We need “MDATP Lite,” not full MDATP, in order to complete Defender’s value proposition in the SMB–and this is what it looks like
TL;DR: Just give me the device risk level with a description of “why” so I can follow up with potentially at-risk users. You can keep Advanced Hunting, etc.
So many people I talk to in the SMB community think that they want MDATP. Well, it is available now as an independent add-on that is compatible even with the (recently renamed) Microsoft 365 Business Premium subscription… but if you had this tool, would you really use it to its full extent? My guess would be no.
Before we go further, let me quickly distinguish between two different but related things that I think are at the root of many a person’s confusion:
- Microsoft Defender – this is the software on the endpoint that applies protections like Antivirus, network protection, attack surface reduction rules, controlled folder access and more
- Microsoft Defender ATP – this is not software on the endpoint at all per se, but rather a cloud-based service that collects data from the Defender-protected endpoints and presents that data for you in a more consumable, searchable format (and yes, exposes some other controls over the devices)
To be clear, today we don’t really have any meaningful feedback in the Intune portal re: the status of Microsoft Defender clients. But with these terms laid bare, here is the main feature-set of the MDATP cloud service that I think could actually be used by SMB customers (including MSP’s who manage SMB customers), summarized in one screenshot:

Note: to get this data populated you need to on-board your devices into the service.
This depicts the Microsoft Defender Security Center, and I am focused on the Machines list (although slices of this data also exist in other places like the incidents and alerts queue). Here we can see a listing of devices in the environment along with a corresponding Risk level–probably one of the only data points I care about, other than machine identifiers, OS patch level, etc. Now this demo tenant just has a couple of devices we can pick on. But let’s select the device that shows a threat level of Medium. What’s up with that?
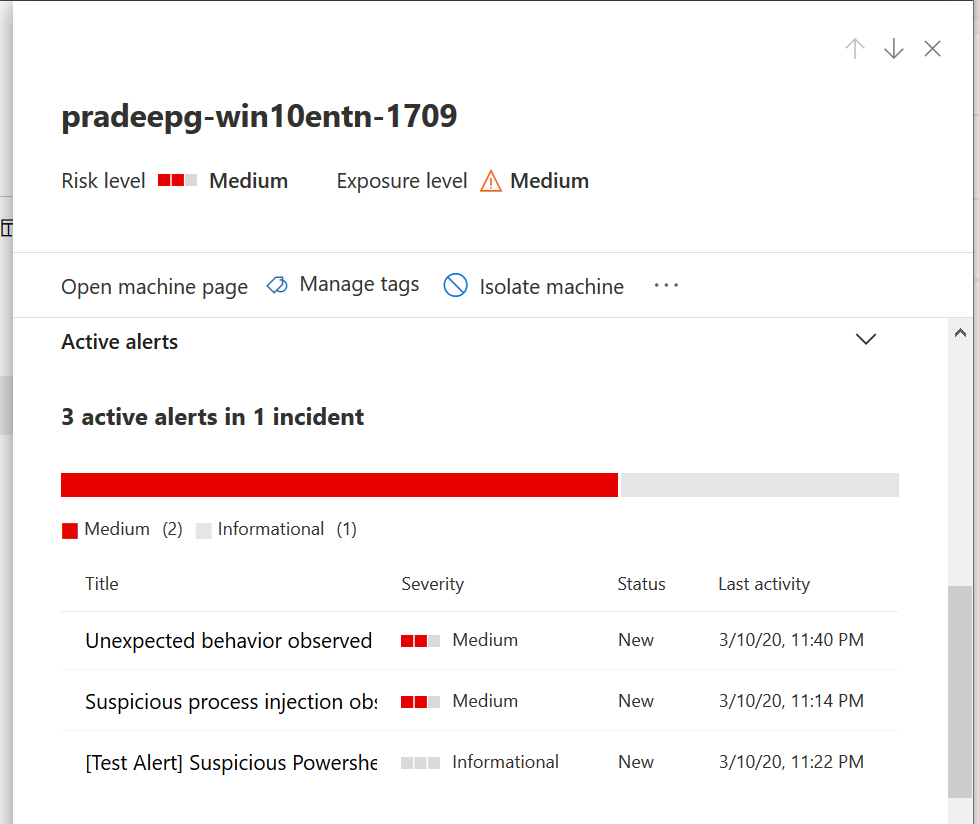
Scrolling down we can see three alerts here and we could click on each to get a bit more detail–you will see right here that there is an option to Isolate the machine at the top of the page, which we may want to do while we investigate further. I can see some unexpected behaviors and suspicious process injections have been observed. That doesn’t sound awesome, does it? Possible that some of these were thrown by Defender because Exploit Guard was enabled?

Basically this is giving us crucial visibility into potential post-breach indicators, with a small breadcrumb trail so we can go check it out and decide what remediation steps to take (if any). For example, you may decide to autopilot reset or wipe/reload a system that had a suspected breach incident.
A fair warning: you may see some false positives (FP’s)–I have already seen some even with common 3rd-party software packages like Adobe products. In this case you can just make an exception in Defender as needed. But whether it was a false positive or a real threat–this feedback loop is critical to both endpoint security and providing a valuable customer service, and every MSP should want this data so that they can follow up with at-risk customers.
The risk rating ties directly into our Compliance policies. For example, you can require devices to be at or under a certain risk level, or they get marked as not compliant; and if you are using Conditional Access–as you ought to be–that means an at-risk device loses access to resources instantly and remains that way until the issue is resolved. This is arguably one of the most powerful compliance settings available and yet it is very easy to configure and use–perfect for SMB’s with limited access to resources and talent.

The full MDATP service also has a bunch of other features, too, like Advanced Hunting. But most of this other stuff is simply not going to be touched in the SMB, for a variety of reasons–the main one is that these customers tend not to employ actual Info Sec people who know how to work with these tools.
Having a SOC, running Blue Team and Red Team exercises, etc., just isn’t happening today in the SMB. And even if a managed service provider had the talent, it would be difficult to implement a good practice at any sort of scale, since every tenant is isolated from every other tenant. Meaning that you have to run the same queries multiple times and go hunting in multiple portals.
Further opportunity for service providers…
That isn’t to say there isn’t a massive opportunity here–I think there is, if someone can figure out how to offer a full SOC service to existing MSP customers at an affordable price point that could be added on as a complimentary service to the rest of their stack, that would be great! But I just don’t see that happening today “in the field” outside of my own organization, which is admittedly an outlier (and we’re not doing it with MDATP). The full MDATP is of course still available as a premium add-on, for those who are interested.
Note that if you were ready for the full featured version of MDATP you would find some other cool integrations with the various products in Microsoft 365 such as MCAS, Azure ATP, etc.–but that’s again for the outliers–not your typical MSP or SMB of today.
My argument to Microsoft is that every Microsoft 365 customer both large and small should have the basic “Risk level” indicated to them immediately. I mean think about it–the data is already sitting there, we just need to have it exposed so that we can act on it–and what better way to enforce action than removing the user’s access when the device’s targeted risk level is exceeded?
You can even configure an email notification on device compliance failures, and the user would undoubtedly be calling the help desk to get put back together again. This simple measure alone would take us leaps and bounds from where we (in the SMB) stand today in the industry at large, and I argue, it would be a very good entry point into Security-as-a-Service for existing MSP’s of all sizes, helping the SMB customer and the entire partner channel to up their security game at the same time.
The only other ask I would have here is to bring this risk data from multiple managed tenants, along with other basic data around Intune devices, Compliance and so on, into a single pane of glass for partners to manage all their customers without switching into separate portals for each one. That’s a much bigger request obviously–but my fingers are crossed that we see at least some of this come to life. Otherwise, it’s just really hard to use Defender from a practical standpoint at scale–even though I know it’s amazing and I would love to be able to use/recommend it.



Comments (9)
Great article Alex! M365 Business Premium has quite a bit of security and yet little to no feedback in order to assist our customers in finding and then remediating any issues found. Yes, “MDATP Lite” is a great idea with reporting of threat risks. I also agree and so wish Microsoft would have a central partner admin center, in the MS Partner CSP Portal, to be able to manage all my customers M365 tenants.
It’s too bad that Microsoft has put a hold on their SMB new features and solutions. Which I guess includes anything that resembles what you are suggesting. At least according to this article below. What are your thoughts on this Alex? Have you heard anything Microsoft doing this?
https://www.thurrott.com/cloud/microsoft-365/234773/microsoft-is-hibernating-its-smb-efforts-because-of-covid-19
Not too worried about it. Most of us are using 3rd party AV/EDR’s at the moment and we can continue to do so. Microsoft will catch up eventually. But it makes sense to divert resources during this time.
Great post @Alex! Our IT team feels the same. We administer about 280 people spread across 10 offices around the world, so these kinds of security features are essential to keep tabs on everything – but we quickly get lost trying to figure out what is a problem and where. We were using the azure portal to see most security issues, but now with MDATP we can look into the defender portal… not to confused with the device portal or the protection portal or the cloudapp portal.
The only issue i have is that with compliance policies. With 3rd party AV, I am having issues with security center issues where the AV allegedly doesn’t report to security center. I would love to keep the compliance policy with integrated AV, but it only seems to work well with defender AV.
Totally! Due to weirdness like that, I am down to basically requiring a minimum OS level for the time being, which reduces the usefulness of compliance policies.
Totally reduces it. I do get a kick out of the partner presentation that windows defender is great, it is rather inefficent when there isn’t an easy way of managing it compared to the countless other cloud based AV products. I just wish that they work with compliance policies as they are fairly useless without them
They better speed up the improvements, other vendors are starting to catch up. Some AV programas are transforming in full security suites that include AV, OS and third party patching, risk management, EDR, etc. And the pricing is very competitive.
Recently I had to switch to another AV vendor and I was plesantly surprised by the value proposition of some companies. I’m also wary of Microsoft’s AV products, I’ve seen them fail too many times with really bad detection rates.
I do agree with you that even small customers should have a basic risk level indication, and some basic security tools should be there, like when they added conditional access to Office 365.
Do you think the new defender endpoint p1 helps here Alex?
That is only for E3, but today (Ignite 2021) they are announcing Microsoft Defender for Business, which is included in Business Premium, and is even better than P1.