How to use DLP to automatically file HIPAA incident reports in Microsoft 365
I have previously written about Data Loss Prevention (DLP) on this site, and today I am going to demonstrate another important use of this technology in helping to meet certain compliance requirements for HIPAA.* You can also apply this process to other sensitive information types, where incident reports are recommended, or in some cases required, for external sharing.
Most of the time, allowing ePHI outside of the organization (“Covered Entity” in HIPAA language) should be avoided. However, this type of information sharing is sometimes unavoidable and even necessary in the course of normal business–especially with regards to certain vendors and partner organizations with whom the covered entity has a Business Associate Agreement (BAA). Still, whenever ePHI is shared externally, whether by accident or in the normal course of business, according to HIPAA, there needs to be an incident report kept on file by the Covered Entity. We can automate this filing using a simple shared mailbox and a DLP policy, which will deposit any detected incidents into an email report.
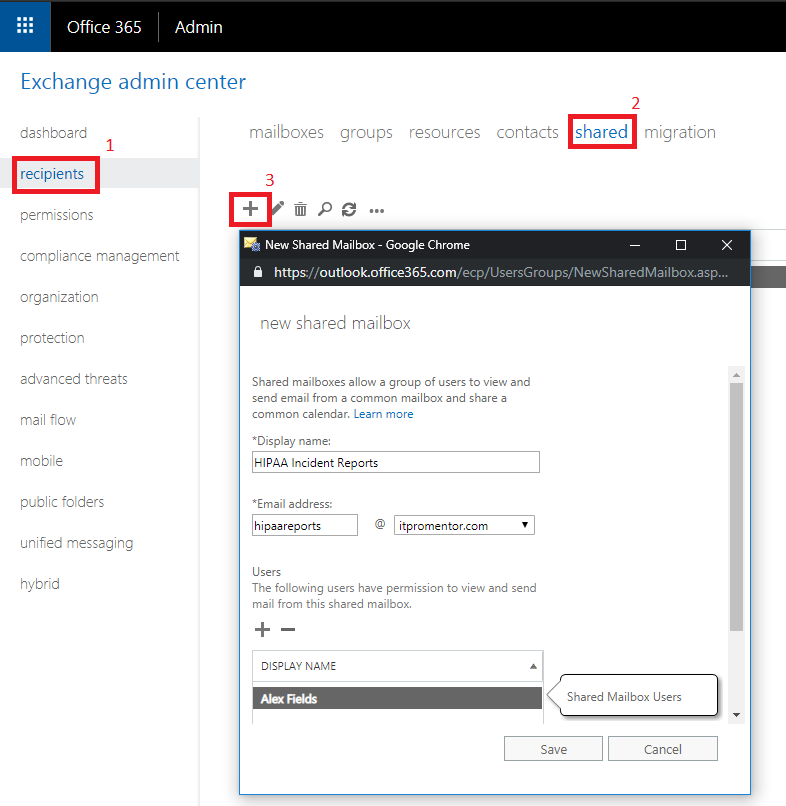
1. Create a shared mailbox
First, create a shared mailbox in Exchange Online, and give it a descriptive name such as “HIPAA Incident Reports.” Go to recipients > shared > New Shared Mailbox (+). From here, fill in the Display name, email address, and grant access to at least one user (often the designated HIPAA officer). Click Save after making your selections.
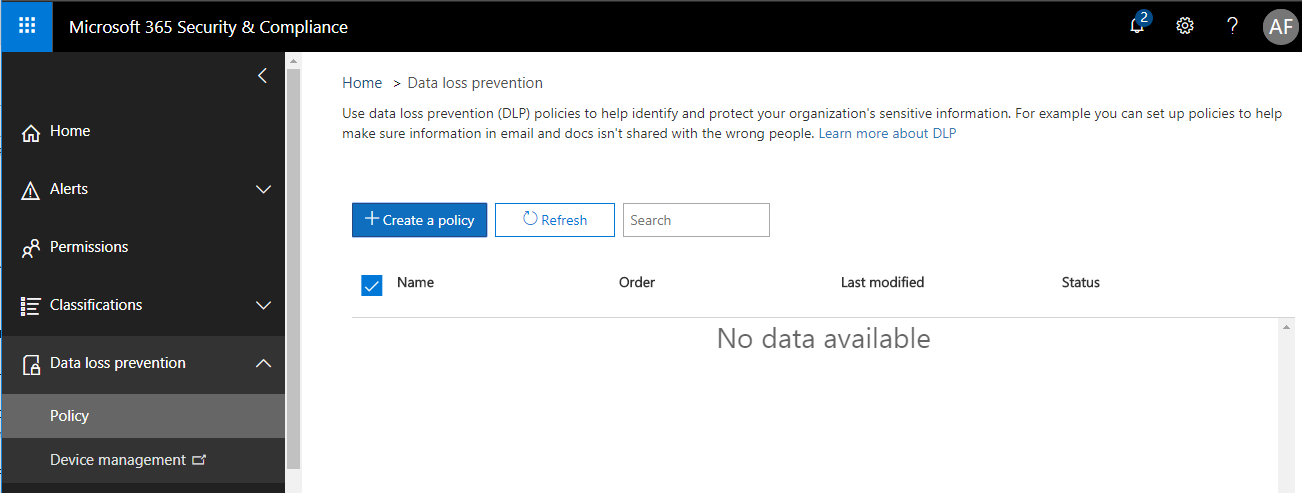
2. Create a DLP policy with advanced settings
From the Security & Compliance center, go to Data loss prevention > Policy. Choose Create a policy.
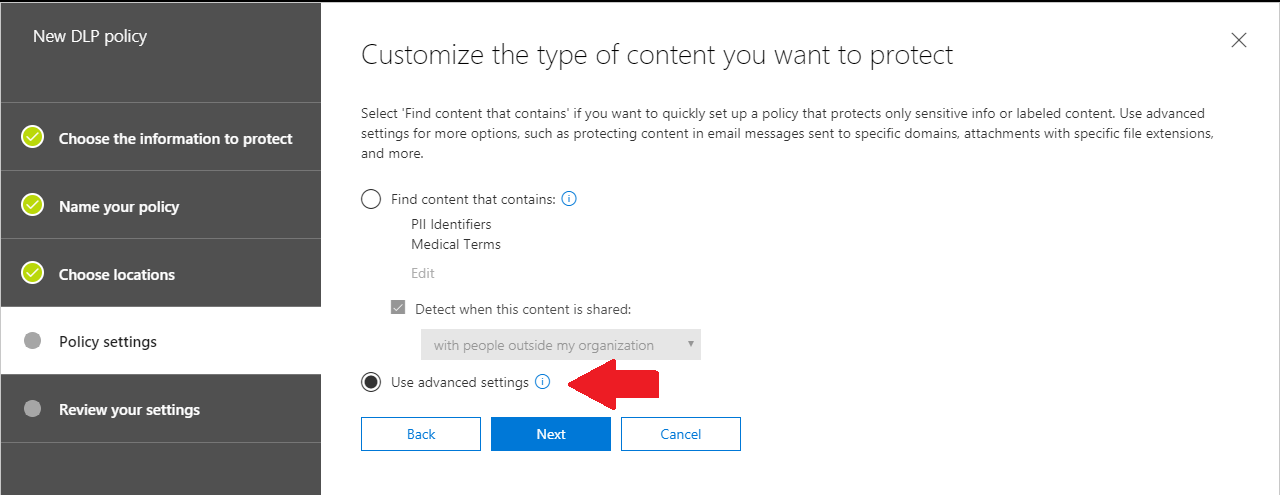
As you step through these screens, give your policy a descriptive name. I usually chose to protect All locations in Office 365 (e.g. SharePoint libraries/Teams sites also). Next you will want to be sure to choose the Use advanced settings option, so that we can edit things more to our liking.
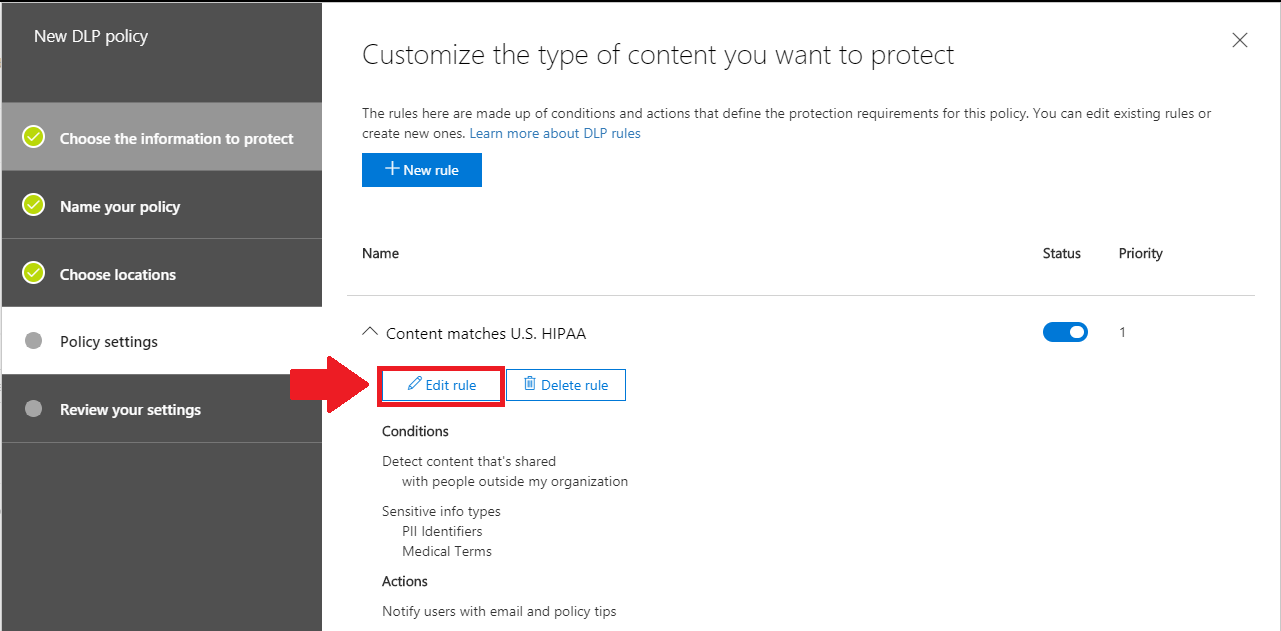
3. Edit the rule
Expand Content that matches U.S. HIPAA, and choose the option to Edit rule.
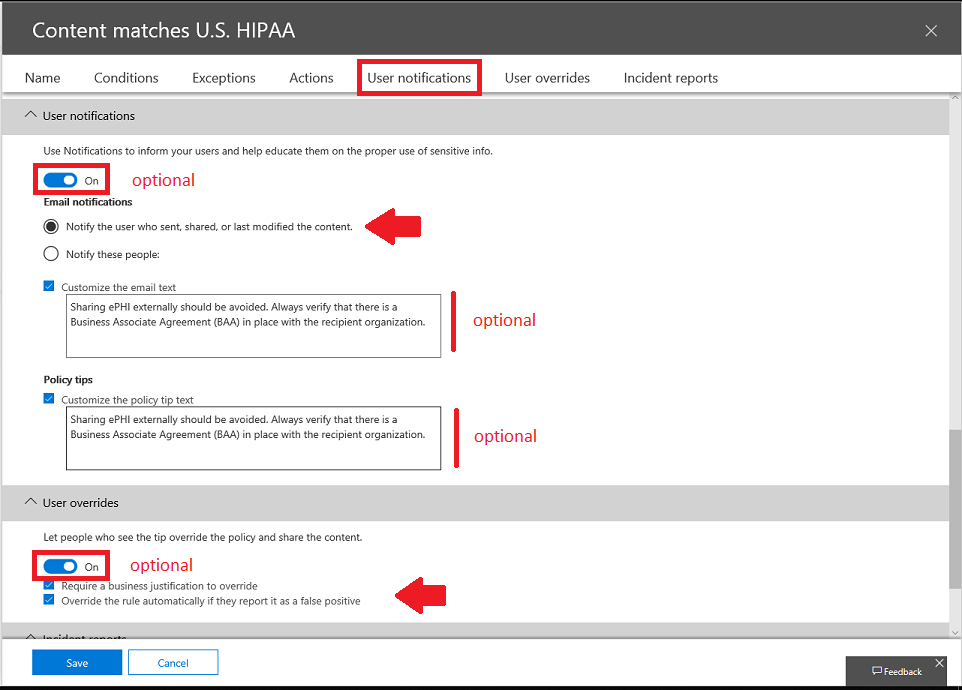
Optionally: Under User notifications, you can notify end users and give them an opportunity to provide business justification or identify false positives. The override piece applies more to policies that are designed to block sharing–which in turn is configured under Actions.
But we’re not concerned with that here–we just want incident reports. I do want you to be aware, however, that these things are also in your menu of options when deploying DLP. For example, I have also written some custom text for the end user notifications and policy tips.
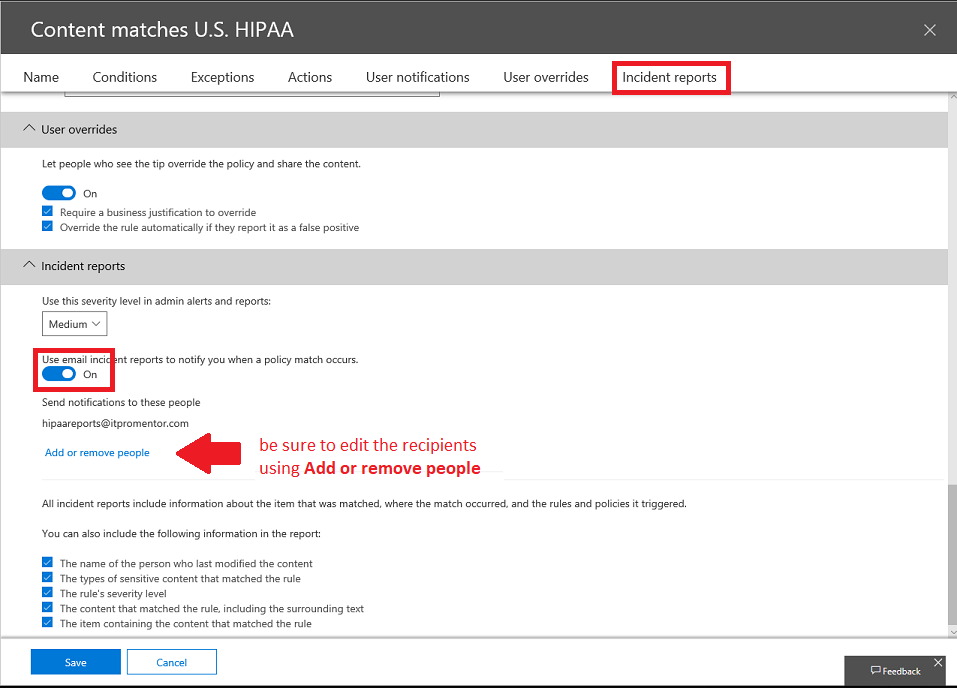
Next (and most importantly) configure Incident reports. Switch the setting to On, and be sure to edit the recipients using Add or remove people. Be sure to add your newly configured HIPAA Reports shared mailbox.
You will also notice there are options here for whether or not to include the content that was shared along with the incident report–this may or may not be advisable depending on how you handle incident reports. For instance, may only need to show that an incident was recorded, and not what the explicit content actually was. I recommend consulting with an attorney who represents your organization, and is versed in HIPAA. Save the settings when you are done.
4. Finish the policy, and turn it on
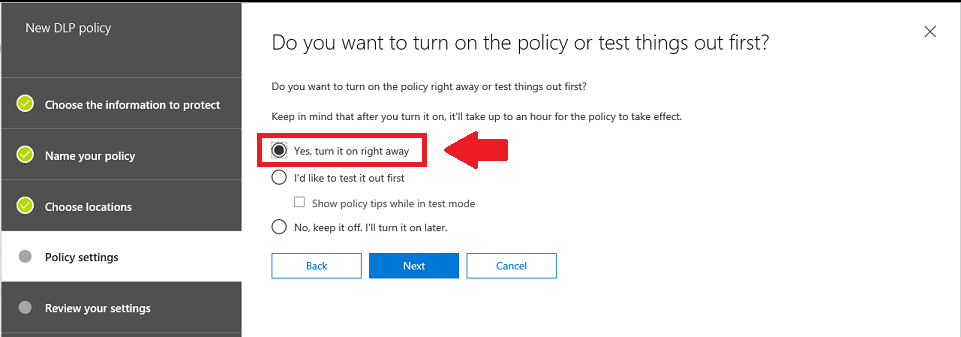
Finally, you can say Yes, turn it on right away, then Next and Create on the final screen, to finish the wizard, and after reviewing your choices. This can take some time to take effect. Sometimes it is fast, other times I have waited for more than hour.
5. Verify the results
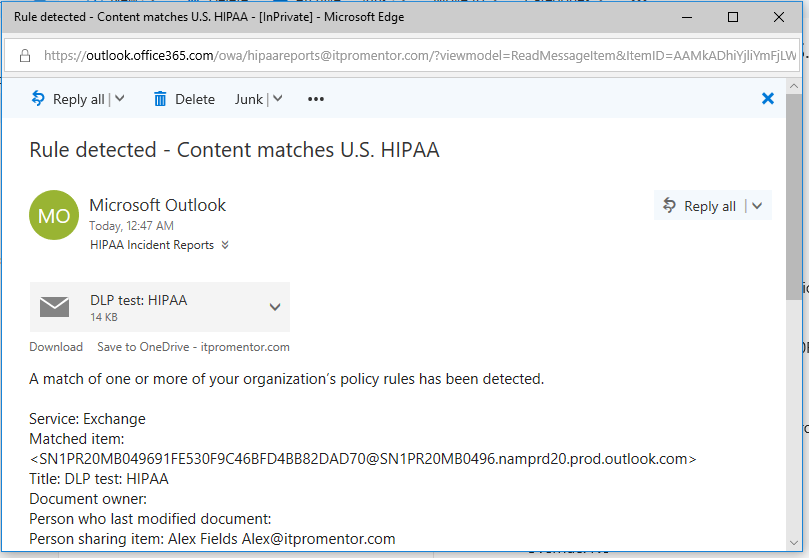
The result of this policy is that any detected Personally Identifiable Information (PII) that is used in connection with known Medical Terms will generate an incident report that is filed in our shared mailbox. If ever auditors (or litigators) want to see your incident reports, you can simply do an export of this mailbox to PST. Here is an example below.
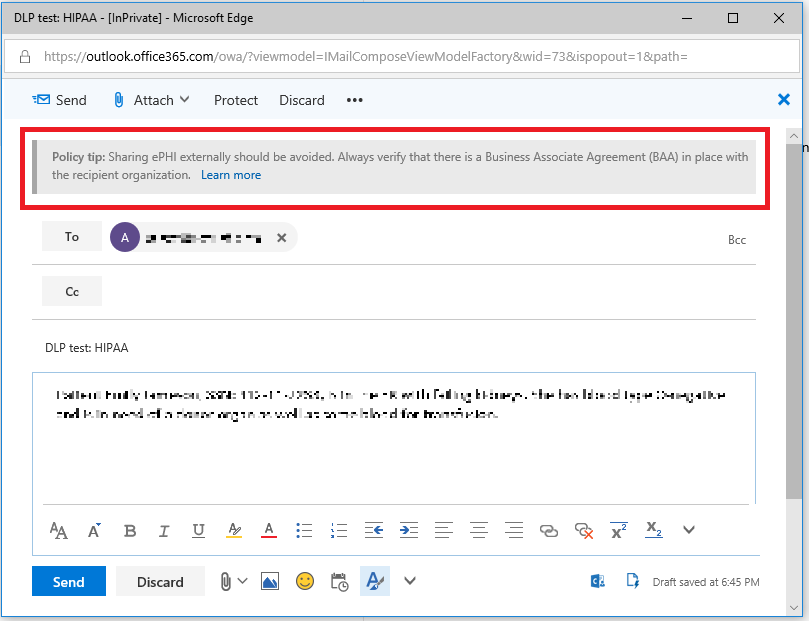
If you also had the user notifications turned on, then the individual sharing the content will see the custom alert text you entered, known as a policy tip (and they also get an email to a similar effect, after sharing it).
This concludes our demonstration of the DLP rule to automatically file incident reports for HIPAA. As I have stated before, DLP can do a lot of different things, and comes with a lot of options, so be sure you have the end goal in mind when you begin to build your policy–and don’t just go after this feature haphazardly.
*Microsoft is careful to point out, however, that implementing DLP policies does not necessarily make you “compliant” with any laws or regulations–they are just providing tools that can be useful in working toward compliance (but they cannot guarantee compliance of course).



Leave a Reply