some circumstances, you might want users to have their choice:
- Use the native mail apps and have their mobile devices managed via Intune MDM, OR,
- Use a managed application such as Outlook on their own personal devices, and opt out of full device management.
The catch is, they must go down one or the other path to gain access to resources. So as an admin, you know that their device will either show up in your inventory and be properly managed, or, that the user will be protected using the MAM policies from your Microsoft 365 subscription. Win-win.
Previously, I described this scenario in another post, as an alternative to straight up requiring managed apps at all times. I promised to show another option that gives us a bit more flexibility between MAM and MDM, so here it is.
I will ask you to configure three policies:
- Require either MDM or MAM for access to Office 365 Exchange Online and SharePoint Online via mobile devices
- Require MDM or MAM for access to Exchange Online via an EAS client
- Block legacy client applications from Exchange Online
Policy # 1: Require either MDM or MAM for mobile access to Office 365 Exchange Online and SharePoint Online
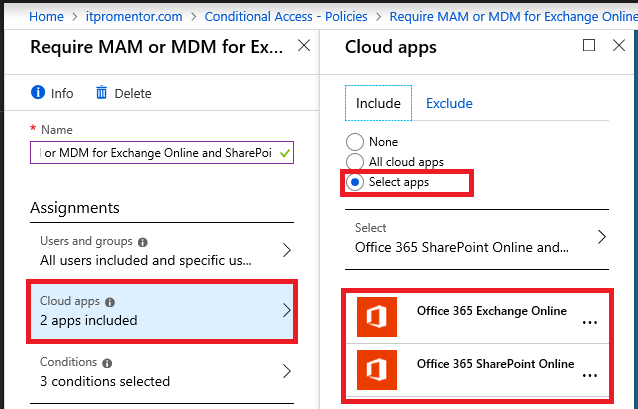
From the Azure AD portal, go to Conditional Access and create a new policy. Name it something descriptive like require MAM or MDM for Exchange Online and SharePoint Online. Choose All users, or scope it to a subset of users. I usually exclude at least one admin account in there, as previously described in other examples. Select two Cloud apps specifically: Office 365 Exchange Online and Office 365 SharePoint Online–these apps are the ones worth protecting, with online locations for storing company data. (Note: With Teams there really is only one client to choose from, and all the shared Team files are stored in SharePoint anyway.)
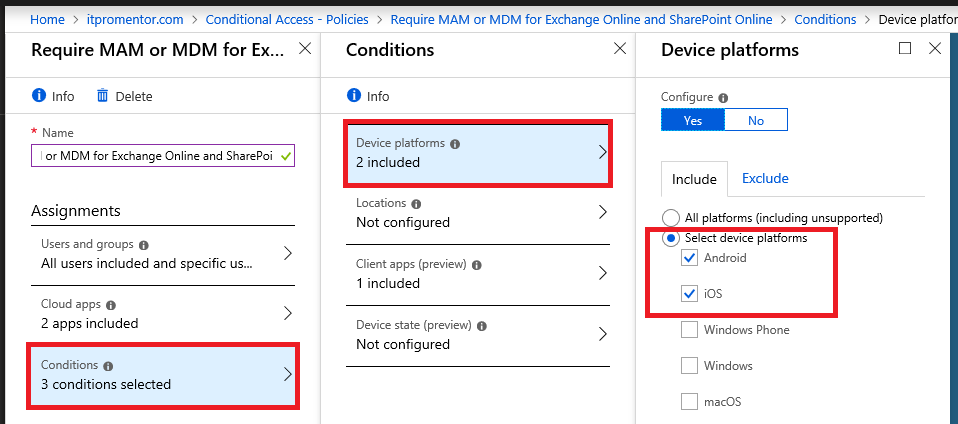
For Conditions, under Device platforms you need to select at least Android and iOS (this policy is scoped to mobile devices).
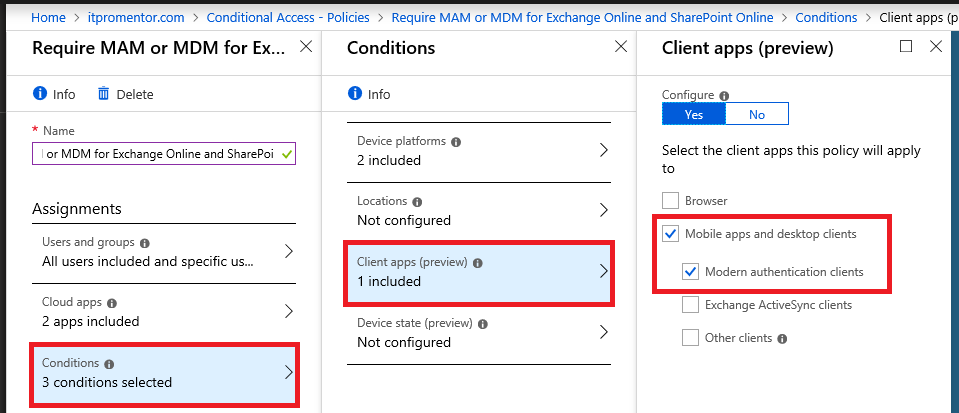
The second condition is Client apps, choose Mobile apps and desktop clients, and under that, Modern authentication clients only.
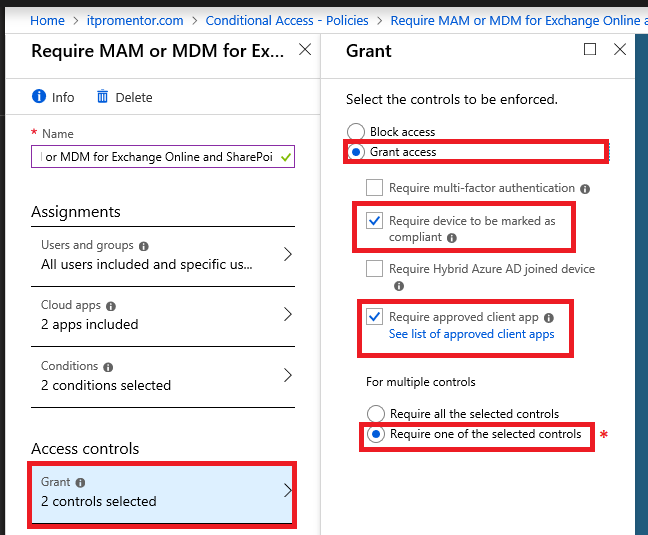
Now, here is where the magic takes place. Go to Access controls, choose Grant access, and select both Require device to be marked as compliant, AND Require approved client app, BUT, be sure to pick Require one of the selected controls. This is where you get two possible paths–meeting either will grant access.
The effect of choosing the other option here, to require all controls, would mean that devices would be required to become both MDM and MAM managed. Some orgs may want to do this, but our goal here is to provide options for BYOD scenarios, not to create strict policies for corporate-owned devices.
Policy #2: Require MDM or MAM for access to Exchange Online via an EAS client
For some odd technical reason (for which I still haven’t found a super great explanation), Microsoft does not support configuring a Conditional access policy for Exchange ActiveSync alongside of other applications or conditions, so you need to configure this separately to be “officially supported.” It looks like this:
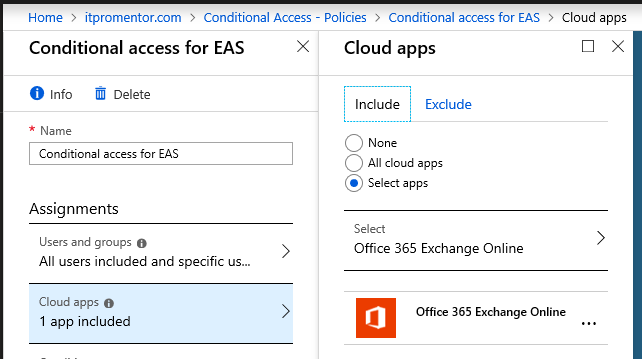
Name a new policy something like Conditional access for EAS. Again I would apply this as liberally as possible across the user base, but we should only select Office 365 Exchange Online in this case under Cloud apps, to be supported as a policy scoped specifically to EAS clients.
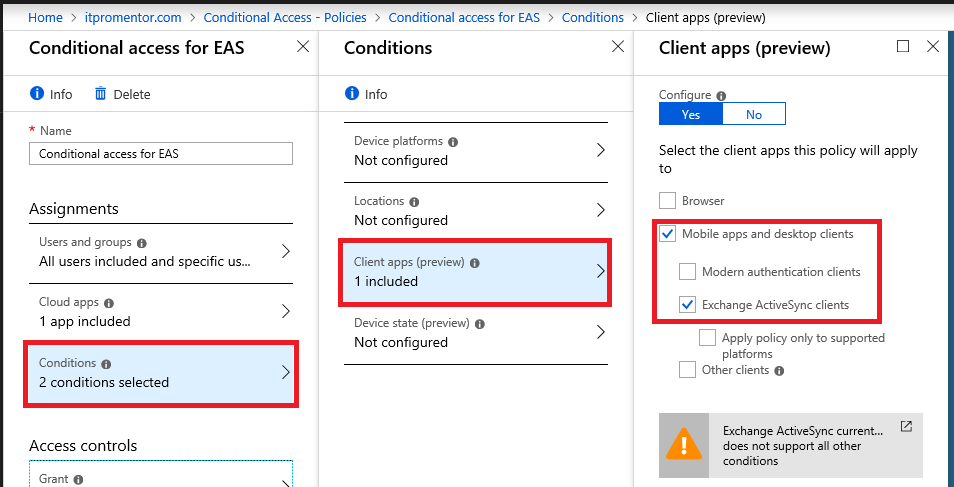
Then under Conditions > Client apps (which is the only supported condition in this case), pick Mobile apps and desktop clients, as well as Exchange ActiveSync clients.
And last: the Access controls will be the same as we saw above, so just replicate that same selection again.
Policy #3: Block legacy client applications from Exchange Online
Last, you may want to take one further step to block access to older legacy applications. For instance IMAP clients, etc. Only implement this policy if you have removed all legacy applications from your environment, and are using newer, Office 365 subscription-based desktop and mobile apps.
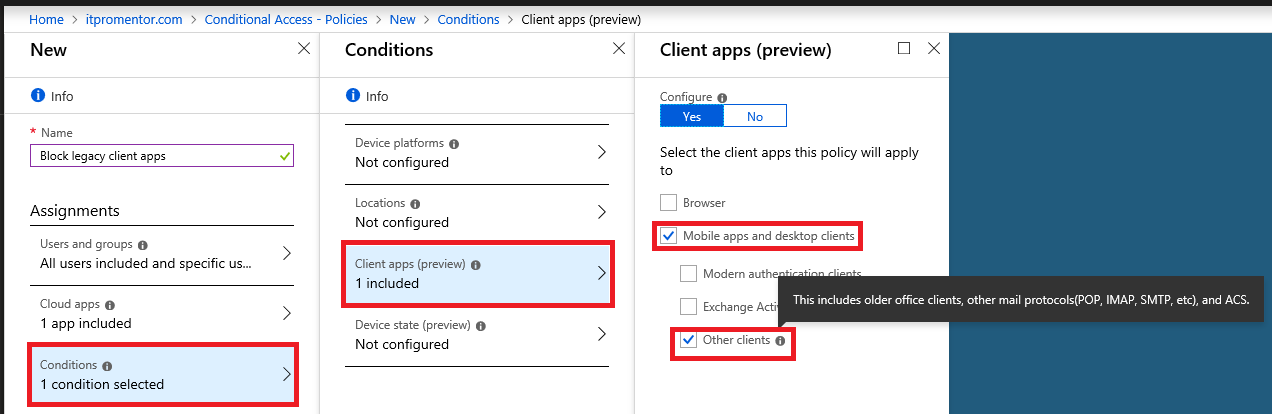
Name the policy something like Block legacy client apps from Exchange Online. Again we only need to select Office 365 Exchange Online under Cloud apps. Under Conditions > Client apps, choose Mobile apps and desktop clients, and Other clients underneath that.
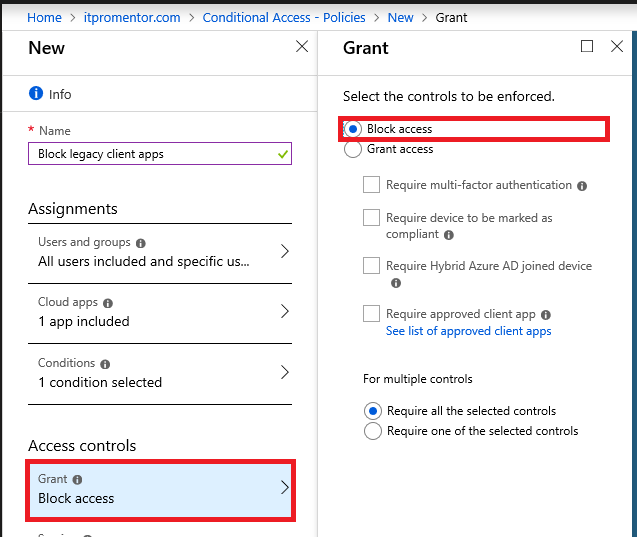
Access controls will be different this time: just choose Block access.
Save selections and Create the final policy.
Test it out!
Now, when a user goes to add an email profile to the native mail app on their phone, for example, they will be required to register their mobile device, and run through the process to become enrolled for MDM. See the screenshot below as an example.
Otherwise, a user could choose to add the Outlook app to their device, and thereby they would be granted access without the requirement to enroll for MDM. This is perfectly acceptable, as long as you have already configured your MAM policies. Either way, users will be protected either via MDM or MAM, depending upon which application experience they prefer.




Leave a Reply