Give extra Consideration before implementing WIP (Windows 10 App protection policies)
In Microsoft 365 plans it is possible to configure application protection policies for Android, iOS and Windows 10, right from the 365 Admin center under Devices > Policies.

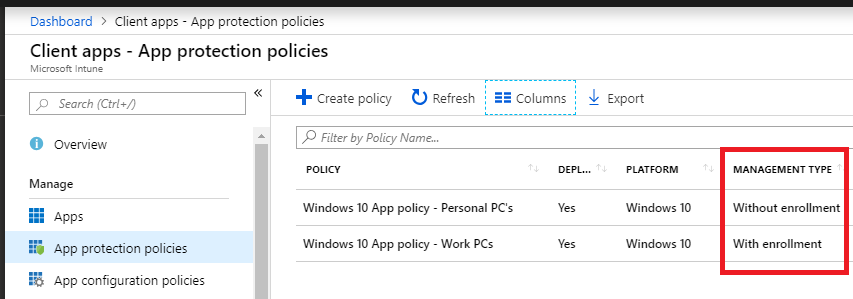
Once built, these correspond to policies that you can find within the Intune / Device management portal under Client apps > App protection policies. When you enable one for Windows 10, it will be activating Windows Information Protection (WIP). Personally, I do not configure application policies for Windows 10. I usually just configure app policies for managing mobile devices (Android and iOS).
I generally recommend that customers manage personal mobile devices using Mobile Application Management (MAM), vs. full MDM. And stick to MDM with Windows–corporate owned machines should be managed machines (and Windows is almost always corporate owned nowadays).
However, it is possible to create distinct policies here with respect to corporate vs. personal devices. That’s good to know–it means you can have different restrictions for a personal vs. a corporate owned Windows 10 PC (like restrict the ability to copy/paste/export on personal devices but not corporate). But then again, when you just start deploying these things without thinking about it too hard, you could run into issues.
How to create confusion quickly
To be fair, this was an honest mistake, and the offending policy wasn’t actually supposed to get created. But, mistakes are what life is really made of–that’s how you learn stuff.
Do you know what happens if you create an app policy for Windows 10 with the restrictions enabled, and apply it ONLY to personal devices?
Oh, and of course, I forgot to mention: not one Windows 10 device in this scenario has been joined to Azure AD or enrolled in Intune. They are all still just tethered to the local AD.
Any guesses how this turns out? Well, every device that is not joined to the Azure AD or enrolled in Intune is considered personal until proven corporate owned.

Therefore, the restrictions will get applied. And users who attempt to copy/paste, save or open encrypted content will get some really strange error messages that they don’t understand.

Email attachments might not open or save correctly to local media. In fact it wouldn’t even allow saving to OneDrive. Hm… You will not be able to drag and drop or copy content out and paste into other apps, even notepad. You might see stuff like:
- Your organization doesn’t allow you to use work content here
- Either your organization doesn’t allow it, or there’s a problem with the file’s encryption
- There was an error opening this document. Access denied.
- You find that you can only browse to certain locations like SharePoint in Edge or IE (not Chrome or Firefox)
- Can’t open attachments
- And other issues
Looking under the hood
You can see the WIP settings at work in your apps in real time. Open Task manager, go to the Details tab and add the column for Enterprise Context. Here you can see which apps are running as personal vs. corporate.
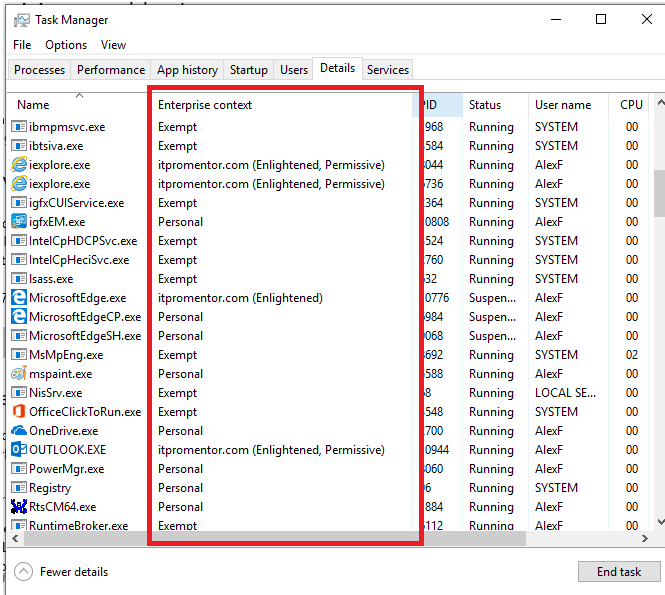
- Corporate apps: when you see the domain name (e.g. itpromentor.com) it means that the app is being managed by the corporate entity, and its data is protected from personal apps
- Enlightened means that the app can also distinguish between multiple accounts and data types. You could have personal and work email, for instance, within Outlook.
- Permissive appears to have something to do with how files are encrypted–but there is nothing definitive published by Microsoft. I do see that it is possible for developers who are writing an “Enlightened” WIP app to either enable Permissive mode or disable it. But there is no explanation for these terms anywhere in their support documentation or on MSDN, that I could find. Would love to learn more about that–let me know if you find anything out there, or happen to talk to one of the developers.
- Personal means non-business related, these apps cannot interact with business apps and data
- Exempt means that WIP just doesn’t apply to these apps (e.g. system processes) — and these processes can interact with both personal and business apps alike
By the way, if you’re poking around in task manager, you might notice that Teams is not going to be among the corporate protected apps–it is labeled as personal. Neither is the OneDrive desktop client categorized appropriately.
What? OneDrive is clearly included in the protected app list via the Microsoft 365 admin center, so what gives?

Go look more closely at the Protected apps in the same policy via Intune–it is indeed protecting the OneDrive (Store app), but not the OneDrive (Desktop client), onedrive.exe. So that explains why we couldn’t save to OneDrive, for example–because it was considered a personal/non-corporate app, and you can’t save corporate data to personal apps when this policy is on.
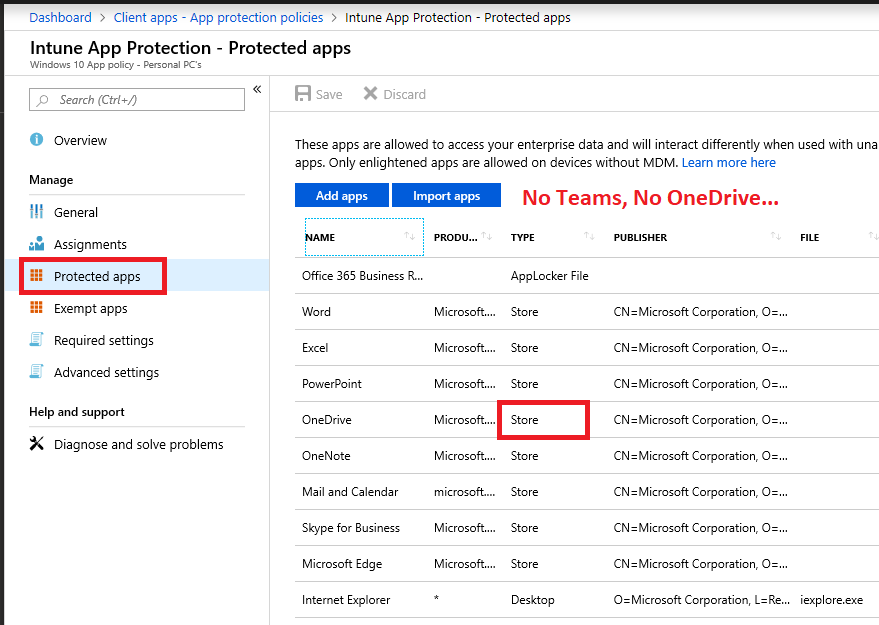
Fixing this would fix at least part of the issues. If it were a legitimate home or BYOD user scenario, you’d want to get this right (and it seems like an oversight on Microsoft’s part not to include both Store and Desktop versions of their software in these policies, from the 365 admin center).
Protected Apps > Add apps. Some like OneDrive are already pre-populated under Recommended apps, but there is the consideration for Desktop client versions of winword.exe, excel.exe, outlook.exe and so forth.
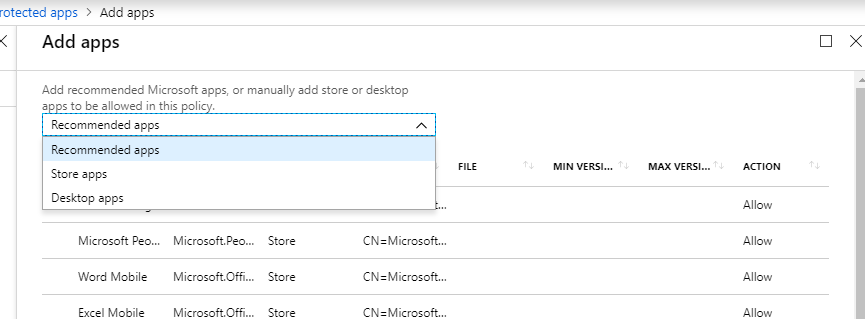
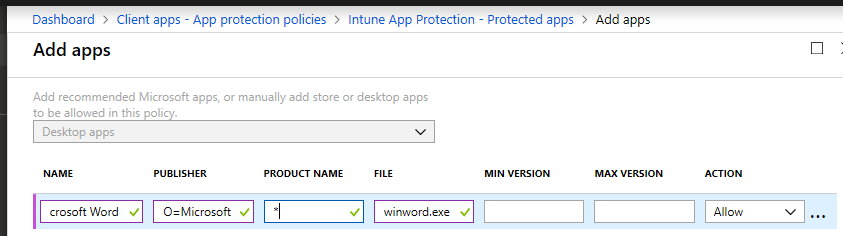
Regarding Desktop apps, to set those up, you would use the same Publisher as you see for the other desktop apps:
| O=Microsoft Corporation, L=Redmond, S=Washington, C=US |
Just fix it!
So we learned some cool things so far, about how we might do this the RIGHT way, if we were going to do it at all. But, given our actual problem here you might say: “Alex, you’re overthinking this stuff. Just go delete the policy–you don’t want it, don’t need it, just blow it away!”
Sure, that could work. Deleting is one option–in this case the preferred option since it was “accidentally” published to all users instead of just as a pilot. But, you could try to modify the policy, instead. WIP is not all bad news, after all–it will also encrypt at rest corporate data that resides on the endpoint, whether you restrict the copy/paste/export functions or not.
I like that, especially if you haven’t gotten around to deploying Bitlocker org-wide yet. It’s worth learning a little more, anyway. Find Required settings and change the Windows Information Protection mode setting from Block to one of the following:
- Allow Overrides (just like it sounds)
- Silent (no restrictions, actions are logged only)
- Off (no restrictions, actions not logged)

I will choose Off. Be forewarned–whether you update or delete this policy entirely–it may take a while to kick in for everyone. I haven’t been able to find anything official in MS documentation about how often client apps check in for policy updates, but in my recent experience, it must be a pretty dang long time (delete policy on Friday afternoon, still some users reported the issues Monday mid-day). Or their client was just hung up on the update.
If you have ever worked with Intune for Device management, the first thing you might want to try in order to shake the new settings loose is Settings > Accounts > Access Work or School, then to the Info on the connected corporate account, and hit Sync. After all, this is a good way to resolve issues with compliance or device configuration policies when using MDM. You will have no luck here, though–even if it happens to be a managed device and you are using a corporate WIP policy (not personal).
And that should make sense. Because we are looking at more of a MAM rather than MDM function with WIP. No device enrollment is required to use MAM/WIP policies. That is in fact what distinguishes the two types of polices you can create here (corporate vs. personal is a distinction between enrollment vs. without enrollment).
Rebooting also doesn’t seem to trigger a forced update. But, signing out of the Office application and then back in again, or alternatively, disconnecting your account from Settings > Accounts > Access Work or School, then reconnecting, does seem to do the trick. Apparently when this happens, the token or whatever mechanism is at work in the background is refreshed.
As I was looking into this, I kept wishing there was some kind of equivalent to gpupdate /force, but for WIP, I am at a loss–nothing out there in the Microsoft documentation was helpful, and sign out /sign in is the only thing that seemed to do the trick. I have also heard from other sources that some instances of botched WIP require full reinstall.
Other notes, and what to do instead of Windows app policies
Look, I think these MAM / app protection policies have their place, and it is on iOS and Android. There are actually a host of limitations you need to be aware of if you plan to implement it on Windows (WIP). Plan carefully.
For instance, MS strongly recommends keeping to one user per device, and being mindful of data encrypted on USB or other storage locations. And, especially with regard to unenlightened apps, since they will treat all data as corporate and encrypt it, there are gotchas. E.g. if you ever go to remove WIP from these apps, you will likely need to uninstall/reinstall them. This is because they aren’t really aware of corporate/personal distinction: the entire app is just forced into corporate mode while it is managed by WIP.
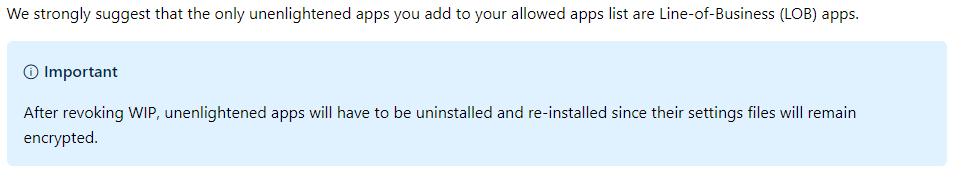
What I am reading there is that once you add WIP to an app you may not want to go back…or at the very least you’d want to be very careful about it.
Robert Crane of CIAOPS fame has some great supplemental articles to all the lame MS documentation out there that provides no real-world guidance on setting this up the “right” way. Check those out here:
- Adding Acrobat Reader as an Allowed app
- Windows Information Protection (WIP) in action
- Intune App Protection Policy blocking browser
He even covers some of the “advanced settings” which I didn’t get into here.
At the very least, what this all has taught me is that if you are going to do WIP, make sure you know why you need to do it, and that it is your best option. Then go in with a solid plan and review every setting that is exposed via Intune–make sure you understand what they mean before you proceed into implementation. It is worth piloting it first with a subset of users, if it is your first time.
Otherwise, I have found that MAM is perfect on the MS apps for Android and iOS. But here is what I recommend for Windows devices if you are sufficiently scared away from WIP:
- Conditional access policy to require compliance (Device management)
- Manage Windows using Compliance policies and Device configuration profiles to enforce and restrict settings related to BitLocker, OneDrive, Windows Defender, etc.
- Allow Web browsers from unmanaged devices to access resources like OWA, SharePoint Online, etc., but still protect that access with MFA.
- And yes, you should know that with Conditional access session controls it is also possible to limit SharePoint access and prevent downloads from document libraries on personal devices.
In this configuration, your corporate Windows endpoints are actually well managed, and without the extra baggage of WIP. The experience on unmanaged devices is just a bit more limited (think web access only, no downloadable content). Compared to WIP, I still think this is to be preferred as a balance of usability/security. But what do you think?




Comments (8)
Yes! MDM, MAM, WIP – feels like tricky stuff. We (which means I) thoughtfully set MDM and MAM to apply to all users… which, considering that we do not have high enough licences for all users, meant that AAD device registration started to fail. Strangely, another admin who did have all the security licences was also unable to register new devices using their account until MDM and MAM was set to none. We will need to carefully revisit MDM and MAM to secure our high-risk users.
But, hard to get the usability and security balance right – our company does not need to protect our data, but we do have a higher level of exposure to hacked accounts – so trying to lock down accounts while still allowing freedom of sharing information is a learning process.
Hi Alex,
Great article!
Question: As far as I know, WIP is not supported on Windows 10 home (https://www.microsoft.com/en-us/windows/compare-windows-10-home-vs-pro). But you mention the following in your comments: “So many *Home edition* users out there may be using Desktop apps, to set those up, you would use the same Publisher as you see for the other desktop apps” – does that mean that WIP is working on Home editions as well?
A follow up question would be, if there are Windows Devices not supporting WIP – how can we block them from accessing company data? I assume using Conditional Access, but haven’t found an option yet to select WIP enabled apps and only allow those access to company data. So I assume we have a GAP here and the only option is to either enrol the device (checking for compliance) or only allow browser based access to the corporate data. I’m very interested to find out your experience on this subject.
Thanks in advance,
/Kenneth
Just to note , Windows 10 MAM policies only apply to devices joined to Azure AD , or Hybrid Joined via Local domain or they do not get a policy : https://imgur.com/a/A8kVgbF
Actually you can publish a WIP policy against either an enrolled or non-enrolled device. Depends on how you set up the policy. However, even Microsoft is not recommending WIP anymore–they have angst internally over it, and my understanding is that something else is coming soon to replace it, but I still have not heard details as to what. The overwhelming response to this product is that the impact on user experience is too great for the benefits it delivers.
The file ownership menu item , will only appear on your computer once you add your PC to Azure AD for that organization, you don’t need to enroll in Intune , but it needs to be joined to azure AD to get the MAM/WIP policy, without this the device never shows in Intune as devices either so you won’t be able to wipe
Interesting to know what’s next, this is a cheap way for organizations to restrict company data , AIP is expensive E5 for autolabelling and RMS has its limitations
Excellent Article, Alex.
Any update on new service to replace WIP, not having a great experience trying to roll it out in Silent mode. Teams getting blocked (when in Allow Override) and Enterprise Icon always showing even though its Off (Silent or Allowoverride). Also had issue with the original DRA cert deployed with an AD Domain being in place but expired.
The replacement is Endpoint DLP (which is an E5 feature sadly). They aren’t really developing WIP anymore is my understanding. I have been trying to get folks moved off “MAM for Windows” and just stick to MDM/device-based management. If Endpoint DLP is a hard requirement, the most cost effective path is the E5 Compliance add-on for E3. Or, use a third party solution. I have not heard whether they intend to release an E-DLP solution specifically for SMB (as they did with the EDR).