How to configure Advanced Threat Protection (ATP) part 3: safe links
This will be our last post in this series on Advanced Threat Protection (ATP). We have previously covered anti-phishing policies and safe attachments. Now we will consider safe links.
Safe links are basically just taking hyperlinks which exist in Exchange email messages or other content in Office 365, and “rewriting” the URL to include a Microsoft “wrapper.” The Microsoft URL acts like a proxy, launching the links and the links that are found within those links, and the links within those links and so on, before sending your own web browser on to the “real” destination. This allows Microsoft to test out in advance if a website has “gone dark” or contains potentially bad content before you get there.
Note: it is important to realize how this timing works–the scans are taking place literally at the time you click the link, not when the link was created or sent–but when you click on it. So even older emails, etc. would be protected for ‘today’–after all, a website that is good and clean one day, might get dirty the next day.
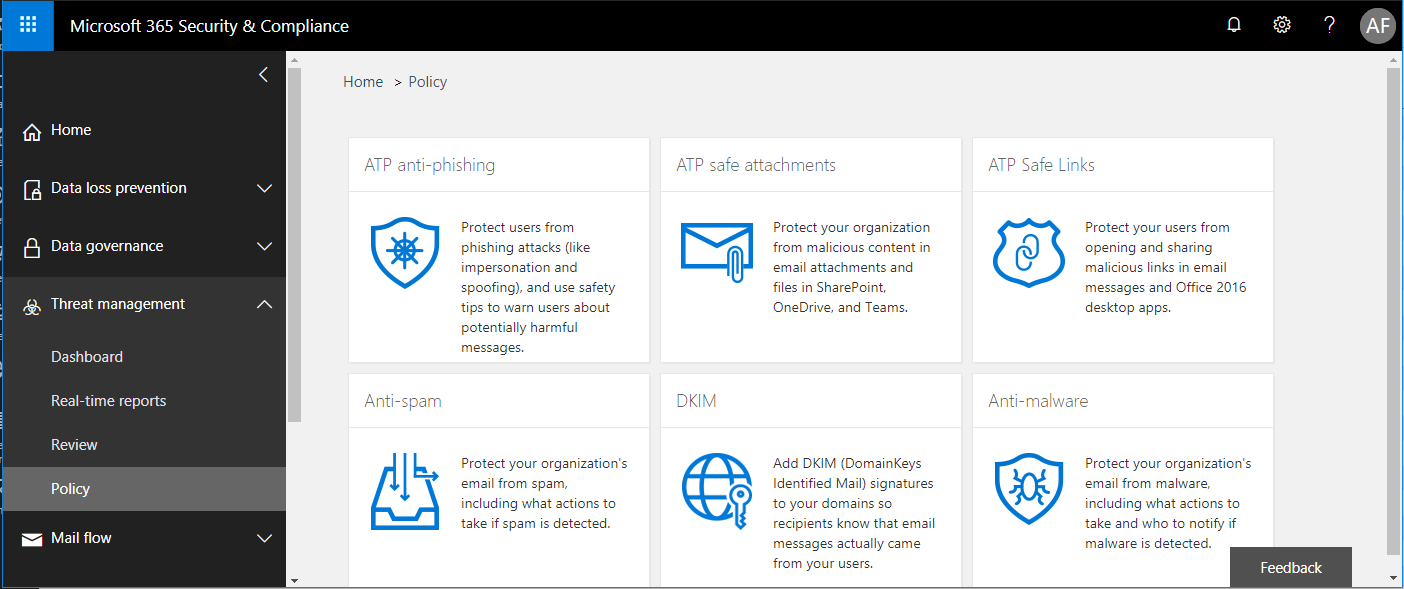
Let’s set it up, again by starting at the Security & Compliance Center > Threat Management > ATP Safe Links. Estimated time to complete: 10 minutes.
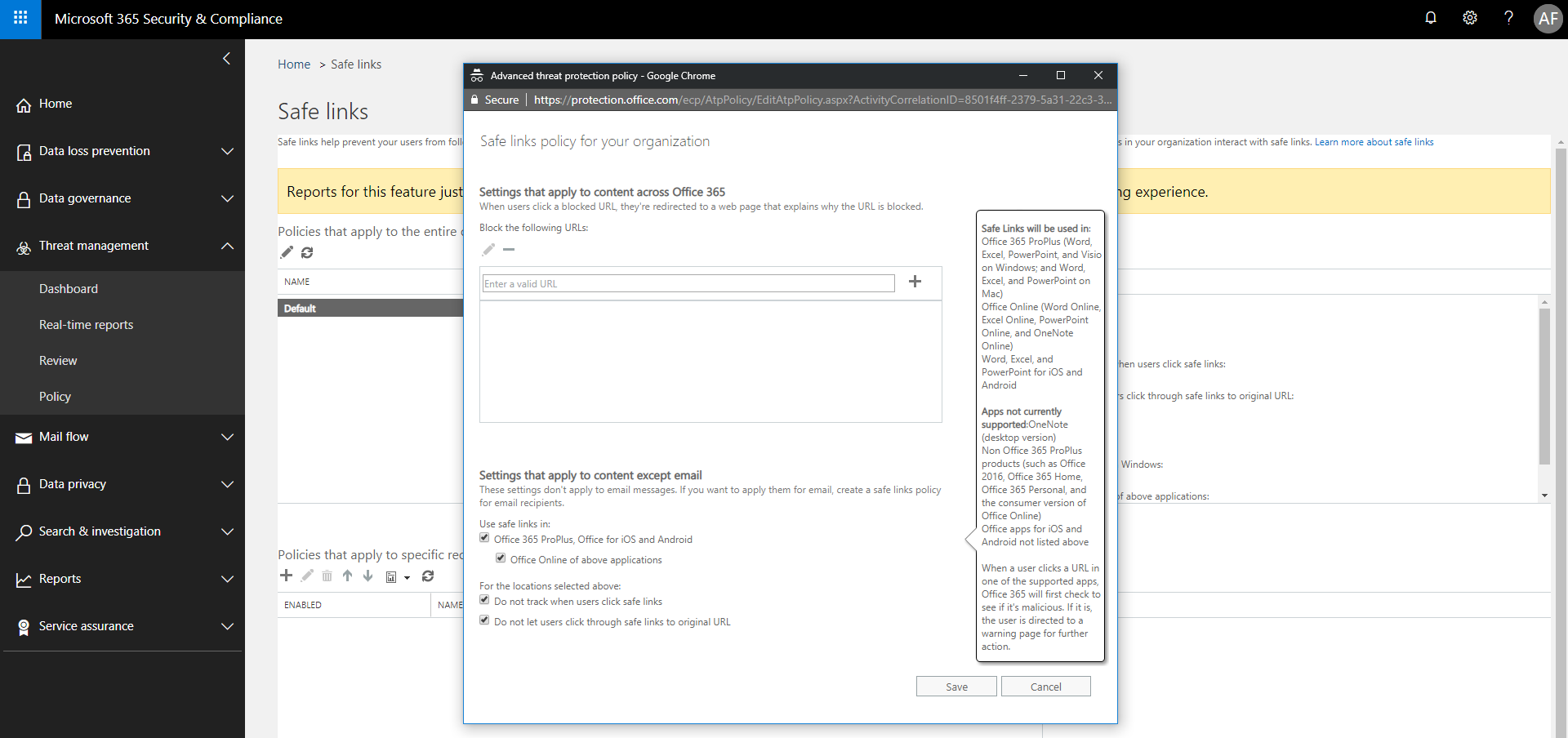
First edit the “organization wide” Default policy, from the first box up top. You can choose your own level of involvement here, and outright block specific URL’s if you like. Otherwise, you can choose to enable it for Office 365 Pro Plus, Office for iOS and Android, and optionally Office Online apps. Last, you do not have to track the clicks if you don’t want to (I don’t, typically), or allow users to click through to the destination from a warning page when a problem is detected. But it is also possible to allow it (I usually don’t). Save the policy.
Then it is also possible to scroll down and add (+) a new policy that applies to specific recipients/domains.
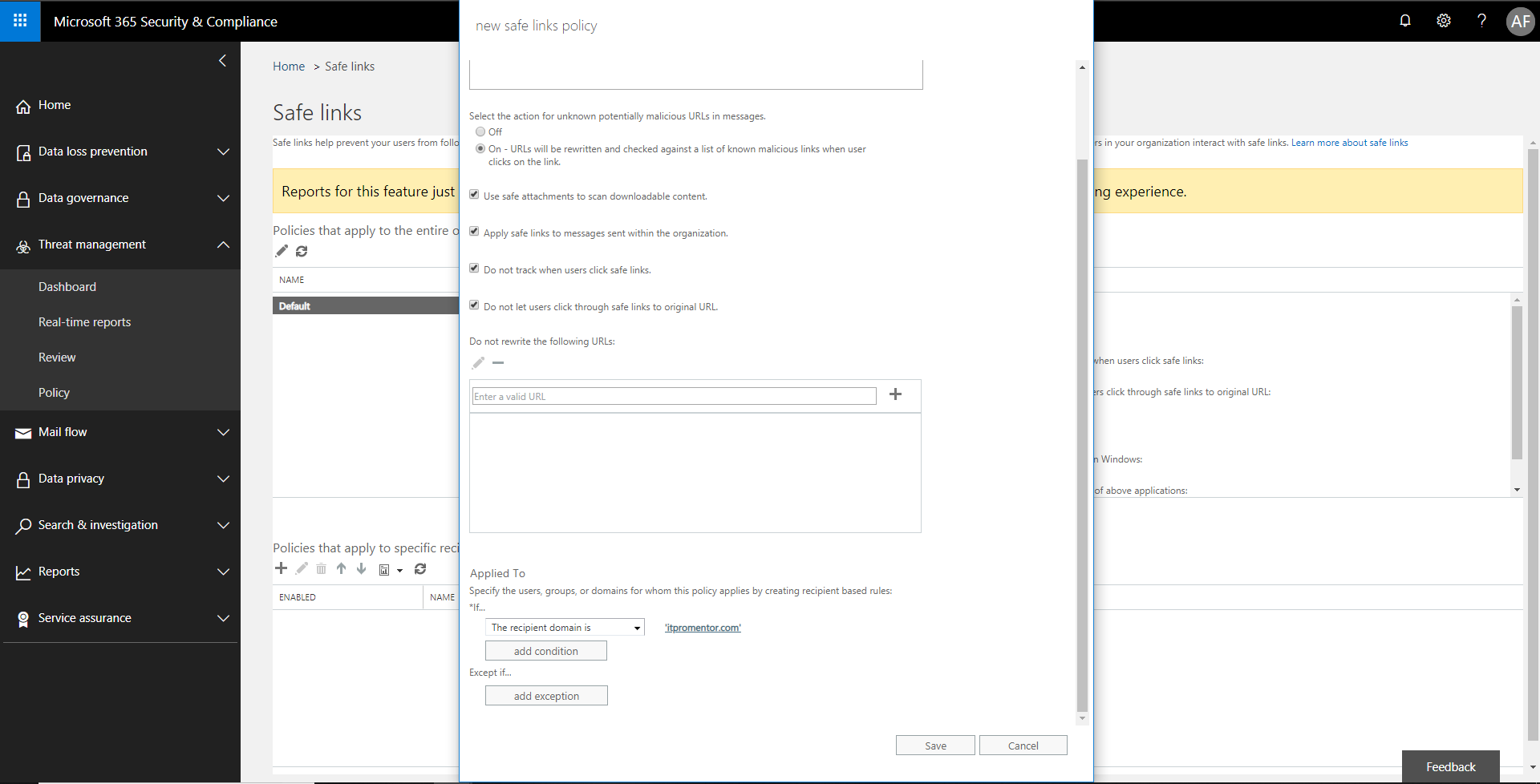
Normally you would select On to re-write URL’s for incoming messages. I also enable the safe attachment scanning, even though we did set a policy up for attachments on messages, this would apply the safe attachments sandbox detonation to “downloadable content” which are coming from the safe links.
I usually apply this policy to the entire domain, but you can also use group membership, etc. Save after making your selections.
End user experience
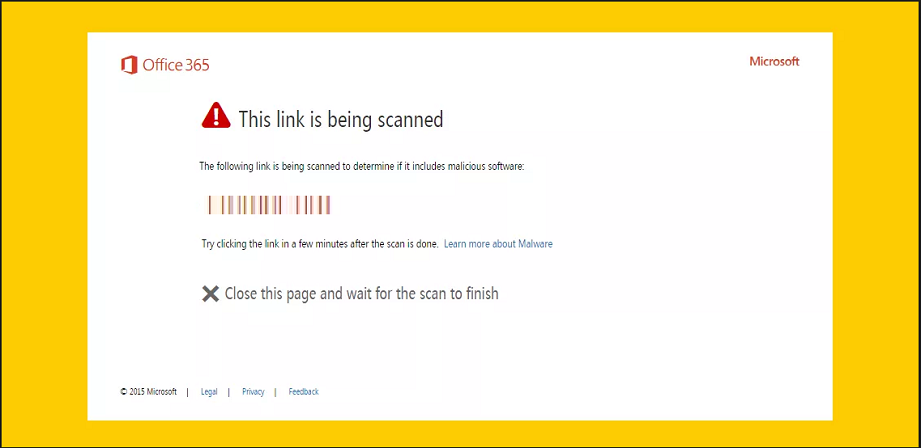
In some cases, the scanning may take longer than usual, and the end user could be presented with this warning page, with an option to click through to the website.
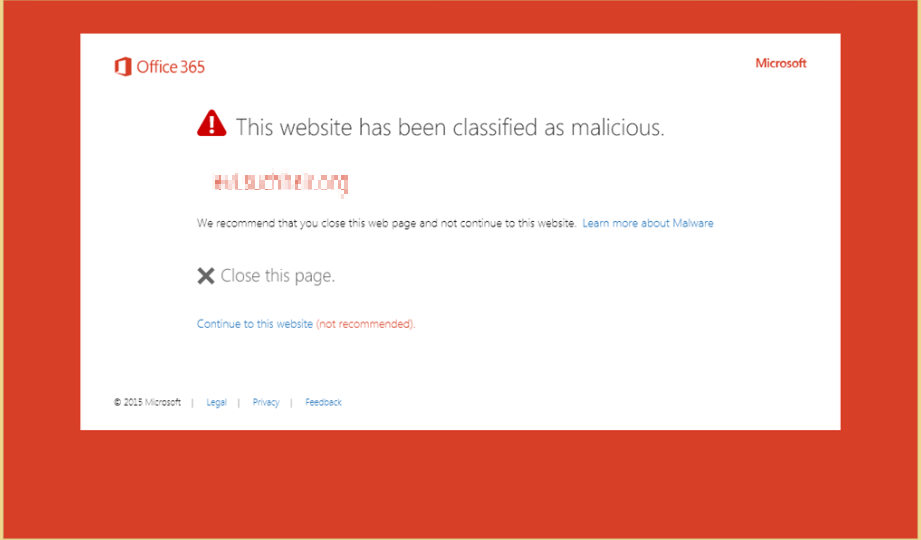
And in other cases, when it finds malicious content, end users will see this page instead.
Remember that the option to click through to the site can be presented, or not, as per your policy selections. And while I suppose false positives could be possible, why risk it? I usually prevent them from being able to do this.
Bonus tool: ATP decoder
Microsoft also has a website for messages that have been processed (and subsequently, rewritten) by Safe Links, you can use this decoder to return the original URL. To use it, simply copy a rewritten URL from a processed message and then paste it in the link window. The decoded link will appear below.
And that, my friends, concludes our review of Advanced Threat Protection. Again, I am thrilled that this now comes bundled inside of the Microsoft 365 Business SKU–on the Enterprise side, you have to move all the way up to the top (E5) to get the more advanced features like this, which are based on machine learning, etc. Of course, as I mentioned, it is always available to add-on to any other subscription, for just $2.00 /user/month (USD).




Comment (1)
An awesome work Alex. Thank you!