Question from a reader: Compliance and Office 365
I have great readers, asking great questions. Recently, I received this one:
Do you think you can do an article on HIPAA compliance and the types of licenses needed? My situation is I am the admin and have an E3 license and all of the other employees have a Business Premium license. Some people tell me everyone needs an E3 and above license to be HIPAA compliance. As me having E3 I can use and turn on DLP, archiving, eDiscovery hold and export, mailbox hold, Information protection: message encryption, rights management, auditing, etc. So why would everyone need an E3 license when I can turn on those things for the Business premium employees? Thanks –Jacob
Good questions, Jacob. I’m going to answer it in two parts:
- Regarding Compliance
- Regarding Licensing
Compliance is not about subscriptions or products
When you’re dealing with HIPAA or any body of compliance standards really, you have to realize what that really means. When it comes to licensing and software, just know that it isn’t so much about the subscriptions or set of products that you have. First and foremost, it is about how you choose to meet the controls called out by the compliance.
For example. One of the requirements that is spelled out in the Health Insurance Portability and Accountability Act is that a covered entity must file incident reports whenever Protected Health Information (PHI) is shared inappropriately (either by accident or because of a breach).
Now, this gets a bit complicated, because some sharing of PHI is often necessary between providers, etc. and that is okay so long as they are protected with a Business Associate Agreement (BAA) and the other entity is following their own proper procedures. So that would be considered appropriate. But it would be inappropriate to accidentally forward documents containing personally identifiable information or PHI to the wrong individual, for example, whether internal or external.
Now according to HIPAA every breach minor or major needs to be recorded and kept on file. In the event of major breaches, the covered entity is required to report the details of the breach within a certain time frame of discovery. Minor breaches can often be handled internally, without a requirement to notify the feds.*
But how can you monitor communications to ensure that accidental or nefarious breaches are even taking place to begin with? Obviously, one might naturally look toward Data Loss Prevention (DLP) in Office 365. Does that mean you have to use DLP in Office 365 to be “compliant?” No. Not necessarily–you could find other ways to monitor/review/block certain communications.
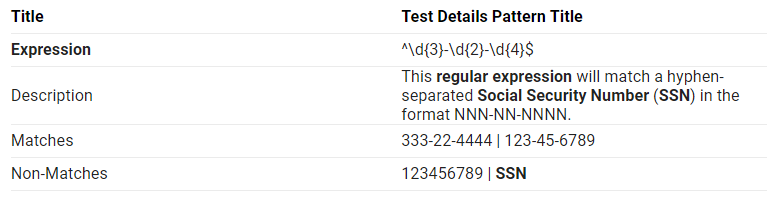
For instance, you could use regular expressions in a transport rule that would not allow social security numbers and the like to be emailed around. Or you could just choose to do a supervision against your users’ mailboxes and perform regular review. If and when breaches are discovered during these regular supervisory reviews, then you have a certain amount of time to file an incident report and respond to the event.
But DLP is “smart” tool that is available to you in the right subscriptions, and which can make identifying (and preventing) possible breach events much much easier. So it is very often recommended (but not “required”).
Remember that it is up to the organization how they want to mitigate and manage their own risks. It is a business decision.
Note also, that DLP in and of itself is not a guarantee of compliance. Microsoft is careful to remind us of that. Adhering to the rules of compliance isn’t just setting up a DLP policy, ticking a few check boxes or whatever. And you might still want to combine methods together anyway, once you learn how DLP actually identifies sensitive info types (yes, it can misidentify data).
I’ll give you another example. One of the most common things that organizations do in a HIPAA environment to prevent the accidental viewing of ePHI on a screen by an unauthorized person is to enforce automatic screen lock (after a very short period of inactivity such as a minute or two), and/or by using “privacy screens” that attach to monitors so that content cannot be viewed at angles less than (or greater than, depending on how you look at it) 90 degrees.
But another way you could deal with this is to avoid putting monitors that could potentially display ePHI in public areas in the first place. So a physical control rather than a digital control (sometimes you have no choice based on how the business operates). One more example, and then we’ll switch over to the licensing piece.
I had a client come to me insisting that we implement port security on their switches, because they read about it in a tech journal–some article on HIPAA. Port security means that you would literally make it impossible for any other MAC addresses to become connected to the switch fabric, other than the ones you have already approved in the environment. So it’s a pretty good measure for tight security, but it comes with a cost, too (and is more difficult to maintain over the long term). But the control itself is highly generic, basically just saying that the covered entity must take measures to prevent “unauthorized access to ePHI that is being transmitted over an electronic network.”
Well that could mean all kinds of things, and imply both physical and digital controls. So we started with a physical walk-through of the premises and I could not find any areas where I would have been concerned that someone would have gained unauthorized access to a physical port. Those areas that would have benefited were entirely within their business office and not connected to the clinic in any way. The switches themselves were completely locked up in a room that only two people in the organization have access to with an electronic key card. And the business office itself was not a place for the general public.
I asked if they were concerned with insiders gaining unauthorized access by hijacking a switchport. They laughed. No. Most of them don’t even know what that was. Then I asked if the premises was well protected with door locks, cameras, alarm systems and so forth. Yes. Okay then, so implementing switchport security may not really improve your posture that much, and it’s hard to argue that it helps tick off any compliance check boxes that you don’t already have covered in some other way.
So instead, we focused on improving wifi security since the clinic is primarily dependent on wifi access. See what we did there? What is the control asking you to do, and how might you close the gaps that actually present risks in your unique business environment?
Licensing and Compliance
Now obviously technology can make our lives much better and provide some options and tools so that we can manage risk more efficiently (nevertheless it still requires human labor at the end of the day–very few things are set-and-forget when it comes to compliance).
In the world of Office 365, you are correct, Jacob–that Office 365 E3 includes DLP, Office Message Encryption, litigation hold and so forth, and all of that stuff makes your life easier than Business Premium. Microsoft 365 Business also contains the goodies you’d be looking for, and assuming your org is less than 300 users, I would suggest upgrading your users to that, rather than E3. But that’s my opinion.
Anyways, while it is true that even adding a single license in some cases will unlock capabilities for the entire organization, Microsoft’s official stance is this: If a user benefits from the features of a subscription license then they must be licensed for that feature. Therefore, if your users benefit from email encryption, litigation hold, DLP, retention policies, etc., etc., then they MUST be licensed for those features (even if it “works” without assigning every single person a license).
*As with anything, you should go check what you read on this blog against first sources, such as the Department of Health and Human Services.






Comments (4)
Hey
Thanks for writing the article up so fast. So after reading, it seems we do need to upgrade the licenses simply for the fact that you said
“Therefore, if your users benefit from email encryption, litigation hold, DLP, retention policies, etc., etc., then they MUST be licensed for those features (even if it “works” without assigning every single person a license).”
I have looked into Microsoft 365 Business and it does seem to offer more things we would use compared to E3. Do you know if upgrading everyone to Microsoft 365 Business that we can meet Hipaa compliance and stay within Microsoft’s license usage as mentioned above?
Thanks
By upgrading everyone into M365 Business you will have access to a lot more security & compliance goodies than what you have with Business premium, or what you can get in E3. For example, Microsoft 365 Business just announced today that Conditional access is now included, which is huge. https://techcommunity.microsoft.com/t5/Microsoft-365-Business-Blog/Conditional-Access-is-now-part-of-Microsoft-365-Business/ba-p/684063
There is a giant divide now between what Microsoft 365 Business and Office 365 E3 offers now–there is just no contest (and it’s the same price).
Another great article Alex. How can a screen lockout be configured in an Office 365 cloud only environment? I know Group Policy can be used in an on-premise Windows server but is there a way to set it up in Office 365? I see so often users leave their PCs powered on or not log off or use the lock option by pressing Ctrl-Alt-Del.
Yes, Intune can do this using either device configuration or compliance policies. Intune is included with Microsoft 365 Business.