Why aren’t you protecting your mobile devices with Microsoft Defender?
Recently I was on a call with Microsoft, and I was surprised to hear that adoption for Microsoft Defender on mobile devices is still extremely low. But according to other industry partners, this is true of Mobile Threat Defense (MTD) solutions in general. I think this unfortunate trend could be due to a variety of reasons.
The reasons we ignore mobile
One obvious factor here is that mobile devices generally are not regarded the same as desktop devices by administrators, who probably still have less experience with mobile threats than with those that affect the desktop. And this is unfortunate, because mobile devices are also endpoints with access to corporate data, and they shouldn’t necessarily be considered less vulnerable to exploitation versus traditional desktop computers.
After all, when you look at a cybersecurity framework like the CIS Controls, is there an asterisk next to each control that says, “Except when dealing with mobile devices?” No. Of course not. If you have a requirement to manage vulnerabilities and apply malware protection to one set of endpoints, why would another set be exempt?
Yet another reason for low adoption in this space could be that admins assume they are “already covered” by existing protections, whether those are provided by manufacturers such as Apple and Samsung, etc., or because they have already enrolled mobile devices for MDM or MAM. To be clear, this thinking is simply not correct. Having an inventory, pushing down certain settings, and being able to respond to physical loss or theft events is one thing, but this is not a complete strategy for mobile threat defense, which goes beyond traditional MDM/MAM solutions.
And that brings us to the last factor, and perhaps the easiest one to address: knowledge gaps. I think some folks may not even realize what is available to them, and even if they “sort of know” about these features, they have never taken the time to learn how to configure their product accordingly.
Now the good news is that if you have Microsoft 365 Business Premium (or Microsoft Defender for Business standalone), then you already have access to this software, so there is no good reason not to be using it. Most vendors will charge extra for their MTD solutions—it is normally considered an “add-on.” By contrast, Microsoft views this as essential coverage for every small business customer, and therefore it is included in their flagship offering. This approach makes much more sense to me, and it is just more evidence supporting my claim that dollar for dollar, there is not a better value out there than Microsoft 365 Business Premium.
Preparing for Mobile Threat Defense with Intune and Defender
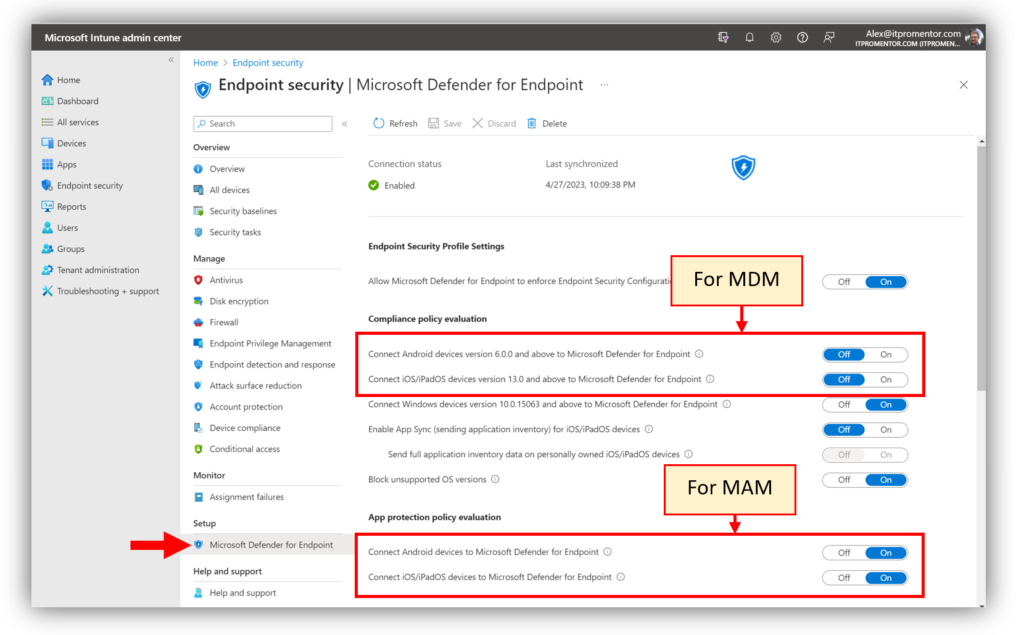
The first thing you will want to do is check to make sure that the requisite “connectors” between Microsoft Intune and Microsoft Defender are activated. From the Intune portal, visit Endpoint security > Microsoft Defender for Endpoint (under Setup).
For each device platform you intend to support, you will want to switch the setting to On. Under Compliance policy evaluation, these refer to devices that are enrolled for full management (MDM) with Intune. Under App protection policy evaluation, this refers to device platforms that can be managed using MAM.
These days, many SMBs are choosing MAM for BYOD mobile devices over MDM. What I have pictured above accommodates my own setup. Just be sure to make the selections that match up appropriately with your own configuration.
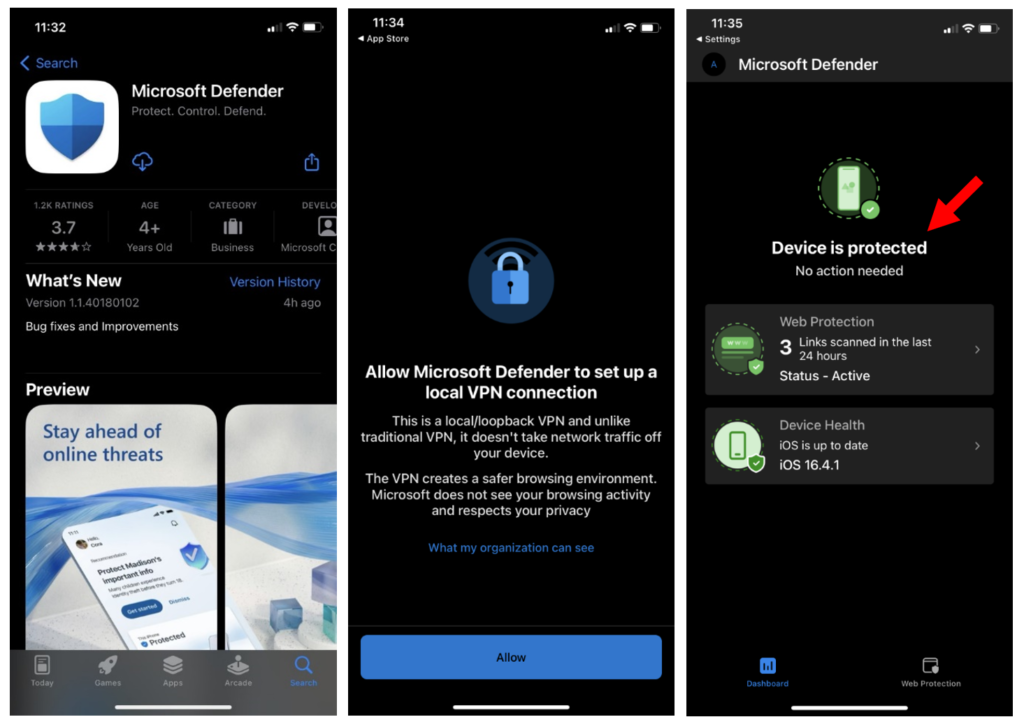
After you have verified these settings are in place, you can begin onboarding mobile devices. For BYOD/MAM devices, simply instruct end users to download the Microsoft Defender app from their app store and sign in to begin protection.
They will see several prompts such as accepting terms of use, allowing notifications, and allowing a VPN connection to be installed (this is used for link scanning). The simplest instruction for end users here is just “Always answer prompts in the affirmative until you see the screen that says Device is protected.”
If you have company-owned mobile devices that are MDM-managed by Intune, then you can push the app to their device for them.
Once the app is installed, you can start to get Threat & Vulnerability Management data, which is visible in the Microsoft Defender (Security center) portal. You will also get link protection, meaning that links followed from mobile devices will be scanned using the same technology which supports Safe Links in Office 365. Last, any active threats detected on the device will raise the machine risk score for that device in the cloud. This is data that can be leveraged with Conditional access.
Enforcing the protection
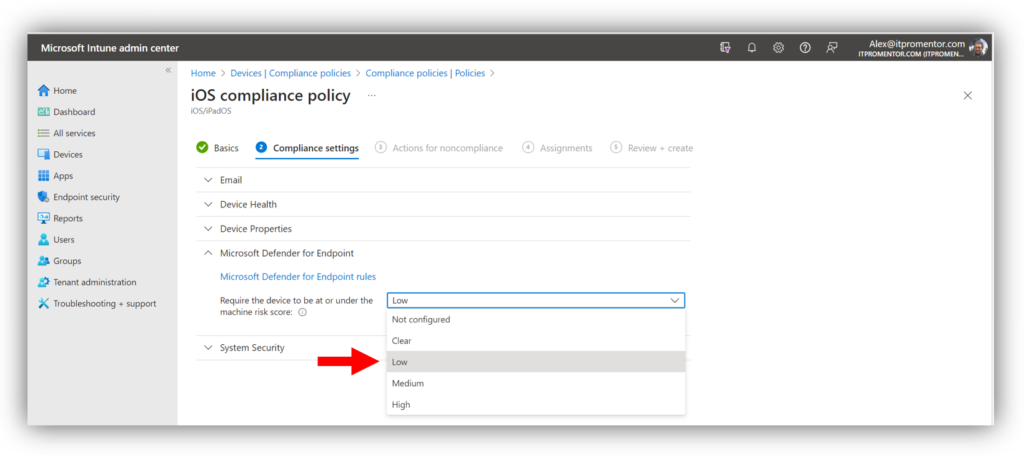
For mobile devices protected by MDM, you must create a Compliance policy that sets the acceptable risk threshold under Microsoft Defender for Endpoint.
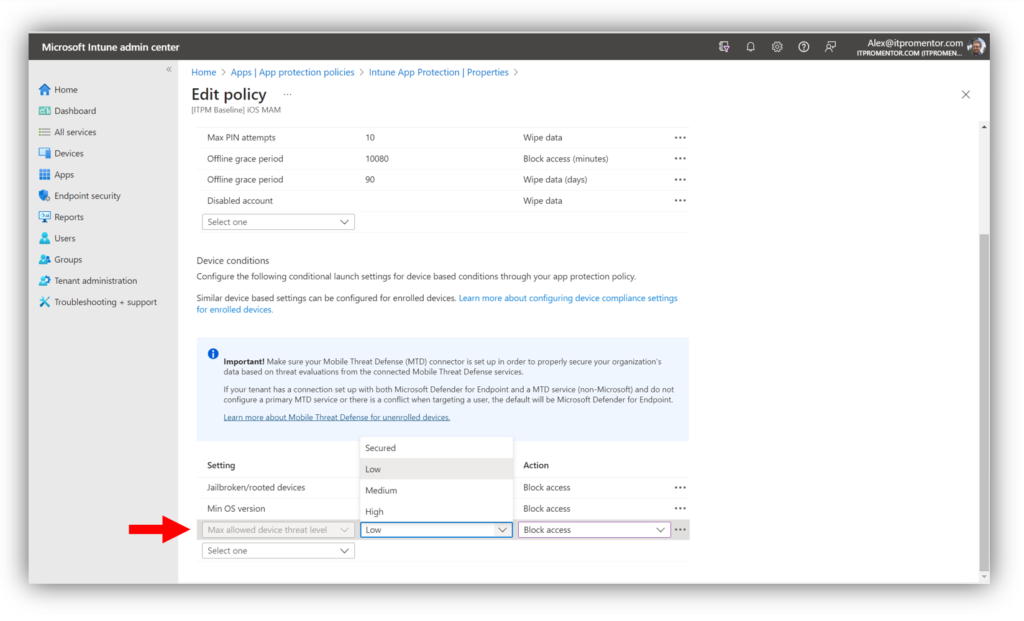
For mobile devices protected by MAM, you would edit your App protection policies, and modify the Conditional launch > Device conditions settings. Add the option Max allowed device threat level and choose your desired threshold.
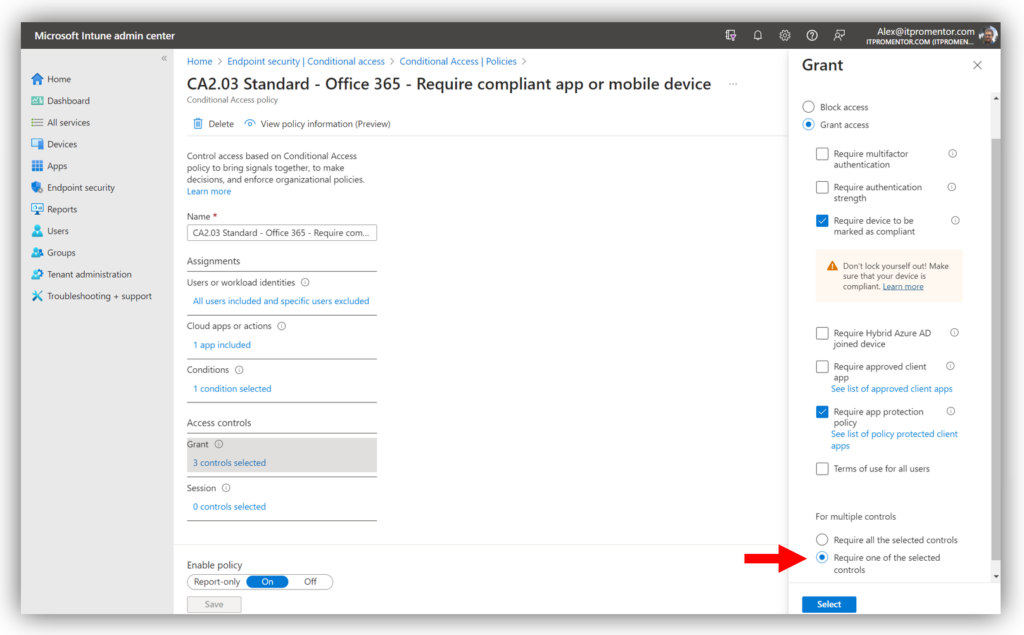
With the necessary pieces in place, you can now complete the picture with Conditional Access. This policy would allow you to offer both options in a mixed environment (MDM and MAM):
- Users & groups: All users or select mobile device users, exclude Guests & Externals
- Cloud apps: Office 365
- Conditions: Device platforms: iOS & Android
- Access controls: Require device to be marked as compliant OR Require app protection policy
- Require one of the selected controls
If you only plan to support one option: either MAM or MDM, you can just select the desired access control instead of using both access controls as I pictured above.
And now you’re all set: mobile devices with access to corporate apps & data will have to respect either the compliance requirements, or the conditional launch requirements according to their app protection policies, and these now include your mobile device threat level in Microsoft Defender. A risky device will immediately lose access to corporate resources until the threat is resolved.
Looking to the future
Microsoft Defender for mobile is still evolving, but we have yet to see significant adoption of this product (or ones like it) on mobile device platforms. That having been said, the future of Mobile Threat Defense is bright, especially with Microsoft offering these capabilities at no extra charge right within their flagship SMB SKU. As awareness grows, and as we see more threats begin to impact mobile users, undoubtedly Microsoft will be in a good place with a solution all-ready-to-go for their customers. I suggest getting on board sooner rather than later.
For those who may be interested, soon I will be offering a live course on Microsoft Defender for Business, which is an update to existing course content. Members of SquareOne already have their invites secured (will be later this summer). Stay tuned for additional information in this space.




Comments (2)
Hi Alex: Another great article, thank you. I’ve been messing around with Defender on my Android for months now. This is one huge problem I’m seeing on my android device that is stopping me from rolling it out to others is the constant accessibility permission prompts. I don’t know how many times I’ve had to reenable the permissions. It pisses me off and I won’t push it out to my users until I’ve figured out why this is happening.
^^ Create an automatic permission deployment profile for the application to grant the permissions.
End user will experience an almost seamless experience. Thx