How to require MFA for Azure AD Join, and enable Enterprise State Roaming
Hey folks! We have already covered a few posts on Azure AD Premium and Conditional access; and that’s great–because you do things like enforce requirements like Multi-factor Auth, but only in situations where devices are unmanaged. This provides a way better user experience than enabling MFA across the board, and without sacrificing much in terms of security. But now let’s assume someone is able to join a device to your Azure Active Directory–then they may gain access more easily to other corporate data, especially if you have “conditions” like those mentioned already setup (e.g. joined devices are not challenged for MFA).
To mitigate the very real risk that I describe, it is possible to require MFA in order to join Azure AD in the first place. I would recommend this setting for every subscription (not just those with Azure AD Premium).
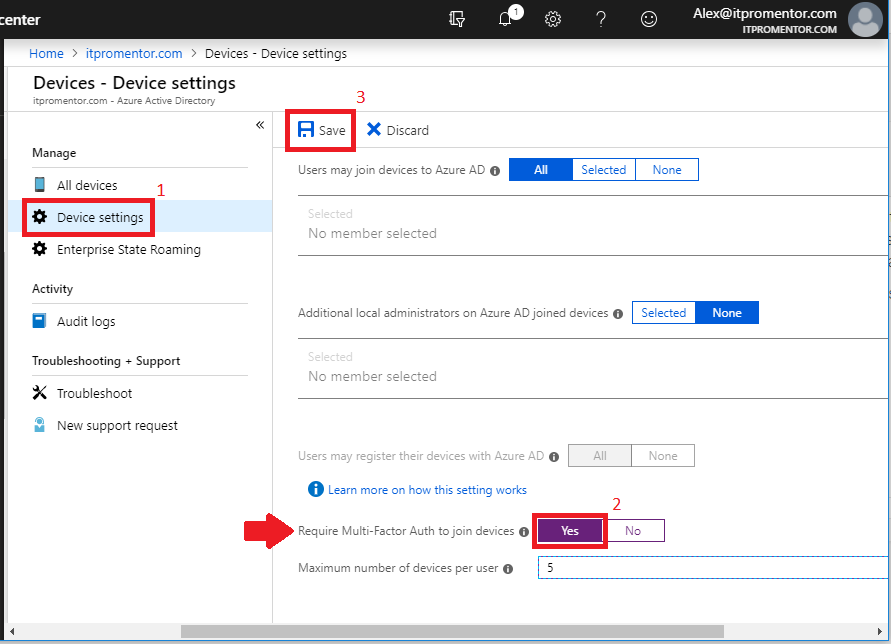
Navigate to the Azure AD Admin center and go to Devices > Device settings. Choose Yes for Require Multi-Factor Auth to join devices. Then Save.
At this point, if someone attempts to join Azure AD, they will be challenged for MFA in the process. This raises your confidence level in the inventory of devices that you see under All devices. You will also notice that there are several other options in here, and I think they are worth discussing.
Consider managing local admin access on devices
First and foremost, we have the ability to restrict who is allowed to join devices to Azure AD. If that first option for Users may join devices to Azure AD is left set to All, which is the default setting, then any user in your directory can join a device to Azure AD. That might be fine for you, but be aware: if a user joins Azure AD as part of an OOBE setup on their own device, then they are considered the owner of the device, and they will become a local administrator on that machine. So you may want to consider preventing this.
Furthermore, where it says Additional local administrators on Azure AD joined devices, we find that it is also possible to define membership in the local Administrators group on any Azure AD-joined device. By default, all Global admins will have this membership, as well as the owner (the person who joined it), as mentioned above.
Managing device inventory
I want to draw your attention to the Maximum number of devices per user setting. I recommend dialing this way down–currently you can drop it down as low as 5, which is what I’ve pictured above. If I could, I would set this down to 1-3. Some people are confused by this stance, but let me explain why it is important. The first and most critical security control listed by CIS is device inventory. If you allow 50, 100 or unlimited devices per user, then you’re being lazy, and putting your organization at risk. You do not want that many devices in your inventory–how do you know which are legit and which are not? You can’t properly protect or mitigate risk if you don’t even know what you have.
For the same reason, I also recommend regularly auditing and pruning the devices in Azure AD–this would be a much more difficult maintenance task without this limit in place, and it keeps everyone honest. If a user or admin runs into this limit, then you ought to perform another audit, and prune some of those stale devices. You may also look into scripting this process for easier execution on a quarterly or semi-annual basis, for example–especially if you have to do it for a very large enterprise, or a lot of small ones.
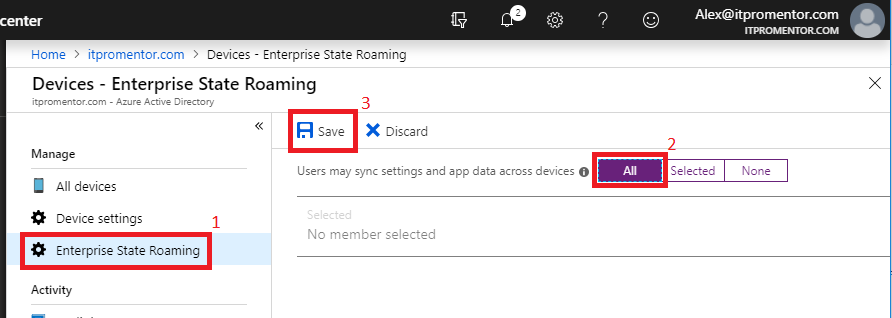
Enterprise State Roaming
Last, flip over to Enterprise State Roaming settings–this is a great feature which makes changing out end-user devices a breeze, especially when combined with features like Autopilot and managed client app deployments, as part of the Microsoft 365 plans. Simply set this option to All, or scope it down to a specific group of users. Save.
And that’s all I have for today, folks!


Leave a Reply