Windows Hello for Business: Azure AD Join vs. Hybrid Join
Windows Hello for Business replaces a traditional password when signing into your workstation, with a stronger two-factor authentication. One factor being some kind of local gesture such as a PIN, fingerprint or facial recognition, and the other being a key or certificate that is bound to the device itself.
When you do as you’re supposed to, and join PC’s to Azure AD rather than a local / legacy Active Directory, Windows Hello for Business is setup for you auto-magically. No special infrastructure or certificates, no federated services or other junk. It just works.
This is on by default for Microsoft 365 subscriptions that include Intune. So when a computer is joined to Azure AD and enrolled for MDM, one of the first things that a new user will be prompted to do is setup their Hello PIN on their Windows 10 device.
If you go look in the Intune portal, you will find some settings for controlling Windows Hello for Business under Device enrollment > Windows enrollment > Windows Hello for Business.

That’s all fine and good… unless you aren’t doing as you’re supposed to. If you are one of those poor souls still joining their PC’s to a traditional Active Directory domain, then you’re going to run into a problem with these default Hello settings when you go to enroll your “hybrid-joined” devices for MDM.
While a “hybrid-joined” user will still get prompted to create a PIN, they will immediately discover that they cannot actually use it. They might see a message like:
Windows couldn’t sign you in.
Your credentials could not be verified.
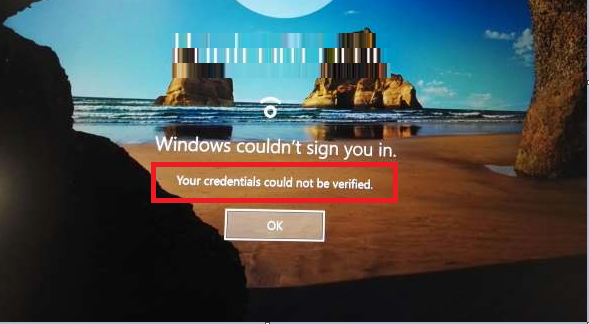
The same thing will happen for facial recognition or fingerprint. Bummer.
The reason is because Windows Hello for Business is disabled by default on domain-joined computers. If you want to setup Windows Hello for Business in a hybrid environment, there is a whole bunch of technical stuff required before it’s ready to rock. And it’s not a breezy process, either.
There are actually two different methods for configuring Windows Hello for Business in a hybrid environment:
- Hybrid Azure AD Joined Certificate trust deployment (legacy)
- Hybrid Azure AD Joined Key trust deployment (preferred)
A certificate trust deployment requires you to have AD FS setup in your environment. So this is not a popular option as many orgs are trying to get away from Active Directory Federated Services and all the complexity that comes with it.
The key trust deployment can be completed with or without federation and will therefore be preferred in most circumstances. Either way, you will need to have Azure AD Connect installed and configured, as well as an Enterprise PKI (meaning a Certificate Authority installed on your domain with certs being issued to your domain controller). As well you need at least one 2016 Domain Controller in each site. If it is a very large organization then you need to plan for an “adequate number” of 2016 domain controllers.
As setting all of this up is not a trivial task, I think it is worth asking yourself: is this worth the effort? Especially if you are trying to get rid of the legacy domain, and this hybrid stuff is just an intermediate step that should be temporary. Consider that question first, then proceed. Here are your three options, as I see them:
Option 1: Hybrid Azure AD Join (Key Trust deployment)
If you decide to move forward with a full hybrid deployment, then you must meet the pre-requisites and subsequently follow along with the installation process described by Microsoft. There are several linked articles in this series: just step through them to the end.
Option 2: Skip ahead to Azure AD Join (not hybrid join)
For a lot of smaller sized organizations especially, this will actually make the most sense. Traditional Active Directory, after all, is like 20 years old. Why hang on to the past? If you just start joining your PC’s to Azure AD straight out of the box, you’re going to fall in love, and be that much closer to nixing your old domain for good. It’s easy, it doesn’t require any local hardware or server, and you can manage it from anywhere.
If you have Azure AD Connect in place, as most hybrid organizations do, then Azure AD Joined machines can still seamlessly access on-premises resources. Sure, group policies from the local DC will not deploy to your workstation, but you can configure policies from Intune instead.
The biggest downside is that if you have local resources like printers then you need to install those locally per PC. But in my mind that’s a small trade off for all the other cloud benefits, and you can find other options out there for printer deployment / management anyway.
Option 3: Disable Windows Hello for Business in Intune
You can also just ask Intune to leave the Windows Hello pandora well enough alone. Device enrollment > Windows enrollment > Windows Hello for Business.

When you’re over your case of hybrid-join madness, you will wake up out of your stupor and it will hit you: You should just go straight Azure AD Join, as you should have in the first place! Then you can come back in here and re-enable this. But until then, just let the domain password continue to be the login method. Also be sure there are no Hello settings being deployed by other configuration profiles or Security baselines:

Option 4: Don’t be fooled by option 4
Some bloggers out there have pointed toward the “fix” of enabling a convenience PIN. But don’t fall for it. This is a GPO that is found at Computer Configuration\Administrative Templates\System\Logon and it can go by two different names (but they are the same, one is just a newer version of the ADMX to emphasize that it is for convenience, not security):
- Turn on PIN sign-in
- Turn on convenience PIN sign-in (updated wording)

This setting is not really enabling your “Hello” PIN, but rather a local PIN, which actually caches your domain password on the computer inside a convenient little wrapper (no bueno). Convenience PINs and Hello PINs are actually mutually exclusive of one another–you will have issues if you try to enable both. But switching to the convenience PIN couldn’t be further from the spirit of Windows Hello for Business–it’s actually a big downgrade for your security, so don’t do it.


Comments (13)
I’ve probably misunderstood or missed something, but how would a user access a local file share
” then Azure AD Joined machines can still seamlessly access on-premises resources”
if printers won;t work because the user is not logging in as an AD user, why would file shares?
With Azure AD Connect in place, your identity in the cloud is understood to be the same as the identity on-prem. So when you browse to a server with \\servername you will see all of the resources, and you will be able to connect to them. Printers, file shares, whatever you like. And you do not need to have the computer joined to the local domain for this to work. The only difference is, you can’t “push” those shares via a group policy (because the machines aren’t joined to the domain, they won’t see any GPO’s you publish). So if you want to connect to those file shares or printer shares, it’s manual.
Ciao..I am in the case where everything has been configured as Hybrid Azure AD Join, but when I try to access the local server via server it asks me for the domain credentials (once entered I access the shared folders); what is missing?
Sorry, I don’t follow the question…?
We using Autopilot Hybrid and Hello for Business is not enabled on domain level. We would want to use Windows Hello only and we would like to use as well Security Baseline (May 2019).
But in Security Baseline there are settings for Windows Hello for Business and Configure Windows Hello for Business is set to Not Configured. But it seems because there is settings like Require lowercase letters in PIN: Allowed etc actually turn Windows Hello for Business to enabled and you can’t set this kind of settings to Not Configured…
Information for this settings says:
“Windows Hello for Business is an alternative method for signing into Windows by replacing passwords, Smart Cards, and Virtual Smart Cards. When set to Yes, you enable this policy and the device provisions Windows Hello for Business. When set to Not configured, the baseline does not affect the policy setting of the device. If Windows Hello for Business is disabled, it remains disabled. If its enabled, it remains enabled. You cannot disable Windows Hello for Business through this baseline but can disable it when you configure Windows Hello for Business as part of Windows enrollment, or as part of a device configuration profile for identity protection.”
But what I know based my testing with default Windows Hello for Business you can’t really disable this because it’s with lowest priority and Security Baseline overwrite this.. And if you disable Windows Hello for Business with configuration profile then this is conflict policy and not working..
Have you tested this or found any workaround? We would really want to use Security Baseline because there’s so many cool security features which you can’t set very nice with configuration profiles..
I think you can switch the security baseline to not configured if you want to… In fact I had done this successfully somewhere (just make sure the enrollment settings match what you select in the policy). However, why not just configure Hello for Business? If you want improved workstation security this is a major one–2FA for your workstations!
Hi Alex, Do you think Microsoft will add Windows Hello as a MFA option for Office365/AAD? It currently supports hardware key, but I have a customer interested in facial recognition for login to both Windows and Office 365 (ie Dynamics 365).
You could enroll the device in Intune and alter your CA policy to say if logins to 365 are from a compliant device, then dont require MFA.. but if an attacker gained access to a device they could use just a password to login and therefore access 365 without any second factor (other than the fact they have the computer itself). It would be ideal if you could lock this down to only allow access from Windows Hello-authenticated sessions?
For now I feel fine treating the compliant device as the second factor. If the attacker has control of the machine then it is game over anyway. Even with MFA the machine will have tokens that already contain MFA approval and can be refreshed, and it will have locally cached data most likely. If machine is physically lost/stolen then you can wipe, but if you’re talking about someone lurking on the machine silently using some kind of malware, then MFA isn’t your defense for that–you need other things like EDR, etc.
Hi Alex,
I’ve attempted to perform Option 3, and found the option was already set to ‘Not Configured’.
My previously working GPO prior to MDM/Azure enrollment now no longer works and I’m receiving “This option is currently unavailable” when attempting to set up pin/facial recognition.
Are you aware if Option 3. no longer applies?
Regards,
Shane.
GPO:
– Computer Configuration/Policies/Administrative Templates/System/Logon/Turn on convenience PIN sign-in – Enabled
– Computer Configuration/Policies/Administrative Templates/Windows Components/Biometrics/Allow domain users to log on using Biometrics – Enabled
– Computer Configuration/Policies/Administrative Templates/Windows Components/Windows Hello for Business/Use Biometrics – Enabled
Sorry, I might not be clear on the question–what are you trying to accomplish? Option 3 is when you do not want to deploy Windows Hello at all–not on-prem, and not in the cloud. If you are in a hybrid environment and want Hello to work properly then you have to deploy Hello on-prem using the Hybrid key trust method.
Windows Hello for Business seems to be a mess. Is the easy option you allude to mean we need to pay Microsoft a monthly per user fee and it all just works well. And if we don’t were cursed to IT purgatory. Just reading this article and dozens of others like it on the web seems like a form of torture. I can’t even tell what I would buy if I would want to. Is Azure AD Join a product or a setting? And what is EDR?
There is almost no reason that you would not buy a subscription that includes Intune now. The other plans that only have Office 365 apps / productivity are in my opinion now LEGACY plans, and only using those is the equivalent to recommending a workgroup instead of a domain. You want the security and management suite (EM+S) which includes Intune, and you can get through Microsoft 365 Business Premium for only 20/user/month. It’s nothing–that’s a killer deal when you look at everything included. You’re saving $12/user/month compared to E3 equivalent. So it’s not a big deal to pay for Intune, you get a lot more than just Hello–but that is a good feature (among so many others). An EDR product is Endpoint Detection and Response. Microsoft’s offering there is Microsoft Defender ATP–which would be an add-on for Business or E3, otherwise only included in E5.
Hey Alex, seems like we have Hybrid Cloud Trust available, so your nice article could be updated a bit.
Cheers!