A Reader’s input for your consideration: Blocking unsupported devices with Conditional access
Consider the following scenario (from a reader who wished to remain anonymous):
Let’s say you have implemented my recommended baseline policies for Conditional access, which require Windows & Mac computers to become managed/compliant with Intune, and iOS & Android devices to use approved client applications. In turn, you get control and leverage over the corporate data with either MDM (PC) or app protection (mobile).
But what if a user authenticates from some other device that cannot be identified as any of the major supported platforms (like a Chromebook). What will happen then?
If you have implemented all of the recommended policies, then the user would at least be required to perform multi-factor authentication. That’s because we are using another policy called “Require MFA on unmanaged devices.” But, if you would rather BLOCK devices that cannot properly identify themselves as one of the explicitly supported platforms (and/or if you don’t want to support a specific platform like Windows Phone or MacOS for example), then you should do the following:
Create a new Conditional Access policy. Name it Block unsupported devices or similar. Assign it to All users (excluding break-glass account) and All cloud apps. Now pick Conditions > Device platforms, and select Any device under the Include tab.
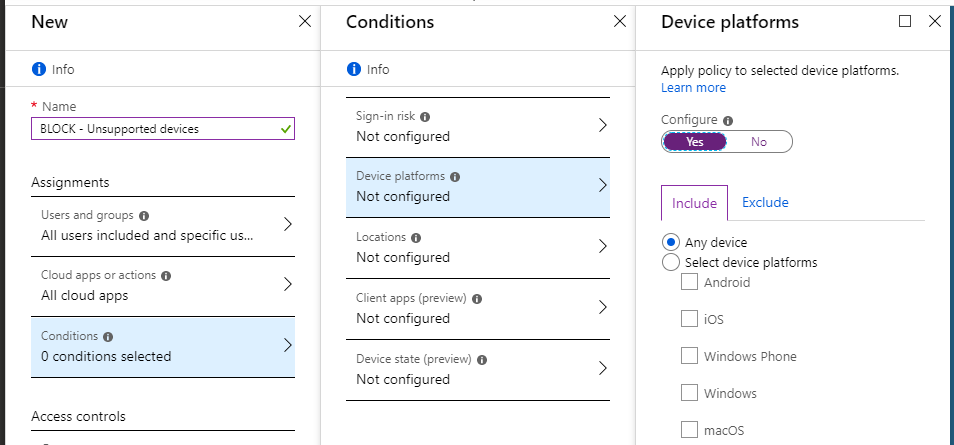
Under the Exclude tab, however, select all of the device types that you fully support in your environment. If you don’t want to include Windows Phone or Mac, etc., then do not select them.
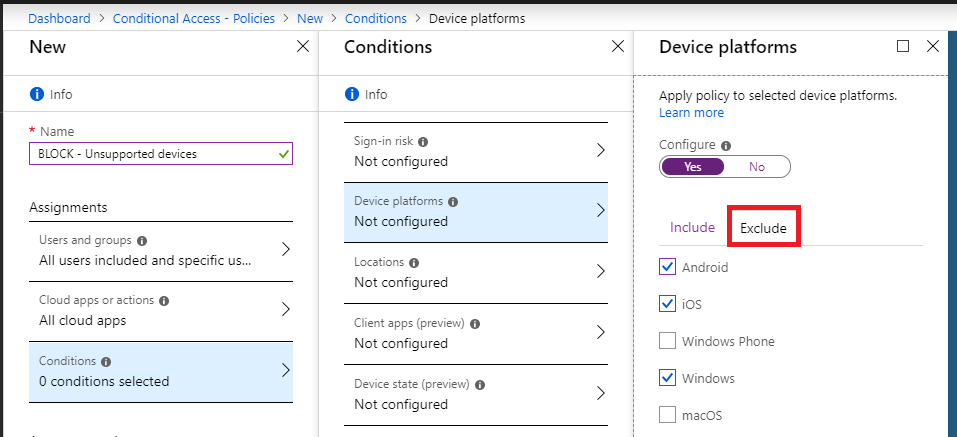
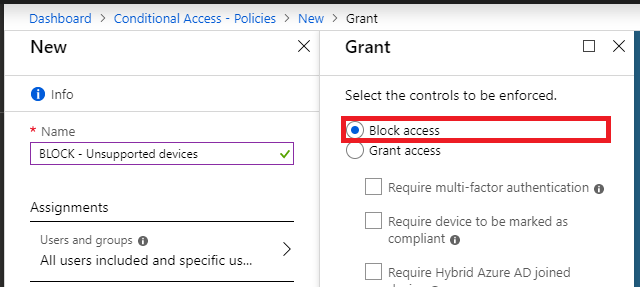
Do not specify any other Conditions, and under Access controls, pick Block access. Create and enable the policy.
NOTE: This would also effectively block Chromebooks and the like, which are not one of the supported device platforms that is being specified here under the Exclude tab. (But they are still captured by the Include condition “Any device”). Therefore this control is also much stronger than using Device enrollment > Enrollment restrictions, because that control will only allow you to prevent specific types of devices from becoming enrolled.
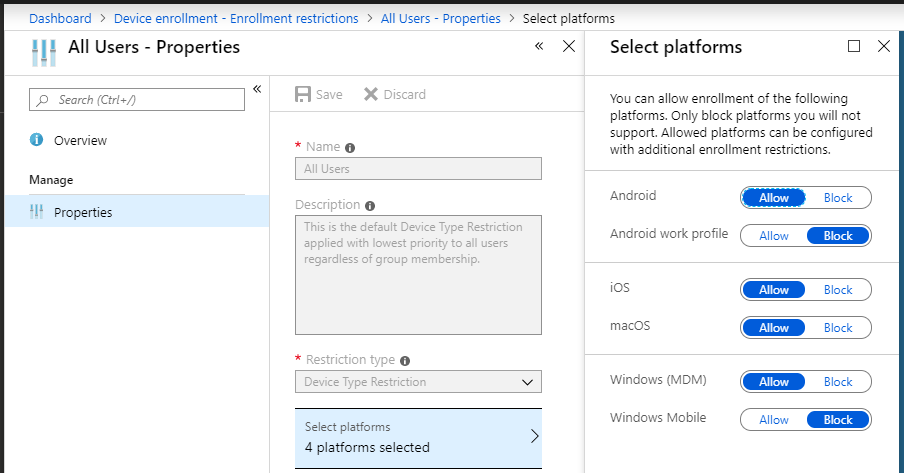
Whereas this policy will outright block any access attempts from unsupported device platforms.
Of course, I would not consider this a policy for “everyone”–some people want to allow access to outside devices like Chromebooks for instance. Not to mention, you are already covered by the MFA policy for unmanaged devices (and that one should be adopted by everyone).
But for extra sensitive environments where you want strict control over any and every device that is allowed to connect and access data, this is a good addition to consider. In sum:
- Require MFA on unmanaged devices (my default policy set does this–use this for most environments)
- Block unsupported devices (NEW addition recommended for extra sensitive environments)
So I’ll probably add this as an update later this month to my CA policy design and guide on GitHub. Just wanted to share it with you here first.
Keep the feedback coming folks. I am learning as much as I can from many places right now and the community has been good to me in turn–readers, you are doing an awesome job of contributing to this project. I’ll do my best to keep paying it back by refining the best practices guides and checklists from everything we uncover together.
Thanks, “Anonymous.”


Comments (5)
Question: Why not just include the devices you want to block instead of excluding the ones that you support?
Good question, and the answer is that if you only target specific types of devices to block, then only those devices will be blocked. But what about device platforms that aren’t on this list? Like Ubuntu, or a Chromebook? The only way at present to block those is to block everything, then make exceptions for the supported platforms.
I know this is getting a little specific but if you would..
If I want to only support iOS, macOS, and Windows PCs but want to allow all other devices to access OWA w/MFA (in a separate MFA policy) could I just scope the client app (modern auth clients) and keep everything else as is above?
If the goal is to allow access to OWA (which is an application you access via a web browser) and this should be possible from any device while also requiring MFA, then I would build a separate policy that targets All users, Exchange online as the cloud app, Web browser as the client app under conditions and Require MFA as the Access control. Then, to block other devices from using non-browser apps, yes I would use this policy to target client apps (do not include web browsers).
Perfect! Thanks!