Updates to the CIS Controls and Free Microsoft 365 Assessment Workbook
I know my community is already familiar with the CIS Critical Security Controls, as well as the free assessment workbook that I adapted from AuditScripts to apply to Microsoft 365 environments. This week, the Center for Internet Security released updates to the framework (we are now on v8). You can download the new controls here, and if you want to see the recent webinar covering these updates, go here.
Updated for Cloud
This is a particularly important update for Microsoft 365 customers, and any cloud-first, mobile-first organization who operates primarily out of SaaS-based applications. Why? Because one of the goals with v8 was to modernize the Critical Security Controls for this type of environment! The result is surprising!
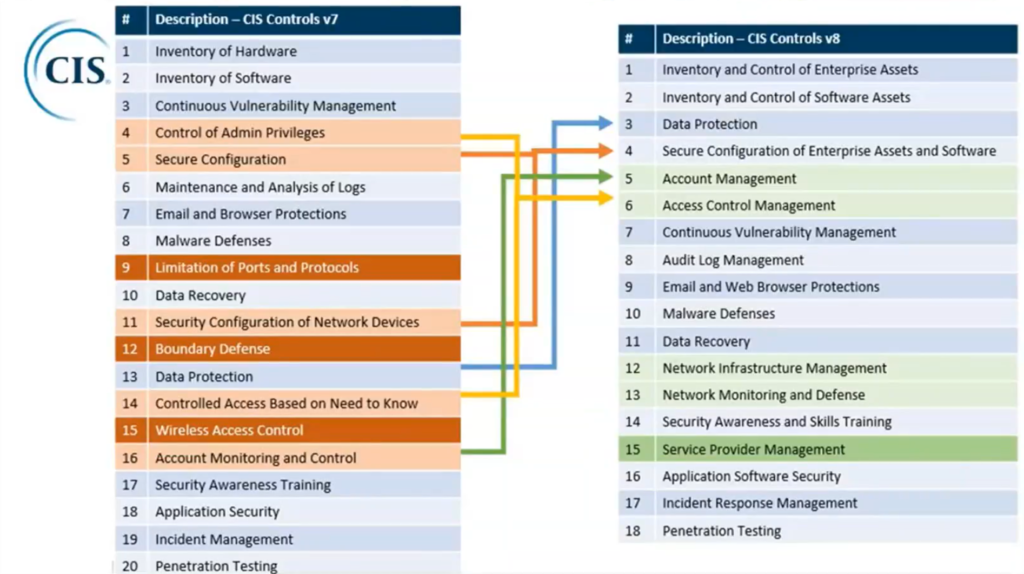
That’s right! We actually have fewer controls; the list has shrunk from 20 to 18. What happened? Well, a number of the controls that pertained to legacy network and server infrastructure have been collapsed (e.g. Limitation of Ports and Protocols, Secure Configuration of Network Devices, Boundary Defense, Wireless Access Control). It is not that these have been completely discarded, but in some cases the sub-controls (now referred to as “Safeguards” in v8) have just been moved under new headings such as Network Infrastructure Management. We also have a brand new control (#15) covering Service Provider Management, to address all the cloud services that we have to manage these days!
A New Emphasis on Data Protection and Identity + Access Control
One really significant difference I want to highlight is the re-ordering of certain controls. The CIS framework prioritizes the list of Safeguards for you; so the logic goes that you must establish inventory and control of hardware assets (#1) and software assets (#2) before you can proceed to later steps (you cannot protect what you don’t know you have). Therefore the first two controls have not really changed much; what is more noticeable is that Data Protection has been advanced all the way up to #3 on the list!
Establishing a secure configuration for devices and applications has moved up to #4 (previously #5) and now we have Account Management in position #5, and Access Control Management at #6. Therefore Identity has moved up the scale as well (some of these identity-related Safeguards were located way down in control #16 previously).
If you think about the tools that are included with Microsoft 365 Business Premium and Enterprise plans, and specifically within the Enterprise Mobility + Security suites, you will see how well Microsoft tracks with the “cloud-first” updates to this framework. Microsoft Endpoint Manager (Intune) and Azure AD Conditional Access can help you accomplish control of hardware and software, secure configuration, and strong authentication and access controls. Azure Information Protection can cover most of the requirements under Data Protection.
But I should also highlight that Microsoft 365 cannot address every Safeguard within the new control framework. In fact, pretty much everything from #11 on down to #18 would require working outside the Microsoft 365 suite of tools (and some of it is policy & procedure, versus some kind of technical control or feature, anyway).
No More Categories (Focus on the Implementation Groups!)
In version 7, we still had “Categories” such as Basic, Foundational, and Organizational. That concept is now retired, and there is more emphasis placed on the Implementation Groups which were first introduced in v7. Implementation Group 1 (IG1) is a “Basic Cyber Hygiene” or “Baseline” set of Safeguards for any Small or Mid-sized Enterprise.
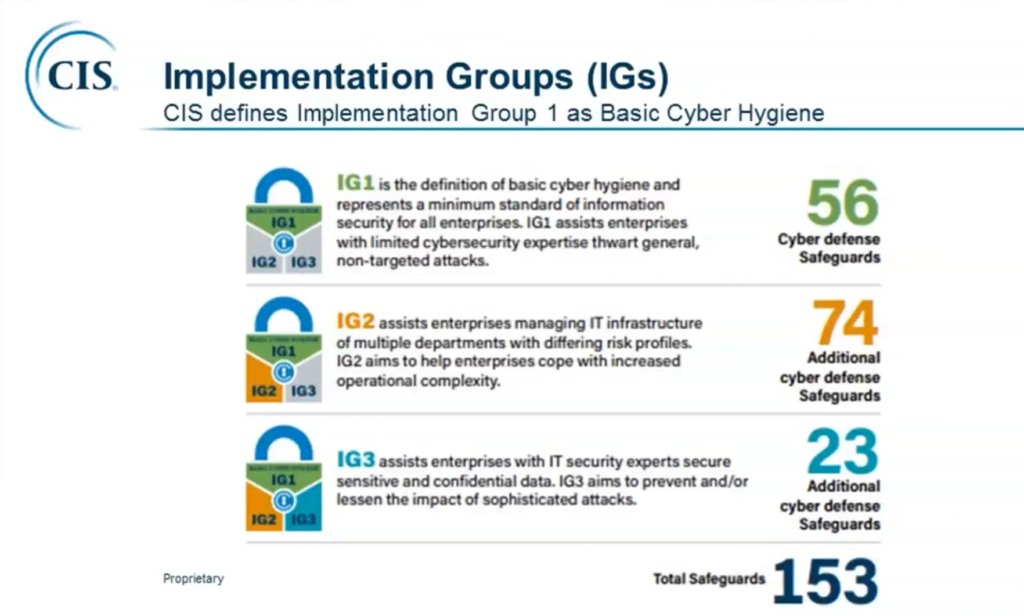
Interestingly, even though we have fewer controls overall, we have more Safeguards within IG1 (previous version had 43 sub-controls, we are now at 56). However, if you are a Managed Services Provider, you should be looking to adopt IG2 or even IG3 for your own organization. Why? Because you manage a lot more complexity and may have differing risk profiles among your customer base (see the description for IG2). Not only that, but you are a bigger target for more advanced attacks (e.g. the recent Solorigate supply chain attack). That having been said, most of your customers will probably benefit greatly just by adopting IG1.
Conclusion
I participated in a recent webinar with Acronis, and one of the questions from the audience was, “Where does the responsibility of the MSP end the responsibility of the MSSP begin?” Today these are still (potentially) separate entities, but in my view, that distinction cannot continue for very long. It is past time to open our eyes to the sharp increase in advanced attacks that we have seen against MSP’s and other IT vendors. If you are not on your way to implementing a formal framework such as CIS or NIST CSF to a pretty high degree within your own business, then it is unlikely you will still be in business 5 years from now. You can outsource some MSSP functions of course: detections, Incident Response and so on, but however you build it, you have to be ready to offer a full spectrum cybersecurity solution to your customers. There is no room for “Bronze/Silver/Gold” packages here: everyone gets advanced security, full stop.
Now, if you stuck with me to the end of this article, here is your reward: the updated Assessment Workbook for Microsoft 365. This tool contains all the Safeguards from the CIS Controls IG1. As a bonus, I am also including a worksheet for the Australian Cyber Security Centre’s Strategies for Mitigating Cyber Security Incidents (this is the larger framework from which the Essential Eight is derived).
Update: I also offer a course on implementing the CIS Controls. Included with this course is an expanded assessment workbook (to include all three implementation groups) and other resources such as Information Security Policy templates, and more.




Comments (4)
So Important – I’m still amazed how many businesses aren’t implementing security measures due to perceived costs. Excellent update!
Thanks, Jim! Agreed. I did a poll recently and it is shocking how many folks still don’t have some of the first few controls addressed.
This is a great tool for MSPs. I also watched the Acronis video Alex mentioned above and it has useful info. The Five Top Secrets:
1. Integrate, automate, consolidate, practice the recovery
a. Start small with CIS Controls or NIST CSF
2. Principal of Least Privilege
a. Cloud-only AAD Admin accounts – different from on-premise, different password
b. On-premise AD Admin accounts – different from cloud, different password
c. Minimize the number of Global Admins in your environment
3. Use Microsoft Secure Score
a. Track improvements over time
4. Make sure your people are trained
a. Stay up to date on new threats
5. Zero Trust – Focus on Identity Security – 3 principals
a. All access attempts are completely verified
b. Grant the least amount of privilege
c. Assume breach or compromise
With regards to practicing Incident Response, the State Government of Victoria of Australia has some useful info here:
https://www.vic.gov.au/practice-your-cyber-incident-response