Removing local admin: a game of compromise (and some tips and tricks)
Look, I am a realist. Yes: from a security perspective it would be ideal if we could take away local admin privileges on every corporate owned Windows 10 workstation. But that still isn’t very easy to do for many organizations.
Some orgs do need to maintain a bit more flexibility, with users able to install new app packages as required. Some Line of Business apps also will claim not to support removal of local admin. (Although, I usually find they are bluffing, and when pressed can often explain the folder permissions and/or registry changes that would be required to run without local admin).
Nevertheless, there are certainly barriers that make this a difficult path in some cases. But Microsoft has a more pragmatic approach to this problem these days. They even publish a continuum of various Windows 10 security configuration profiles, intended for the Enterprise.* Removal of local admin is part of their “High” security profile. But we also have “Enhanced” security as an option, and this is a good starting place for many orgs who don’t know where to begin, but need a solid baseline.
*ASIDE: Some of the settings contained in these profiles are not compatible with the Business edition of Windows 10, or even E3. For example, the security profiles all call upon Microsoft Defender ATP. This is used to evaluate threat level on the device, and deny access to risky devices using a compliance policy. That is one way to mitigate the need for local admin (albeit expensive, and still not perfect). Inspired by these profiles, I released my own version of this framework which IS compatible with Business and E3 editions, and does not rely on Defender ATP.
Enter Exploit Guard
Another mitigation that we have access to, even in the Business subscription, is Exploit Guard, including Attack surface reduction and Controlled folder access. These are sub-features of the Microsoft Defender suite, and all of the official MS docs describing them still say Windows 10 Enterprise is required to use this feature, but the Microsoft 365 Business service description confirms that it is one of the Windows 10 Business security features that is included with the Business SKU.
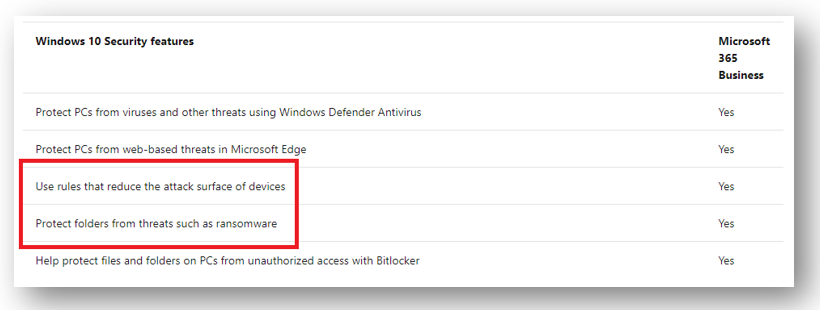
Granted, you have the best experience with these features in E5, because of its tight integration with Microsoft Defender ATP–there you get advanced management features including monitoring, analytics, workflows, advanced hunting, etc. While these aren’t part of the Business or E3 editions, you can still enable the various rules in either Audit or Block mode.
You can find these settings in Intune. If you navigate to Device configuration > Profiles, create a new profile for Windows 10, and choose Endpoint protection. Under Microsoft Defender Exploit Guard you will find the settings.
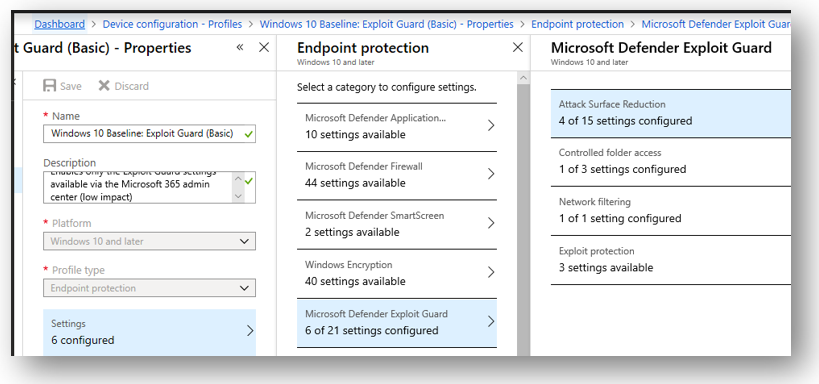
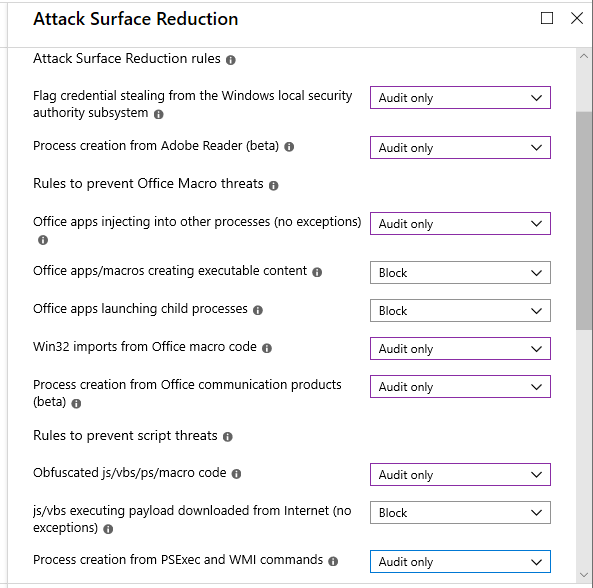
Attack surface reduction
Attack surface reduction will allow you to either audit or block certain actions that are often associated with malware and zero-day exploits. For example, preventing Office apps from launching child processes.
If you want to see what the impact will be, you can run these in audit mode for a few weeks first, and watch the event logs on your workstations. Just open Event Viewer and filter for Event ID 1122 in the Microsoft/Windows/Windows Defender/Operational log.
If you do find that you have a line of business app, or some monitoring / security agent that requires an exception to ASR, you can add exceptions (scroll down).
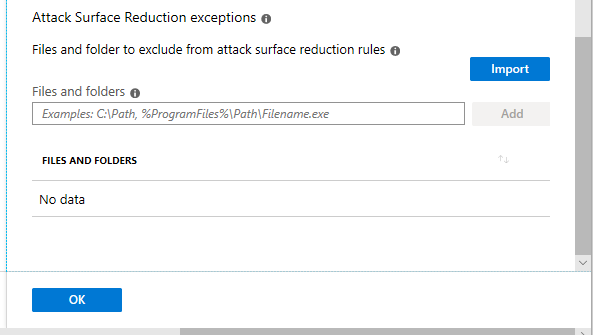
Controlled folder access
Especially useful in thwarting ransomware, Controlled folder access is another feature of Exploit Guard that watches system and other custom-defined folders (e.g. OneDrive sync locations); its purpose is to prevent untrustworthy and unknown apps from making changes or writing data to these locations.
Enabling the feature also requires that you have enabled Windows Defender Antivirus Real-time protection. You could accomplish this either using a Windows 10 Device restriction profile, or by using a compliance policy (under System Security).
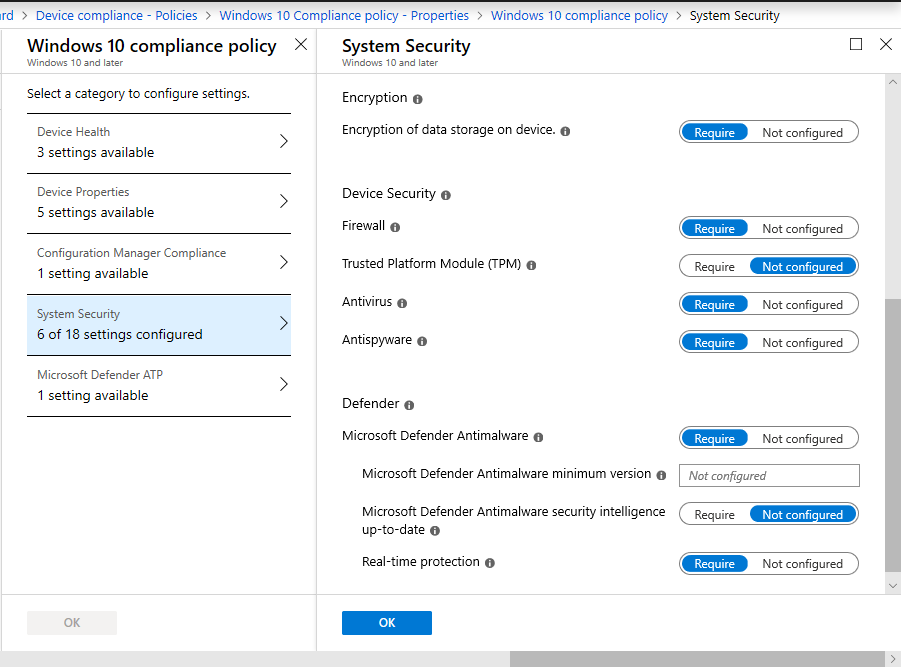
With that in place you can enable Controlled folder access back in the Device configuration > Profiles > Windows 10 / Endpoint protection policy, again you can Audit only or Enable. As well, you will be able to specify paths to executables that are allowed to make changes (trustworthy/well known apps are included automatically). Last, you can add other folders (such as OneDrive sync locations) that should be protected, along with the default folders.
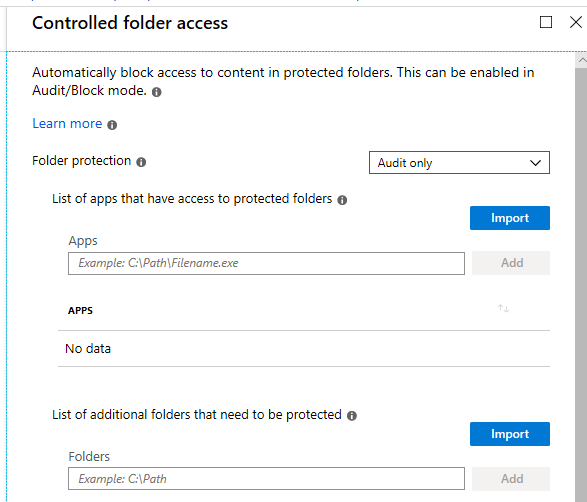
If you choose to audit the policy (recommended if this is your first time enabling it), again you can monitor the event logs for event ID 1124 under Microsoft/Windows/Windows Defender/Operational.
Network protection
Even though this feature is not called out in the Microsoft 365 Business service description, it is included with Windows 10 Pro, as long as Defender AV Real-time protection is also enabled. Network protection will basically just monitor outbound connections, and block any that attempt to contact known bad domains and IP addresses.
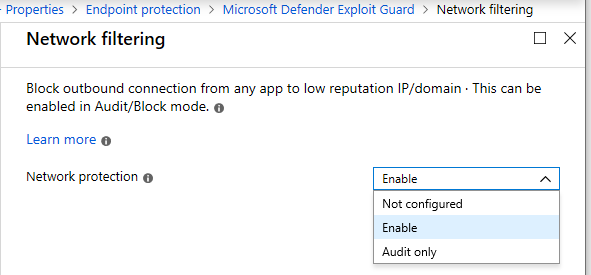
While I usually find exceptions will be required for the other pieces of Exploit Guard (e.g. I have even found some hiccups with MS apps like Teams), I have so far not had any issues just enabling the Network protection feature. Still, the audit events to watch for would be ID 1125 (and 1126 if you have it enabled in block mode).
All of these protections cannot really compare to completely removing local admin privilege (these are different things and stand on their own), but they do help us to limit our exposure, and mitigate risks. They are especially valuable if we cannot take away those privileges, and they still hold value even if we can. Plus, they can provide excellent audit data for piecing together ‘what happened’ in the event of a breach or ransomware infection.
User Account Control
Whether or not you ultimately take away local admin, you should be implementing User Account Control. I would consider this a mandatory/typical corporate security baseline. With UAC enforced, Windows will allow the local user account to run in “Standard user” mode, and only prompt to elevate the session to “Admin mode” when required. I am sure you are familiar with these prompts.
So many admins were scared away by this feature when it first came out in Vista. Since then it has been common practice for admins to disable it, either when troubleshooting issues, or just because they think it will prevent issues and remove question marks. But that’s a mistake. Many of the early days headaches were due more to the “goof” of Vista than UAC.
Within Intune, you can find the UAC settings by creating a new Device configuration profile, Windows 10, Endpoint protection: Local device security options > User account control.
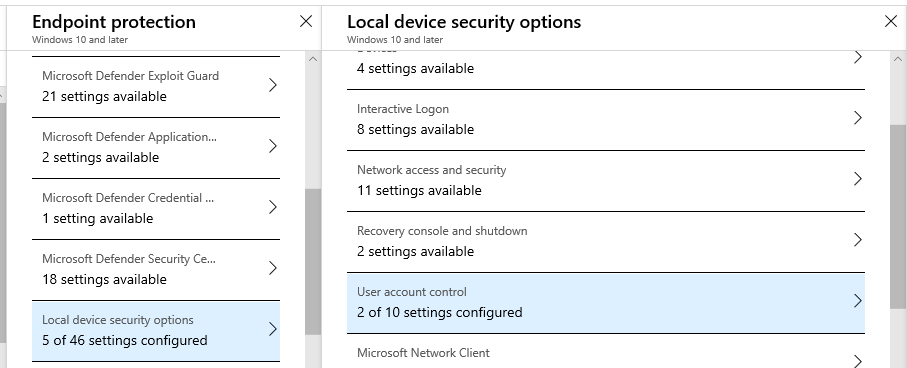
Here is what I recommend as a minimum.
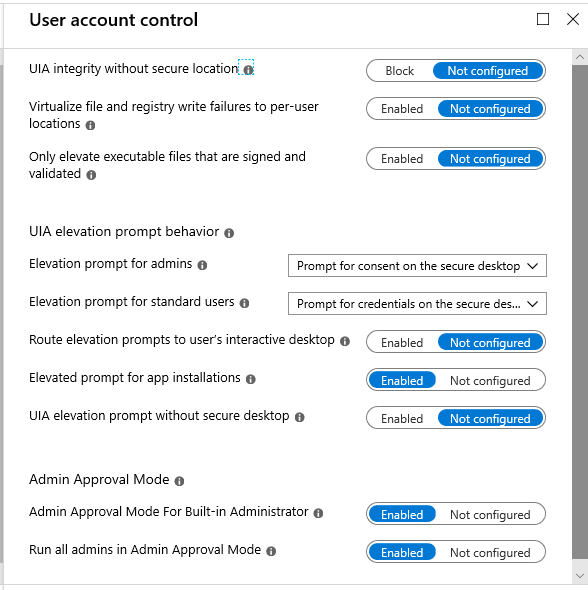
Microsoft’s recommended baseline is actually more stringent than this, and denies elevation requests automatically for standard users. However, what I like to do is Prompt for credentials on the secure desktop. The secure desktop (rather than the interactive desktop) is more jarring and is more effective at snapping your attention and allowing you to focus on the question–so you’re less likely to dismiss it outright.
If you do take away local admin and users are running as standard users, then I do one more thing in conjunction with this: I create a “Desktop admin” account that has no special roles or privileges in the tenant (it is not a global admin for instance), but we place this account as an additional local admin on any Azure AD joined device. This can be accomplished from Azure AD > Devices > Device settings.
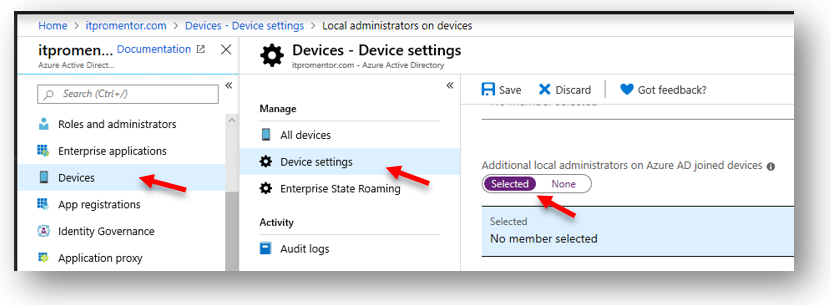
The password for this account is known by the admin, and by another trusted technical contact (or two) at the organization. If and when a system change or update or other software package is required (and the action is not being accomplished via central administration with Intune), then the user has an option to get one of the designated people to assist them with completing the elevation request.
There is some training that goes with this change for end users and the technical contacts. If they are suddenly prompted on the secure desktop and they weren’t trying to make a change or install software, they should not allow the elevation to continue (and they should notify IT immediately). With the lack of local admin and the secure desktop credential prompt in the mix, there is more activation energy required to make the change happen, so users really have to be sure that they want to continue (they won’t just click whatever makes the interruption go away the fastest).
Note that even when taking away local admin privilege and having UAC in place, Microsoft Defender Antivirus and Exploit Guard and other protections still remain useful. Not only for the audit log information, but also because some of the potential malware actions would not trigger a UAC prompt as they are relying on other system and application processes to do their work. So you can and should use these features in conjunction with one another.
And of course, all of this and more is detailed in my recent product, the Windows 10 Business Secure Configuration Framework.


Leave a Reply