Top Mobility-Enabling Security Features in Office 365
At this point, even the staunchest conservatives among us have to admit that we live in a post-perimeter world. In recent years there have been even more developments and trends chipping away at our traditional conceptions of so-called perimeter-based security.
Cloud and mobility means two things:
- Users can go straight to the Internet from any device and any location and get access to their corporate resources (they are usually stored in someone else’s datacenter)
- As a corollary, IT has very little control, visibility and protections to offer their cloud-enabled mobile users (sorry)
But there are other indicators besides that a domain-and-firewall lock-down approach just can’t be that successful anymore. For example, with Internet encryption on the rise (which you might think is a good thing), it paradoxically means that IT has a harder time protecting their user’s traffic with traditional tools like firewalls and other forms of packet inspection.
Software-defined security
It is now on the heads of the software and service providers to protect their users and their users’ data. So what do you think? Do you trust Google to do that for you?
I believe that when you look out across the landscape of cloud software products with an eye toward modern, mobility-enabling security features, Microsoft is the clear leader. We have some pretty great application-level controls and levers available to us, which makes us feel good since it puts more control–more options–into our hands.
Let’s ignore the Enterprise Mobility and Security products for a second, and just look at what we can achieve with Office 365. We can look at security in Office 365 from three angles.
1. Identity is managed through Azure Active Directory
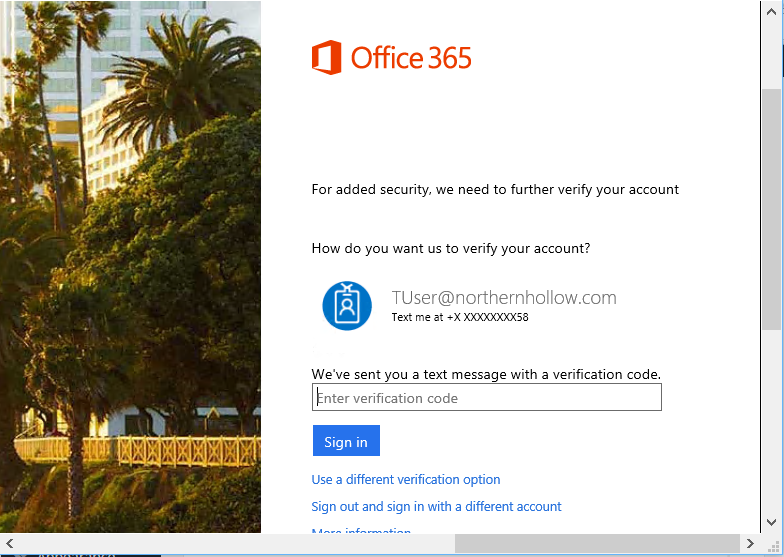
Do you know what comes with every single Office 365 plan? Azure Active Directory. That’s how you authenticate to the cloud with your email address and password.
Do you know what else you can do to protect that identity, again with any version of Office 365? Multifactor authentication (MFA). It is quick and easy to setup, and makes it much more difficult for attackers who are able to gain access to your password, whether through a keylogger, a website breach or hack, or some other means.
One thing to note: MFA can be sort of annoying. In addition to getting a code sent to your mobile device as a second step every so often, it carries the added complexity of an “app password” which is a randomly generated string of characters that you might have to supply sometimes for certain applications. The only reasonable solution I’ve come up with to deal with this is to store the app password in something like LastPass’s Secure Notes, since you have to dig it out now and again, and it’s almost impossible to memorize unless you’re some kind of savant.
2. Devices can be managed with Mobile Device Management for Office 365
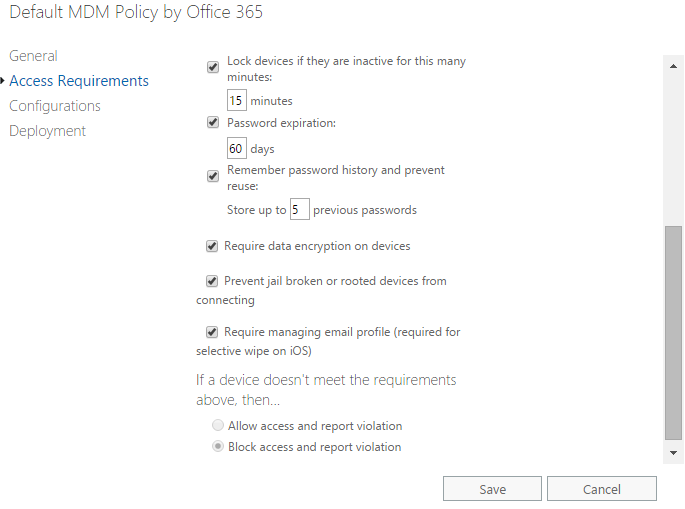
Every version of Office 365 comes with a “Lite” version of Microsoft Intune that allows you to enable “Conditional Access” for your mobile users. This means that you can withhold access to corporate applications and data stored in the cloud until users agree to accept your terms, which includes a managed profile, the ability to require encryption, passcodes, auto-lockout and wipe policies.
Also, with Mobile Device Management turned on, you can “selectively wipe” a device, meaning that just the corporate data/email profile will be removed, without destroying other data on the device.
3. Data from applications can be protected with Information Rights Management and other cool add-ons
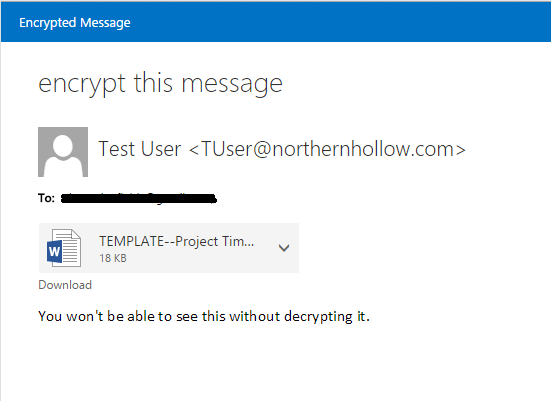
With Information Rights Management (available with E3 or as a separate subscription for Azure Rights Management) you can do cool things like flag Email messages and documents with special rights such as “Do Not Forward” (meaning: I want to share this content with you, but I don’t want you to share it with someone else). You can also enable secure message encryption which requires authentication by the intended recipient on a secure website to retrieve the content of the message.
Data Loss Prevention (DLP) is available with Exchange Online Plan 2 / E3. This lets you apply policies that in turn automatically flag content with sensitive types of data based on templates (think SSN’s, ABA/routing numbers, credit card numbers, etc.).
Another add-on worth mentioning is Advanced Threat Protection (ATP), which helps protect against zero-day threats. This is available wtih E5 (almost nobody buys this expensive plan) or as a separate add-on, and it comes with two great features: Safe Links and Safe Attachments. In this case, Microsoft is “detonating” the contents of an email message in a cloud sandbox before users ever receive it. If a link is determined to be “dark” or an attachment malicious (even if it passes other Antimalware scans), the user will be protected from it, whether they are inside your perimeter or not.
Security. Be About it.
So here’s the thing. A lot of this stuff isn’t on by default. And it’s not always intuitive to get setup. So you might need to work with a technology partner to help you stay protected and ahead of the game when it comes to this “mobile-first-cloud-first” stuff.
Yes, I totally drink the mobility Koolaid, as I think most of us should. But we have to at least try to be somewhat safe about it, too, right? I believe Microsoft has given us a good start in the right direction with Office 365.



Leave a Reply