A Sneak Peek at Application Management for Edge
This blog has been active for at least six years. To this day, I probably receive more questions about BYOD and the various options we have for management with regard to personal devices, than any other topic that I have written about. I think this just goes to show the types of challenges and questions that consultants and service providers face in the wild. It is also telling because I would have expected by now to see these types of questions taper off as the market “figured it out,” so to speak.
But we haven’t quite figured it out yet. Especially for Windows devices (ironically). Part of the problem, I think, is that we can approach the BYOD concerns in several different ways, so folks need help navigating their choices. While we have many tools available which can help us to enable BYOD experiences, unfortunately, every solution has its trade-offs. Some good, some not so good.
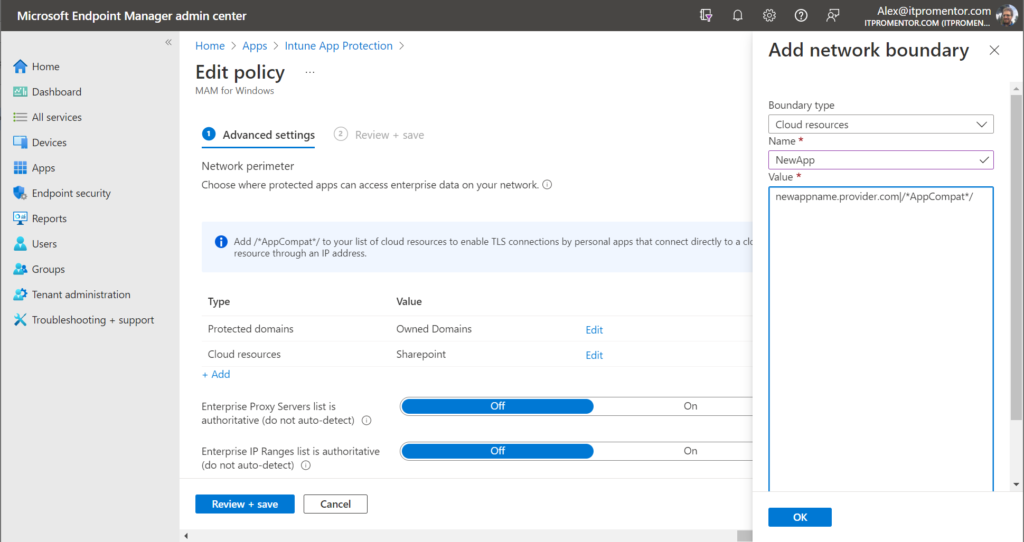
For example, take Windows Information Protection (a.k.a. MAM for Windows). This solution can be difficult to configure, and has a fairly large impact on user experience. Certainly it is not something you would casually roll out without some pretty decent planning and testing in advance, not to mention communication and expectation-setting with your user base. Plus, you’ll often find yourself needing to do maintenancy-things like update your approved network locations and cloud resources list, so that certain websites can be considered “inside the corporate fence” and play well with all of your corporate-protected applications.
And even after all that effort, you’ll still notice some serious limitations and drawbacks to the solution. To make matters worse, it is my understanding that Microsoft is stepping away from further development on WIP; when I have asked them about possible improvements to the product, they have pointed me toward Endpoint DLP as an alternative (thanks but no thanks…it’s an E5 solution anyway).
Therefore, I generally recommend against WIP, and suggest that customers either block personal Windows device access outright, or use an alternative approach like requiring device enrollment and full management (which does open another can of worms) or settling for the “Limited web access” experience via Conditional Access / App enforced restrictions.
In short, no matter which path you walk down with regard to Windows devices, every option seems riddled with gotchas and caveats that put a sour taste in your mouth. (And may I just add that it is absolutely maddening that Windows–Microsoft’s own product–still has a less mature and less functional app management solution than iOS and Android? I mean MAM for mobile devices is awesome–so why does it still suck on Microsoft’s own OS?!)
Anyway, soon we will have another option, and this one looks more promising (fingers crossed). It’s called Application Management for Edge. I believe it was first announced publicly here. There was also a digital event where they teased a bit of this functionality in a short demo (see the 11:20 mark in the IT Management and Hybrid Work breakout). Some notes from my observations:
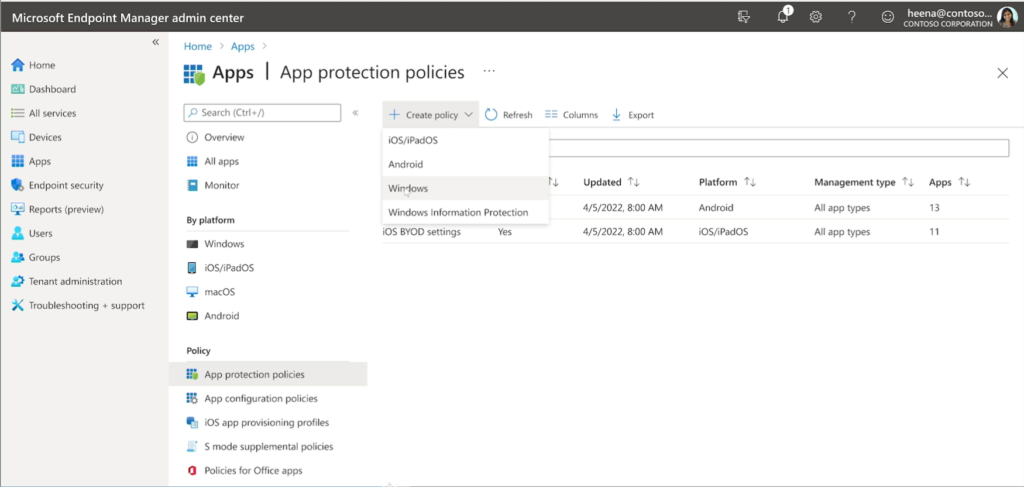
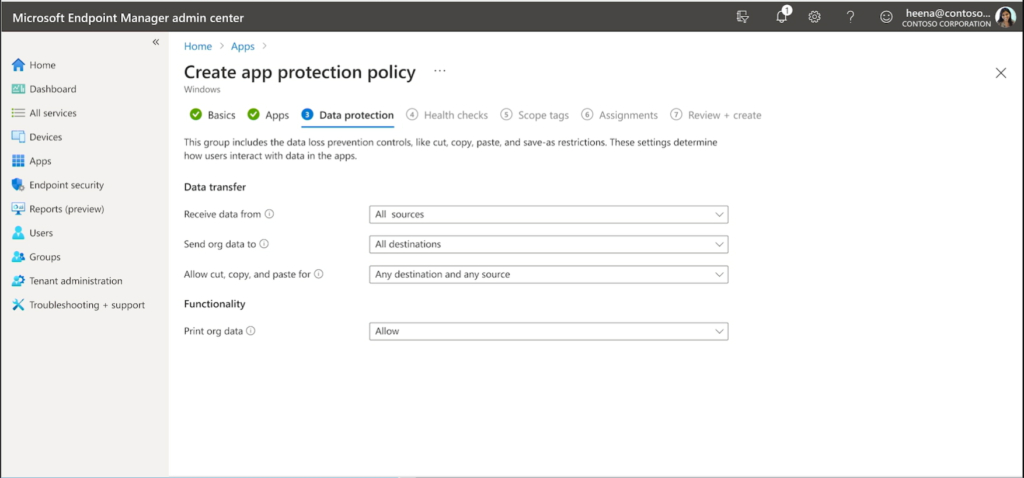
First, we see in the demo that there will be a new App protection policy type in Endpoint Manager (Apps > App protection policies). It appears the current policy we have will be renamed to Windows Information Protection, and we will be given a new option called Windows.
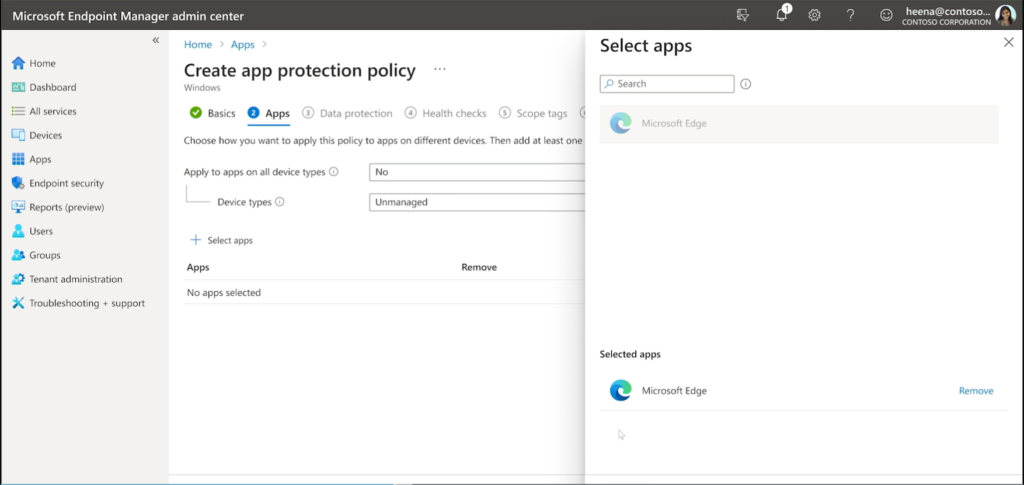
Based on these screenshots from the demo, only the Edge app is going to be available at first, but I am hoping that in the future we will see other Microsoft 365 apps (for the desktop) added here as well, including Word, Excel, PowerPoint, Teams, etc. (I have no idea if this is true but it would be awesome if so).
In any event, being able to target the Edge browser has some important benefits. First, we can enable a better web access experience that is tied to a corporate Edge profile, rather than a pre-defined network boundary, where we have to add all of our “protected” websites and apps to a list in advance. Then, it appears we will have the ability to set Data protection boundaries between the corporate profile and personal profiles, just like we experience with App protection policies on mobile devices (and it is about time)!
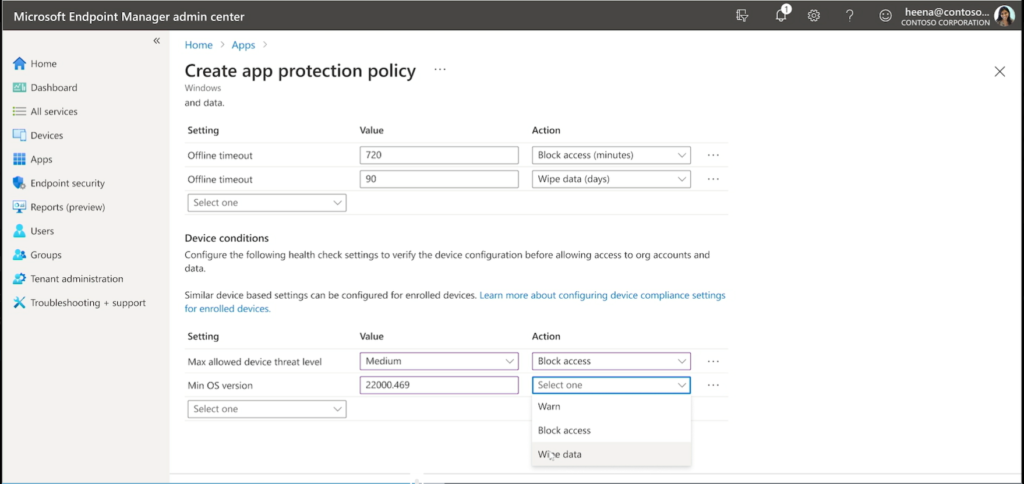
We even have Health checks, and I spy that Minimum OS version as well as Defender’s Max allowed device threat level integration will be included off the bat as well, where the threat level on the device can become a bar for access to corporate data.
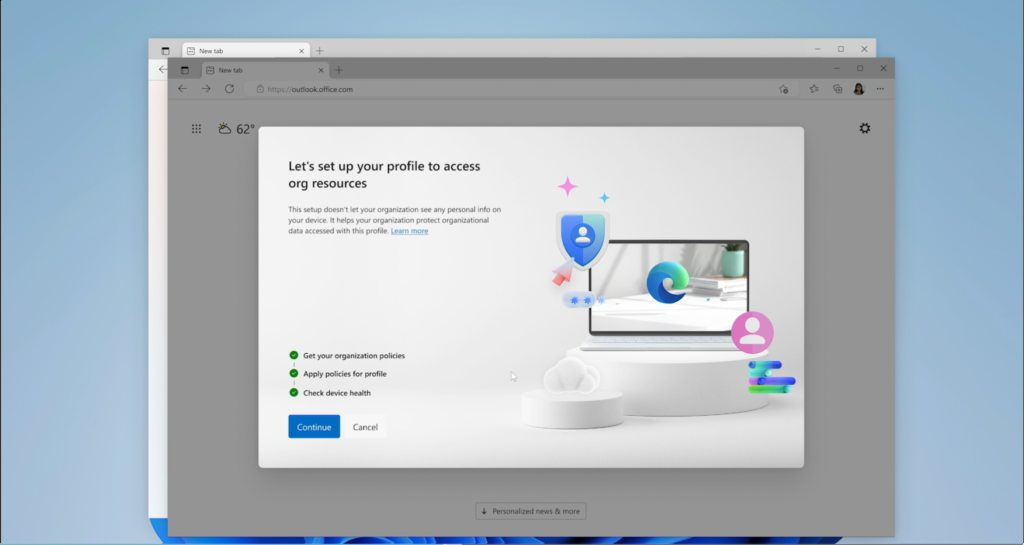
Once the policy is implemented, the end user experience looks pretty slick so far (and it doesn’t say this anywhere but I wonder if there is a Conditional Access policy requirement at play here as well, take a look and let me know what you think):
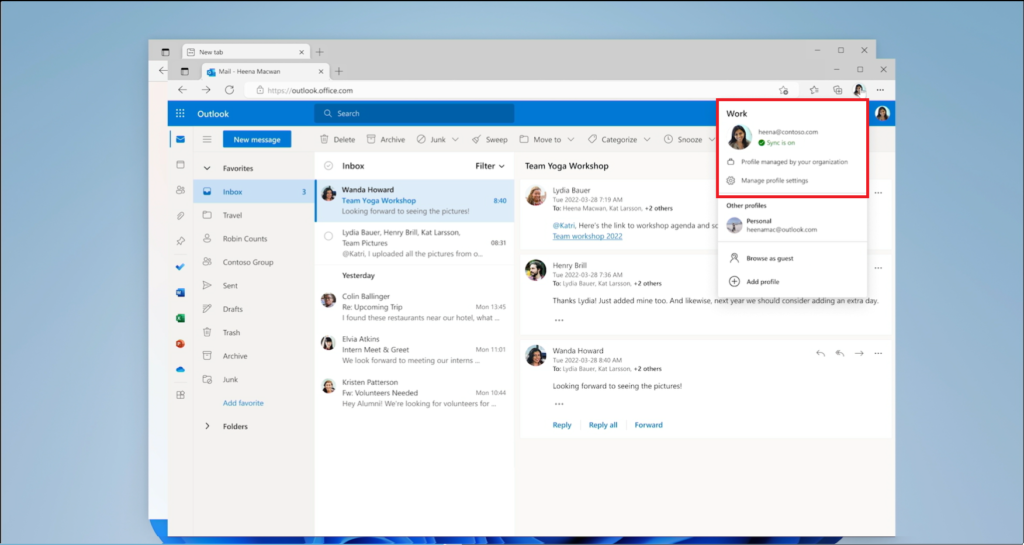
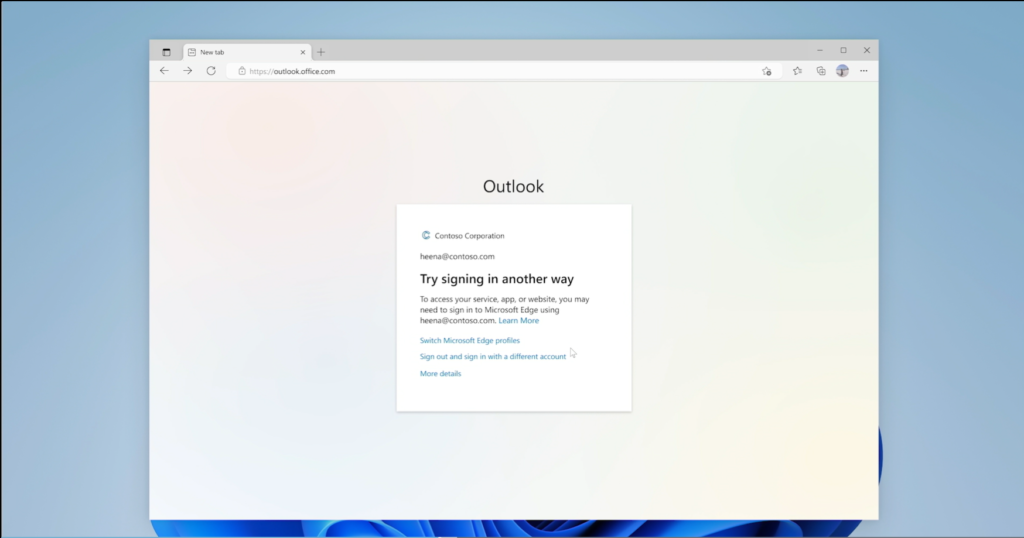
When a user attempts to access a corporate resource such as email from a personal profile in Edge, they are blocked, and given an option to Switch Microsoft Edge profiles.
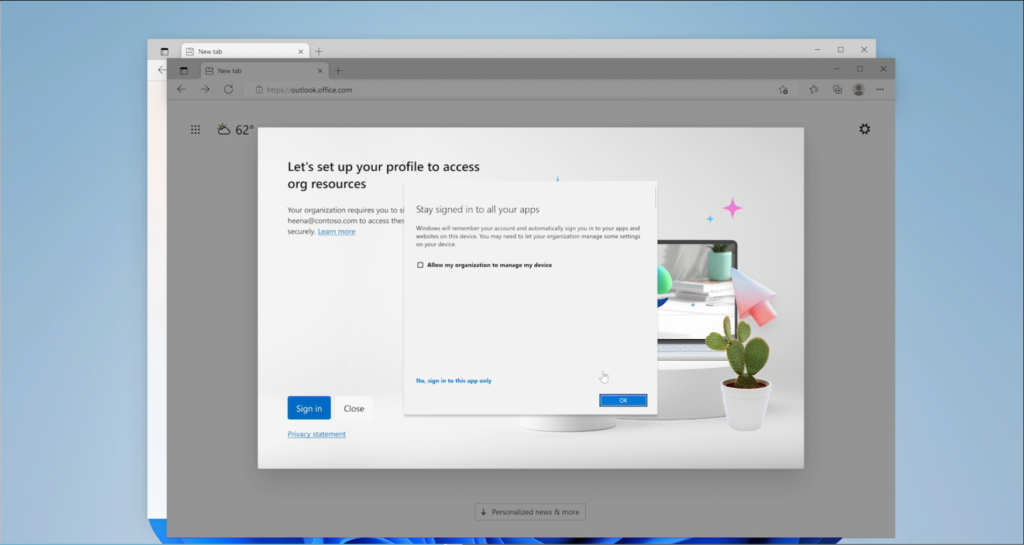
They sort of gloss over this prompt in the demo video, but when you sign in with a corporate profile, there appears to be an option to enroll your device in order to “Stay signed in to all your apps.” There is a checkbox here, “Allow my organization to manage my device.” Then at the bottom is an option “No, sign into this app only.” If you click OK without checking the box, I assume that would have the same effect as clicking the No… option.
Hopefully we will get an opportunity to remove this prompt entirely, in cases where we do not want users enrolling personal devices (I would suggest that blocking personal enrollment via device restrictions should automatically remove this screen from the end user’s view, but I suspect that it would still remain, so the end user who is restricted from enrolling could get an error if they attempt to check the box–we’ll see if Microsoft is smart enough to improve this flow before it is released to Public preview).
We can see that the health checks have passed, the policies have applied, and the profile is now available on the device.
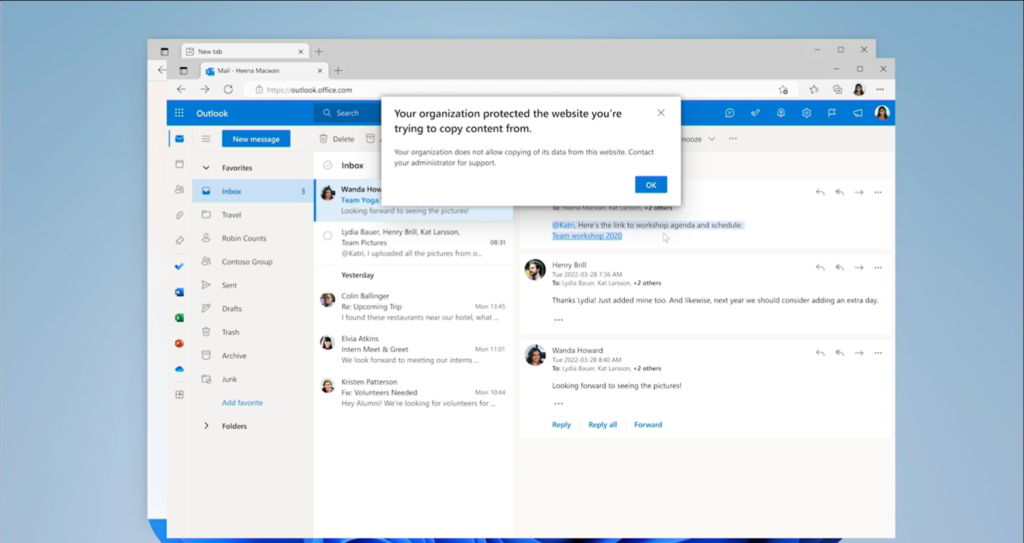
Finally, we can see the policy in action, blocking a copy/paste action:
All in all, a massive, MASSIVE improvement over the legacy WIP experience: easier to set up for the administrator, and easier for the end user, as well. Although, until they add client app support for the desktop apps, this solution appears to be limited to web-only access at first, which is somewhat similar to the experience we have always had with Limited web access (using Conditional Access App-enforced restrictions). Still, I am optimistic that we will find this “profile-based” app management solution allows for more granularity and flexibility as development continues. I am excited to see this released to pubic preview (I haven’t seen a date on that yet), and of course, everything the future holds beyond it.
(I just hope this new policy will be included with Business Premium, and not held behind the E5 paywall!)






Comments (4)
I am hoping that they add it to the intune license or don’t make it an expensive add on license for intune. With most smb having laptops you may not need this for every user in a tenant
That popup about enrollment is really irritating. Click OK or No? You can avoid it by adding a registry key. But that only works on devices you manage. We had to do this in VDI, otherwise users were registering dozens of instant clone machines when logging into Teams.
Ha! That is a good tip, glad to know it can be turned off with reg hack. How annoying though… I want a button in AAD or MEM to disable that, for sure.
Just to update – the Edge MAM topic starts around 17.38 mins into the video