The evolution of small business networks
I believe there are only three basic types of networks alive in the small and mid-sized business market today.* Legacy, Hybrid and Modern. Now the labeling on these categories is purposeful–the language represents a progression in time, but it is important to remember that there still exist “legacy” environments, just as often as we can point to real-world examples of both hybrid and modern networks.
Let me describe each in turn.
Legacy Networks
The Legacy Network is where most of the small businesses came from, if they were in business prior to say 2011 or 2012. For the most part, if and when cloud apps were being used at all, it was because an end user went out and signed up for some third-party services on their own. This was (and still is) widely known as “Shadow IT.” The most common Shadow IT apps back in those days would have been DropBox, Google Drive, Evernote, GoToMeeting, Webex, and maybe a few others. These days we have a lot more, like Slack for example.
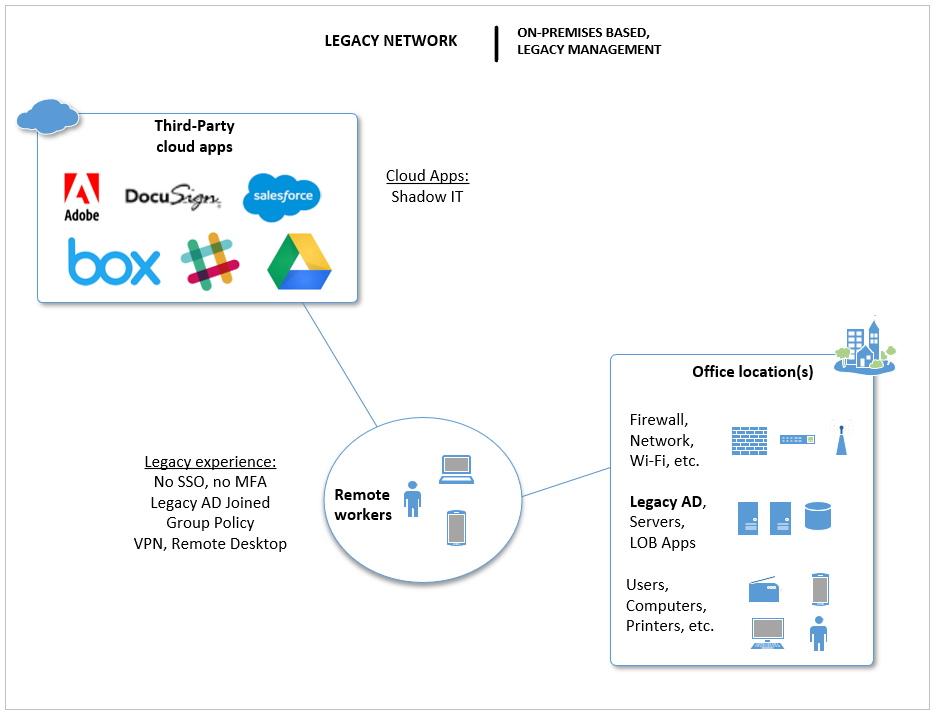
The experience for end users went something like this: they had to physically come into the office to do their work. From their work-tethered PC’s, they could access file servers, printers, and line of business applications. They signed into a local Active Directory domain, and their password would change every so often, so they would just append the next digit in line to the end of their password when it came around. We thought this was more secure, but the hackers and bad actors were just laughing at us. If we were really on top of stuff, we added other good things like a firewall with UTM, antivirus on every endpoint, and kept up with patching, etc… but all of those measures, while still necessary, are not sufficient in today’s world.
Getting remote access was possible, but challenging. VPN and/or Remote Desktop were the options. If laptop computers that belong to the local domain leave the environment–especially when they leave often or for longer periods of time–chaos ensues. Domain password changes couldn’t link up to the cached credentials on the computer. If network drive mappings or other Group policy changes were pushed, then the remote devices often fell out of sync with those changes, and so on.
Even at the office, it could be tough to get certain requests handled. All of these experiences frustrate users, so naturally they are forced to find third-party apps out on the internet that can “just work” for them out of the box, without IT.
Finding data was getting harder and harder because those old file servers had been migrated from one version to the next as-was for over a decade. Besides that, people would often email themselves or upload copies of their documents to Google Drive and other places, just so they could keep track of “their” most recent version, and/or be able to work on the documents when out of the office.
Summary of the legacy model characteristics:
- End users were frustrated and finding ways to service themselves without help from IT;
- We had multiple logins, and islands of technology
- Password management was a nightmare
- Endpoints were often not well managed
- Visibility to risks, e.g. information security and compliance–was very low or non-existent
- Remote access was based on VPN and/or Remote Desktop, and is often challenging or frustrating to use
Hybrid Networks
This is the most common type of network in existence today. One key identifying factor is that some corporate applications now live in the cloud–they are actually sponsored/managed by corporate IT–such as Office 365. We may even find identity and password synchronization between the legacy AD and Microsoft’s Azure AD in the cloud. You might see some use of multi-factor authentication (MFA). Most other cloud apps are still islands though, whether sponsored by IT or not. And, there are probably still other legacy apps and data living on-premises. The same old legacy management tools anchor down the work-issued computers, and many of the same issues in general therefore persist.
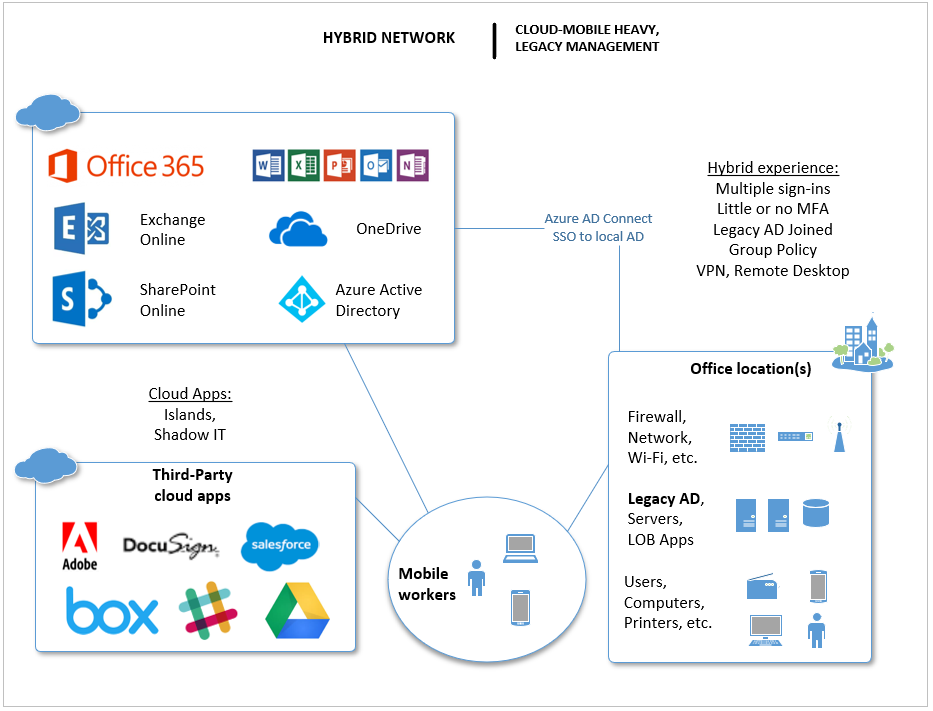
Most importantly, the biggest distinction we find in this new world is that “remote workers” have now become “mobile workers.” This is because of the rise of cloud applications and the proliferation of mobile devices that can connect to them. Users prefer working away from the office more than ever, and mobile devices are very often preferred to traditional PC’s. Employees may also be more likely to connect from their own laptop, such as a MacBook or other consumer product.
A summary of the hybrid characteristics:
- Reduced sign-on, but many apps are still islands
- Passwords are still changed regularly, and very little MFA implementation, if any
- Users still rely heavily on email for communication and sharing documents, but also use solutions like DropBox or OneDrive
- IT is still using legacy tools for device management
- Corporate IT sponsored devices are still difficult and time-consuming to provision and maintain
- Visibility in IT here is still considered low to medium; it is often hard to know who has what devices, and who uses what applications
- There is more awareness of risks and compliance issues, but not “caught up” on security yet; systems and process are built around protect (hope), while often neglecting detect and respond;
- Even if they started to get the hang of things on-premises, there remain huge blind spots since half their devices and apps are not under the same management framework
Modern Networks (Networks of the future)
Very few SMB’s have adopted the modern framework yet, but it’s coming fast. Some are more ahead of the game than others here. But, it is important to understand the movements that are happening, and the implications to both customers (end-users) and service providers (IT pros).
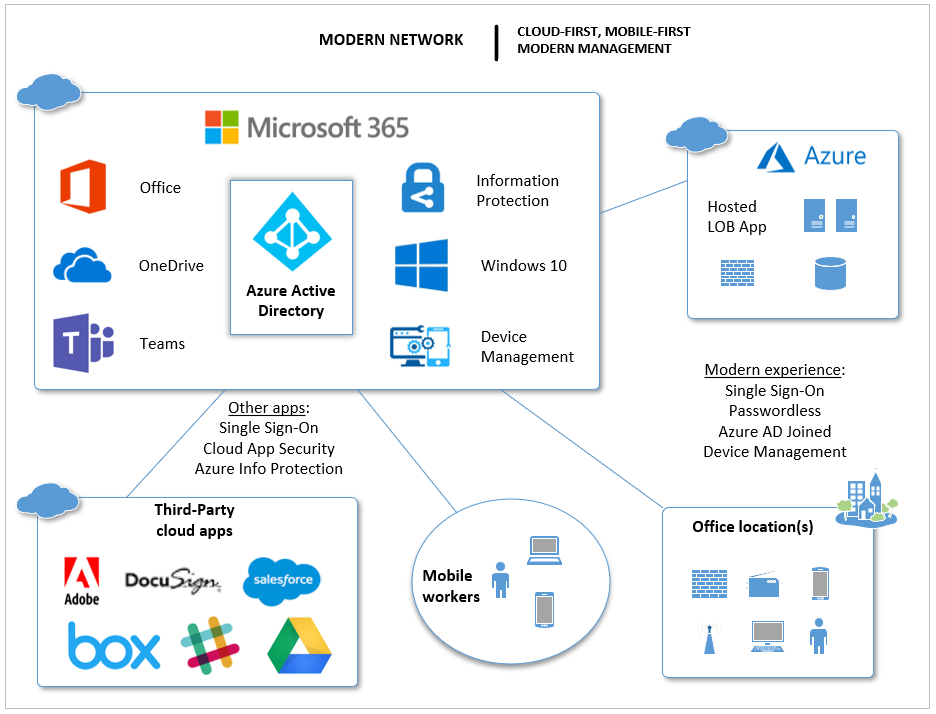
The modern network has a few distinguishing characteristics:
- IT has a handle on third-party applications; they all tie back to a single identity provider such as Azure AD, and most likely nothing is hosted on-premises anymore;
- You may see a legacy LOB app hosted on Azure or somewhere, but that is a temporary situation until a migration to SaaS can be accomplished
- Passwords never really need to “change” unless there is a detected breach, and multi-factor is implemented globally (or password-less)
- More “self-service” available for end-users, including modern apps like Teams; more communications and document sharing move away from email and toward these more modern apps
- All devices (iOS, Android, Windows, Mac) are centrally managed using modern tools (e.g. Intune). Devices are easier to provision and manipulate at-a-distance.
- All the endpoints are accounted for and protected, and we have added detection and response capabilities (e.g. Identity Protection, Threat Intelligence, Windows Defender ATP or another EDR)
- Application and data protections are in place that transcend device-and-cloud boundary lines (e.g. Cloud App Security, Azure Information Protection)
Because there is so much self-service and automation available for us to configure as IT admins in this more modern scenario, users will have a better experience. It means they don’t have to come to IT for simple stuff like password changes, provisioning new devices and so on. They can roll back to previous versions of their data. They can share out, invite in, add or remove membership to groups–all without bothering IT.
So what is IT’s job now?
Look, I know it feels sad to some–the users won’t be bothering you anymore for requests that they have historically. But guess what? That means you just gained extra capacity. And Thank God too, because you were already drowning in technical debt for the last decade. Especially in the areas of automation and security.
The “magic” of modern does not happen on its own. Someone has to go discover all the cloud apps, get SAML setup so that SSO works to each one of them, then provision app packages and push those along with configuration profiles out to new devices, so that when users pick up a new computer, Autopilot takes over and all their apps and data show up appropriately.
How about personal devices, will the experience be different on non-corporate devices than personal ones? You can control stuff like that, you know.
What else do you need to do, and what else should you be watching? There are several good alerts that come out of the box in areas like Identity Protection, Threat Intelligence and Cloud App Security, but you can customize a lot more once you start digging in.
When you do get alerted to suspicious activities (and you will), what is your process to respond to them? How do you notify and involve the customer in various circumstances?
What about helping customers with retention and data classification? Help themmanage against various compliance bodies such as GDPR (in EU), HIPAA (in US), and others? That is an ongoing deal, too, you know.
Conclusion
At the end of the day, just because everything moved to the cloud and the balance of power has shifted to the end-users, this doesn’t mean your job is diminished. This stuff still requires someone to engineer it, and someone to steer it.
Despite what the marketing will tell you, Modern is not as easy as ticking the check boxes–very little here is “truly set and forget.” Why? Because it’s always changing. Adoption is now continuous, and not just something that happens at refresh time. (By the way–end users need help with adoption, too–some of your time should be focused on helping them get more from their apps).
If you work for an IT service provider, you might have to restructure and modernize your service agreements (e.g. they should be per-user and per-app, not per-device), but don’t worry–it is highly unlikely that you will run out of valuable stuff to do. In fact, I find that I have the opposite problem. With the modernization of IT, it can be difficult to keep up with all that is out there!
So celebrate, and help us bring the next generation of computing into existence. Start converting your end users and customers over to the full Microsoft 365 platform, so you can modernize your management of identities, apps and devices. And as always, feel free to hit me up for questions or comments. You can reach me on Facebook, LinkedIn and Twitter.
*As I mentioned above, I only draw a distinction between three categories. I have come across a few businesses who imagined themselves in a fourth camp, or put themselves in the “modern” camp, simply because they have no servers on-premises. Look, just because you have no servers of your own, and connect to a virtual desktop in the “cloud” of some provider, doesn’t mean you are modern. In fact, where we see this happen, it usually represents a step backward, or at best, a lateral move from legacy to legacy or maybe legacy to hybrid (just hosted in someone else’s datacenter). The worst examples of this setup are when there is literally no attention being paid to the endpoints, and they are not part of any kind of common security boundary (e.g. they sit in a work group).






Comments (2)
And what would be needed (on the Microsoft cloud side) for a “modern network”?
Will Microsoft 365 Business do, or will more be needed?
Well it’s a pretty good start. I recommend Azure AD Premium P1, until they add conditional access. Also Cloud App Security. See recent post for more on that.