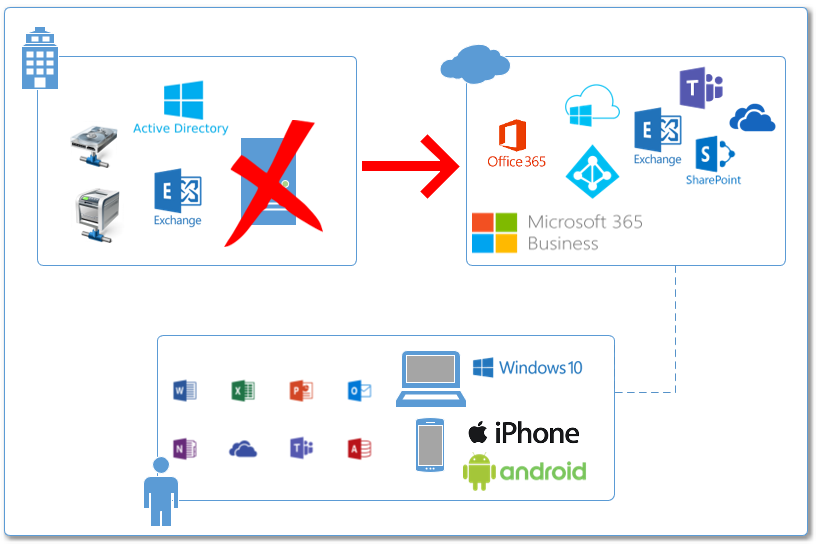
How to migrate from Windows Server Active Directory to Azure AD and Microsoft 365 Business (including Teams) in 5 easy steps
Microsoft 365 Business is a very compelling platform for the small business, particularly those that are “born in the cloud,” or, those who have shed most of their on-premises server weight already, by moving their line of business apps to cloud-based alternatives. I can’t tell you how many clients I have these days who have ditched QuickBooks Pro for QuickBooks Online, or Dynamics on-premises for a 365 flavor of the same. So if this sounds like you (or any of your own customers), then listen up:
I am here to tell you that it is completely possible to leave your on-premises server behind, and get out of the datacenter business in your small office. Forever.
For small organizations, it is going to become increasingly difficult to justify having even a small server sit in the wiring closet, when the alternative is a $20.00 USD / user / month subscription (plus managed services of course). Yes, you are still going to need your firewall, yes you are still going to have switches and WiFi access points and printers. Yes, you will still have security needs and IT support for normal trouble tickets as well as proactive maintenance of your devices. But no server. Not. Ever. Again.
The pre-requisites for this solution are:
- Line of business apps are all cloud-based or hosted elsewhere by third parties
- You are coming from Windows Server (SBS or Standard), probably with file and printer shares
- Exchange on-premises is possibly also in the picture (but it could be hosted elsewhere)
- You should already have “Pro” versions of Windows 7, 8, 8.1 or 10 (and you WILL be upgrading to 10)
- You have to be willing to make changes and adopt new software such as OneDrive for Business and Teams
So without further ado, let’s get started. Here’s how you move your infrastructure from an on-premises Windows Server and Active Directory, to Azure Active Directory and Microsoft 365 Business (including Teams), in five easy steps. Note: this post won’t have every screen and detail, just the big strokes, with some helpful links to more detail.
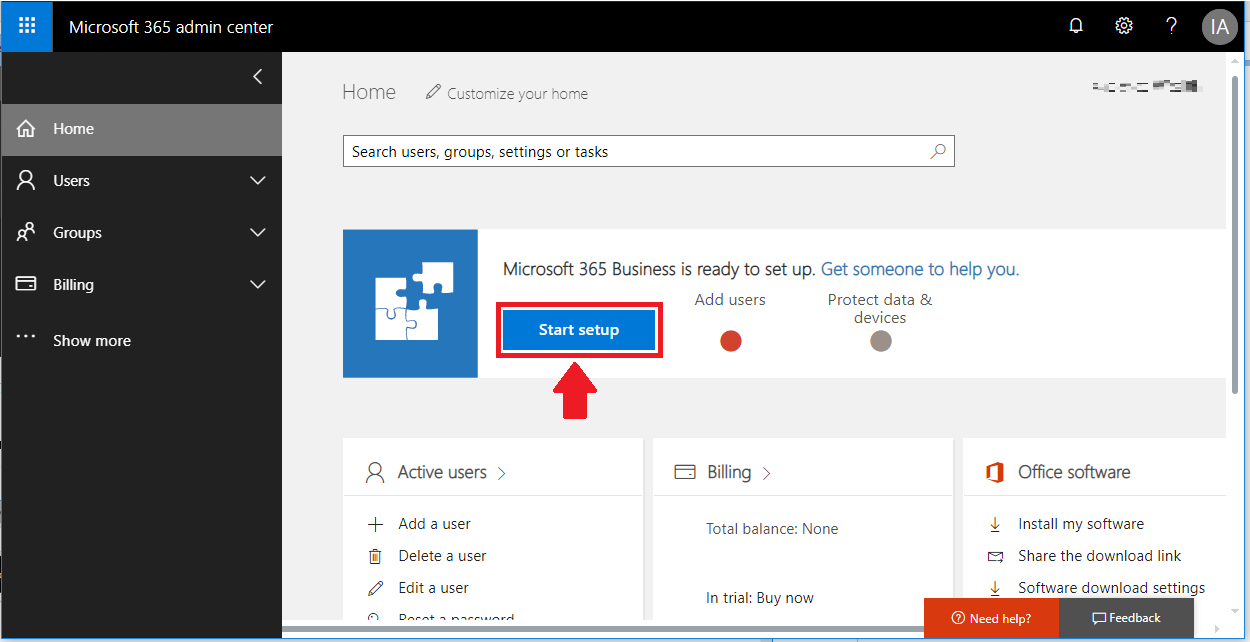
Step 1. Provision Microsoft 365 Business and Exchange Online
First thing is first: Go get yourself signed up for a Microsoft 365 Business account. There are a few setup screens to walk through where you pick how you want to manage devices and so on. I also recommend, before migration, to provision your Exchange Online and Advanced Threat Protection subscription with the security defaults that you would like to have in place.
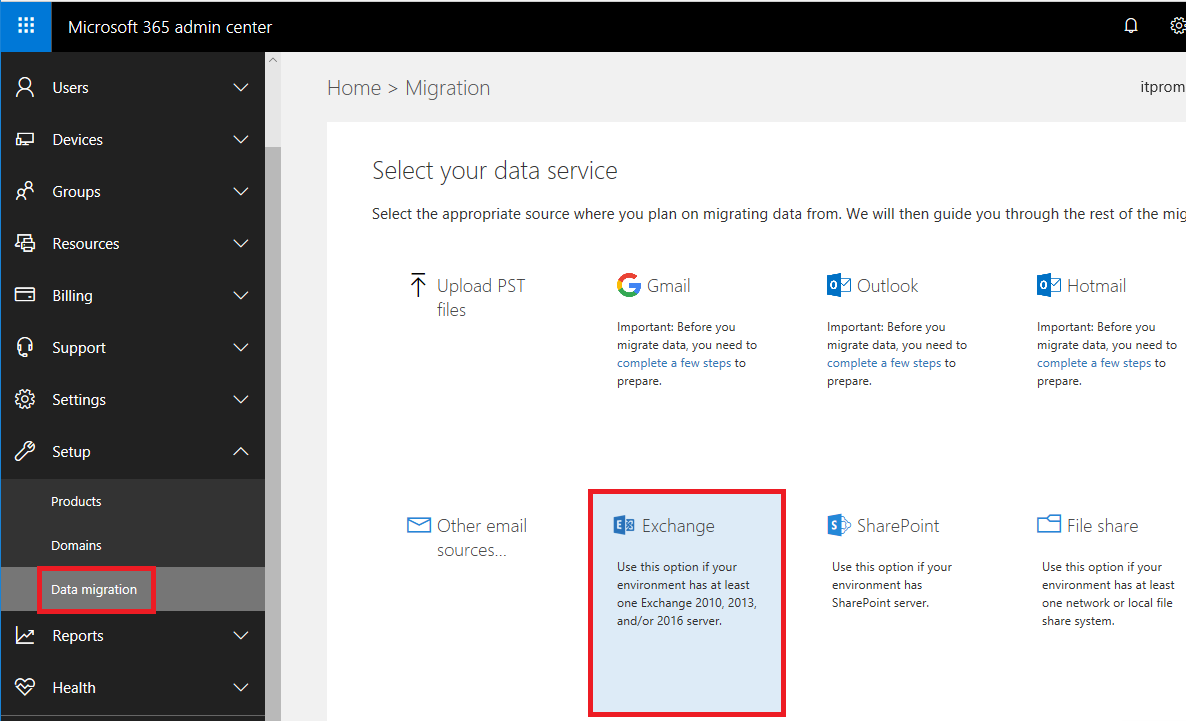
Step 2. Migrate Email to Exchange Online
Almost every organization starts their journey to the 365 cloud with a migration to Exchange Online. These days, there are a lot of options to get your email, contacts and calendars moved over from a legacy system such as an older Exchange Server (whether hosted at a third-party, or on-premises). If you have your own Exchange Server on-premises, consider using the native hybrid functionality to migrate your users initially. Once you are fully migrated, you can remove both Azure AD Connect and Exchange hybrid. Normally Exchange server is kept in place for “hybrid” organizations, but since your intention is to get rid of all remaining servers, there is no reason to keep it active once the mailboxes are moved. As an alternative, and certainly if you are hosted elsewhere, consider using BitTitan’s MigrationWiz product–I have been using it for the last couple of years, and absolutely love it.
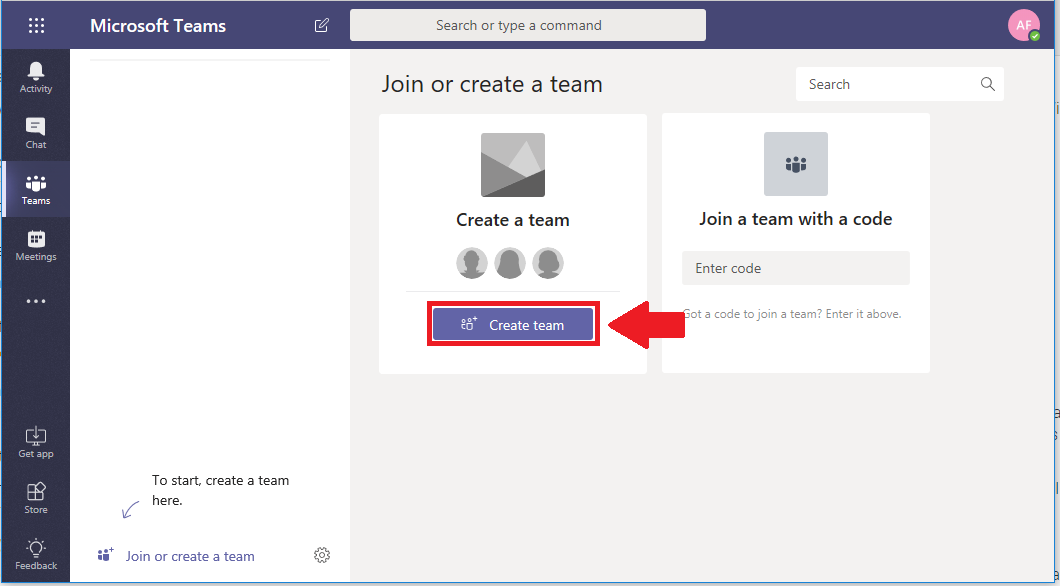
Step 3. Setup Microsoft Teams for your SMB organization
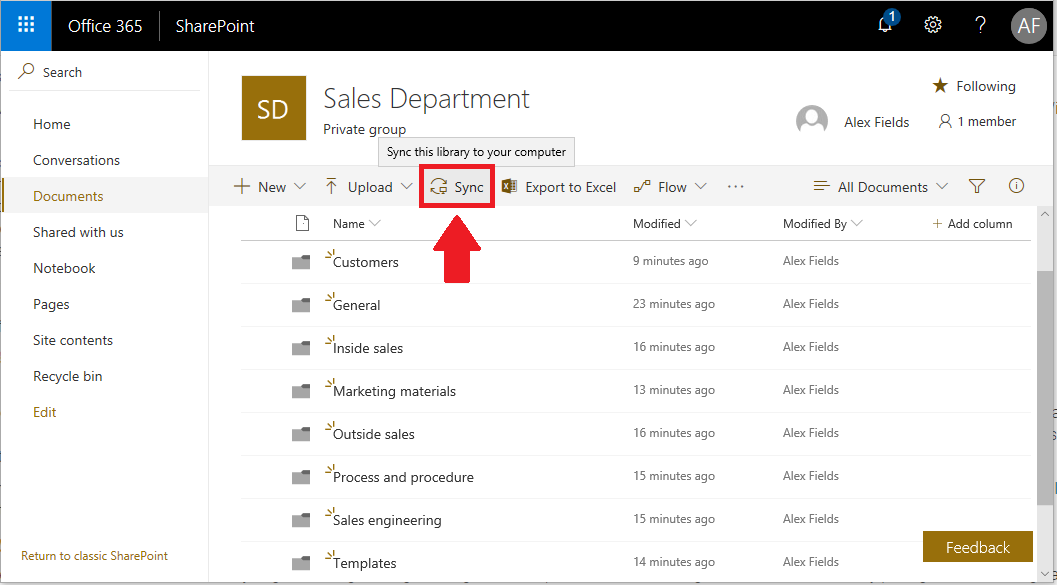
Most SMB’s can start adopting Teams very quickly: just go to teams.microsoft.com to get started.. It is easy-to-use software with built-in chat/instant messaging, file sharing (SharePoint), notebooks (OneNote), and more. The main reason we want to provision this app is because you can quickly create new cloud-hosted file shares based around the core teams within the organization. Each “Team” will represent a “file share” (think mapped drive) such as Accounting, Executive team or Sales department. You can have multiple “channels” or discussion threads underneath, and each of these will get a sub-folder for storing files within that Team. Of course, there are many ways to leverage and structure Teams, but this is one that I recommend simply because it maps well to what we see in a lot of Small Business environments.
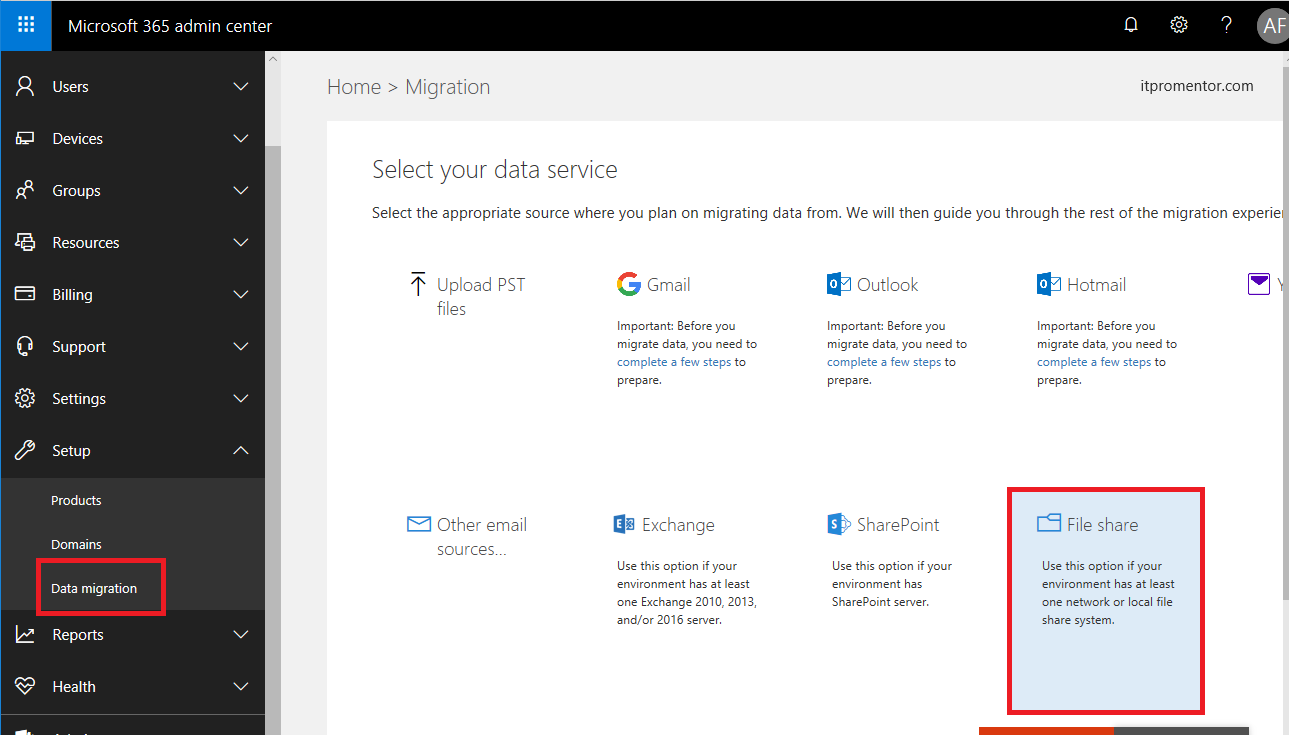
Step 4. Migrate file shares to OneDrive for Business and SharePoint Online
Microsoft has a migration tool available which can help you to migrate existing file shares. But, there is a good chance that your organization doesn’t necessarily want to migrate everything. Most file servers are a giant clutter mess. So this is a great opportunity for Organizations to clean house and shed weight. It is possible for example, to copy over only active files that people really need or “care about” and then dump everything that remains to a NAS or similar solution, for backup/archive purposes. This way, old files are still available if users need to go back and pull “missed items” into OneDrive or SharePoint. Once you have everything in its right place, shut off the old file shares.
Step 5. Upgrade to Windows 10 Pro and Join Azure AD
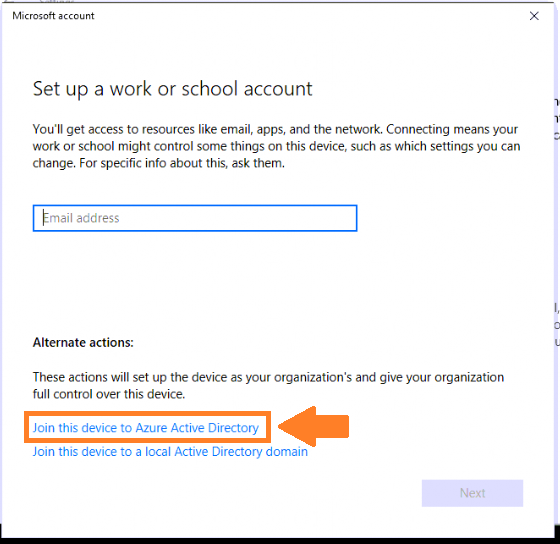
To take full advantage of Azure Active Directory and your Microsoft 365 Business subscription, you will want to join your computers to the Azure AD cloud–that way users can sign in to their PC’s using their cloud identities & passwords. Hopefully your small organization is already using Windows 7, 8, or 8.1 Pro–if so, then you qualify for an upgrade to Windows 10 Business using your Microsoft 365 Business subscription. Once you have installed Windows 10, or if your computers already meet the requirement, it is time to join Azure Active Directory, so you can take advantage of the slick Device Management features built-in to Windows 10 and Microsoft 365 Business.
If you previously belonged to an on-premises Active Directory domain, then you will need to dis-join the machines first before joining up to Azure AD (but my favorite method is to start with new or freshly imaged Windows 10 Pro computers that were never part of a domain). Settings > Accounts > Access work or school > Connect. Choose the option below to Join this device to Azure Active Directory.
Once your users are signed into their devices using Azure Active Directory credentials, make sure to setup OneDrive for Business, so you’re taking advantage of Files On-Demand and Known Folder Move (protecting Desktop, Pictures and Documents). Install the Office apps (autopilot can do this for you actually) and Microsoft Teams, and then sync your Teams document libraries using the OneDrive client. Now you can see all those files in your file explorer, and in Teams!
In case you missed it, at this point, you no longer need your on-premises domain controller–so go ahead and turn that sucker off. Other network services such as DHCP and DNS should live on the firewall or router at the edge of the network, and printer drivers will just be installed locally on each machine rather than on the server.
Further notes on security and management of devices
There is an older generation of folks out there who do not yet grasp how beneficial this type of infrastructure can be–for end users and IT alike. The truth of the matter is, most small businesses never really leveraged Active Directory and tools like Group Policy correctly, or to the fullest extent anyway. At most, the technology probably provided mapped drives, printer shares, and of course the shared login capabilities that come with a centralized security boundary. Enterprise IT departments are usually tied into a lot more of the functionality and feature sets of Windows Server Active Directory: Certificate Services, Rights Management Services, Remote Desktop Services and so forth. This means that migrating a larger organization can be quite a bit more complex than this.
But for the SMB of say 25 users (give or take) who have small server footprints, this move is not that hard to do. Resistance to it is mostly mental / emotional.
Once you are moved over to this platform I encourage you to check out the modern device management features, which are a great improvement over GPO. For example, you can see when a policy has been successfully applied, or when it has failed to apply, and which endpoints were impacted.
So the way I see it, Microsoft 365 Business represents a huge opportunity for Managed Services IT Providers, because these companies can manage all of the cloud resources and identities centrally for their customers within the Microsoft 365 Admin portal, and supplement that suite with their own support and security tools. These are things they were going to do anyway, but now they can do it without having to spend their time deploying, updating, replacing and generally toying with servers. I for one will be glad to see that part of the business go away. What do you think?


Comments (21)
This is pretty much word for word on how we have been migrating clients. It took us the longest time though to decide whether to do Microsoft 365 Business or Business Premium + EMS E3 + Advanced Threat Protection, as the price difference is negligible but it included the full AD Premium that allowed the setting up of conditional access policies. We went for the latter in the end because Microsoft were being funny about utilising the Intune included with 365 Business (suggesting that it wasn’t a full license).
It is indeed a full Intune license. Also, I would still recommend 365 Business, and just add AD Premium instead. You aren’t getting everything by layering Business Premium + EMS E3 + ATP. You miss out on Archiving, DLP and Windows 10 licensing. Just go up to Microsoft 365 Business and then layer in the Azure AD Premium, because you will have everything you need at that point, including the Windows 10 license, etc.
I just wanted to say thank you for your resources.. you have made this really easy to run a small business with all your help
This is a great article! I am hoping to do this very thing shortly. We have moved from SBS 2008 to Office 365 Business Essentials and Business Premium about 3 years ago now and has been a great success. Moved to Server 2012 R2 for AD, GPO and local file shares as well as our ERP system requirements. But now want to fully embrace Teams, OneDrive, SharePoint etc. I do worry about losing some of the GPO control I have been using to lock desktops down. I am evaluating products like JumpCloud and PolicyPak to fill in the gaps. Will combine this with Azure based servers for our ERP system to complete the transformation of our server room into a coat room :-). Always need to keep an eye on pricing though.
Great stuff! We are planning our final move away from the local AD – we did the email thing back in March, so we thought it was just our local server files that were the last big step. But, the major sticking point is actually the anti-virus software on clients. What should we use, and how does it integrate into Office 365 / Azure / InTune? We are using Sophos through local AD – works nice on Windows, not so much on Macs (about 25% of our machines). Any lessons learned about which anti-virus software we should use for end-point protection, that we can monitor or deploy using our E3 licences, and that work on both Windows and Mac?
Well the Microsoft 365 Business subscription includes Windows Defender AV, but that only applies to Windows I believe. I work for an MSP, and MSP’s tend to have their own agent that does monitoring, remote control, AV, etc. bundled in. So I don’t have another recommendation, unfortunately.
Ian,
For Windows 10 endpoint clients (desktops/laptops) then you might not need to replace your Sophos installation with another paid for non-Microsoft product. About 6 months ago I scrapped our 3rd party endpoint AV solution (AVG) in favour of using the built in (and Free) Windows 10 Defender & Firewall combo. This along with making sure that all of the the anti-spam, anti-phishing, anti-,malware tools in Office 365 were more pro-actively set up (there are numerous articles on setting these tools up more robustly on this Blog provided by Alex) and a higher emphasis on user education (do not click things you do not recognize!) has worked at my installation.
It saved a small amount of cash on an AV subscription and improved our protection against Malware threats from email and internet links. 6 months later we have had no cyber-security issues. For better or worse, it would appear that the days on buying a single, ready-made cyber protection solution like Sophos (as good as Sophos were/are) are past and that your cyber-security strategy has to be much more broadly based.
A good first step would be by going through Alex’s articles on Office / Microsoft 365 security.
Sorry, I cant advise about the Macs.
Thanks Alex! And thanks David! I thought as much for Windows machines. It feels like it would be more “neat and tidy” to use the same AV across all machines, but saving some money for our non-profit would probably take precedent.
Thanks for this article…we’re in the midst of this transition right now, and it’s nice to know that SOMEbody believes it’s possible.
There are four “gottchas” we’re currently working through:
1) it’s not clear how to handle DNS. I’d like to spin down ALL the Windows servers here, but aren’t sure how to handle local naming (for things like printers, workstations, and the one FTP server that’ll remain in our DMZ… yeah, we have to keep that).
2) RDP (across a VPN) to AAD Joined machines is… ah… either impossible or very difficult.
3) When a user logs in to an AAD join a machine they actually get a different SID than they get from the local DC. Seriously. This will require per-user apps be reinstalled, and a,so impacts things like directly attached storage that might be prexisting on the machine (iSCSI connections or actual hard drives on which you have files from before being AAD joined).
4) If you keep ANY on-prem file servers, it’s not clear how they can authenticate users for access.
I realize it’s been months since you posted this… but hopefully you’re still willing to discuss this approach.
Yes, I should have some more detailed ones… Good idea. There are many things that are just different. For example, Win 10 can discover printers without you doing anything on a local network segment. Also, if you are keeping some local infrastructure, then with AAD Connect your machine can be either hybrid joined or aad joined and BOTH of those scenarios will give you seamless SSO access to on-prem resources like file servers. Just need to have your seamless SSO and directory sync working. Yes, I know–a bit of black magic. In general though until you get rid of everything (yes everything) that requires hosting hardware and local DNS zones for named items (the link-local name resolution only takes you so far) it is worth keeping the DC. That’s probably the last item to go. If you got anything else that you’re hosting which relies on it, gotta keep your AD/DNS going. When switching PC’s from AD to AAD, I think it is best to backup the profile (in case they are storing stuff there that they shouldn’t be), then start with OOBE/fresh copy of Win10 pro. Way better. Sign into laptop using corporate ID right from the start, fresh policies from cloud, etc. Anyway, I could go on. I should queue up some more content, I guess.
I’ve run into an issue with Azure Active Directory, Directory Services and Filesync though. The two do not preserve ACL’s. I’ve got a client that’s an ISO company and they really, really want their ACL’s locked down and tight.
Do you have any suggestions for preserving the OnPrem ACL’s, and allowing cloud access like “OneDrive for Servers”? The idea would be to be able to access off-site, easily like OneDrive, and the ability to send links to documents via email, and still use ACL’s.
GPO is still pretty useful. I’m looking at Hybrid join, as I found out that OneDrive will not log in automatically, like Teams does, unless you do Hybrid.
Also, MS support has confirmed that “Autos Save” cannot be turned ON via GPO, and apparently can’t be turned on with local drives (including file shares). This is sort of absurd.
Thanks for the article, very informative!
== John ==
Several things I want to respond to here. First, you do not need hybrid to control OneDrive. I have an article on that. Also, you should NOT attempt to implement custom ACL’s on folder hierarchies. Technically it could be done and there are tools out there that would help you with that, but it’s a legacy way of thinking and we need to adapt to the modern method of file sharing and collaboration. That means simplified permissions and flatter structure. Unique permissions sets = new site collection (in SharePoint) or Team in MS Teams. To protect extra sensitive data do not rely on ACL’s that only apply to files as long as they are in a specific container–files are way too mobile for that. Instead you have to use Sensitivity Labels to protect documents no matter where they go, or how many copies are made. When you need to revoke access or update permissions, it is much easier if there is label attached to that file, etc. In summary, yes you could use a migration tool to preserve the ACL’s but there are better ways now.
You know what’s funny? I could put quotation marks around multiple sentences in your post, and they were have been nearly verbatim the thoughts I came to this weekend.
I have been reading up on the new Azure AD features, and got excited. Device join makes sense for us, considering we have literally a hundred devices that constantly roam. With better functionality all the time, we can now consider the identity to be the user + device, unlike the last time I looked into the features or worked with it (mind you, it was a solid cloud identity solution for user auth then).
It hit me: When our users/devices authenticate against our domain, it’s only by chance! Otherwise, it’s cached credentials for hours, days, or even the better part of a year.
We have been budgeting for new on-prem infrastructure to ensure that AD DS is made to be highly available, but it will only support just a couple of LDAP configurations that we never thought about! Get rid of those, and we’re down to just DHCP and DNS, which the network stack can handle.
The proof as to how little we scratch the surface of AD DS: Beyond 2-3 LDAP configurations, I could literally shut down the DCs, and no one would notice anything. (In fact, it might actually improve user experience if one of the extreme roamers was on site, and didn’t lose trust relationship due to being able to reach a DC.)
Great post. I’m glad to see affirmation for the thoughts that have popped into my head recently. For anyone reading this:
1) Figure out what kind of a fleet you have. 50/50 static/roaming, hybrid might make sense.
2) Think about what kind of services your business depends on. Or, to put it this way: Would it be worse if the Internet went down, or the domain controller?
3) If you had to answer whether a certain roaming device was under your control, at this very moment, what would you say?
4) Do you wish you had more control and insight regarding authentication than just a username/password/MFA?
If so, take a look. I’m no Microsoft shill, but I have to say that for anyone using Windows 10 endpoints, the Office productivity suite, and a need for security and compliance, this is probably one of the most exciting developments in the cloud era.
Hi Alex,
thank you again for this high-quality post.
Thanks to your other great articles we have recently managed to move from our 2008SBS to Server 2016. With an imminent move to O365 and the rollout of plenty of Win10 workstations we are reading into the pre-requisites for the possible move to Azure AD for our environment.
One thing that we are challenged by is the question how we go about changing our non-routable domain (.local) to a verified domain: https://docs.microsoft.com/en-us/office365/enterprise/prepare-a-non-routable-domain-for-directory-synchronization
In this context Exchange 2013 seems to be a roadblock where we would need to look into Cross-Forest Migration: https://social.technet.microsoft.com/Forums/ie/en-US/35afda9a-934d-4675-a4db-866224477717/domain-name-renameexchange-2013
This scenario seems to require a new on-premise target forest.
Or is there an easier approach with perhaps just renaming the Domain, moving into Azure and then moving the mailboxes into the new AAD?
Perhaps you can point to some articles/guides that might help with such a scenario.
You do not need to rename a .local. You can keep that–it provides no benefit to move from .local to like a .com or whatever on the domain controllers. You can easily just add domin suffixes via AD Domains and Trusts, and just use those suffixes for your UPN’s on user accounts. That’s all that is required.
That´s a relief to hear that :)
So looking at the article: https://docs.microsoft.com/en-us/office365/enterprise/prepare-a-non-routable-domain-for-directory-synchronization
it would be the option “Add UPN suffixes and update your users to them” I guess then?
Yep
This article is a little old, but I am hoping someone can help. We have been moved away from a Hybrid configuration for a couple of years now however we find that even though we moved all our users off (old users) AD, and they clearly show AzureAD now when users log in to an Azure AD machine their users retain the previous domain name instead of the AzureAD domain. For example, their original user on the old domain was carls/shellcu, and new users are toms/AzureAD. We are having issues with a couple of programs because of the value of “onPremiseDistinguishedName” still contains the SHELLCU domain. The value should be empty. Any idea how to fix that? We tried to clear/write to it but apparently it is a read-only value. We have an open ticket with Microsoft but they at this point for over 3 months say that should not be an issue. We have been trying to get them to clear out that field for us and they have been no help at all.
Where do printers fit in?
Totally different thing. There is a universal print option in preview, which may work for some people. Generally in the SMB you can just install printers locally and go forward. That’s how I work now–I don’t deploy them from a “server.” If you want a central management option either wait for Universal print, or check out Printix.
Good Information Alex.The steps which you said to migrate from AD to Office 365 and Exchange is good stuff.Keep it up .Thanks for sharing this stuff.
cionsystems