There is no panacea, there is no silver bullet
I had a really interesting question come up during one of my recent online courses. One of the participants asked whether device management, and even MAM (application-based management) were necessary anymore, now that we have stuff like MIP and Sensitivity Labels. I was taken aback by this question and I think that it is important to address it more thoroughly and for a broader audience.
Actually, I have been seeing this idea crop up in some other places as well, though sometimes under slightly different context. For example, some MSP’s out there are selling some flavor of a hosted VDI solution, whether via WVD, VMware, or whatever, and they often tell their customers (foolishly) that they should just use whatever endpoints they want to connect to the remote environment, and that they do not need to manage those endpoints. Users’ physical devices, they suggest, are basically disposable, and have no meaning since “everything is secured in the cloud.”
In my opinion, any provider who tells you something like this is either just dangerously ignorant, or they are being highly irresponsible with their service and their customer’s data. Or most likely, both. These examples here (the Sensitivity labels and the VDI provider), are basically coming down to the same error: they assume that some particular solution is the solution and that nothing else is needed to ensure the Confidentiality, Integrity, and Availability (CIA) of the business services and information.
But if that were really true then we could all just stop implementing any cybersecurity or compliance frameworks because hey, we already bought/implemented this one product so, you know, we’re good! Let’s just shut down NIST, CIS, CISA, CCCS, NCSC, ACSC and any other organizations out there dedicated to keeping our infrastructure and data safe.
Layered approach to security
But of course, we don’t live in a fantasy land. We live in the real world, so it turns out that no one product or solution can really cover every single concern or scenario. When you look at a big bundle such as Microsoft 365, which includes many different security products, even if you really took the time to implement every single feature, would you be 100% safe? No. You can never be 100% safe. Only safer. This is as true in cybersecurity, as real life.
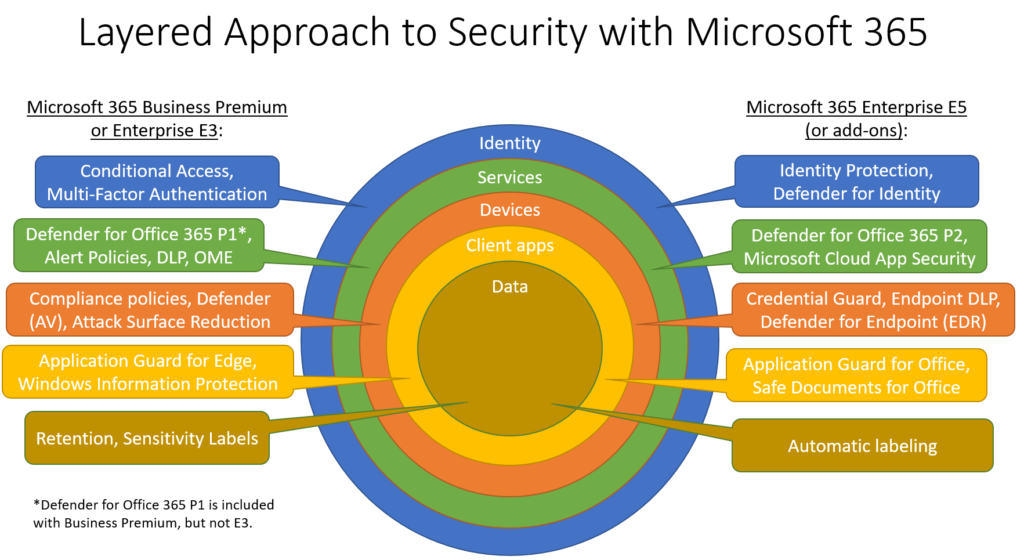
One way we can easily demonstrate this is by considering the diagram above. We have many layers to consider in our cloud-based information services architecture. We have the identity layer (and MFA is still our best defense for identity-based attacks), then the service layer (such as Office 365 Exchange Online), and then we have devices which connect to that service, and client applications as well as data (data may live in the service but it can also be synced or downloaded via a browser or client app). If an attacker can successfully infiltrate any one of those layers they have a shot at achieving their ultimate goals.
Microsoft 365 bundles are mindful about providing us with some safeguards/protections for each one of the major layers. And implementing more of them will certainly help you to meet certain compliance requirements or security controls, reduce risk, and so on. But to be clear, there is no such thing as a silver bullet. Even in the Mighty Microsoft 365.
How hackers are wired
Many times you are protecting against different risks at different layers. But for example, a sensitivity label will not protect you if your identity is compromised, or if your device is compromised. When you work with the data, it is unencrypted and exposed. If there is an attacker dwelling on your device, they can see what you see. Or, consider stuff like Windows Information Protection, Attack Surface Reduction, or even full AppLocker (whitelisting). Did you know that these safeguards can be bypassed if an attacker has local administrator rights on the machine?
It goes on and on. Even the often-boasted effectiveness of MFA will be eroded over time as attackers find new ways around it. Already, I have seen instances in the wild this past year where an end user was tricked into granting access even with MFA enabled for their account.
You have to understand how hackers are wired; they aren’t like most people. And I use the word hacker here and not attacker because the good guys do this stuff too and thereby help to make our systems even better. Anyway, when a hacker runs into some barrier, they don’t just throw up their hands and say, “Oh well, I guess they got me.” No. They pivot, and find a new way. “There is always another way,” could be a good mantra for these types.
But again, you can likewise always find ways to reduce your risk, and, the saying goes, you make yourself a more expensive target in the process. Even the bad guys are “on the clock” so to speak, and they have to be practical about how they spend their time earning that dishonest paycheck. If the payout does not seem likely to match the effort, they will eventually move on to the next target.
Plus, wouldn’t you at least want to try and implement something rather than nothing? Sure, an attacker might trick someone into helping them past this barrier or that, but it is still a barrier nonetheless, and oftentimes the barriers will hold, or one will hold even while another crumbles. In fact, I argue that a well-designed system following a solid framework is better because you end up pairing many of these protections together. For example, at the human layer you will want a security training program to reduce the chances of someone being tricked in the first place. So you can thereby reinforce protections you have implemented at other layers.
Back to Sensitivity Labels
I think I made my larger point here, so now let’s talk about this question of Sensitivity Labels. Yes, as I have mentioned before, they can be a powerful tool in your arsenal, but they do not, and cannot, replace your device management strategy. In fact, in some ways they complement a modern device management framework. For example, one of of the functions of a Sensitivity label when applied to a Site, Group or Team is that you can block downloads on unmanaged computers.
Or, consider Microsoft Cloud App Security: using this tool, we can choose to apply labels only if they are being downloaded to an unmanaged computer. But why not just encrypt ALL the data? Couldn’t we just let the data fly around to any old device once it is encrypted?!
Again, encrypting files does not meet every cybersecurity control or protect you from every threat. There are reasons you may want to prevent certain files from being distributed and proliferated on outside devices, whether encrypted or not. By the same token, there are reasons you might not want to apply labels that encrypt data in every circumstance. When a file is encrypted it is harder to work with: it destroys some of the collaboration features in the process. The situation has improved recently with OneDrive and SharePoint, but it is not perfect and there are still several well-documented limitations.
But remember: even if all these limitations are eventually overcome, there is just no possible way that this one solution will ever be good enough to provide for your entire list of cybersecurity concerns or compliance requirements. Being able to distinguish between corporate managed and non-managed devices and apply different policies or protections based on this information is a huge benefit and a major piece of the modern management framework, in my opinion. I do not think it is going anywhere anytime soon.




Comment (1)
Your comments align perfectly with the new Security and Compliance exam path. Each tool and service is there to assist in your overall security posture.