Making sense of the many DLP options for Microsoft 365
One of my readers wrote to me recently about an article that I penned a couple of years ago, on the topic of Data Loss Prevention in Microsoft 365. They pointed out that my breakdown was a bit dated now, and that the Microsoft universe seems to have become more complicated since then.
I suppose that’s true in some ways. I think some of this confusion was multiplied by the fact that many (if not all) of these products have new names now, such as the recent rebranding of the “compliance-related” features to Microsoft Purview. The other confusion points tend to revolve around licensing: “What is included in my subscription, and what requires an upgrade?”
I wonder if I can help those who are seeking clarity by taking another stab at this from a slightly different perspective.
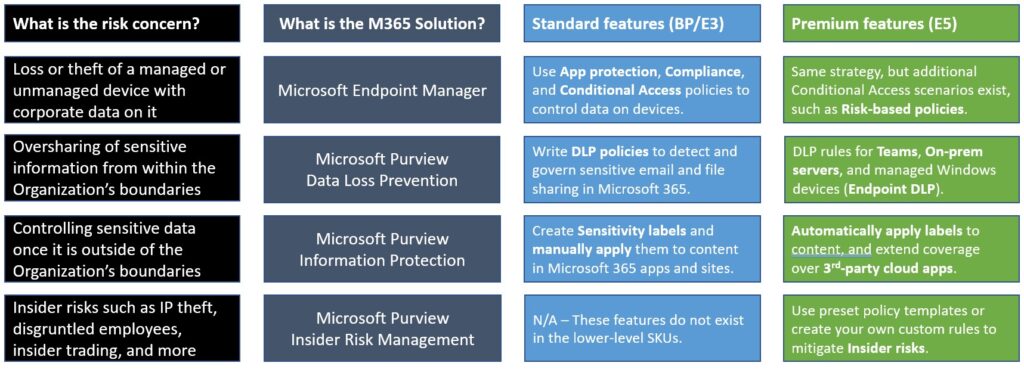
There are many different risks associated with data leakage and/or loss of data. Each risk has a different set of possible mitigations, and most of the time we can find a solution within Microsoft 365. In fact, sometimes there is more than one technology solution in this suite of tools which could help us to address a particular area of concern. Let us examine a few common risk concerns that businesses may have, and apply the Microsoft 365 features that best help us to address these concerns. I will also highlight the features that require a full E5 subscription, versus the more common Business Premium or E3 that we tend to see in the SMB space.
Concern #1: Loss or theft of a device with access to corporate data
This is the first concern I normally ask small businesses to address. If a device were to fall into the wrong hands, wouldn’t you want to be able to wipe the corporate data from it? There are several solutions to this problem.
The first is App protection policies (a.k.a. MAM policies). This would be the minimum recommended mitigation for most small businesses, and more specifically with regard to personally owned iOS and Android devices. Although these policies are also available for Windows devices, it is more difficult for me to recommend this option (for Windows, this turns on a feature known as Windows Information Protection, which ends up being a difficult user experience for most people).
We will soon have a new App protection policy for the Edge browser on Windows; when combined with a Conditional Access policy, this would allow us to grant access on personal Windows devices via the Edge browser (using a corporate profile), while blocking access from client applications such as Outlook or the OneDrive sync client. Therefore, no company data would persist on the device itself. You can already accomplish a similar outcome using something called Conditional Access App Enforced Restrictions, which enforces ‘limited web access’ where downloads are prohibited on unmanaged devices, and this works on any device platform or browser.
Another option that I generally recommend is requiring devices to be enrolled and compliant with corporate policies in order to gain access to corporate data in the cloud. This is accomplished with a combination of Compliance policies, and Conditional Access policies. I always require this at least for Company-owned devices, but this can be made mandatory for personal devices as well if you prefer. This way, not only do you have remote wipe capability over the device, but you can enforce specific rules and settings as well, including rules to reduce other risks such as malware, for example, by deploying Microsoft Defender policies like Antivirus, Attack Surface Reduction, and Endpoint Detection & Response (at which point you are addressing risks well beyond data loss).
Controlling access to corporate data on managed and unmanaged devices can be accomplished with Business Premium or E3 subscriptions, but if you happen to have E5, some additional scenarios open up. For example risk-based Conditional Access policies that apply certain restrictions only when risk is detected.
Concern #2: Oversharing of sensitive information stored in the Organization
Some types of information should not be shared externally, or at least not widely outside the walls of the Organization. For example Social Security Numbers, or other Personally Identifiable Information (PII) are often considered sensitive information which should be shared more carefully. The same can be said for financial information like credit cards, bank account numbers, and so on. Sometimes these information types are even regulated by certain laws whether local or state or federal/nation-wide.
To address concerns with handling sensitive information within the Microsoft 365 service, we can write rules using Microsoft Purview Data Loss Prevention that can help us monitor and govern how these data types are to be shared and sent outside the Organization. In most subscriptions (e.g. Business Premium, E3) this includes common services like email and file sharing, meaning we can have rules which are triggered when sending emails or links out of OneDrive or SharePoint. With an E5 subscription we gain rules for additional services such as Teams chat and channel messages, and even on-premises file severs.
Usually the rules we write include such common scenarios as notifying an administrator when something sensitive has been shared, or filing an incident report. As well, we can take actions to automatically encrypt emails containing sensitive info, or we can block certain types of data from being shared at all. Any of these rules can be accompanied by notifications or “policy tips” which display warnings to the end user when sensitive information is being shared in a way which triggers the rule.
Concern #3: Movement of sensitive data from a device to an unapproved app or location
This is sort of a sub-concern of #2 above. Sometimes organizations will want to prevent the movement of certain sensitive data types on an endpoint, for example, to prevent sensitive information from being copied off to a USB storage device, or printed to a network printer, or uploaded to an unapproved cloud service.
For these types of rules, App protection policies can once again come to the rescue. I normally turn these features on for iOS & Android devices, and, as I mentioned before, Windows Information Protection is available as an option too, but I generally shy away from implementation of WIP for various reasons. Within all of these policies, we have the ability to block copy/paste and save to unmanaged apps and storage locations. Sort of like an “Endpoint DLP Lite.”
And that brings us to the “Premium” E5 subscription: here Microsoft offers Endpoint DLP, which brings some more granular DLP controls down to Windows devices only, and these can even be extended to Google’s Chrome browser using the Microsoft Purview Extension (note: all of this is still included under the umbrella of Microsoft Purview DLP, but again you need an E5 subscription to unlock it).
Concern #4: Control of sensitive information once it leaves the Organization
There are cases when sensitive information needs to be sent or shared beyond the boundaries of the organization. And in these cases, we want to ensure the data can still enjoy some protection once it moves beyond our control, to an unmanaged device for example, or to an outside party.
The flagship solution in this space is Sensitivity Labels (part of Microsoft Purview Information Protection). Labels which define Sensitivity can have a lot of different powers attached to them. Sometimes they may do nothing more than mark a file visually with something like a header, footer, or watermark. In other cases, we may want to apply encryption, so that the recipient of the file or email message will need to sign-in before they can read or work with the information. Encryption can also be accompanied with permissions that restrict certain capabilities (for instance we can prevent exporting or printing the data).
Other powers include being able to restrict certain sites or groups (including Teams) with rules like, “Unmanaged devices cannot download, print or sync the contents of this site.” Further, Sensitivity labels can be used as a condition when writing our rules in Microsoft Purview DLP.
Finally, it is possible to automate the application of Sensitivity labels under various circumstances. For instance, we can scan for and label data at rest using auto-labeling policies. Otherwise, we may want to apply or even just “recommend” that a certain label be applied using the auto-labeling settings within the label itself. Or, only apply labels under specific conditions, such as when a file containing sensitive information is downloaded to an unmanaged device from a managed cloud application (including third-party apps like Box or Google); in this case we would need to layer on an additional solutions, for example Microsoft Defender for Cloud Apps. Most of these auto-labeling capabilities will require the E5 subscription, of course, or another add-on which includes these features such as Microsoft 365 E5 Compliance.
Another “premium” auto-labeling feature (read: E5) includes the ability to use trainable classifiers to recognize information that you want labeled in a certain way. With this solution, you feed examples to Microsoft Purview so that it can “learn” what you consider sensitive data. This gives you some capability to move beyond the common preset information patterns like Passport Numbers, Social Security Numbers, Credit Card numbers, etc. that you get with the standard DLP features.
Concern #5: Insider Risks
Some businesses may have a higher level of concern around insider risks such as:
- Data theft by departing users
- Data leaks by disgruntled users
- Insider trading
- Intellectual property (IP) theft
- And more
Microsoft 365 E5 includes a Microsoft Purview solution called Insider Risk Management with several policy templates that can help you detect and take action on these types of events. This is an example of a more “advanced DLP” solution that also relies on additional components of E5 such as Microsoft Purview eDiscovery (Premium).
Since these are all dependent on more expensive subscriptions, most small businesses will choose to handle these risks in an alternative way. For example: by having a strict written policy, and leveraging the standard Microsoft Purview DLP rules to monitor or alert on the movement of sensitive data.
Conclusion
Here we presented a few examples of common risk concerns around data loss or leakage, and how each of these concerns can be addressed or mitigated using one or more possible technology solutions available within Microsoft 365. When you get into more advanced DLP scenarios, especially involving more automation, or control over third-party cloud apps, or insider risk management scenarios, etc., then we are talking about the more expensive Enterprise E5 subscription. The below table is an updated breakdown of the landscape today:
I think this is a simpler summary, which is perhaps even easier to understand than what I previously published. I can’t say it is completely exhaustive, but it’s a pretty good overview of the most common risk concerns and the associated solutions that we tend to implement.







Comment (1)
TY Adam! This was an awesome read and as always, I begin with your guides for my customer engagements. :)