PSA: Careful with MAM – there might be more to it than you think
I have written extensively on Mobile Application Management (MAM), as an alternative to Mobile Device Management (MDM). When implemented properly, it is the perfect solution for protecting company data on unmanaged devices (e.g. BYOD situations).
But therein lies the rub. You need to implement it properly. I can’t blame you if you have it wrong, either. Because Microsoft’s own documentation does not always reflect the reality. Here is a case in point: go to this link and read the following (screenshot included below):
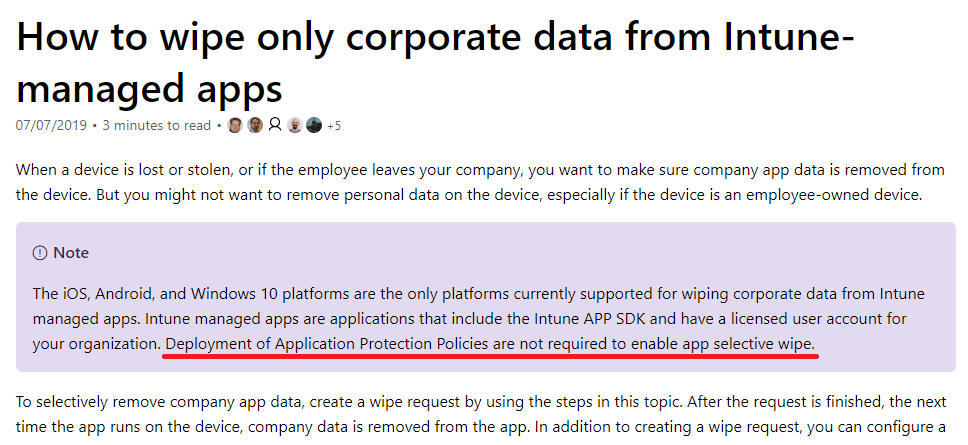
The relevant line reads, “Deployment of Application Protection Policies are not required to enable app selective wipe.”
Oh really? Because that is not my experience. Go ahead and test it–you will find that the exact opposite is the truth. So either this is a typo, or something has changed and the document hasn’t been updated yet.
App protection policies are what enables MAM, really. They are found under Client apps > App protection policies.
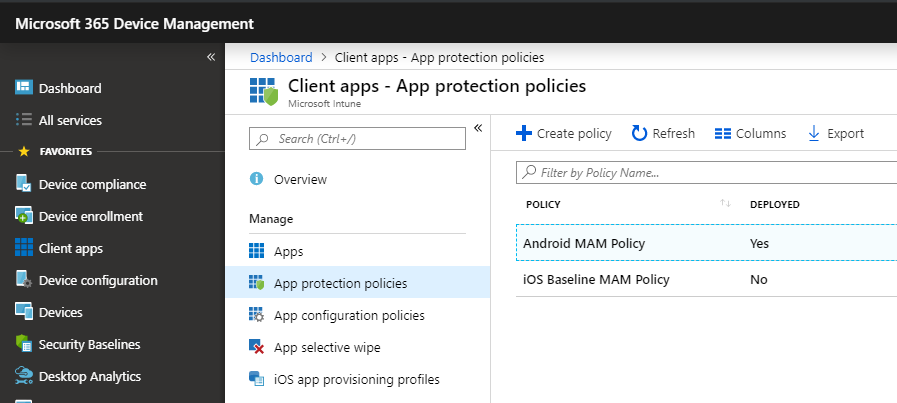
The reason this gets confusing for some people is that they will read my guide on Conditional access, and implement my recommended Conditional access policy for iOS and Android, with the access control called “Require approved client app.” Basically the policy says that if you want to access corporate resources, then you have to use the “approved” (read: Microsoft) client apps. E.g. Outlook, not Apple Mail for instance.
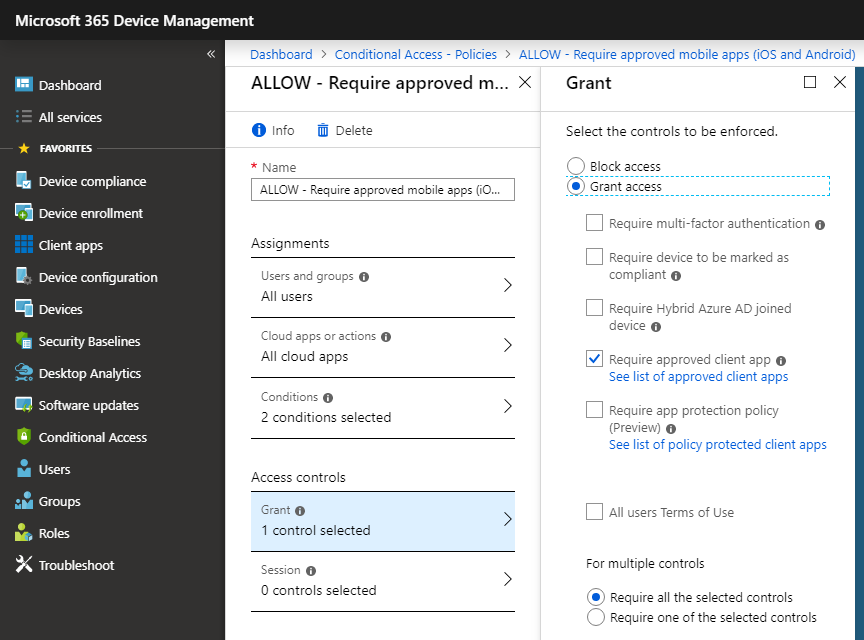
Now if you enable that Conditional access policy, it will have the desired effect: you must use the Microsoft apps at that point. But, if you fail to setup an App Protection Policy on top of it, then you will not be able to issue remote wipe requests against those devices, which pulls back the data within the app.
The whole point of managing the application rather than the device is so that you can gain control of the corporate data being presented through that client application without touching the device itself. But you don’t have that control via Intune without applying an App Protection Policy.
Configuring your MAM policies
For some quick guidance on this, just note that the minimum required configuration to enable the remote selective wipe feature would be to have a protection policy that targets the apps you are trying to protect (e.g. Outlook, etc.), with Data protection settings that at least require the app data to be encrypted, like this:
Minimum Data protection settings for enabling app selective wipe:

I could likewise leave the access requirements totally wide open, and still be covered with remote selective wipe.
Minimum Access requirements:

Now that would be the minimum recommended settings to get your remote wipe working. You can initiate one of these wipes from Client apps > App selective wipe. Simply click + Create wipe request and then choose a user and device from which you would like to wipe corporate data.
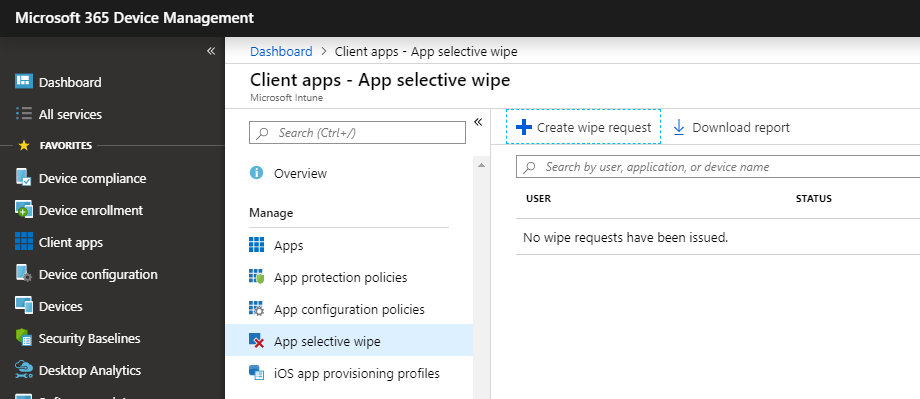
If you do not target your iOS and Android devices with an App protection policy, you will find that these devices don’t even populate for the selected user. If you previously had an App protection policy applied, but since removed it, the devices will show up in here but the wipe requests will not succeed, and it will just sit in a pending state indefinitely.
Data protection for sensitive businesses
If you have more stringent access control requirements due to the sensitive nature of your business data, then you may want more restrictive options, like these:

Here we block data outbound from corporate apps, disable backup, and disable copy/paste except within the managed applications. OneDrive and SharePoint are acceptable locations to save data, but nowhere else. Likewise for Access requirements, you might enforce a PIN or biometric:
Access requirements for sensitive businesses:

Note that when you dial up the protection level, it is going to have a user-facing impact. Not going to lie to you: not everyone is fan of it. Being prompted each time you open the app, even just for a biometric, can feel annoying. And, you may run into some instances when that copy/paste/export restriction can really ruin your day. But, if you deal in sensitive data with lines of red tape and regulations all around it, these may be the right protections to have in place.
If that doesn’t describe your business, and all you want is the ability to remove data from a lost/stolen/terminated device, then the minimum settings may be all you care to have.
So there you have it. Don’t neglect the other half of the equation–the Conditional access policy is not enough on its own. You need the App protection policy to round out the picture, even if its only there to provide encryption of the app data.


Comments (5)
Good read thank you for sharing. This was a recent gotchya for me as we were doing an implementation of both MAM and MDM and wanted to “require approved app” for Outlook. With our MAM policies we wanted to have more control than we did with our MDM policies when it came to app protection. In order for users to get the right app protection policies and to be able to wipe Outlook we had to be sure to push the app (iOS store app) and put in the configuration key (IntuneMAMUPN, String, {{UserPrincipalName}}).
Hi Alex
Not sure if you, or any other readers have come across the same recent experience I have had with this topic…. In the last 24 hours, I ticked ON “Require app protection policy” in an App Protection policy that we’ve had running for a few months now, which already had just the “Require approved app” ticked on. The policy had 12 “Targeted apps” selected.
After doing so, when testing with a Managed iPhone, I found that 6 out of the 12 apps would no longer load with a message saying “you can’t get there from here…. it looks like you’re trying to open this resource with a client app that is not available for use with app protection policies……….”.
And then rather ironically, after de-selecting “require app protection policy” and trying again, the apps DID load, along with an initial message saying “your organization is now protecting its data in this app. restart the app to continue.”!
Apps that loaded ok when require app protection was ticked on were::
Word
Excel
OneDrive
Planner
PowerPoint
OneNote
and those that failed when require app protection was ticked on were::
Flow
Power BI
Skype for Business
SharePoint
Teams
To Do
Hi Alex
I’ve found that TEAMS IOS client doesn’t work with conditional access if you check both settings, managed app and app protection, but it does if you only check app protection.
Have you heard about this issue?
You will not want to enforce the control for app protection, just “require approved client app.” Yes, Teams is not supported yet for that access control.
Thank you Alex