Password best practices
Some people say passwords are dead. I don’t know if I 100% agree with that, since in actual fact and practice, we still rely on them heavily to secure access to our personal information online. The idea behind these “passwords are dead” sentiments is that a single factor of authentication is no longer “enough” on it’s own. Partially because there are so many hacks and credential leaks, and partially because people tend to keep very bad password practices (like simple passwords or passwords that are used on multiple sites with the same identity/email address).
Therefore, the argument goes, you need to be thinking about adding other protections such as 2FA (Two-Factor Authentication) wherever possible. Rather than passwords only, you should be introducing multiple forms of authentication:
- something you are (e.g. biometrics)
- something you have (e.g. mobile device or hardware key)
- something you know (e.g. your traditional passphrase, or a security question)
So here’s the thing: Regardless of whether you’ve enabled 2FA, proper password hygiene is still very important. And if you are exposed in a confirmed security breach, such as the LinkedIn or Yahoo ones in the last year or two, you STILL need to go and change your passwords. And probably when this happens, you have to go and do this on more than just those websites, if you are like many people, and tend to re-use the same passwords in multiple locations.
Start eliminating your risk factors
Without further ado, here are the simple password hygiene rules / best practices that you need to be following:
-
Pick complex passwords (11-16 characters, non-dictionary words, non-alphanumeric, etc.)
-
Use different passwords everywhere (use a password manager to help)
-
Change your passwords at least every few months (e.g. quarterly)
-
If you are caught in a breach, change passwords ASAP
-
Still enable 2FA as an extra layer of defense
There you go, following those 5 simple rules will place you in the safest 5% of users on the Internet. This is a completely made up statistic, and I have no idea if it’s accurate, but for every one of these things that you’re not doing, you are allowing yourself to sit in a much higher risk bracket. Don’t be the sucker in the room. Start eliminating that risk by following those simple rules.
How to Implement this Today
I get it, this is totally an inconvenience. But you know what else is inconvenient? Having your identity stolen. Having your bank accounts accessed, your email hacked or your personal information or business exposed. But there is good news–it doesn’t have to be a huge project or take a long time (okay, it will still take some of your time, but stick with me–it’s not that hard).
Personally, I use LastPass. This and other programs like it (e.g. 1Password, KeePass and more) can help you track your passwords, and centrally store them (so they can be automatically filled out for you when you visit websites, etc.). They also help generate unique passwords for each site using a built-in password generator (random characters). The key here is that you don’t have to actually know the passwords, you just need to ensure they are randomized, and different for different sites & providers.
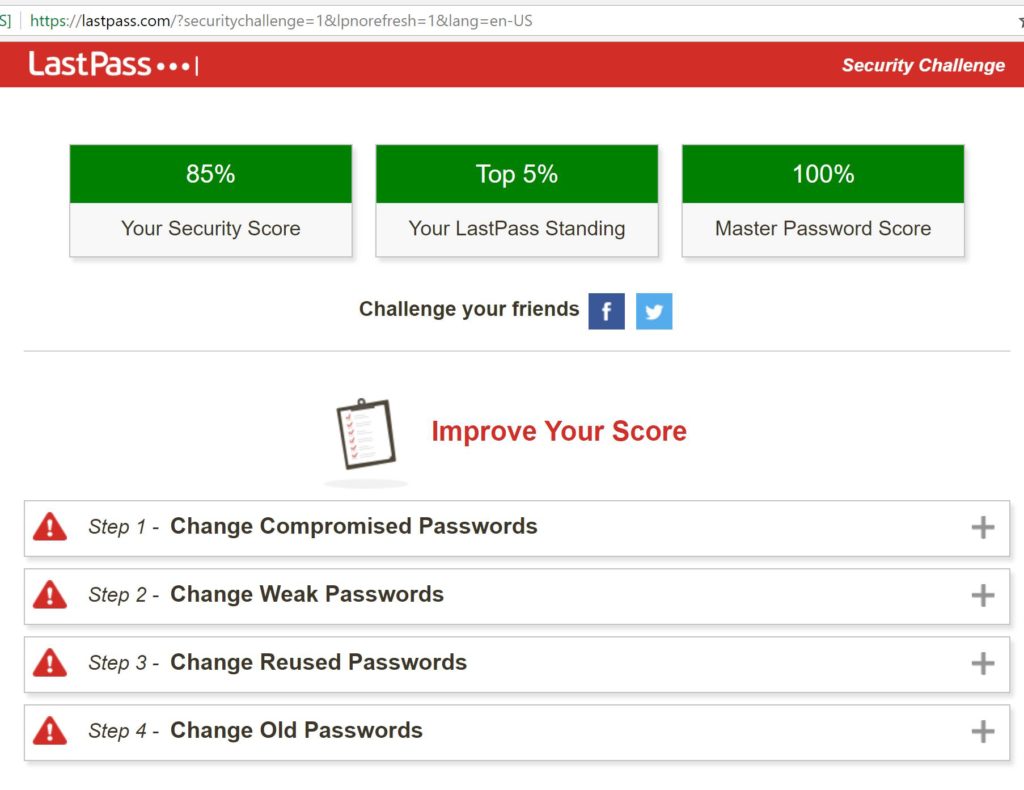
These services have free and paid versions, and I can say from experience, the pay versions are usually worth it (use multiple devices, access to more features, etc.). LastPass even has a feature called “Security Challenge” that analyzes your passwords for weakness, duplicates, etc. and compares how you line up to others.
Drawbacks
Credential managers like these can be a bit controversial, because it means all your passwords live in a single place, and if that one place is compromised, attackers have access to a whole treasure trove of your stuff. Well, that is true I suppose, but without a tool like this, it can be very difficult to achieve the same level of security, since most of us now have dozens of passwords we need to remember and maintain.
Another drawback is user experience. On the PC or Mac, tools like LastPass or even just the key-chain built into many OS’s and web browsers provide a simple and streamlined user experience. But the problem is, it doesn’t always translate into other platforms or devices, such as mobile devices. On my iPhone for example, I sometimes find myself having to leave whatever app I’m signing into (like a banking app), switch over to the LastPass app, find the credentials I need, copy the password into my clipboard, and then switch back to the banking app to paste them into the password field. In a few rare cases, the paste function isn’t even available, so I have to “show” the password in LastPass, then flip back and forth a few times to fill out the values correctly. Not exactly awesome, but I recognize this inconvenience is necessary to achieve greater security.
Mitigating your risk
If the LastPass database ever were hacked & leaked, I would of course have a fair amount of work ahead of me, to get busy changing all my passwords. Some other ways I might mitigate my risk/exposure on this platform is to ensure 2FA is setup on my LastPass account, as well as other accounts, and to tie it to an email account which is not stored in the credential manager itself, or used in other websites & services–remembering just two or three complex passwords is still better than remembering 50+.
Some people prefer using something more “local” like KeePass because the password file is kept on your devices themselves, somewhere of your choosing (in other words, not in the cloud). Therefore you can ensure the file is encrypted and that the device itself is, and you could keep a backup copy on different (encrypted) devices, etc. Note that if you make updates to your “master file” you will want to export/import it to your other devices, to ensure they are kept in sync (this is a manual rather than automatic process–with a cloud service such as LastPass it would be automatic).
No matter how you choose to achieve better password hygiene, just know that it is worth your time. Don’t be a target. Fight back and protect yourself in whatever ways you can. If you’d like to be notified of when your email address turns up in real life breaches, visit haveibeenpwned.com, and sign up.


Leave a Reply