Boost your security with Hybrid Azure AD Join: From Zero to Conditional Access in one afternoon
“Alex, I work at a non-profit and I would love to take advantage of the better security in Microsoft 365 Business (we have Business Premium now), but it sounds like it is for “cloud-only” customers? Is that right?? We are using Office 365 for Exchange, but we can’t go cloud-only with Active Directory and files because our vendor does not support their application in the cloud (has to be on LAN) […] Do you recommend EM+S instead? ATP? […] Also, how hard is it to do conditional access for hybrid??” Thanks, Gaylae
Good questions, Gaylae (not sure if I should pronounce that Gay-lay, or Gay-lee??), but in any event, I can tell you: Microsoft 365 Business fully supports hybrid environments, so you do not need to piecemeal your own SKU together. And have no fear, configuring Conditional Access for a hybrid environment is going to be a snap–I’ll show you today!
Just because you are “stuck” on-premises doesn’t mean you can’t take advantage of what the cloud has to offer. Indeed, most small businesses have already made the move to services like Exchange Online, and are using the cloud for at least some of their critical workloads. File shares will most likely be the next mass exodus. But you can also start migrating your endpoint management & security operations into the cloud at any time–it’s easier than you might think!
In this post I will demonstrate how simple it is to get your small or mid-sized organization connected to Azure Active Directory in order to enable strong security policies that will help prevent data leakage and unauthorized access to company data and resources.
Pre-requisite
As Gaylae has noted, you will first of all need a subscription that supports Conditional Access. For the small and mid-sized business (under 300 seats) I recommend Microsoft 365 Business. Otherwise Microsoft 365 Enterprise, or the Enterprise Mobility + Security bundles will accomplish the same.
Step 1. Prepare for Azure AD Connect
If you already have synchronized your identities to Azure Active Directory you can skip this step and the next one. Some small orgs do have existing hybrid environments, while others may need to establish it.
Now especially in the SMB market, domains on-premises often have a “.local” or “.lan” suffix instead of something Internet-routable like “.com” or “.org.” Non-routable domains are meaningless in the cloud, so this is the first thing we have to fix, and it’s really easy to do. You can follow this article from Microsoft.
Estimated time to complete: 15 minutes.
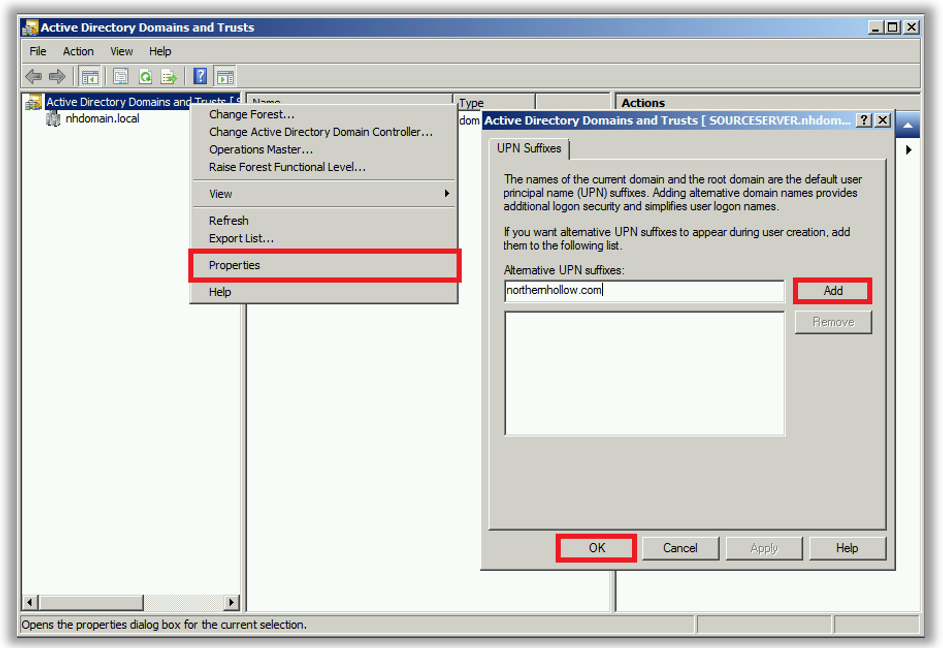
As well, you may need to import alias addresses that you have in Exchange Online. This means you need to have an on-premises Exchange Server in order to edit certain attributes that are specific to Exchange email. I have written about this before, but just keep this in mind–if you have to install Exchange and add back the attributes, it can add 1-2 hours to your mini-project.
Step 2. Install Azure AD Connect
The next step is installing Azure AD Connect; most small and mid-sized orgs will do just fine with the Express installation. However, you can do a Custom installation if you want to constrain the scope of your synchronization to specific OU’s, etc.–technically you only need to sync your active users and computers–I would not bring any distribution or security groups into the cloud as those are better managed using Office 365 Groups instead (which are cloud-only objects).
Estimated time to complete: 15 minutes

Step 3. Configure Hybrid Azure AD Join
Completing Hybrid Azure AD Join requires you to perform two more steps on-premises:
Stepping through the wizard and deploying the GPO only takes a few clicks.

Optionally, you can also deploy a GPO that will auto-enroll devices with Microsoft Endpoint Manager (Intune). This extra step would allow you to put other policies against the domain-joined devices using MDM rather than GPO, but it is not a requirement to get Conditional Access working for Hybrid Azure AD Join.
Estimated time to complete: 20 minutes, although you may have to wait a while for all your domain-joined computers to get the new policy and be recognized as Hybrid Azure AD Joined machines in the cloud.
Step 4. Set up your Conditional Access policies
At this stage the cloud is now aware of the difference between Windows 10 devices that are joined to your corporate domain, and those which are not. That means you can decide to limit access on non-corporate computers in various ways.
For example, perhaps your organization would like to allow web access from home PC’s or personal laptops (as long as the user can pass an MFA challenge), but they would like to limit or block the ability to use thick client apps such as Outlook, Word and OneDrive, which can sync and cache company data on the local device.
To make this happen, create two policies: one for web access, and another for modern client access.
Estimated time to complete: 15 minutes.
Browser access: Require MFA
Go to Azure AD > Security > Conditional Access. Create a new policy:
- Name it GRANT – Windows 10 Browser access.
- Select All users and exclude at least one emergency access account.
- Select the apps you want to protect for example Office 365 (includes apps like Exchange, SharePoint, Teams, etc.)

Select Conditions:
- Under Device platforms select only the Windows option
- Select Client apps and choose only the Browser option.

Under Access controls > Grant pick Require Multi-factor Authentication.

Create and Enable the policy when you’re ready. Users will be required to register for MFA and complete the MFA challenge moving forward, when accessing Office 365 apps on the web.
Windows 10 client access: Require Hybrid Azure AD Joined device
Complete the same steps to begin building your policy, naming it GRANT – Windows 10 client app access, then selecting the same users and apps as before.
Then under Conditions, again selecting Windows 10 as the Device platform, this time target Client apps > Mobile apps and desktop clients > Modern authentication clients.

Moving to Access controls, pick Require Hybrid Azure AD joined device. This means non-corporate, non-domain joined PC’s cannot get access to Office 365 using desktop applications.

It would be your choice whether to also require MFA for this access scenario, depending on your needs. Or you could go even further with Require device to be marked as compliant–for instance if you are going to be enforcing device compliance using Intune policies as well.

The controls can be as strong or as relaxed as you need them to be for each unique access scenario.
Conclusion
See, not so hard was it? Conditional Access with Microsoft 365 Business works no matter where you are at in your cloud journey.
The cloud enables you to go faster, and further, than you ever have before, and with better security than what you have been able to offer on-premises in the past.
Layering “device aware” Conditional Access rules into your security architecture is one of the primary reasons I recommend that organizations upgrade from Office 365 to Microsoft 365, whether they are hybrid or cloud-only. Once you can actually distinguish between corporate and non-corporate contexts, you can start taking advantage of some pretty amazing security controls, and you can choose just how much access personal / unmanaged devices are allowed to get.
And there is so much more–MAM policies for personal mobile devices, Office 365 ATP for better anti-phishing and anti-malware protection, Sensitivity labels, Retention labels and policies, DLP–the list goes on!
Every organization can benefit from these capabilities, especially those that work with sensitive data, or customer data that might be subject to regulations like GDPR or the new California Consumer Privacy Act. Eventually I think it is safe to say that every business is going to be responsible for better data stewardship and more compliance with laws and regulations, so it is best if you can get started as soon as possible.
And hey, Gaylae, did you know that non-profits can redeem 10 free licenses of Microsoft 365 Business to get started? This should be enough for you to demonstrate a Proof of Concept to management, and see if they will open the budget a tiny bit more for that upgrade from Office 365 Business Premium!


Comments (11)
I would also recommend to create a CA policy to deny Other Apps (legacy protocols).
This is indeed recommended in my CA guide, part of the Microsoft 365 Best Practices docs that I produce. In fact, EAS is also considered legacy if you do the right thing and enforce approved apps for maximum data security on the endpoints.
Hi,
Do you know of its possible to enable MFA only for ”Thick” Outlook? I only seem to get it done alongside with other apps as OneDrive and more.
You can be as granular as you like–for example if you wanted a policy that only applied to the Outlook thick client, you would do:
-Assign to users that you want to target
-Pick only Exchange Online as the cloud app (no other apps)
-Pick Conditions > Client apps > Only modern clients
-Access Controls > Select all that apply (MFA, etc.) and then choose either one or all controls
What if you don’t want to require MFA for web apps on AD joined devices?
Simply use the Conditions to target Client apps, and pick Browser. Then your access controls for the “Browser access policy” might be “Hybrid Azure AD Joined” OR “MFA” rather than both. A separate policy can be used for targeting modern clients with your own desired access controls there.
Are you sure that Conditional Access (CA) is available on M365 Business subscription, from my researching it only looks like CA is in the M365 E3 and up plans? Or you need a Azure AD P1 or P2 license. The M365 Business has Azure Business AD, which does not look like it has CA. I am in Canada, maybe that matters. It would be great value if it did at $25.60 CAD/user/month if it does get you CA.
False, it is available in Microsoft 365 Business. Please refer to this article as well as the service description.
Thanks. I did not come across that article in my searching, but that is great to see. I will likely be upgrading a number of Office 365 Premium users to M365 Business this year who are remote workers, and having Intune and Conditional Access will be most beneficial. Thanks again, I have enjoyed many of your articles, very informative.
Hi – can you setup a policy to only allow access to cloud apps from only Windows Azure AD joined machines rather than hybrid? We have a customer that is going wants to limit access to only corporate PCs joined to Azure AD.
They don’t have a control for Azure AD Join, instead you must use the access control called “Require device to be marked as compliant”–and that refers to Intune/Microsoft Endpoint Manager. So the devices that are joined to Azure AD should get enrolled into Intune automatically if auto-enrollment is configured in the portal, and you have the right subscriptions (e.g. Microsoft 365 Business Premium, E3 or E5). That’s the way to do it for sure. You want to start moving your management of devices over to Intune/MEM.