Configure alerts for your 365 Tenant from the Security & Compliance Center
If you have an Office 365 or Microsoft 365 subscription, then you should check out the Security & Compliance Center–there are plenty of tools in here to help you step up your game. Generally speaking, nothing is really configured by default, so if you want to be secure or compliant, just know that these things don’t happen by magic–you have to do the work to make it happen. Nevertheless, in recent months, Microsoft has been making strides toward giving us all a better “head start” to speak. For example:
- Auditing is now enabled by default (this did not used to be the case)
- Anti-spoofing technology has come to all subscriptions, not just those with ATP
- Some default alerts have been added into certain subscriptions
Today, let’s take a look at configuring alerts through the Security & Compliance center. With E1/G1, E3/G3 and E5/G5 subscriptions, there will also be a few default alerts enabled (which will send email notifications to tenant admins). I also found these available in Microsoft 365 Business subscriptions.
Browse to the Security & Compliance admin center, then choose Alerts > Alert policies.
From here, depending on your subscription level, you may see these four policies which are created by default:
- eDiscovery search started or exported
- Elevation of Exchange admin privilege
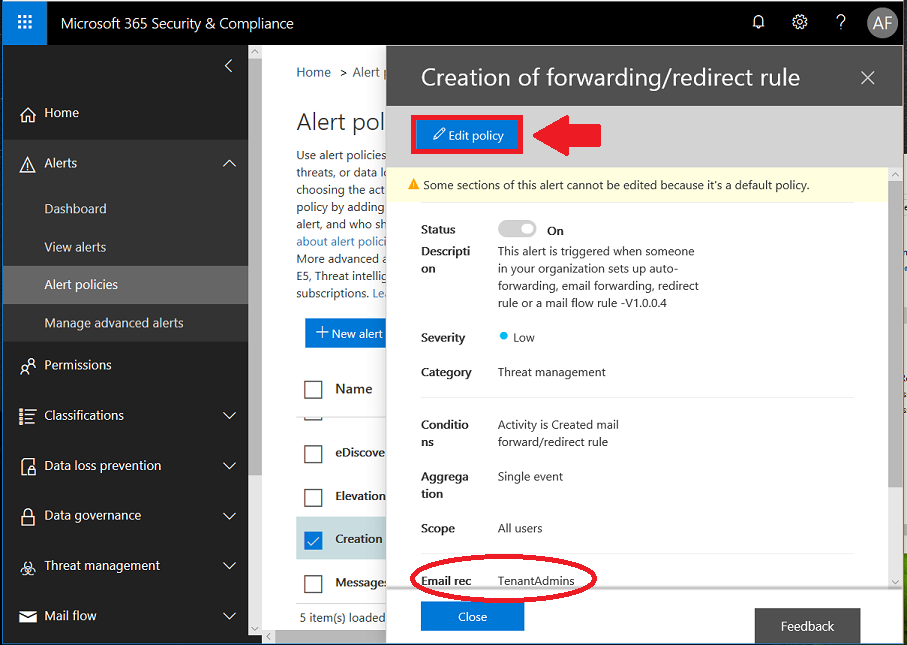
- Creation of forwarding/redirect rule
- Messages have been delayed
This is a good list of default alerts. I especially like elevation of privilege and creation of forwarding/redirect rules (this is one of the first things attackers will attempt if they gain control of a mailbox account). There will be quite a few more if you have the E5/G5 plan–some pertaining to malware campaigns, and others like “unusual” file sharing or deletion activities. See here for more detail on the default policies included with each subscription.
If you don’t monitor the inboxes for your tenant admins day to day, then you should probably edit these default policies now, and change the recipients to people who will actually see the alerts, and take action.
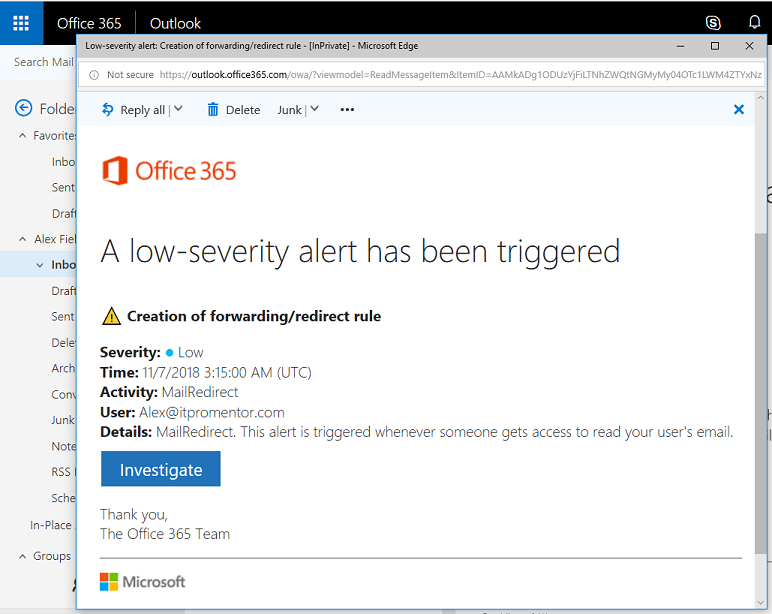
When an event occurs that trips this alert, then you can expect an email notification, like the one pictured below.
Create your own alerts
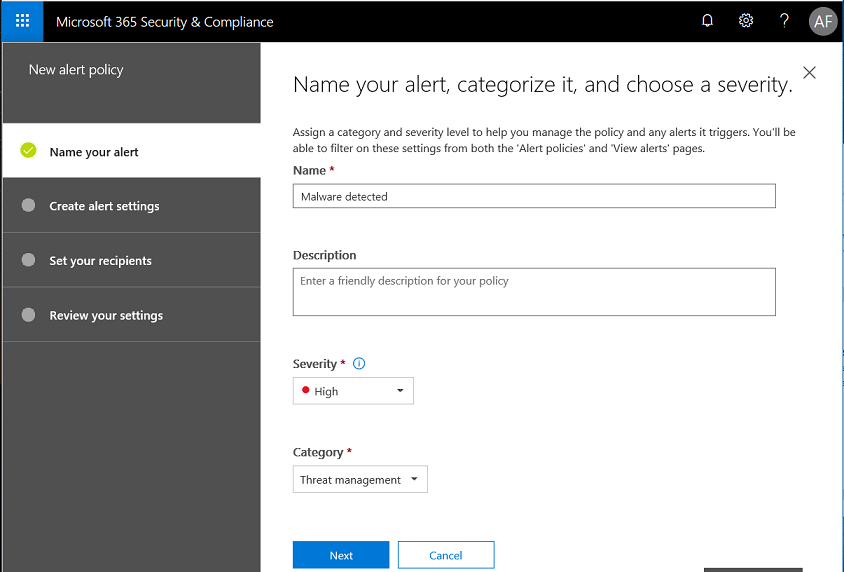
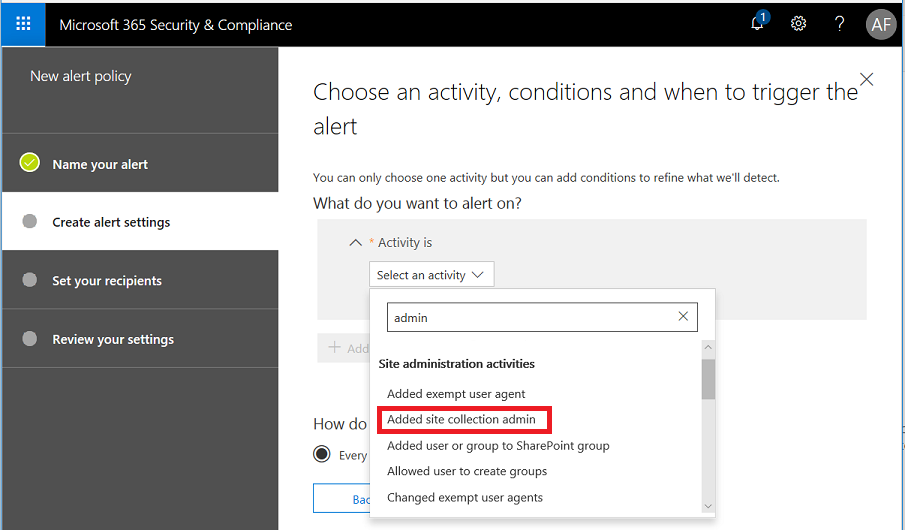
Next, you can also create other alerts, to your liking. Every tenant has access to certain alerts, and if you have subscriptions such as E5, Threat intelligence or Advanced compliance, then you will see even more options available when choosing alerts. In this example, I’ll create a simple alert for Malware detected in a SharePoint or OneDrive file–this one should be available in all subscriptions.
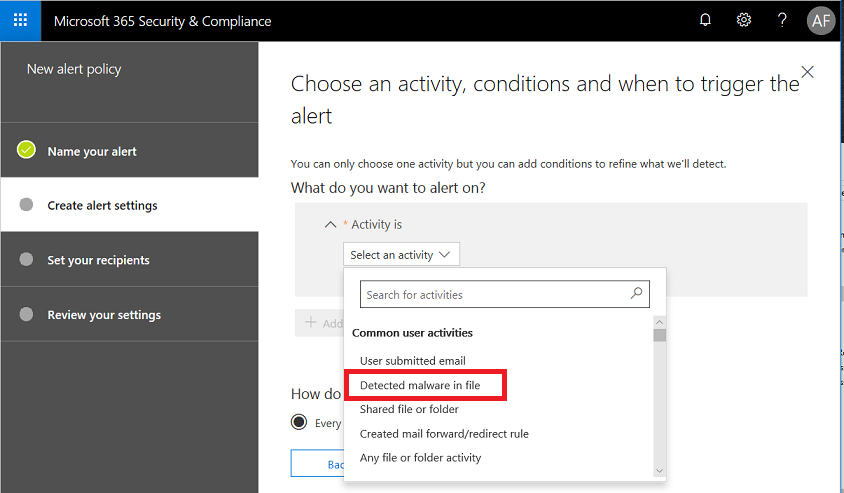
You can search for activities–find Detected malware in file in this list, and continue.
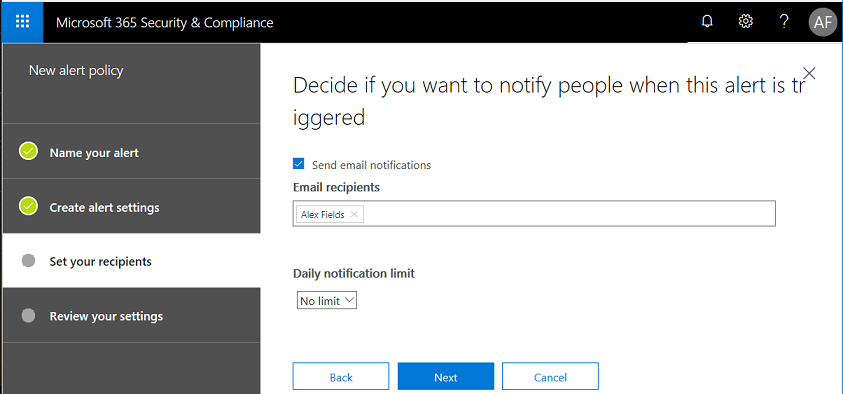
Now choose a recipient (or more than one). If you are a provider it can be beneficial to add your support contact to the GAL so it is available here.
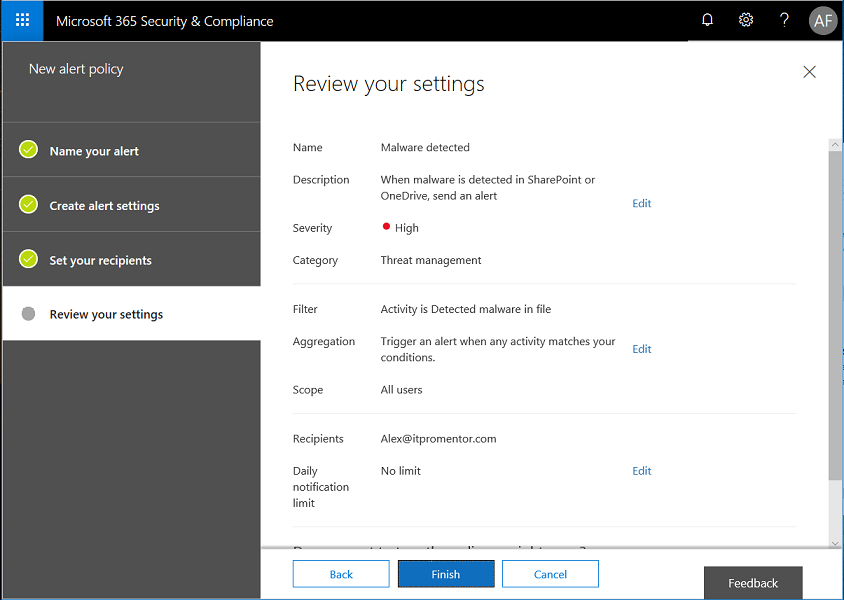
Review your new alert and click Finish.
Wasn’t that easy? You can create all types of alerts–get notified when stuff happens–files or groups are changed, deleted, or new admin privilege is given to a site collection–that’s a good one, too!
Think about the things that should or should not happen in your organization. What do you need to know about? See if you can design some alerts based on your own criteria.
A note about PowerShell
In theory, these alerts are controlled by the New-ProtectionAlert cmdlet available via the Security & Compliance Center PowerShell module. However, no matter how simple I make the rule, I cannot seem to create it in PowerShell, without seeing this message:
Creating advanced alert policies requires an Office 365 E5 subscription or Office 365 E3 subscription with an Office 365 Threat Intelligence or Office 365 EquivioAnalytics add-on subscription for your organization. With your current subscription, only single event alert can be created.
I have seen others out there comment to the same effect, so I assume Microsoft has to straighten something out. The identical rule can be created in the web interface, without issue, but apparently in PowerShell, it’s not the right subscription? Go figure.



Comments (14)
Thank you for the article. Is there a way to change the E-Mail recipients for several rules at the same time? I have removed Global Admin from amost e-mail enabled accounts and need some of these users to receive the alerts.
Unfortunately no, not with the default policies. It is possible to create and modify custom policies in PowerShell module for the Security & Compliance center, but you cannot edit the default policies using this method.
Good article. Per this URL and my testing, it appears there is no capability yet in M365 to create an alert when a new user is created in M365 admin center. Do you know if this has changed? https://office365.uservoice.com/forums/289138-office-365-security-compliance/suggestions/37115071-create-an-alert-user-creation-when-new-mailbox-is
Hi John! There is not an alert in the Alert policies area in the Security & Compliance center that you can configure, however you can still create an activity alert in PowerShell, or use Microsoft Cloud App Security to alert on Activity type of Add user.
Hi,
Do you know if it`s possible to get triggered alerts via powershell or API? As we are only receiving an email, it `s difficult to built an automatic process around that and the email only includes link to the alerts list.
Thanks
Unsure, you can use Graph explorer to see what is available. But you’d be writing an app or an Azure automation or something in order to periodically run and look for new events. Emails sent to the right system can trigger whatever you like. Even PowerAutomate can help you there, depending on what you want the action to be, based on the trigger of receiving the alert email.
Great article! Quick question. I’m with an MSP and trying to figure out the best way for us to receive these alerts on the customer’s behalf. You mentioned adding to the GAL which I assume means creating a contact, which I have done but it’s not a selectable option when I try to edit the recipients for alerts. Any suggestions or best practices you can share?
Thanks!
All you have to do is type in the external email address and hit Enter, if you don’t hit enter it searches to try and find a contact, but it is not necessary. Just input any external addy and hit Enter.
Hi Alex,
Great article!
I created an alert for when from MS Stream user “Marked video public” in Activity alerts few weeks ago. I did some tests after 24 hours, I didn’t get an alert so far. Is there another way to create an alert for Marked video public?
Thank you in advanced
Perhaps MCAS is an option?
Fantastic article!
I’m just confused around the “Tenant Admins”.
How do I know if someone is considered a “Tenant Admin”, does it go off of their permissions i.e Global admin, or is this pulled from somewhere else? Apologies for the noobish question, still got a lot to learn!!
Many thanks
Yeah it means your global admins. I don’t use that option, and always remove it, opting to put in specific destinations instead.
Hi Alex, this is great info (as is all your info), thank you! :) One thing I am stuck on is receiving alert emails to an email address outside of the client’s tenant when auto forwarding is disabled by the default anti-spam policy…do you know how we might achieve this? Thanks, Sam
Auto forwarding does not have a bearing on sending alerts to outside addresses. Instead of having the message come to an internal address and then “forwarded” out from there, you are just telling the service to directly send the message to an external address. So it will not encounter any block rules, etc. with regard to auto-forwarding that you may have set up.