Tutorial: How to downgrade to the old Office 365 Message Encryption
I recently shared the method used to enable the “new” Office 365 Message Encryption features, built on Azure Information Protection. That process can be followed either to setup a new tenant with the latest version (v2), or to upgrade an existing tenant from the old version (v1.2) to the new version.
And now, I will share the opposite–how to go from v2.0, and downgrade to the old 1.2 version, which uses a different transport rule, and comes with a slightly different client-side experience.
But first, “WHY?! Why would you want to go backwards, Alex? WHY?!!!”
I’ll tell you why.
Because for some Organizations, the “new” hip OME experience will be unacceptably cumbersome in certain situations. The two biggest issues I’ve seen so far are:
Restrictions
In the new version, recipients cannot forward, print or copy the content of of the messages they receive. The reason is because the “new” features are really just using the RMS template for “Do Not Forward” to encrypt messages and apply protections. These protections include restrictions against printing, copying, etc., as well as a natural expiry date about one year into the future. It is the only template that can be used to send to users outside the organization.
So, if your plan is to keep your information very safeguarded every single time you share anything outside the org, then this is a good option. However, if you just want an encrypted delivery mechanism, but if you also want to allow your recipients to be able to work with the message/attachments, and actually do more than just look at the content, then you’ll need a different solution (like the old version of Office 365 Message Encryption). There are plenty of scenarios where you’d want your recipients to be able to print documents they received securely, etc.
Disparate recipient experiences
When using encryption technologies with email, organizations sometimes even have a “write-up” or “how-to” document that senders can get out in advance to their recipients. This is because encryption solutions aren’t always intuitive or convenient to use. But security isn’t always convenient, right? Even in the old version of Office 365 message encryption, users would get an email with an attachment, which they would need to open. That attachment is an HTML file that then presents them with sign-in options (use their MS account or use one-time passcode). It may not have been great, but it was better than a lot of the solutions out there. The steps are slightly different on mobile devices than Outlook or other email clients, but the idea is about the same.
In the “new” experience, this gets convoluted quickly. I can honestly report it does work “better” on almost every non-Microsoft email client. Gmail for example is great, because I can even choose to sign in with my Google identity, and there is no more annoying attachment requiring a special viewer on mobile devices. It just works right through a browser. And if you have an up-to-date Outlook 2016 client, it is seamless–just opens right up. But if you have an older version of Outlook–2013 or 2010 say, it is horrible–you can’t even open the message at all, without a special download from Microsoft (the user will also need to pick between 64 and 32-bit, for additional annoyance). Imagine sending out a document trying to explain the different scenarios depending on whether you have a certain Outlook version like 2010, and a 32 or 64 bit OS. Ick.
How to switch back to the old Office 365 Message Encryption
So in order to move backwards, if you plowed ahead with version 2.2, followed the instructions and were disappointed in the results, this is how.
1. Connect to Exchange Online in PowerShell
$cred = Get-Credential $session = New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri https://outlook.office365.com/powershell-liveid/ -Credential $cred -Authentication Basic -AllowRedirection Import-PSSession $session
2. Disable the “new” IRM configuration
Set-IRMConfiguration -AzureRMSLicensingEnabled $false -InternalLicensingEnabled $false -ExternalLicensingEnabled $false
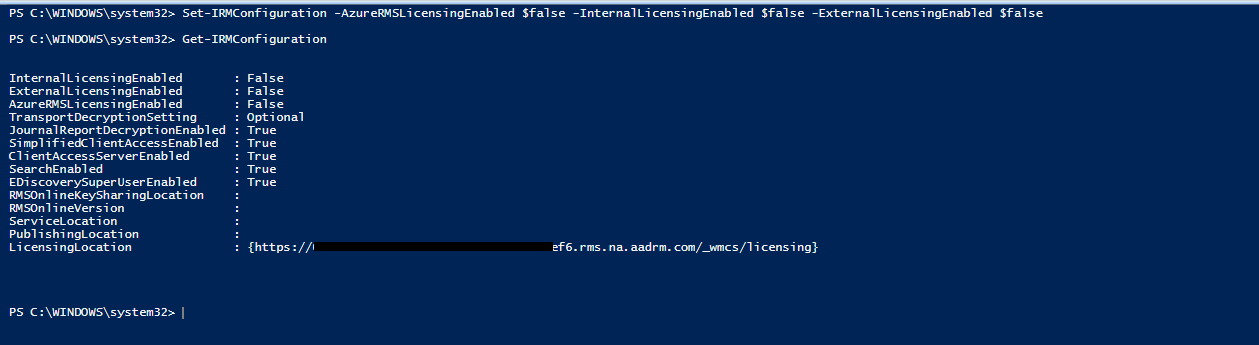
Once you have that done, a test of the service should fail
Test-IRMConfiguration -Sender [email protected]
3. Enable the “old” IRM
Set-IRMConfiguration -RMSOnlineKeySharingLocation “https://sp-rms.na.aadrm.com/TenantManagement/ServicePartner.svc” Import-RMSTrustedPublishingDomain -RMSOnline -name “RMS Online” Set-IRMConfiguration -InternalLicensingEnabled $true Set-IRMConfiguration -ExternalLicensingEnabled $true
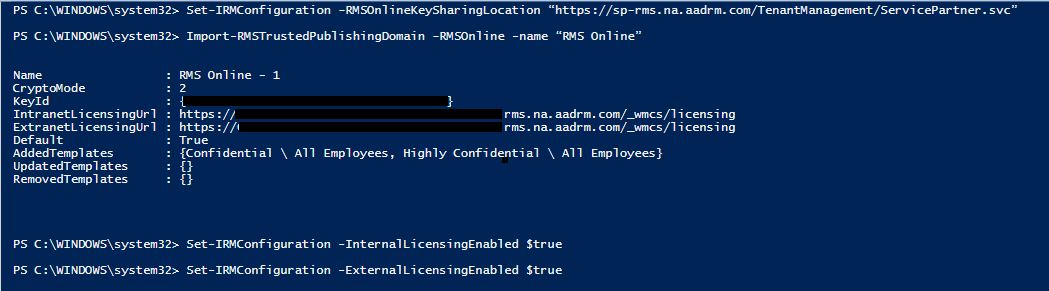
Don’t forget to update your encryption mailflow rules–they should use Apply the previous version of OME.

4. Last step is, test. Probably it won’t work. Then, you wait. Like, for several hours.Then test again. Eventually works.


Comments (9)
And if the recipients email server / filter is blocking attachments with passwords the new OME method will trigger that flag and be blocked. The old OME method will be delivered. Go figure.
Hadn’t noticed that yet, we will have to test this with the new OME template that just came out.
For OME v1 we can remove OME v1 from replies to encrypted message, but we cannot get a rule setup that will work with OMEv2. Keep receiving an error.
OME v1 Example:
Apply this rule if “the sender is located outside the organization” and “the recipiet is located “inside the organization”
Do the following “Remove the previous version of OME from the message”
OME v2 Error:
ERROR – You can’t create the rule containing the RemoveOMEv2 action with value true because FromScope in not specified or its value in not InOrganization.
Without a closer look, I would say it sounds like there is some missing parameter (you have to specify scope to InOrganization). There may be a PoSH way of accomplishing it as well.
OMEV2 is really annoying. I have users all on outlook 365 (Microsoft Office 365 Pro Plus) build 1809 and 1810.
Users on Windows 7 with the AIP client cannot open the message-but can click on the link in the preview pane.
Users on Windows 7 without client cannot open the message and cannot view it in the preview pane.
Same Microsoft Office 365 Pro Plus on Windows 10 works fine.
They all work in OWA.
Frankly a lot of people use Outlook and some are still on Windows 7 and some are on semi-annual channel. This OMEv2 is just too inconsistent for any org to support. We dont want to provide IT support for email recipients outside the org.
This post was helpful-thanks!
The Trusted Publishing Domain (TPD) for your organization should be managed in Microsoft Azure Rights Management.
The ‘RMSOnlineKeySharingLocation’ parameter has been deprecated. For more information, see
http://go.microsoft.com/fwlink/p/?LinkId=789272.
This cmdlet is deprecated. The Trusted Publishing Domain (TPD) for your organization is managed in Microsoft Azure Rights Management.
For more information, see http://go.microsoft.com/fwlink/p/?LinkId=789272.
Late to the party, but another huge reason to avoid the new OME is that it wreaks havoc when you’re sending to a shared mailbox on the other end. The users can’t open the message.
Exchange Online allows you to create a transport rule with the predicate “Encrypt the messages with previous version of OME”.
I’ve confirmed with message traces that messages triggering this ETR use the Exchange Online Encryption Agent (OME v1) rather than RMS Encryption Agent (OME v2)
Yes, OMEv1 is still available. It is recommended to move to v2 however. Back at this time, once you upgraded you would have to manually downgrade. But also at this time v2 wasn’t fully baked yet. It’s been improved since then so I don’t know anyone still implementing or using v1 anymore.