Updates coming soon to the Azure AD Best practices checklist
Update: The best practices checklists and guides are now available.
I will be updating the best practices checklist and guide for Azure AD again soon, but I wanted to post a couple of notes about the coming changes–since it may be a while before I get around to editing and publishing the PDF’s (I will also be uploading the original XLSX workbooks as well, by popular demand).
Change #1: Assign Azure AD Premium P2 (or Enterprise Mobility + Security E5) to highly sensitive accounts such as administrator accounts, or others who have access to the most sensitive data sets in your organization.
Recently on Twitter, Alex Simons clarified something important that has long been misunderstood. The conversation was about how all the best identity features are tied up in E5 plans, or Azure AD Premium P2. Identity Protection, Privileged Identity Management (PIM), Risk-based Conditional access and so forth.
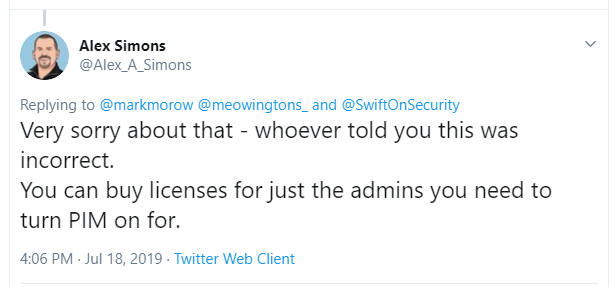
And this response makes sense. The reason being, you should only need to license users for software if they are explicitly benefiting from the features included with said software. Therefore, it would be possible to have risk-based policies, PIM, etc. in place for your admin accounts, without also licensing every single user in the company.
Asked for further clarification, Alex confirmed that even the individuals who are participating in the PIM approval process do not need to be included–just the admin accounts themselves, which are being protected by PIM.
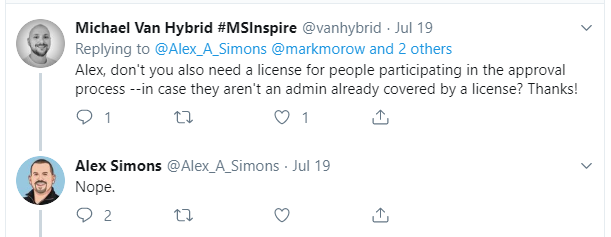
Knowing this, even small businesses could benefit from some of these protections, and it doesn’t have to break the bank.
Now the reason I say go for EM+S E5, rather than just Azure AD Premium P2, is that the bundle holds a lot of extra value without adding a lot more $ (since you only need to purchase it in small quantities for specific users, typically–see my licensing guide for more details). For example:
- Azure Information Protection P2 = ability to automatically classify sensitive data sets, so that users who handle extra sensitive data do not have to “think about it” and manually classify the information;
- Azure ATP = Good tool for Identity forensics, gaining insights into users’ activity, especially suspicious activities;
- Microsoft Cloud App Security = Get pre-canned alerts and the ability to create some really great custom alerts from a filter-friendly activity log; alert when admins sign-in from unknown locations, alert on admin activities–which also gives you a change log, etc.; also discover cloud apps, review OAuth app usage, and more!
Change #2: Introduce a third risk category to the Conditional access policy design.
Update September 2019: I ultimately decided against the third more restrictive category, and kept just two: typical and sensitive or restrictive environments. You do not have to implement every policy, but you should consider each of them in any new implementation.
Currently I describe one “baseline” policy set for the typical small business, and an additional set of policies for businesses with a little more sensitivity, where they want to “go the extra mile.” I am now going to outline three tiers:
- typical
- sensitive
- most restrictive
The new design will leverage some of the advanced capabilities in EM+S E5, for those extra sensitive accounts, like Risk-based, Identity Protection and PIM.
The “typical” and “sensitive” policy sets will basically remain the same otherwise. Currently the sensitive policy set will block downloads on unmanaged devices from SharePoint and Exchange Online. A stronger version of this would just block access outright, and require any devices to become enrolled and compliant, even if they are using a web browser. This will be the behavior in the most restrictive tier, along with the MFA requirement (always enforced).
Also, as discussed previously, we will want to block unsupported devices such as Chromebooks and the like, in the most restrictive tier. And last of all, we’ll look at Windows Information Protection (basically MAM for Windows)–which is to be used only in very restrictive environments.
And that’s about it for now. I’ll have to carve out some time to update the publications on GitHub, and I’ll post back once that happens.



Leave a Reply