Hybrid Network Architecture Options & Pre-Reqs for SBS Migration to Office 365 & Windows Server 2016
In this post I will lay out some of the options to consider when replacing the late Small Business Server (SBS) product with a hybrid architecture. Along with the huge success of Office 365, many small businesses are realizing the benefits of a hybrid deployment model, where some infrastructure is kept on-premises, and other parts of it live in the cloud. Most of the clients I work with opt for a hybrid architecture using Office 365, Windows Server and sometimes even Exchange Server. In certain cases, Azure comes into play also.
Plan for Password Synchronization
When you move data & services to Office 365, you have a decision to make about identity & password management: where will you keep the locus of control for user accounts, passwords, and mailbox properties?
- Shift management over to Azure AD / Office 365 only (no password sync)
- Keep management on-premises using either:
- Windows Server Essentials Azure AD / Office 365 integration (basic password sync)
- Directory Synchronization & Hybrid Exchange Server (full directory sync)
In my experience, when presented with the option more small businesses than not prefer to synchronize passwords, using either Directory Synchronization (Azure AD Connect) or the Office 365 Online Services Integration in Windows Server Essentials. Both of these technologies allow you to provision users and synchronize passwords from your on-premises or hosted Windows Server environments, but they are not the same.
Whereas Azure AD Connect will provide a true synchronization of directory objects and extended attributes on a regularly scheduled interval (e.g. every 30 minutes), the Essentials Dashboard integration will not. Instead, the integration simply writes adds/changes/deletes directly into your Microsoft online tenant at the exact time you make them through the Dashboard.
One key difference to weigh when considering these options is that Directory Synchronization / Azure AD Connect will actually lock you out from making certain changes in the Office 365 Admin portal. For this reason, it is highly recommended that you keep an Exchange server on-premises (you can use a free license) to help manage Office 365 Exchange Online. In the case of Windows Server Essentials Experience, no Hybrid Exchange server is required–user and mailbox management tasks can be executed right through the Essentials Dashboard.
Note: If you add an Azure AD Premium or Enterprise Mobility Suite subscription, you can also configure password write-back & self-service reset (so that users can change their own passwords in the cloud and have them updated on-premises also). This solution requires Directory Synchronization with Azure AD Connect.
Choose a Migration Method
The decision about Directory Synchronization is closely related to the decision about how you will migrate Exchange data from your on-premises server to Office 365. I almost always prefer to use the Remote Move method, which requires Directory Synchronization (Azure AD Connect) and a hybrid Exchange server. However, it is also possible to configure Hybrid Exchange for Remote Move, then convert your environment away from hybrid, and enable the Windows Server Essentials integration after the migration is complete.
Otherwise, if you feel the Remote Move method is introducing too much complexity, or you can’t get it working for some other reason, you have two other alternatives–a cutover migration or using a third-party tool. Both these methods work well with or without either of the two above-mentioned password synchronization options. Read more about the migration methods here. Possible migration options:
- Third-party or Cutover method –> Office 365 / cloud-only user & password management
- Third-party or Cutover method –> Windows Server Essentials Experience / Office 365 integration
- Remote Move method –> Azure AD Connect / Hybrid Exchange Server with Office 365
- Remote Move method –> Windows Server Essentials Experience / Office 365 integration
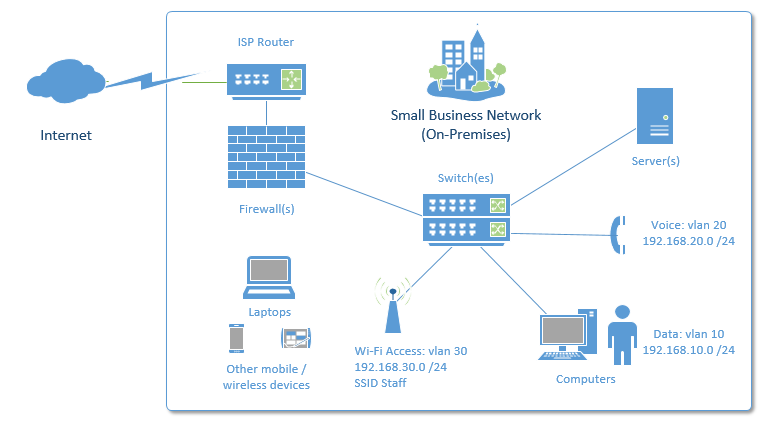
Review & Fix the Existing Network Architecture
In some cases, existing Small Business Server deployments will have a funky network configuration, like having the SBS server assigned a second NIC that communicates directly with the Internet router. I personally never set my clients up this way but I see it out in the field every once and a while.
This legacy configuration needs to be fixed before your migration project. The correct layout moving forward is to have your ISP connection behind a real firewall, which in turn acts as your gateway on the network (usually assigned the “192.168.x.1” address). Then, every other device, including your Small Business Server, gets a single IP interface connecting back to a central switch or stack of switches.
An example of what you are aiming for is depicted in the diagram below.
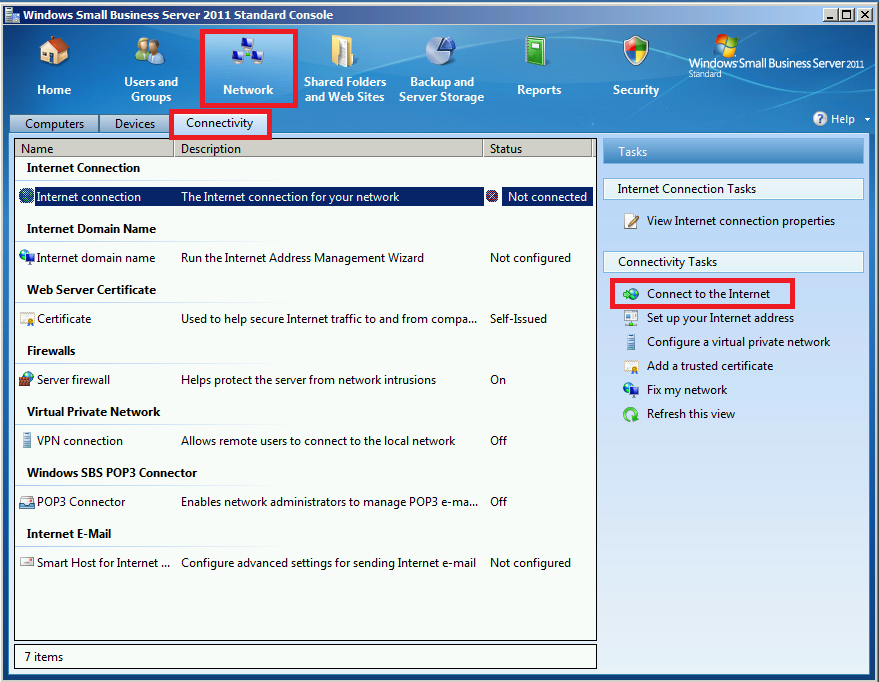
If you have to make these structural changes to your network and retire an Internet-facing server NIC, then it will be necessary to re-run the Internet connection wizard on the SBS source server. Note that clients may not have access to the Internet or network resources until this procedure is completed. From the SBS console, you would browse to Network > Connectivity > Connect to the Internet. Step through the wizard to complete the configuration.
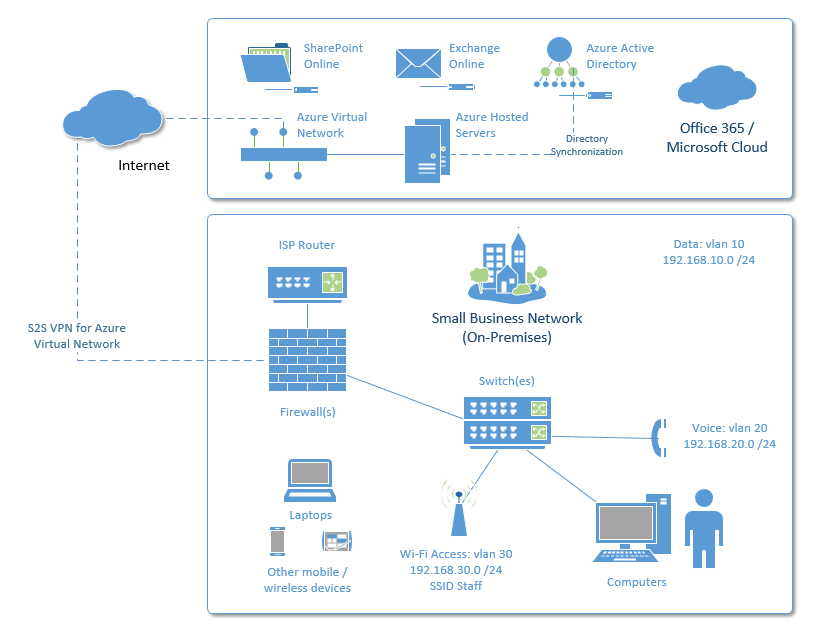
Hyper-V On-premises or Azure Virtual Machines?
If you do not have a lot of data and applications that require a hardware investment on-premises, and you plan to use your server mostly for Active Directory and light file storage, maybe even paired with a RemoteApp deployment, then you might consider hosting your server(s) in the Microsoft Azure cloud. Here is an example of such an architecture:
Otherwise, if you are like 95% of other small businesses, you will probably stick with an on-premises deployment of Hyper-V. Even if you just have a single virtual machine for Windows Server Essentials (WSE), Hyper-V virtualization will enable some impressive superpowers–dynamic growth capabilities, improved fault tolerance, and more robust backup and DR options.
Most organizations have additional line of business applications and other data, which usually implies additional virtual machines. Best practices: separate each of your applications / services into individual virtual machines–doing so removes a common fault-domain. Each VM has its own resources, and its own Operating System–a problem on one VM does not carry over to another.
Options for redundancy
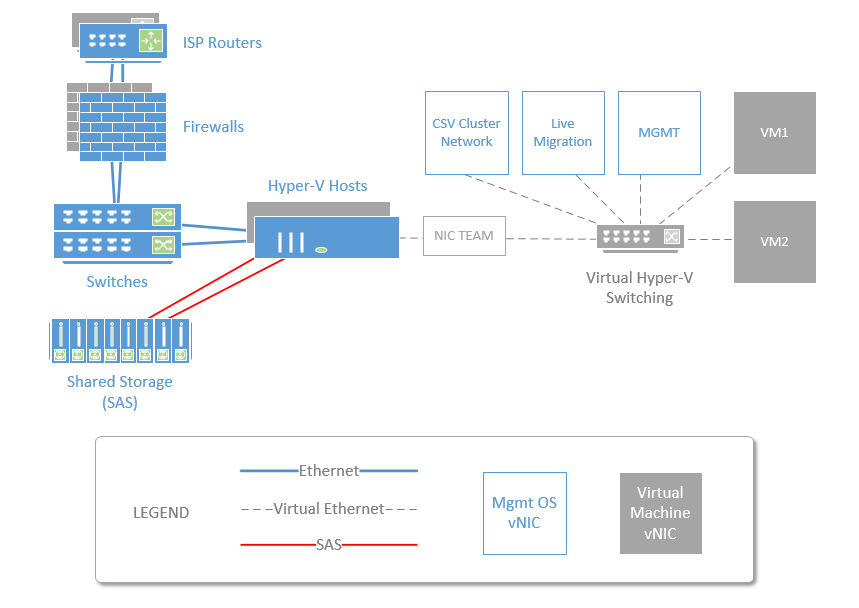
It is worth going over what you have available in modern Windows Server networks, particularly when deploying on-premises. For example, since 2012, we have had awesome built-in features such as Storage Spaces and NIC teaming. The former allows you to deploy highly available software-defined storage solutions, and the latter provides for network load balancing as well as failover–simultaneously enabling better network throughput and redundancy.
Small businesses typically do not get access to these kinds of “Enterprise-grade” solutions since they are cost-prohibitive. In Windows Server 2012, 2012 R2 and now 2016, we have access to more and better “superpowers” than ever before, all at the cost of commodity hardware and a Windows Server license. Let us lay out the components of a robust, fault-tolerant and fully redundant server solution.
Network fault tolerance
For improved fault-tolerance throughout your network, I recommend:
- 2x Internet Service Providers with WAN failover configured in your firewall
- 2x firewalls with clustering enabled
- 2x network switches (even if you don’t need that many ports)
- 2x NIC’s per host server minimum, one connection to each switch
- Enable Hyper-V & NIC teaming, then attach the team to a Hyper-V virtual switch
Maybe this sounds like a lot, but it really does not have to be very expensive. Yes, I know: “But redundancy means twice the price!” That is true, but even small businesses expect a high level of uptime these days–indeed that’s part of why they are becoming more and more invested in cloud-based technologies. In my opinion, a second Internet connection and redundant firewalls/switching is an easy investment to make. But maybe that’s just me.
Server & storage fault tolerance
Many small businesses will shy away from buying 2x servers, and that’s okay. Most server hardware is pretty resilient these days, and will include things like dual power supplies and RAID controllers at very low cost. You may not have full redundancy, but you will have a fair amount of built-in fault tolerance even with a single host server.
On a standalone host, I recommend that you configure a RAID-1 mirror for the OS, and at least one RAID-5 or RAID-6 array for the data volume, where you will store your Hyper-V virtual machine data. Go RAID-10 if you’re concerned about performance. Enable a “hot spare” for auto-recovery of a degraded array. See your hardware vendor’s documentation for more details. You can also use Windows Storage Spaces to manage disks, and this feature is compatible with a clustered configuration.
In order to take advantage of Windows Server Failover Clustering (lose an entire physical server and let VM’s keep running), some kind of shared storage is required. Shared storage used to be fairly expensive, but there are now many affordable options available to the SMB.
In Windows Server 2016, you can even create clusters across multiple servers using internal storage with Storage Spaces Direct. However, this solution requires 10 GB networking & at least four host servers, so a traditional two-node failover cluster attached to an external storage enclosure will still be preferred by most small businesses.
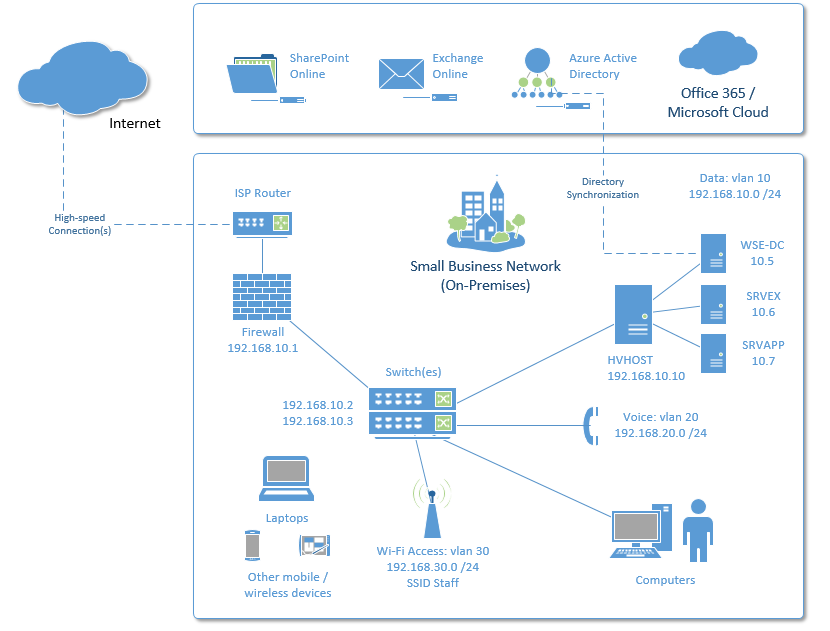
Here is a diagram that depicts an on-premises solution with full redundancy in networking, servers and storage:
Conclusions
The decision to move away from legacy Small Business Server products is the right one–but there is no single “best” migration path forward anymore, as there was in the past with SBS 2003 to version 2008 or 2011. I have my opinion about what makes for a good solution, and I’ve been helping small to mid-sized businesses of all types get there for many years now–in fact some of these alternatives were available with Windows Server 2008 R2 and BPOS even before Office 365 came on the scene. In general, I think the above considerations go a long way in helping to weed through some of the decisions so that you can arrive at the solution that best fits your own business objectives.




Comments (4)
Hi. Thanks for all your articles on these sorts of subjects. Can you point to more details on this line? I can’t seem to turn up anything on it in searches without knowing more about it.
“Azure AD Connect will actually lock you out from making certain changes in the Office 365 Admin portal.”
Yes, when you have enabled Azure AD Connect and you are exporting directory information to Azure AD, you will not be able to edit, for example, alias addresses in EAC online. It will give you a message that says, in effect, you must make these changes on the local AD instead.
Hi Alex,
Thanks for the information which I’m using to plan our SBS08 to WS16 migration. Wonder if you have thoughts or idea on what to do as we are on older style domain.LOCAL domain, where as now it seems it is best to be a FQDN to allow use of non self-signed SSL certificates.
Do I keep going with the .local domain, should (can) I migrate to a .com domain, or start fresh with .com and move everything across?
We only have 40 users, so even a dump and rebuild shouldn’t be too hard to do. We do use O365 for emails/onedrive, with azure connect (??) doing dirsync duties..
I don’t think it is necessary to move from .local–these are still being deployed. The only difference is, that third-party purchased SSL certs will only have the external domain name, which is totally fine. Just ensure that the clients always access published services using the internet domain name, and you’re good to go. It is kind of a pain to move to a new domain, and the best way is either ADMT, or just forklift.