iPadOS breaks MAM-enforced Conditional Access?!
In case anyone missed it, this bombshell dropped last week:
In summary: when iPad gets updated to iOS 13+ at the end of this month, the OS will change from iOS to iPadOS. And when that happens, Azure AD will see these devices as macOS devices, not iOS devices. At least for certain apps like Safari and the native Apple mail app (of course its the ones that matter).
It seems other browsers and apps are not affected, further confusing matters–the Microsoft apps and third-party browsers like Chrome for example, would still be seen as iOS–that is my understanding from reading the above article.
Is MAM-only management broken now?
The most disappointing result of this change is that it will be impossible to enforce the use of the Outlook app for email.
Let me be clear however: your App Protection Policies will still apply to the Microsoft apps like Outlook and OneDrive. So those protections aren’t lost. What is lost, is the ability to enforce the use of the Microsoft applications using the access controls “Require approved client app” and “Require app protection policy”–those controls only apply to Modern client applications running on iOS and Android.
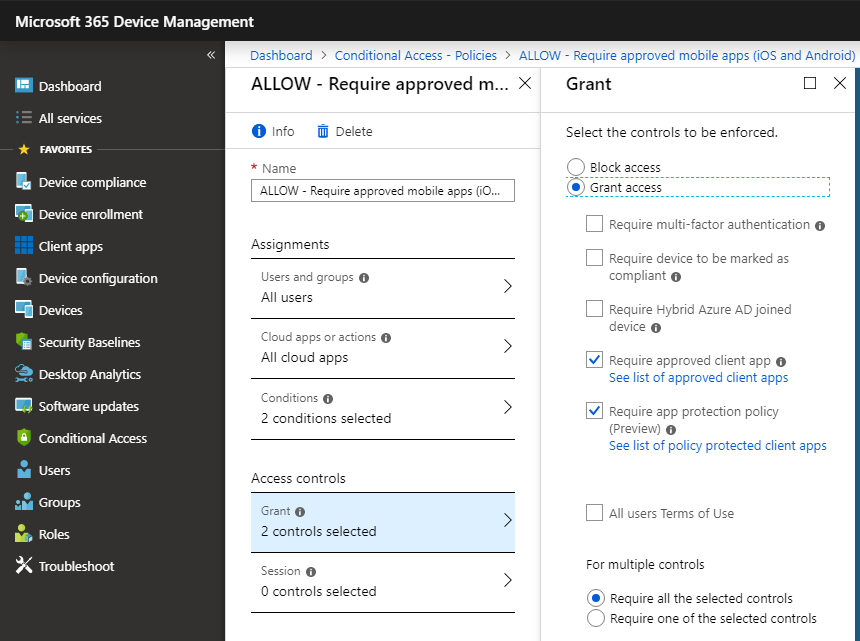
So if I apply these access controls against iOS, then iPhones are still bound by the policy and it will not be possible to add a mail profile to the native mail app, but that same native mail app on iPadOS is not bound by the policy (since Azure AD will recognize it as a macOS device). And, you cannot fix the situation simply by applying these same access controls against macOS–because these access controls only work with iOS and Android platforms.
Bummer.
So what do I recommend? Unfortunately I can see only one way around this dilemma. You are probably better off enforcing MDM. That way you can still control access to the corporate data without leaving any gaping holes, and you can pull back the access to that data if you need to.
My recommended baseline policies already require that macOS and Windows 10 devices become enrolled and compliant with Intune policy–so if you are following those then presumably you are covered… But it still leaves other questions in my mind.
- If you have to compel those iPadOS devices into MDM compliance, which type of compliance policy applies to them? Presumably the macOS policy?
- What about the apps that still register as iOS–if those are tied to a compliance requirement also, then do both the iOS and macOS compliance policies apply to the device?
- Will we see two device objects representing the same physical device get registered in the Intune portal in that case?
And if your goal was to do MAM for BYOD users, now you have some iOS devices being managed one way and others, another. So confusing. We will have to figure it out quickly when the update drops at the end of this month.
Maybe you’re just better off requiring all devices to be fully MDM enrolled, rather than trying to split the difference. It just sucks because there are so many BYOD iPads out there, and many people would rather just enforce MAM on mobile platforms and not deal with MDM if they can avoid it. From my understanding of this announcement, it will no longer be possible on iPads.
Until MS can figure out how to fix this problem–maybe the ability to apply those same access controls against the desktop platforms or whatever–I just don’t see another good choice. Does anyone else out there have another idea–something I’m not seeing?
Let me know if so!





Comments (3)
We have conditional access policies that a) require managed apps from mobile, and b) also block access from anything other than a browser from any other OS (i.e. desktop OS’s).
So I assume that ipads will now be detected as other OS, and so will be blocked from using e.g. activesync and only be allowed to use a browser. In which case at least they remain secure, even though they cannot use their mobile apps any more. Is that your understanding?
With many VIP users using ipads daily, this is going to cause many issues that is for sure.
This has a potential to be a big deal, I agree. However, some preliminary testing on iOS 13 beta has shown hopeful results. Still working to gather more info, but so far testing with policies that target Exchange online it looks like when you update the CA policies that target iOS and the access control require approved app or require compliant device, to simply include macOS, they seem to respect the policies. The app that is requesting access is iOS accounts, and that still registers as iOS it seems. At least for now–again this is just a beta and I have only a single report of this with some screenshots sent to me from an iPad mini user. I have yet to test myself, and on other form factors (iPad Pro, etc.)
Ok thanks Alex, let us know how you get on!