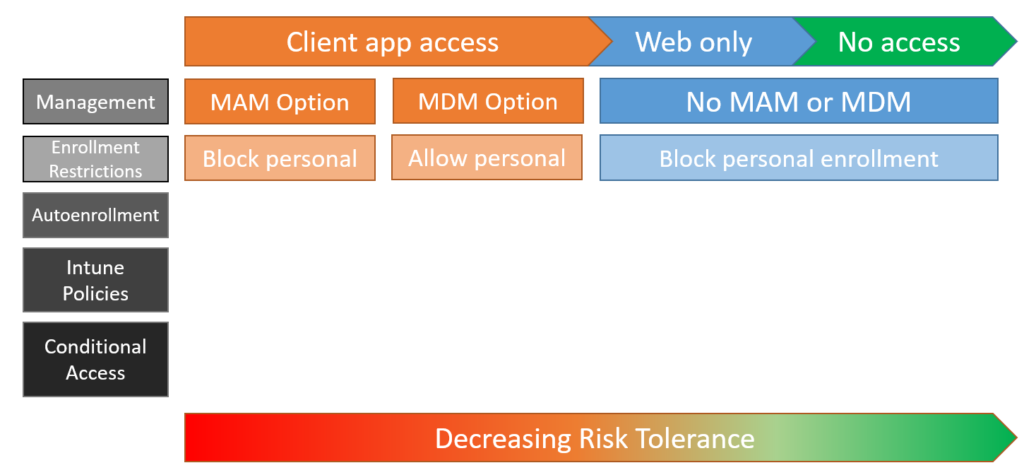
Choosing (and implementing) your strategy for personal devices
In a recent Microsoft blog announcing some cool new discovery features in Microsoft Defender for Endpoint, there is an interesting (but hardly surprising) statistic shared: your users are 71% more likely to be infected on an unmanaged device.
Now the thrust of the article is around discovering assets in your environment that are not yet being managed and exposing them, so that you can more easily remediate (even automating that remediation in some cases). Obviously these are all E5 features targeted heavily toward the Enterprise, but the message should not be lost on those of us in the SMB space. Device management is not something you should ignore.
In my personal experiences serving the SMB and helping others who are doing the same, right now the largest concern is around personal devices. Not just mobile devices, but also laptops and desktops, especially after last year’s Mass Exodus from the office, and dramatic shift toward working from home (or you know, wherever… for example, I just got back from spending a couple of months at a remote ranch in the southwest U.S.).
Anyway, to that end, I think it is massively important for us to be reaching out to our customers and really highlighting this problem. We have many options for reducing risk when it comes to personal devices, even in the Business Premium subscription:

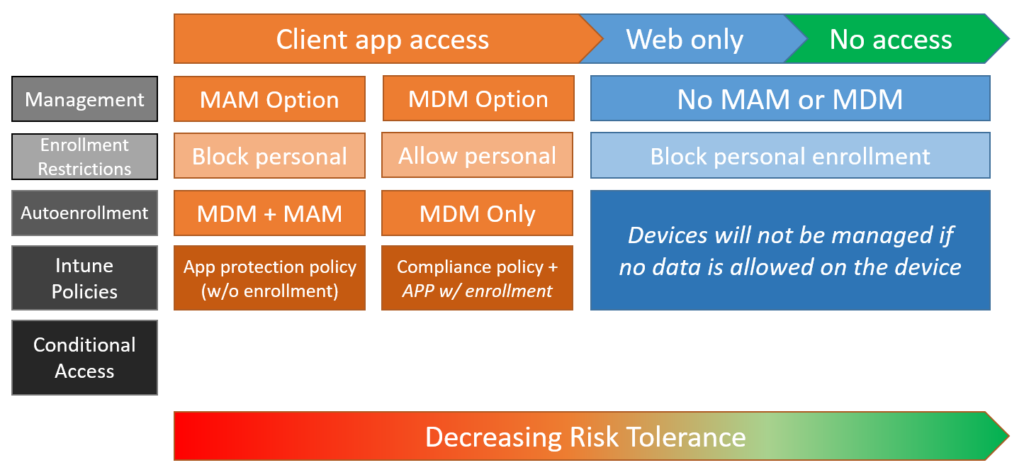
Obviously the least amount of risk (far right side of this image) would mean blocking all access on personal devices. This may not even be feasible for some SMB customers, of course. We are seeing year-over-year increases in demand for BYOD, and after the pandemic lock downs kicked in last year, this number increased suddenly and dramatically. The speed with which we were forced to react to these new demands meant that we did not always have time to address security concerns in making this transition work, and work quickly.
So if you haven’t yet, please circle back around with your customers and revisit this issue. Even after folks return to pre-pandemic conditions and habits, I suspect there will still be many lingering personal devices out there that are unmanaged and connecting to corporate data and resources.
What do I recommend?
As regards the other options for management (which still allow for access to company apps and data), we have:
- MAM – Allows for client app access but provides very little in terms of device-based security or controls
- MDM – Also allows for client app access and provides more capabilities (e.g. push your endpoint security policies and agents down to the devices)
- Limited web-only access: Does not allow client app access, and prevents data (e.g. email attachments, OneDrive files, etc.) from being downloaded over the web.
My personal favorites right now are MAM for mobile devices, and MDM for MacOS/Windows 10 laptops and desktop computers. MAM for iOS and Android technically still gives us “Conditional Launch” settings for the applications whereby the app will not launch if the device is jailbroken or rooted, or cannot meet a minimum OS level. You can even integrate MAM with Defender for Endpoint now, so that the threat level on the device can prevent application launch.
We do not have equivalent capabilities with MAM on Windows (and zero MAM capabilities on MacOS). Therefore, I still lean toward MDM for laptops and desktops, so that we can further reduce risk through device-based controls and pushing our security software/agents down. As well, we still see more threats such as malware and ransomware on laptops and desktops that lead to major incidents and business disruption. I have not personally come across similar for mobile devices yet (not to say these things don’t exist, I just haven’t heard of it yet in the customers that I serve).
So for now that is where things stand for me.
Setting up your preferred option
Most folks still do not set up the various options correctly in Microsoft Endpoint Manager, so let us cover off on the configuration for each quickly.
Enrollment restrictions
The first decision that comes to bear on these options is whether to allow personal devices to be enrolled with the Intune service.
If you are choosing to go with the MAM option, or the web-only option, you would need to configure the Device enrollment restrictions to Block personal device enrollment. Do this from Devices > Enroll devices > Enrollment restrictions.
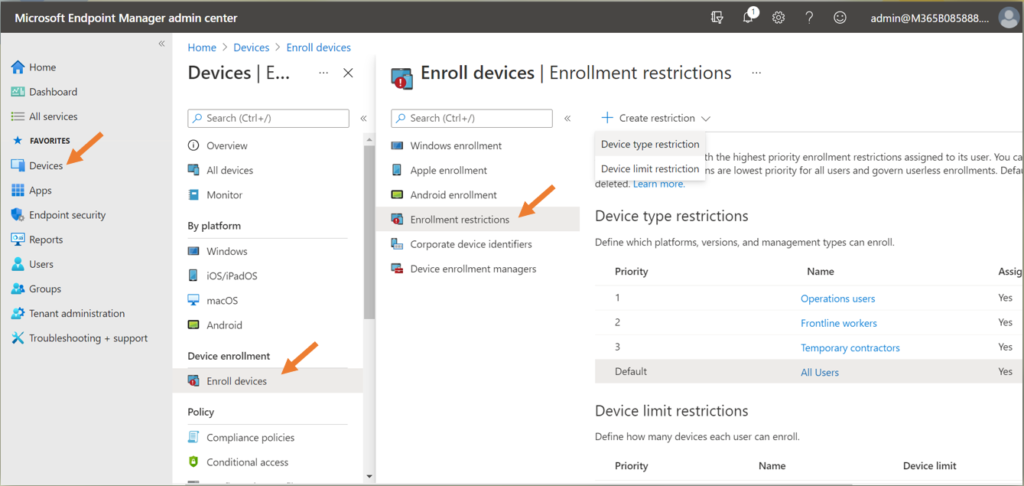
You can either edit the default (All Users) Device type restrictions policy, or you can Create your own restriction policy for specific users and groups. For example, you might have different restrictions defined for different types of workers (frontline, Ops, etc.).
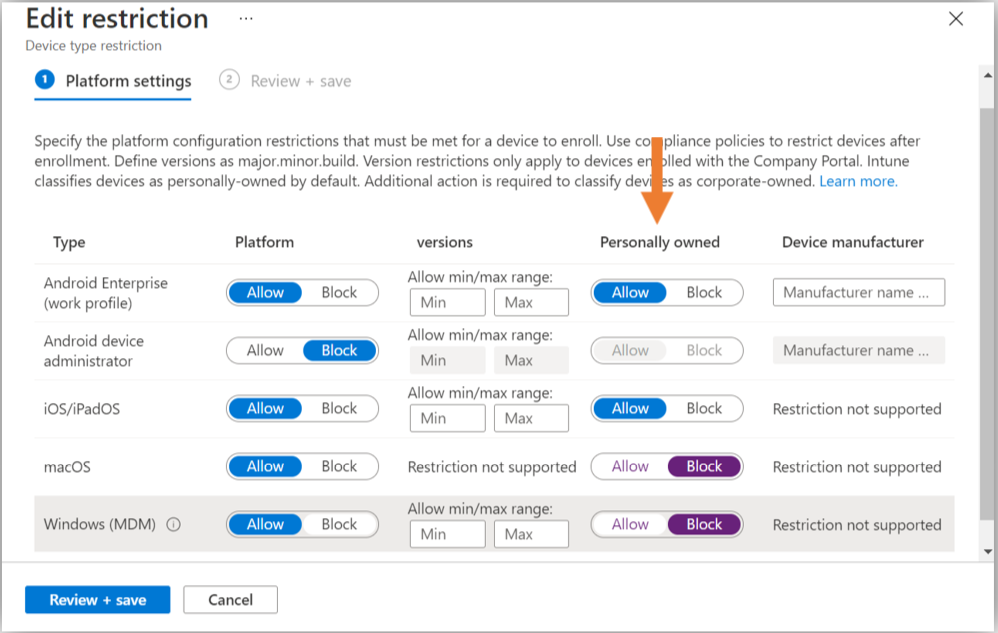
Pro tip: If you choose to target individual users and groups, then be sure to also edit that Default policy and set all the platforms to Block for personal enrollment (so that you are only explicitly allowing it for specific groups). That way someone doesn’t slip through the cracks if they don’t belong to one of the other defined user groups.
Autoenrollment settings
The next item up is Autoenrollment. This applies to Windows 10 in particular. You can set up “autoenrollment” experiences for other device platforms (e.g. Apple Business Manager for Company-owned iOS devices), but for Windows 10 we have a choice to make between asking devices to be managed by MAM-only or MDM.
Windows MAM policies turn on a feature called Windows Information Protection. These policies, in my opinion, are not that great for unmanaged devices. But you can still apply the MAM policies if you want to, even if the device is being managed. And, since managed devices allow us to do slightly better with these policies (e.g. protect non-enlightened apps), I would argue there is no good reason not to enroll for MDM (even if you want to use Windows Information Protection on top of that).
Anyway, navigate to Devices > Enroll devices > Windows enrollment > Automatic enrollment.
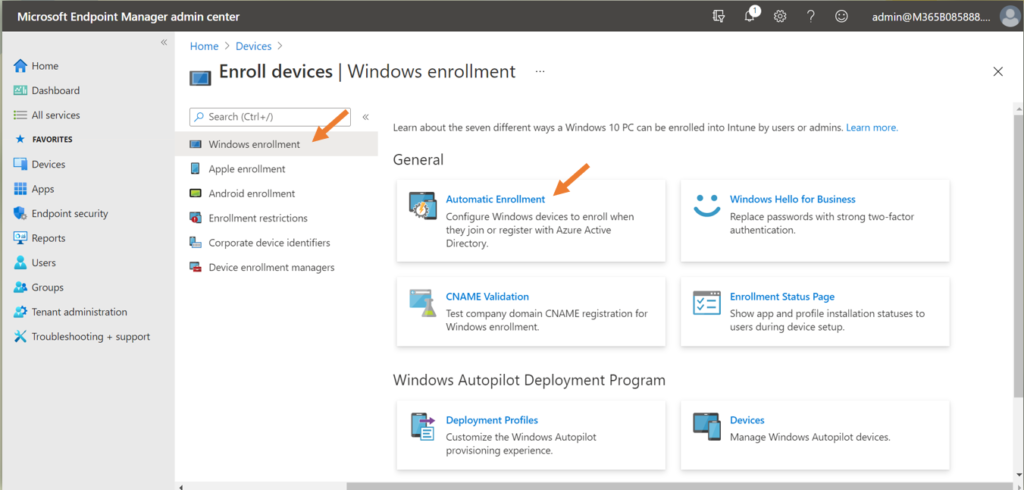
There are two ‘scope’ options here; one is for MDM and one for MAM.
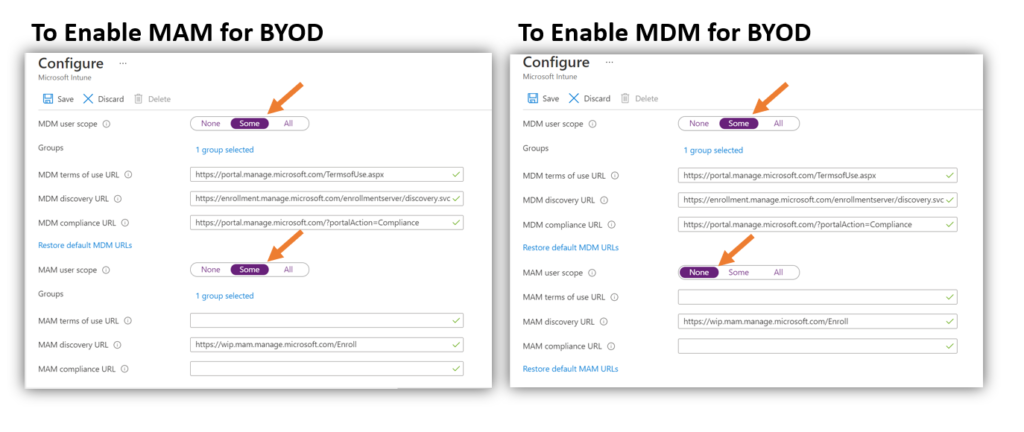
Here is the meaning of these scope options:
- If you configure only the MDM scope, then the users you target with that policy will automatically go down the MDM enrollment path when they Azure AD Join (corporate) or Azure AD Register (personal).
- If you configure both the MDM and MAM user scope, then the users who are targeted in the MAM scope will automatically go down the MAM enrollment path instead of MDM on personal devices only. Corporate devices (Azure AD Join) will always prefer the MDM enrollment over MAM.
Therefore, as you can probably guess, I never configure the MAM scope (because I push all my customers toward full management via MDM).
Intune policies
After the autoenrollment is done then it is time to set up the policies that will enforce your desired settings. For MAM, this means deploying App Protection policies (these are your MAM policies). Find them from Apps > App protection policies. When you work with Windows 10, you can deploy these Without enrollment (just MAM and no MDM) or With enrollment (when you also leverage MDM for management).

When you go down the MDM path, as I recommend especially for Windows and MacOS, then you need to create at minimum a Compliance policy (Devices > Compliance policies) that will measure whether the device meets certain requirements that you get to define, such as minimum OS, antivirus, firewall, etc.
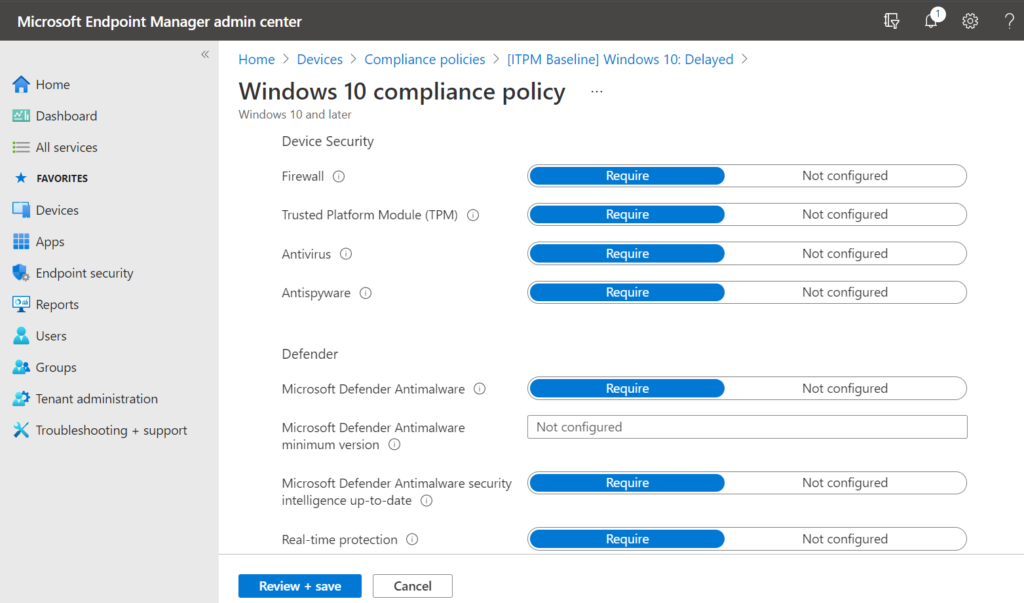
Optionally you can enforce other settings and profiles on the device, but a compliance policy is the minimum. And note: Windows 10 devices should be at least Pro (no home editions) whether you are doing MAM or MDM.
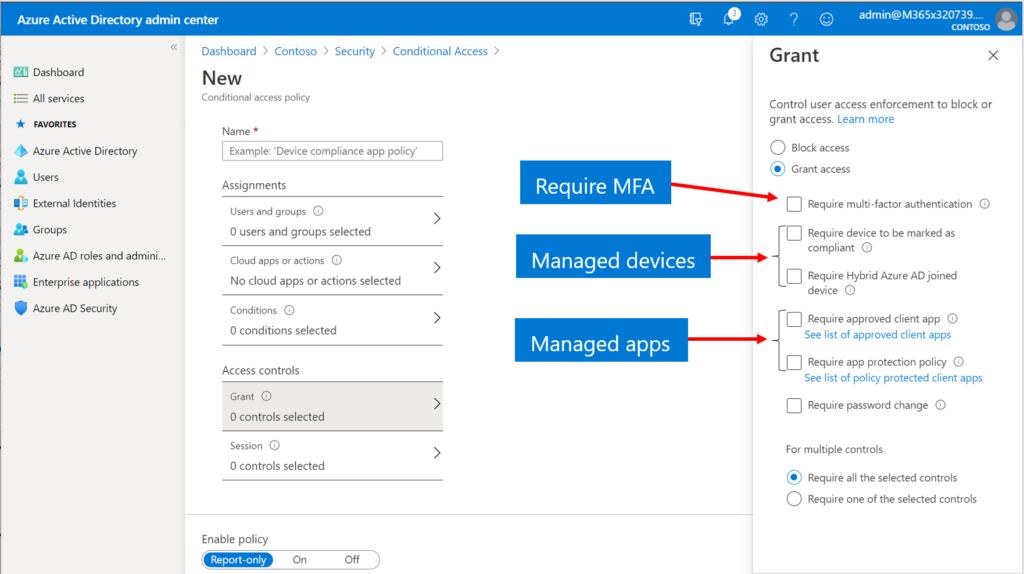
Conditional Access
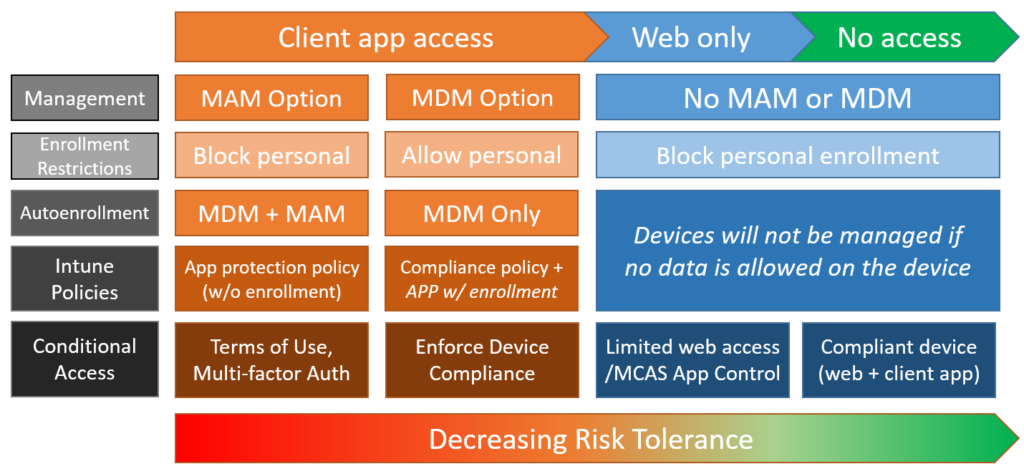
Last move to Devices > Conditional Access. When you are enforcing MAM, you should at least require Multi-factor Authentication (MFA). You may also want to require the users to accept a Terms of Use describing the company’s policy around corporate information on personal devices, although this is optional. And, when you are targeting MAM against mobile devices (iOS and Android only), then you can also enforce the use of managed applications.
Skipping over MDM for the moment, to enable the limited web access option, we have a ‘Session‘ access control called App enforced restrictions and a couple of commands that you need to run via PowerShell: one for SharePoint and OneDrive, and the other for Exchange Online.
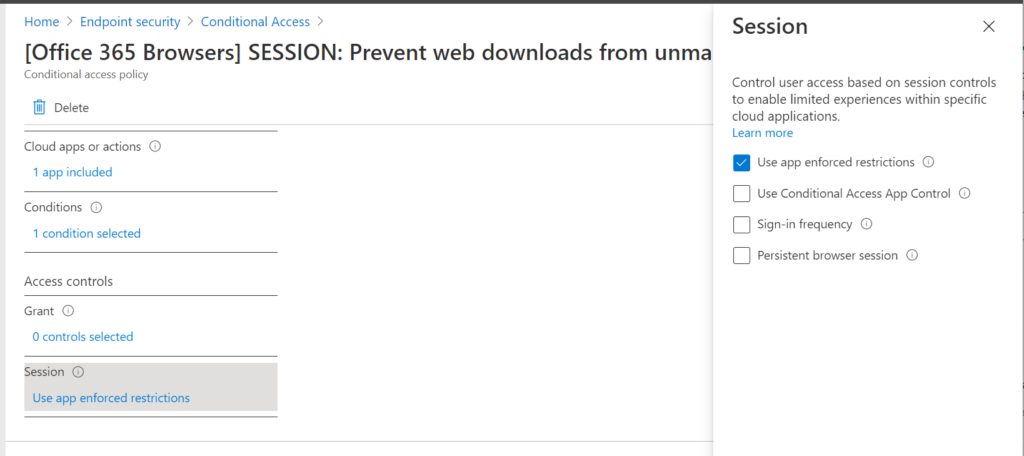
A warning about this: when you run the commands for SharePoint Online it automatically creates CA policies for you and enables them, which I find sort of annoying. Exchange Online does not do this. (So you have to go create a policy anyway; I wish this was consistent behavior between SPO and EXO. I prefer to create these policies myself, so that would be my vote, and just give us a little reminder in the PowerShell output after running the command, or if you are going to autogenerate policies then leave them disabled for crying-out-sideways).
Now when it comes to MDM, you would want to enforce device compliance for at least mobile app and desktop client access (since these apps sync data to the local device). You can optionally choose to target browsers as well under Conditions > Client apps in your policy. And if you are blocking personal device enrollment and you only want corporate owned and managed devices to access the cloud apps and data, then you would need to choose both client apps and web browsers.
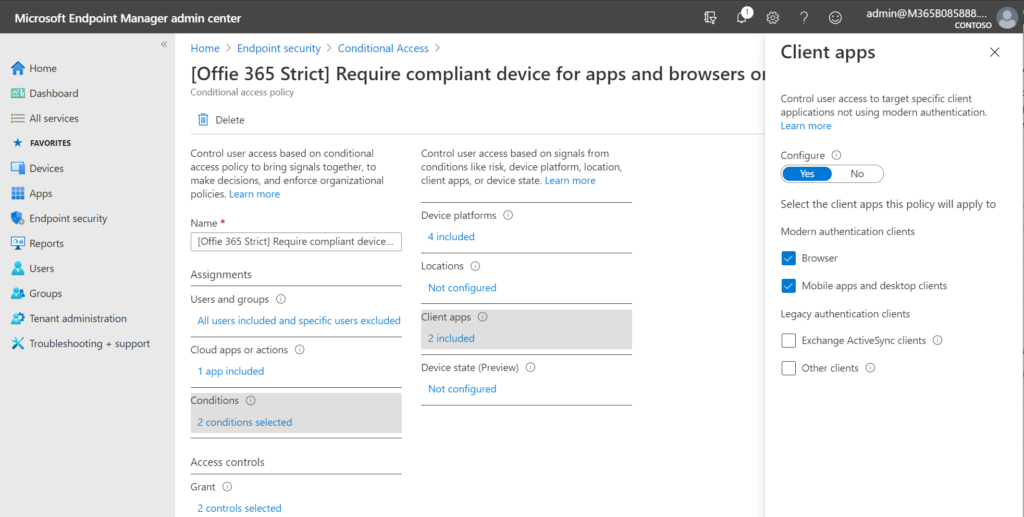
Aside: You can import my recommended baseline conditional access policies to ease this work and make the policy creation more repeatable with less chance for error.
Conclusion
In the E5 subscription we technically have even more options with Microsoft Cloud App Security and Conditional Access App control policies, but most SMB’s will be well served even without those options, and sticking to the ones we discussed here.
I wish I didn’t have to harp on this point so much but I hear from folks all the time who get themselves into bad situations because they ignored device management. I have personally been called to help on two different incidents since the start of the pandemic where a personal device was the initial entry-point for an attacker. And if you have ever worked on incident response, you know that one of the most frustrating parts of the job is needing to fix visibility issues before you can even start the real IR work. When sh*t hits the fan, as they say, we defenders much prefer to have the proper tools in place before we get started on response and clean-up efforts. It adds a lot of cost, uncertainty, and extends business interruption when we do not have an accurate inventory from the start. And remember that statistic from Microsoft: you are much less likely to be infected on a managed device anyway, so go out and get this stuff done with your customers. It’s good money, and good work.





Comments (4)
Very informative. Are there any other licenses that you add on to your Business Premium clients to provide some of the additional security features that are available with E5 but not BP? I find that I am continually frustrated by the BP clients not having access to some of the features I would like them to have.
There are two main security-related products I like from MSFT, with some reservations still. The first is MCAS–this is an essential add-on in my opinion for any org with a cybersecurity practice. The second is Microsoft Defender for Endpoint, however in my opinion this is not SMB-ready today. We really need multi-tenant data from the endpoints, which they are working on but it can’t come fast enough. In the meantime, most providers are leveraging third-party EDR products. If/when they get the SMB version right though, it’s going to be huge, because MDE is a great product.
Are there other things you are missing/wishing for??
I’m a little confused about the “Edit Restrictions” Screenshot. I agree with your “personal favorites right now are MAM for mobile devices, and MDM for MacOS/Windows 10 laptops and desktop computers”. But doesn’t that mean the block/allow settings would be just the opposite of this screenshot?
It seems like we’d want to block enrollment for BYOD iOS/Android since our strategy is MAM, and allow enrollment for Win10 and MacOS. Am I seeing this correctly?
Thanks much for all the amazing work you do, and for providing it to us all so generously. Huge help!
Correct, you want to block personal enrollment for platforms that you do not intend to enroll and manage using MDM. The screenshot is just an example configuration, and in the text above it I am explaining that you could have multiple restriction profiles for different groups of users. For example, with some users you may not even allow them to use BYOD Windows/Mac devices (e.g. Frontline types, etc.).