My opinion on Microsoft Threat Protection for the SMB
Since I released my guide on Microsoft 365 E5 Security and Microsoft Threat Protection, I have been getting a lot of questions and comments about my stance on the use of these products for SMB customers. I left it too neutral, I guess, in the original publication. So, let me take this opportunity to clear the fog, so to speak.
First, realize that these are just security products–they don’t equal good security on their own–you can only reach good security through having a good security practice, following the principles of good security like those laid out in common frameworks e.g. CIS or NIST CSF. Assuming you have laid a good foundation by following one of these frameworks, now you can start to employ tools to help you meet some of the goals and mitigate certain known threats and risks.
Second point, like every product, there are benefits and drawbacks to Microsoft Threat Protection. So you can pick the tools you like best to give you the coverage that you are looking for. I like to be as transparent as possible about strengths and weaknesses, so here is how I see it. Let’s review the products included in the E5 Security bundle.
Which of these do you really need the most?
- Azure AD Premium P2 – Cloud identity protection
- Office 365 ATP P2 – Email/links/documents/phishing protections
- Azure ATP – On-premises identity threat detection
- Microsoft Cloud App Security – CASB/cloud app detections/response
- Microsoft Defender ATP – Endpoint detection & response
So all of these various tools give you coverage over a different domain or area. Azure ATP covers legacy identities (on-prem) vs. Azure AD Premium which watches over your cloud identities, and MDATP covers endpoints while MCAS covers your cloud apps, etc.
So when it comes to Microsoft 365 Business Premium subscribers, I would argue that the most interesting or “important” of the above products really comes down to the endpoints and the cloud apps (MDATP and MCAS). Most SMB’s are trying to ditch legacy AD domain infrastructure in favor of having 100% SaaS subscriptions and centralized management with Azure AD Premium and Intune. Therefore, Azure ATP isn’t necessary if you’re going to shed that weight. As well, I would argue that SMB customers already have the features they want the most from Azure AD Premium P1 (e.g. device-based conditional access, MFA, etc.) as well as Office 365 ATP P1 (sure, the full Threat Explorer would be nice, but the Attack simulator is blah, and they can keep the other stuff in P2).
Therefore, taking a long-view, I am most interested in MCAS and MDATP, which together are less than USD $9.00, which is less than the E5 Security SKU. So that’s just my opinion as regards the “value prop” of the whole bundle vs. these other standalone items.
MCAS is my favorite, and the reason may surprise you
Now, realize that both of these products have competitors in the wider marketplace. There are many vendors who sell CASB as well as EDR solutions. Personally, if I could recommend just one of these two, it would be MCAS–this is my favorite security app right now from Microsoft 365. Not only does it give you mad visibility into the “goings-on” of your native M365 cloud apps, and the ability to create custom alerts, but also you can connect a myriad of popular SaaS apps too, like Box or GSuite. Not only that, but you can auto-apply governance actions such as sending an alert, suspending an account, applying an information protection label, or kicking off a Flow in PowerAutomate.
But the feature that really helps MCAS stand out to me the most, is the ability to customize the email address from which alerts are sent. Literally no other product in the Microsoft security universe allows you to do this. Most of the time, where you have the ability to send an email alert, it will come from [email protected]–so lame.

And this seems like such a simple thing, but when you are an MSP managing so many different customers, it’s everything! Having a uniquely identifiable “from” address (e.g. [email protected]) means that your alerts can be identified automatically by your ticketing systems and associated to the right client. Super important. I wish we had centralized alerting the way we are starting to see a centralized place for incidents “roll up” into the new Microsoft Security center (https://security.microsoft.com). I would want the alert capabilities from MCAS to be the gold standard (highly customizable + come from unique vanity address).
Pros and Cons for MDATP
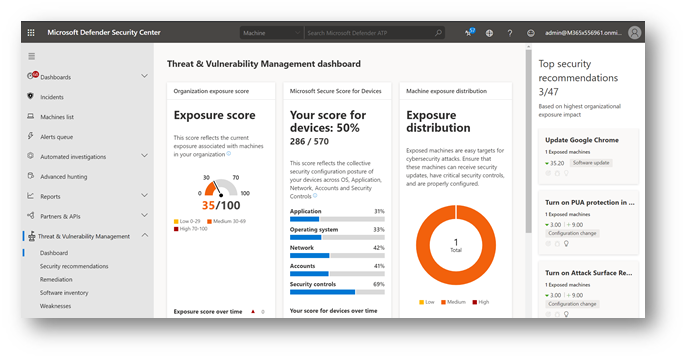
With regard to the EDR product, I actually love MDATP. Such a great product–including Threat & Vulnerability Management, having actual feedback on the threat level of each device, as well as being able to see incidents, a timeline of events on the endpoint, etc.–even what’s happening with some of those Attack surface reduction rules–it’s great! But, the reality is that many MSP’s today may be better served by a different EDR solution, which supports multi-tenancy. Some vendors even sell directly to MSP’s and offer bulk licensing discounts (so if you are buying hundreds or even thousands of seats you get a bigger discount).
Even so, if I had my first wish, which is centralized alerts that follow the MCAS model, where you can bring a custom vanity “from” address, then I could wait patiently for multi-tenant views in MDATP, but start deploying anyway, knowing that our alerting is on solid footing.
I’ve already stated the biggest drawback, and on the flipside, the greatest benefit I believe is that the solution is agentless (for Windows—obviously on MacOS, etc. you still need to install it). All you have to do is configure a policy in Intune that tells the device to phone home its endpoint data to MDATP in the cloud. Super easy onboarding and would save MSP’s a lot of work.
Now some EDR products also give you extra goodies like Application Whitelisting, and honestly 3rd party products in this space are usually easier than deploying AppLocker, or even its simpler cousin AaronLocker (if we’re looking at the Microsoft side of things). But then again, using Intune you could also enable Application Control (the “easy button” for whitelisting, as I like to say). This feature is even supported for Windows 10 Pro.

As well, Web Filtering is another feature that just made the list in MDATP, and has been available for some time in third-parties. So the gaps are certainly closing more and more–and MDATP is starting to look like it might be able to pick up more steam and traction in the marketplace–even, I would suggest, in the SMB space (assuming we get better alerting/multi-tenant features).
The products are better together
The last point I want to make about Microsoft Threat Protection is that the various products are all becoming more tightly integrated with one another. This is not just marketing–for example you can share data between MDATP and MCAS, and use MCAS to block unsanctioned cloud apps to fight back against shadow IT!
Or, get this: through the Intelligent Security Graph, if MDATP identifies a suspicious file that kicked off a series of unfortunate events, it can communicate that information back to Office 365 ATP and ask it to “ZAP” that file from any mailboxes, if it is an attachment that made it past the filters, for instance.
Crazy cool, right? So the other value proposition in the Microsoft story is that these tools are awesome on their own–yes–but they are even better when used together. And it’s continuing to evolve as a single integrated solution under the banner “Microsoft Threat Protection.”
What’s still missing?
Okay, Alex, so you would take at least MCAS and MDATP (or some EDR) and make those a pretty standard thing for SMB orgs trying to go “cloud-only.” I think I get it, but… what am I missing? Isn’t there anything else besides a CASB and EDR that you would want?
Yes. Thank you for asking, imaginary reader who lives inside my head and pesters me daily.
A couple of things come to mind. I personally think that SMB’s can benefit greatly from some End User Security Training and enforcement materials. Office 365 ATP P2 has an “attack simulator” where you can design and send fake phishing emails, but it lags significantly behind competitors like IDAgent and KnowBe4.
So I may still seek out some third-party stuff–always good to have another vulnerability scanner to keep your primary toolset honest, maybe some dark web monitoring, maybe even a better Endpoint DLP solution (WIP isn’t quite there yet), etc., etc. But that list right there would satisfy 99% of the wish list, I think, for a more “complete” toolset.
And if you want to get really serious, then add Azure Sentinel, a cloud-native SIEM, to suck all the data from these disparate tools into one view and make it searchable/huntable–if you are ready to take your security practice to the next level. But of course, remember that the customer always has a choice, and not all of them may care to spend the money it takes to cinch up and address all the various risks and things to the highest degree. And that’s okay, too.



Comments (2)
Hi,
Will you be doing a series or blog on MCAS best practice/configuration?
Yes. That sounds like a great idea. Will add to the list.