Showdown: Exchange Active Sync vs. Office 365 MDM vs. Intune (MDM and MAM)
The Microsoft 365 platform offers customers not one, not two, but three distinct Mobile Device Management solutions (well, technically four, as we’ll see). In my experience, most small business customers will be fine with nothing more than a well configured Exchange Active Sync policy, requiring basics like a pass code, device encryption, and the ability to remote wipe. But it is good to evaluate all of your options, in case your own requirements call for more. Note: there are also a plethora of third-party solutions out there, but in this article I’m just going to compare the ones available within the native Microsoft 365 universe.
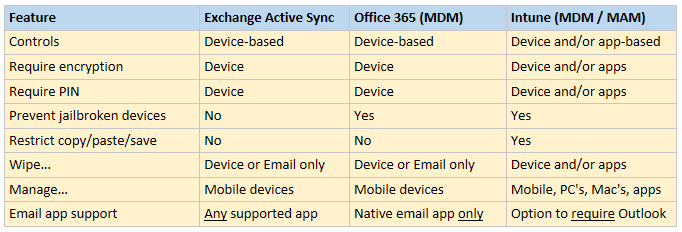
Solution #1 : Exchange Active Sync (EAS)
As I mentioned, the original solution is EAS, and what does it have to recommend it? Simplicity. Here is what you can do, with a basic EAS policy:
- Refuse access to devices that do not support the policies
- Require device encryption
- Require a pass code (non-simple, alphanumeric, etc.)
- Require the pass code to expire
- Lock the screen after a certain number of minutes
- Wipe the device after a certain number of pass code attempts have failed
- Wipe the device (or Account data) remotely
Most orgs are happy with the above options alone. But also know that there are several other items you can control, available via PowerShell. It is furthermore possible to have new devices auto-quarantined by default, meaning that administrators would get a notification, and then choose to approve or block the device in Exchange Online.
And the best part: from an end-user perspective, nothing special is really required, other than adding a mail profile to the device, or using their favorite supported mail app. Enrolling the device in MDM or Intune is a totally different story.
Solution #2: MDM for Office 365
This feature is included with Business and Enterprise plans for Office 365, and it can be a good option for requiring a tiny bit more device-based security without a large investment in additional subscriptions or third party products. Basically these policies can do everything that an EAS policy can do, plus:
- prevent jail-broken/rooted devices from connecting
- require managed email profile (this means that enrollment in MDM will install the email profile in the phone’s native mail app)
- block access to the app store
- block cloud backup, document &/or photo sync, screen capture, Bluetooth devices, etc.
- Require enrollment for access to apps other than just email (e.g. the OneDrive app)
The drawbacks to this solution are many in my opinion, but mainly you should know that the device enrollment process totally sucks. Users have to get the Intune app, and proceed to step through more than a dozen screens, selecting “Continue” and “Enroll” and “Install” and “Accept” and on and on, until FINALLY they get their email profile… and then you learn that it can only deploy to the built-in native email app, such as iOS’s mail app (boooouurrnnss). Last, understand that this solution requires an Apple Push Notification Service (APNS) certificate, which needs to be renewed annually–so yet another piece to manage. If you’re doing this you might as well do the full-blown Intune, in my opinion.
Support for Office 365 MDM is available on iOS 7.1 or later, as well as Android 4 or later.
Solution #3: Microsoft Intune MDM
Intune is available as a standalone product, but is more frequently purchased as part of a bundle, like the Enterprise Mobility + Security E3 or E5 plan, or Microsoft 365 Business or Enterprise plans. Intune actually has two different mobility management solutions built-in: Mobile Device Management (MDM), and Mobile Application Management (MAM).
MDM, or device-based management, is often leveraged when you have corporate-owned and managed devices. Intune’s MDM can do everything included in EAS and Office 365 MDM, plus you get a lot of additional powers over the device. For example:
- Push Wi-Fi and VPN profiles to the device
- Push business applications to devices
- Manage updates to devices
- Use corporate PKI and certificates
I normally only see larger sized enterprises entertaining these types of options, or generally situations where corporate-owned devices are being strictly controlled and “made the same” for various groups of users. That is to say, you can configure different profiles and device rules for different kinds of users in different roles / locations.
Plus, Intune has the capability to manage Windows 10 and Mac OS computers, in addition to mobile devices. Very large companies that use System Center Config Manager (SCCM) can hook into Intune, as well, to extend their management capabilities.
Unfortunately, the same painful enrollment process is required for the Intune MDM (it is in fact accomplished via the same mechanism: the Intune app available via the app store).
Solution #4: Microsoft Intune MAM (BYOD)
Mobile Application Management (MAM) is another advanced feature of Intune, which allows for BYOD scenarios. MAM can actually be paired along with MDM in larger corporate environments, to support either use case: device-based and/or application-based mobility management. But in the small to mid-sized business, almost all users are “BYOD”–using their own devices to access corporate email and other digital resources. So it makes sense to evaluate the MAM options here.
First and foremost, the good news: end-users have no enrollment process to speak of; instead they just get a one-time prompt that their application settings are being managed (and they have to restart the app). Therefore, MAM is a very attractive alternative to MDM, with many of the same benefits, although the execution looks a little bit different.
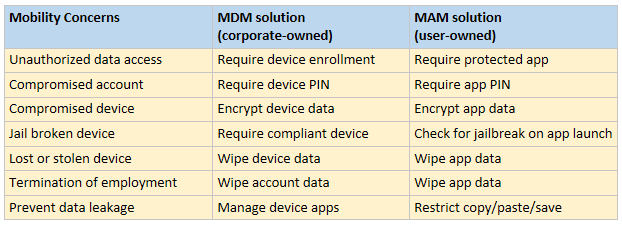
Fig. 1: MDM and MAM address same concerns but differently
As mentioned above, MDM is great when you need to exercise an extreme level of control over a device. But generally speaking, when users bring their own personal device to the table, they don’t want to be bothered or blocked from doing “other stuff”–therefore, many of the controls provided via MDM are moot. These workers are going to have personal data and apps, as well as corporate ones. Who wants to block their users from syncing personal photos to iCloud, for instance?!
Enter MAM. When choosing to manage mobility at the application level, we are most often pairing Intune up with Azure Active Directory Premium, so that we can enable Conditional Access–for example: we can create a Conditional Access policy that forces users to access their corporate data only through the Microsoft apps such as Outlook, OneDrive, Word, OneNote, etc. And, we can also challenge them for MFA. The extra controls are necessary so that we can raise our confidence level in those mobile connections being made to our environment, and protect the data at the application level, rather than the device level.
This means that the device does not need to be enrolled at all, and the application will do the job of protecting the corporate data, effectively isolating it from the personal stuff on the device. This includes blocking users from saving to the device or even copy/pasting out of Microsoft apps and into “personal” ones such as the native mail app, Evernote, DropBox, etc. A pretty effective solution over all, and again, minimally invasive to users.
Conclusions
It is true, I am heavily biased toward simplicity. And, since I support primarily smaller sized businesses, I tend to favor solutions that I think are better suited to that market segment. In my opinion, the built-in features of Exchange Online cover 95% of use cases in the small business. For Nazi-level security, I would skip all the way to EMS/Intune, rather than use the “included” MDM of Office 365. But, for the money, and for the fact that most every business I know and support has personal “BYOD” scenarios at play–I would lean toward MAM rather than MDM in those cases. But again, that’s just my opinion–take it or leave it, and just consider these things when forming your own mobility strategy.
Fig. 2: Summary comparing features
In some upcoming posts I will show you how to turn on MAM, with Conditional Access policies assisting from Azure AD Premium. Note that this is even easier with Microsoft 365 subscriptions, since you can use simplified wizards to setup these policies from the admin center, without messing around in the Intune portal.



Leave a Reply